Fast security hardware structure of AES algorithm
A hardware structure, fast technology, applied in the field of information security, to achieve the effect of high side channel security and optimized efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
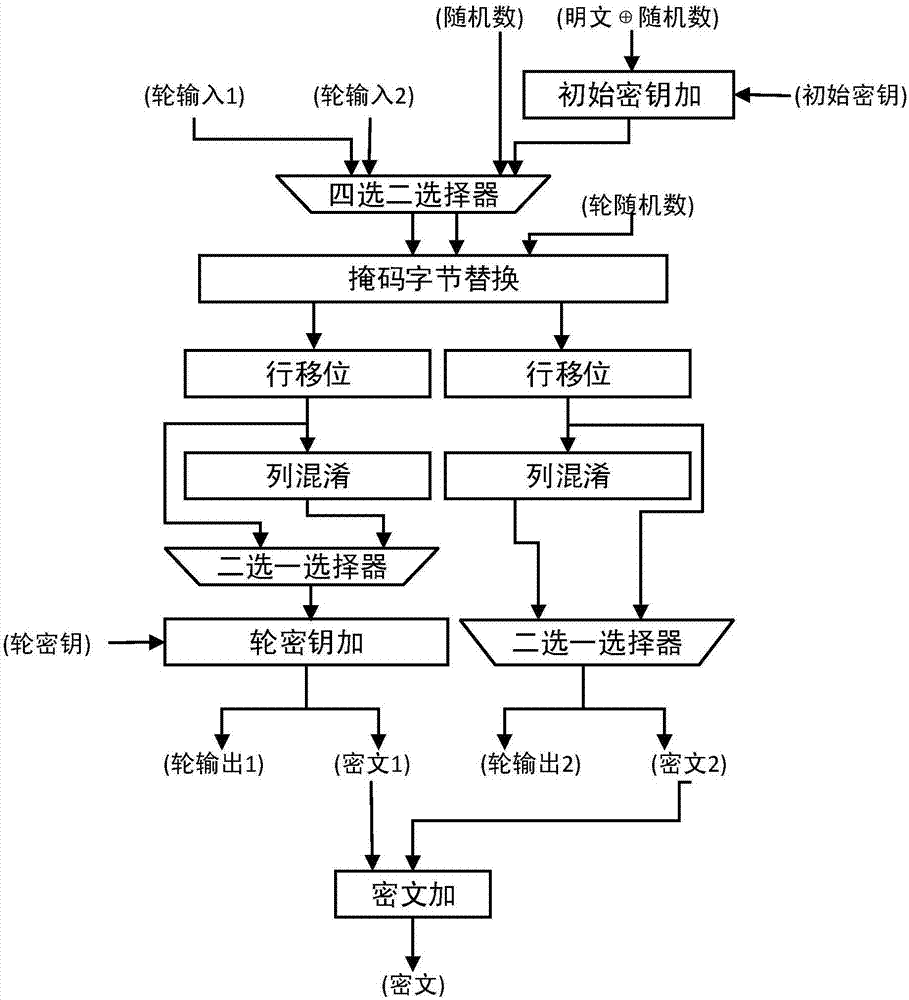
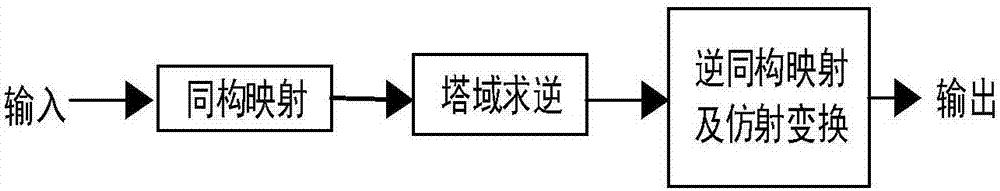
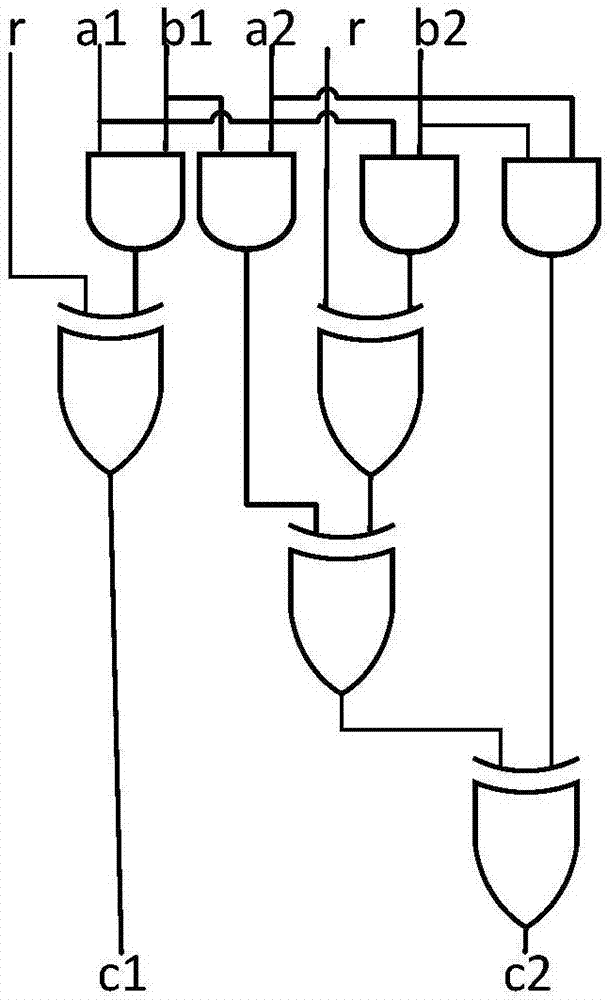
[0053] The specific technology of the present invention, especially the S-box solution of the mask byte replacement part of the core part will be further described in detail below in conjunction with the accompanying drawings. The S-box solution process of AES is as follows: figure 2 As shown, starting from the input, it includes isomorphic mapping, tower field inversion, inverse isomorphic mapping, affine transformation and output process. In the process of inverting the tower field, the image 3 , Figure 4 and Figure 5 Mask implementation of AND gate, OR gate or NOT gate in . for image 3 The implementation of the symbol AND Masked Gate is abbreviated as (&M), for Figure 4 Use the symbol XOR Masked Gate to express the abbreviation as (∪M), for Figure 5 It is abbreviated as (!M) with the symbol NOT Masked Gate.
[0054] 1. Isomorphic mapping
[0055] The isomorphic map f is a matrix transformation of 8 rows and 8 columns. It does not contain nonlinear AND gates, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com