Cloud and local combined data processing method and device
A data processing and data technology, applied in the field of data security, can solve the problems of lack of mass data and big data analysis technology support, passive business work, single detection and discovery means, etc., to reduce system management and maintenance costs and high coverage , Data collection comprehensive effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0062] The specific embodiments of the present invention will be further described below in conjunction with the accompanying drawings. The following examples are only used to illustrate the technical solution of the present invention more clearly, but not to limit the protection scope of the present invention.
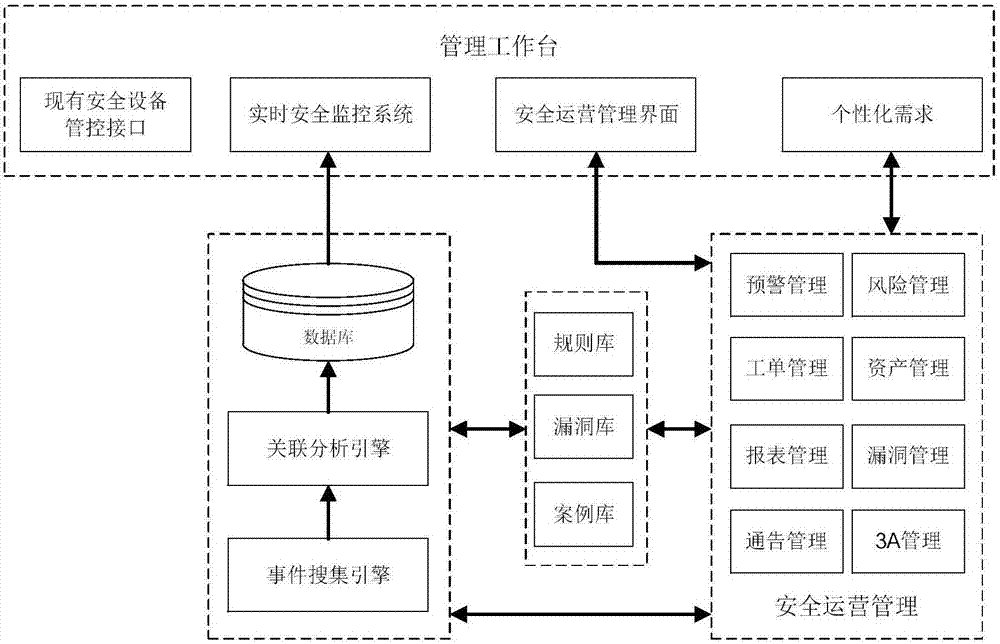
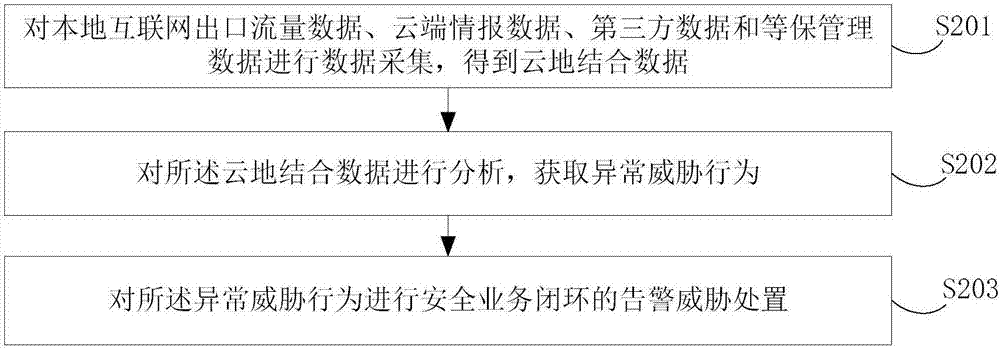
[0063] figure 1 It shows a schematic flowchart of a cloud-local data processing method provided in this embodiment, including:
[0064] S101. Collect data from local Internet egress traffic data, cloud intelligence data, third-party data, and security management data to obtain cloud-local combination data;
[0065] Wherein, the local Internet egress traffic data is local data, and the cloud intelligence data is cloud data.
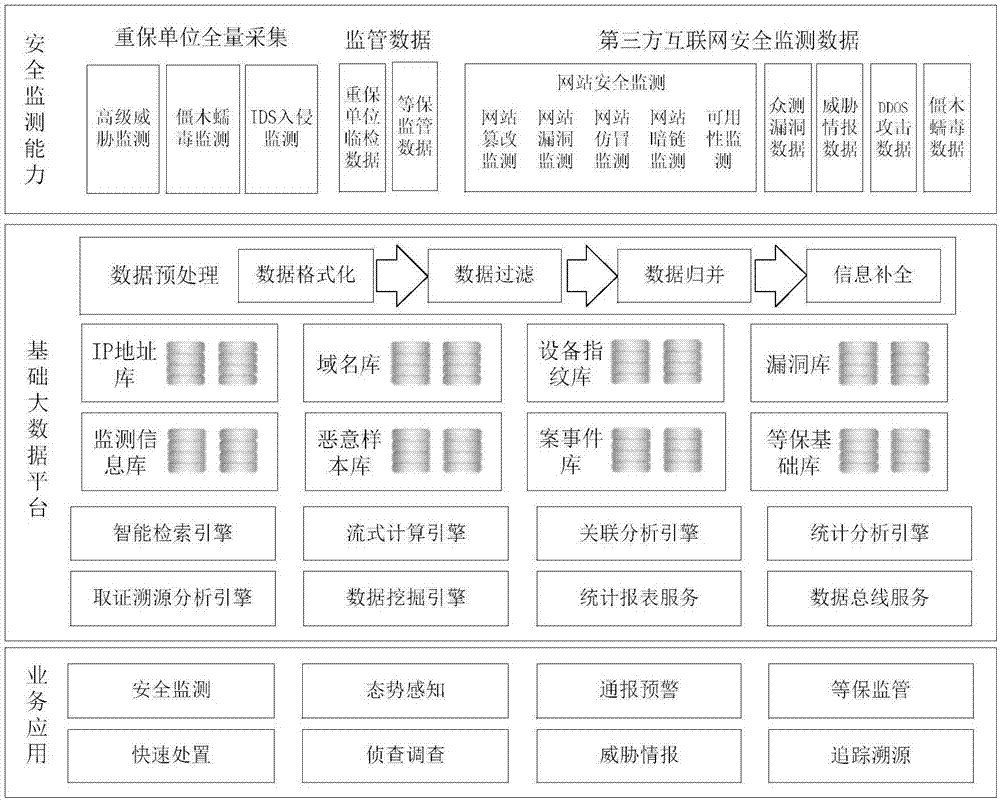
[0066] The local Internet egress traffic data includes zombie and worm attack data of the key protection unit and / or network full flow restoration logs of the key protection unit.
[0067] For advanced threats, such as APT attacks, this solutio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com