Fragile code clone detection method and device based on vulnerability fingerprint
A detection method and vulnerability technology, which is applied in the field of vulnerable code clone detection based on vulnerability fingerprints, can solve the problems of low detection efficiency and high false negative rate, and achieve high detection efficiency, low false positive rate, and wide detection applicability Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0048] In order to make the purpose, technical solution and advantages of the present invention more clear and understandable, the present invention will be further described in detail below in conjunction with the accompanying drawings and technical solutions.
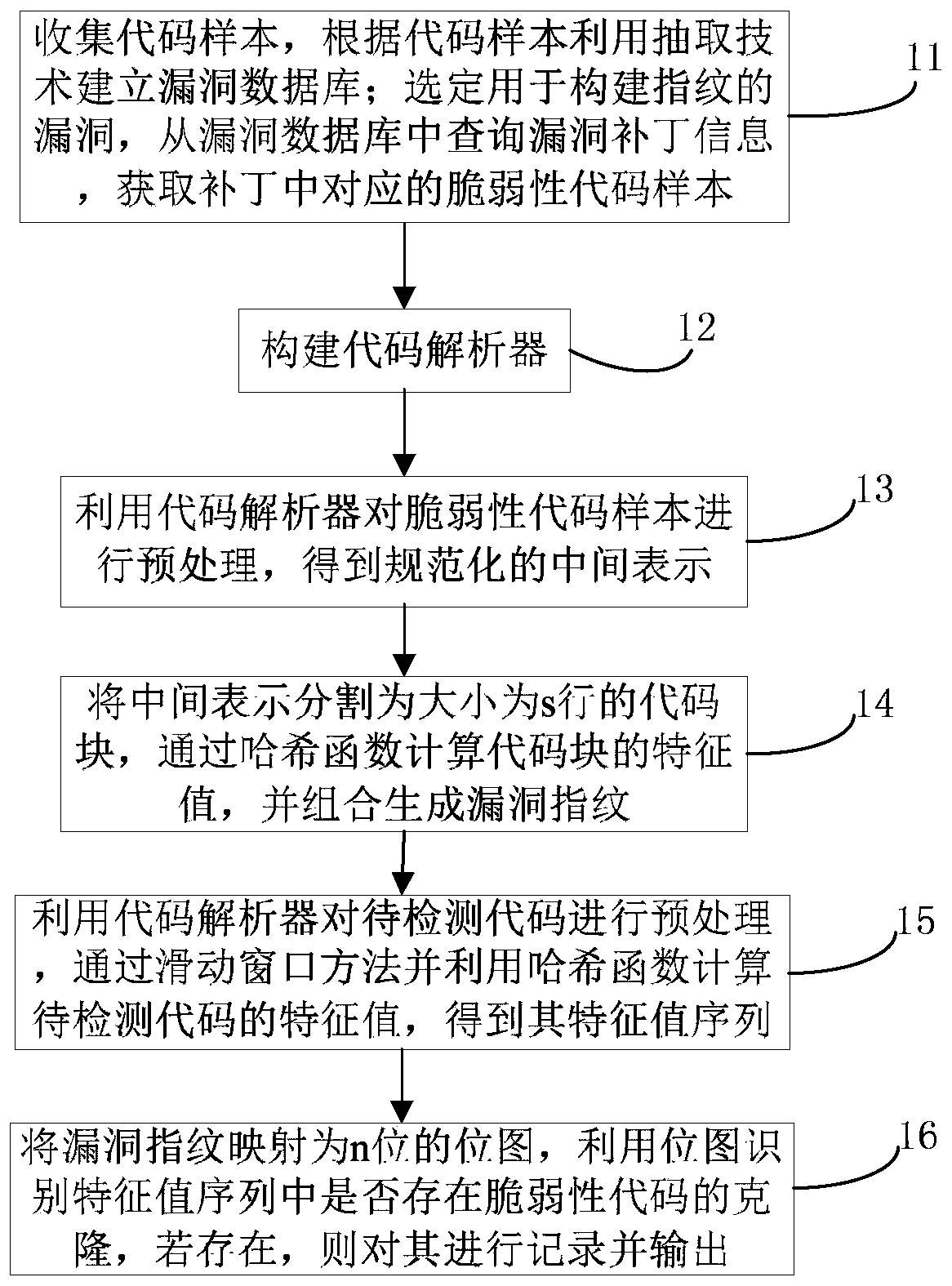
[0049] Vulnerable codes refer to key codes that lead to software vulnerabilities, and cloning of vulnerable codes may introduce the same vulnerabilities during the development process. In order to solve the existing problems such as weak ability to deal with code modification and low detection efficiency in the process