Object data association index system, system construction method and system application method
A technology of associating index and object data, applied in the computer field, can solve the problems of high technical threshold of big data, lack of data, weak data security, etc., to save data storage space and improve reliability.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment 1
[0287] Specific embodiment 1, EDI electronic data interchange application
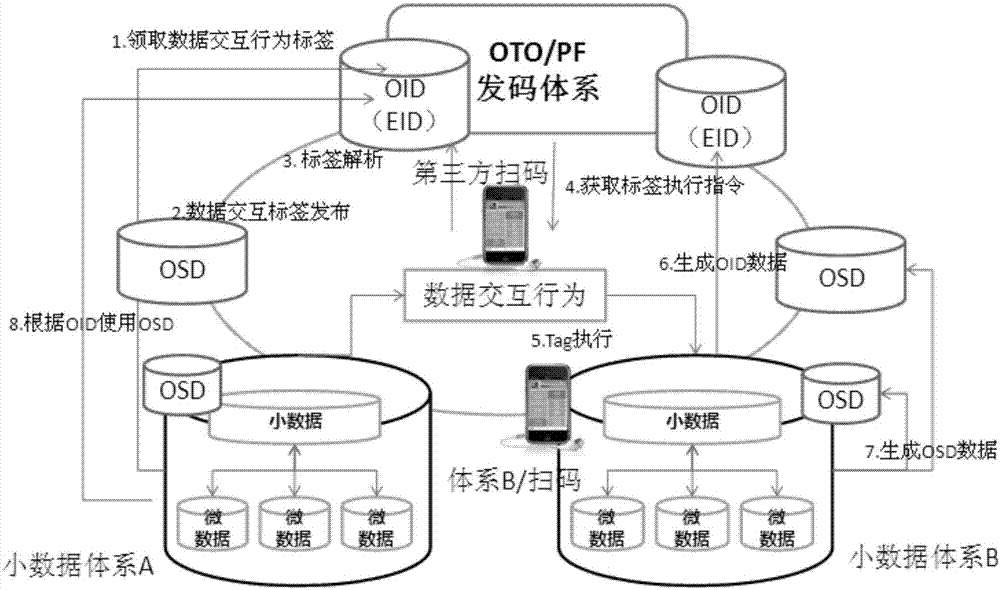
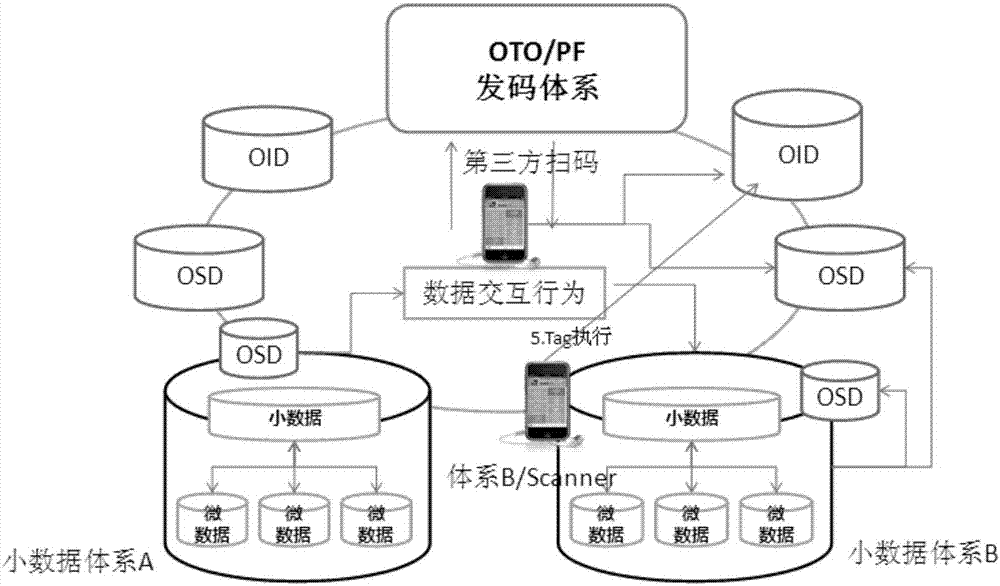
[0288] Master: Utilizing the ID management of OTO can standardize the common master table data during EDI data transmission, making the analysis of EDI data easier, reducing the extra burden of inter-system I / F due to format conversion, and improving processing efficiency.
