A Vulnerability Exploitation Detection and Recognition Method Based on Dynamic Memory Fingerprint Anomaly Analysis
A dynamic memory and identification method technology, applied in the field of network security, can solve problems such as long time-consuming, incompatibility with the operating system, high upgrade cost, etc., and achieve the effects of low cost, wide coverage, high support rate and program compatibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
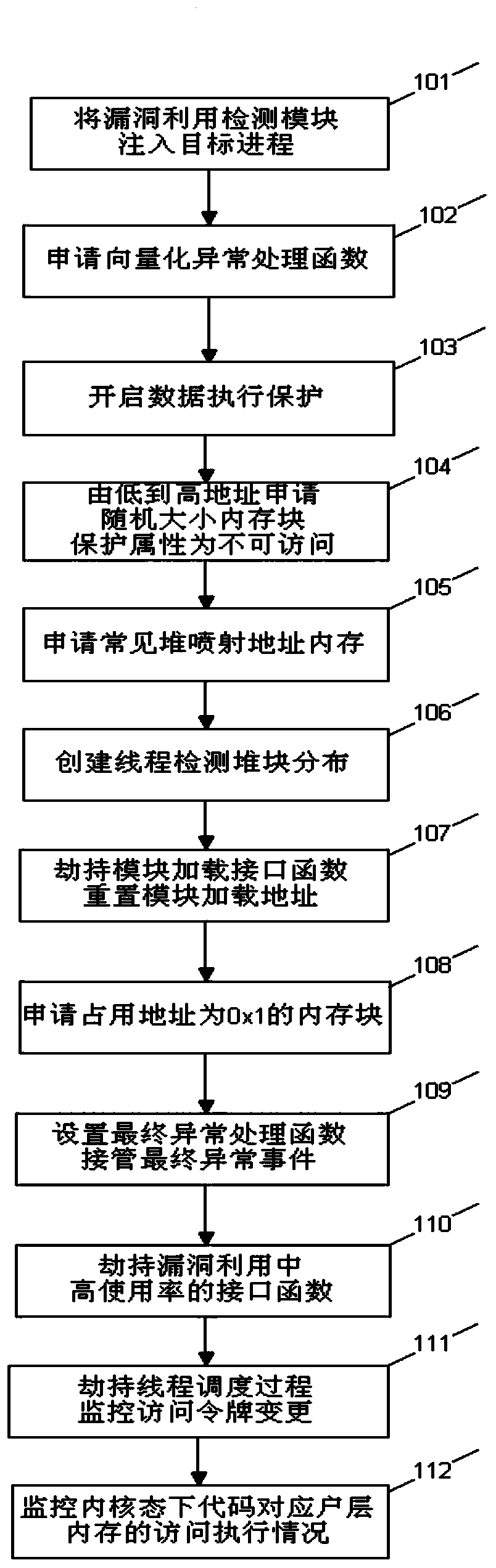
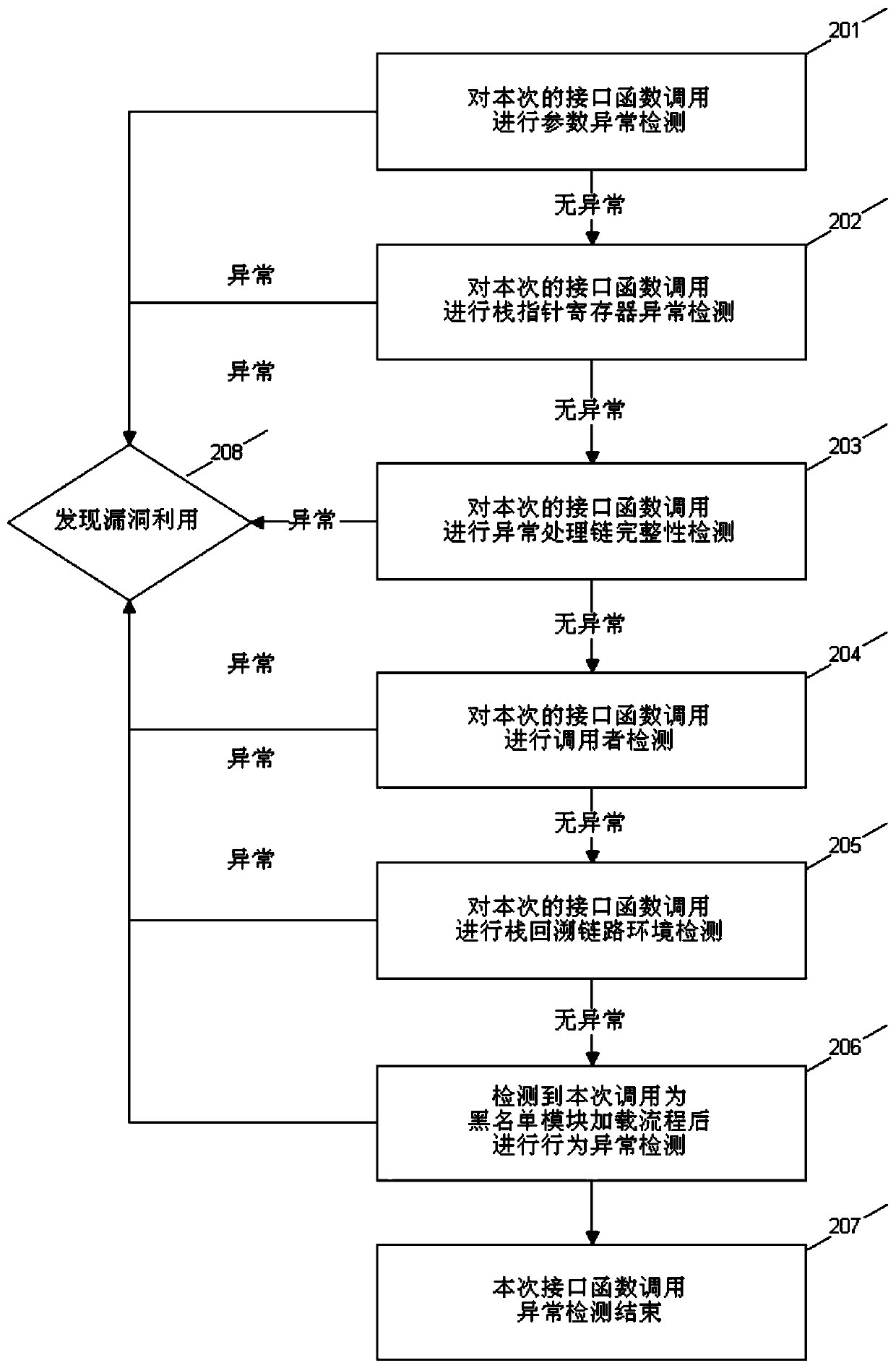
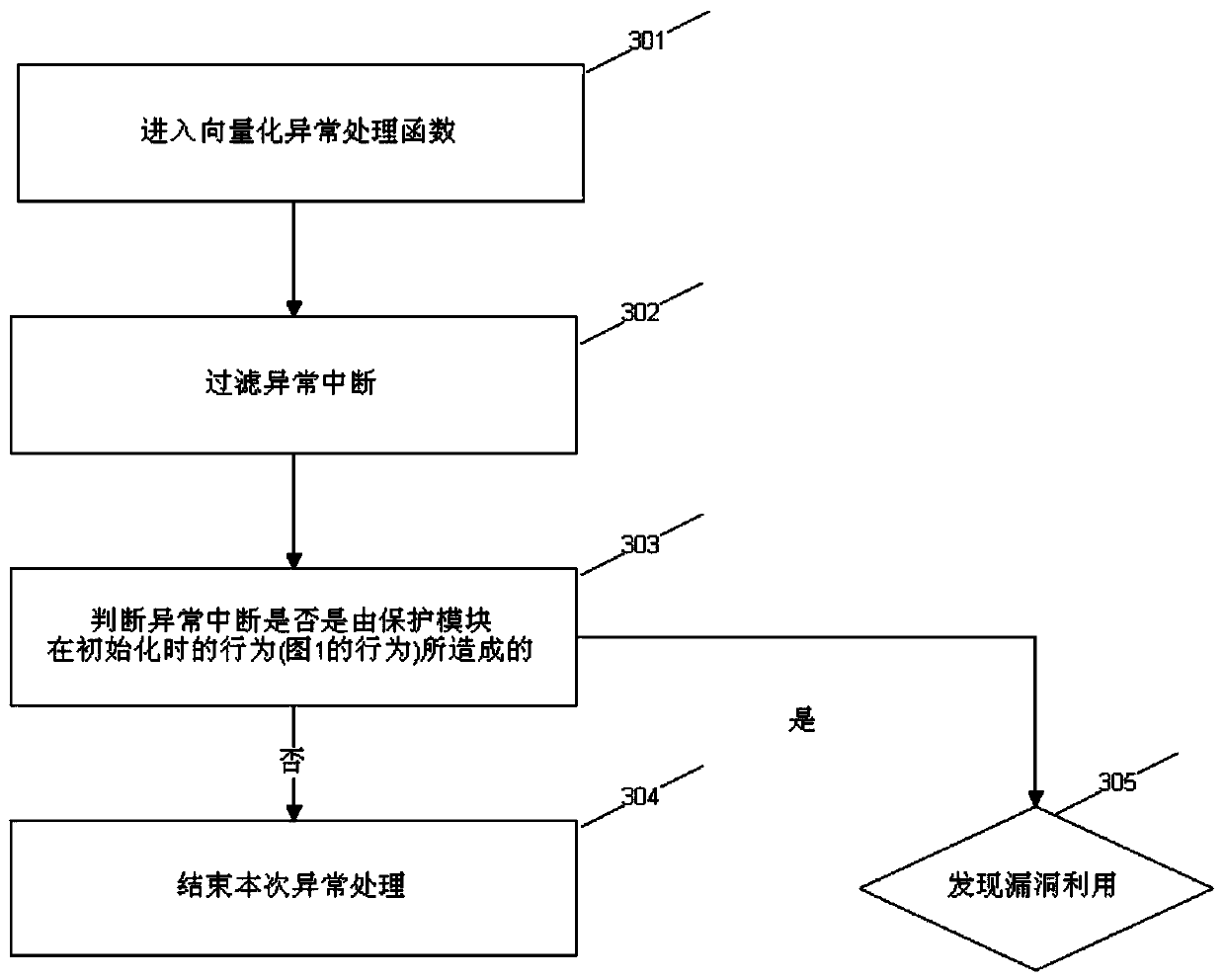
[0051] In order to solve the shortcomings of the loophole utilization detection scheme provided by the prior art, that is, the problems of inability to detect unknown type loopholes, poor compatibility, and small coverage area, the method of the present invention provides a loophole utilization detection and identification scheme. The target process, arranges the memory to the ideal state of defense, monitors the behavior of the target process and conducts dynamic analysis to identify the attack methods of vulnerability exploitation, not limited to known exploits, and has the effect of protecting the process and system environment.
[0052] In order to make the purpose of the method of the present invention and the technical solution more clear, further detailed description will be given below in conjunction with the accompanying drawings.
[0053] see figure 1 , is a schematic diagram of the loophole utilization detection and identification process of the method of the presen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com