of detecting vulnerable code clones, this embodiment provides a vulnerable code clone detection method based on vulnerability fingerprints, see figure 1 shown, including the following steps:
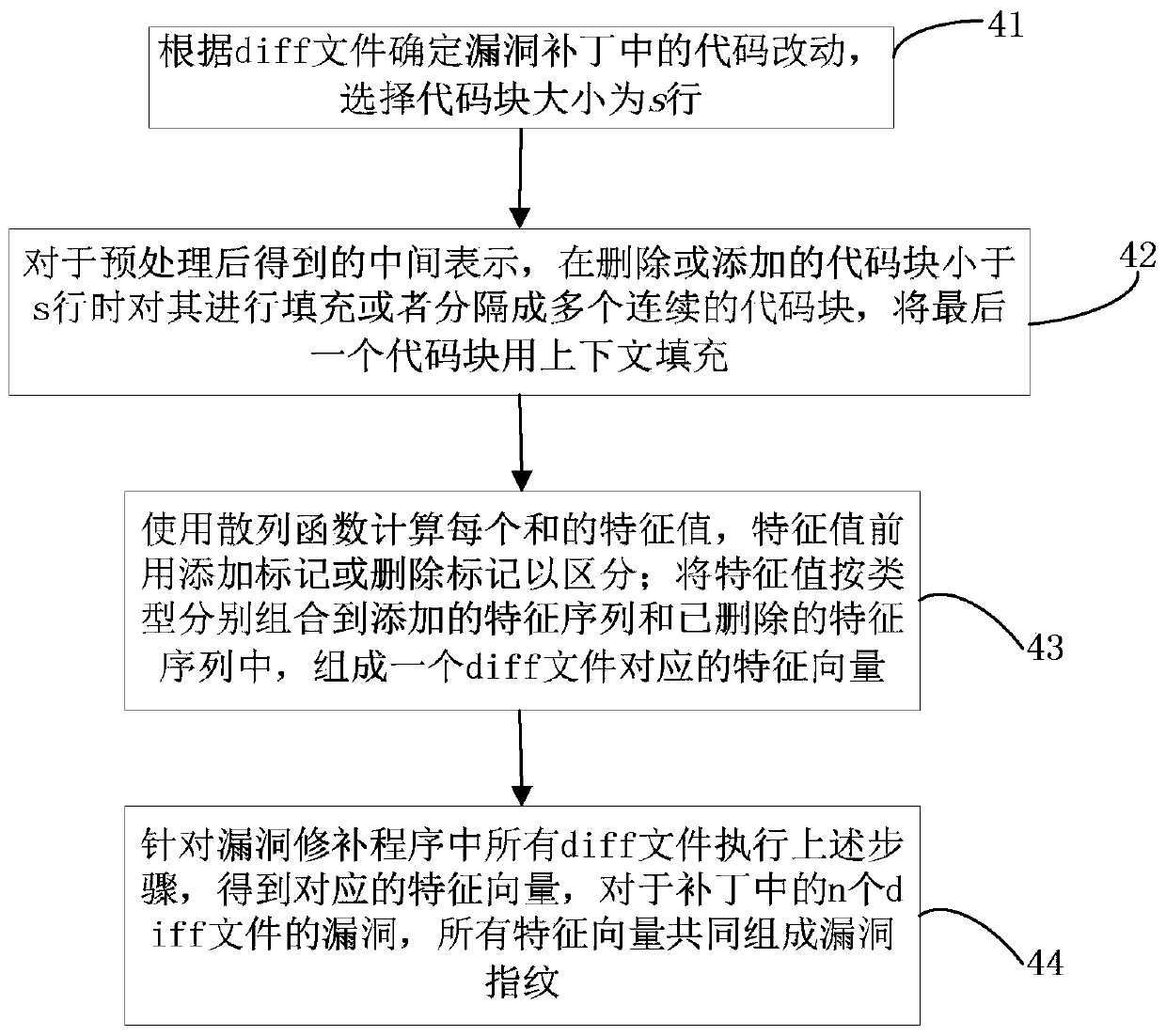
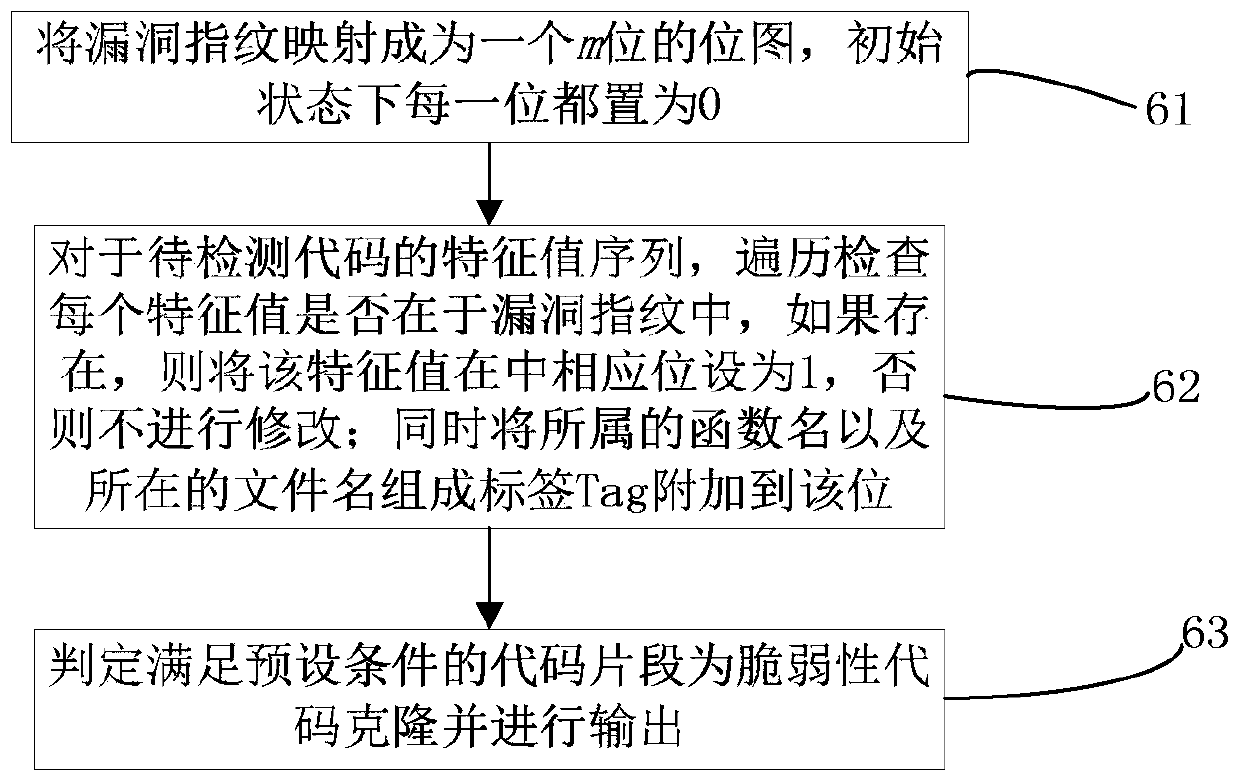
[0050] Step 11. Select the vulnerability v used to construct the fingerprint, query the vulnerability patch information from the public vulnerability information database, and obtain the corresponding vulnerable c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com