[0289] Querying and Analyze (queuing and analysis): Through OTO's small data decentralized processing, cross-platform and cross-system EDI data interaction can be constructed to avoid complicated data synchronization and interfaces caused by data redundancy. Case: The personal credit system needs to be connected to various unrelated databases such as personal data, criminal records, and bank credit. It is implemented in the traditional EDI method, and it needs to be implemented separately with each database, or even a database system that is scattered due to geographical or administrative reasons. EDI data interface, and in the OTO...
specific Embodiment 2
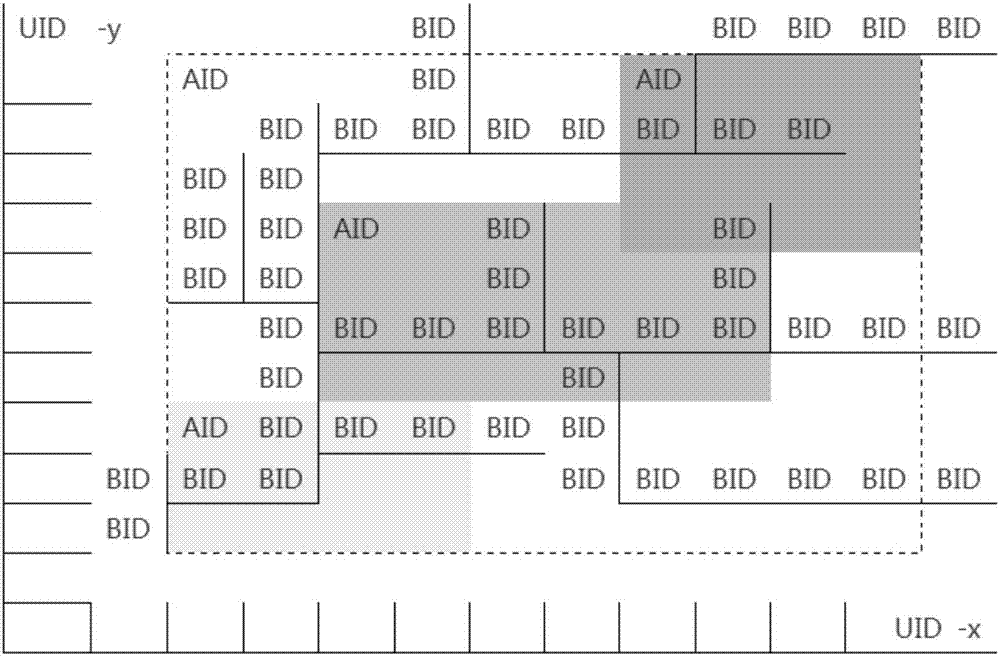
[0311] Specific embodiment 2, use the block chain of OID (object data association index) to carry out market promotion analysis
[0312]In the current O2O environment, it is difficult to analyze the marketing of products. Because each e-commerce / social SNS and offline media platforms are independent, it is impossible to integrate and analyze the promotion information of each platform to the effective promotion data information for final consumers to purchase goods / services. This type of data analysis can often only be done through the collection of huge / massive amounts of relevant data information (most of which have illegal / unauthorized information acquisition), and then analyzed through mathematical formulas, so the final analysis data It is estimated rather than precise.
[0313] And under the OTO environment utilizing the present invention, through the OID (object data association index) of OTO platform, carry out accurate analysis to the marketing promotion of commodity....
specific Embodiment 3
[0319] Specific embodiment 3, electronic / virtual currency transaction
[0320] In recent years, electronic / virtual currency transactions have rapidly emerged in the field of mobile Internet. Virtual currency is a "currency" defined by the developer that is applicable in a specific application, and users can use it to purchase game levels, props, advanced functions or content, etc. within the application. Setting virtual currency and consumption mechanism in the application can promote users to participate in in-app purchases, enhance application stickiness, and increase developers' income.
[0321] In the process of virtual currency transactions, developers focus on providing users with various virtual items or services.
[0322] At present, most of the virtual currency transactions in reality adopt the virtual currency transaction method of third-party arbitration. The transaction of electronic currency, such as Bitcoin, adopts the method of multi-point authentication, that ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com