Flood attack detection method capable of accurately determining attack features
A flood attack and attack feature technology, applied to electrical components, transmission systems, etc., can solve problems such as normal business impact and high misjudgment rate, and achieve the effects of ensuring stability, reducing misjudgment, and improving performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
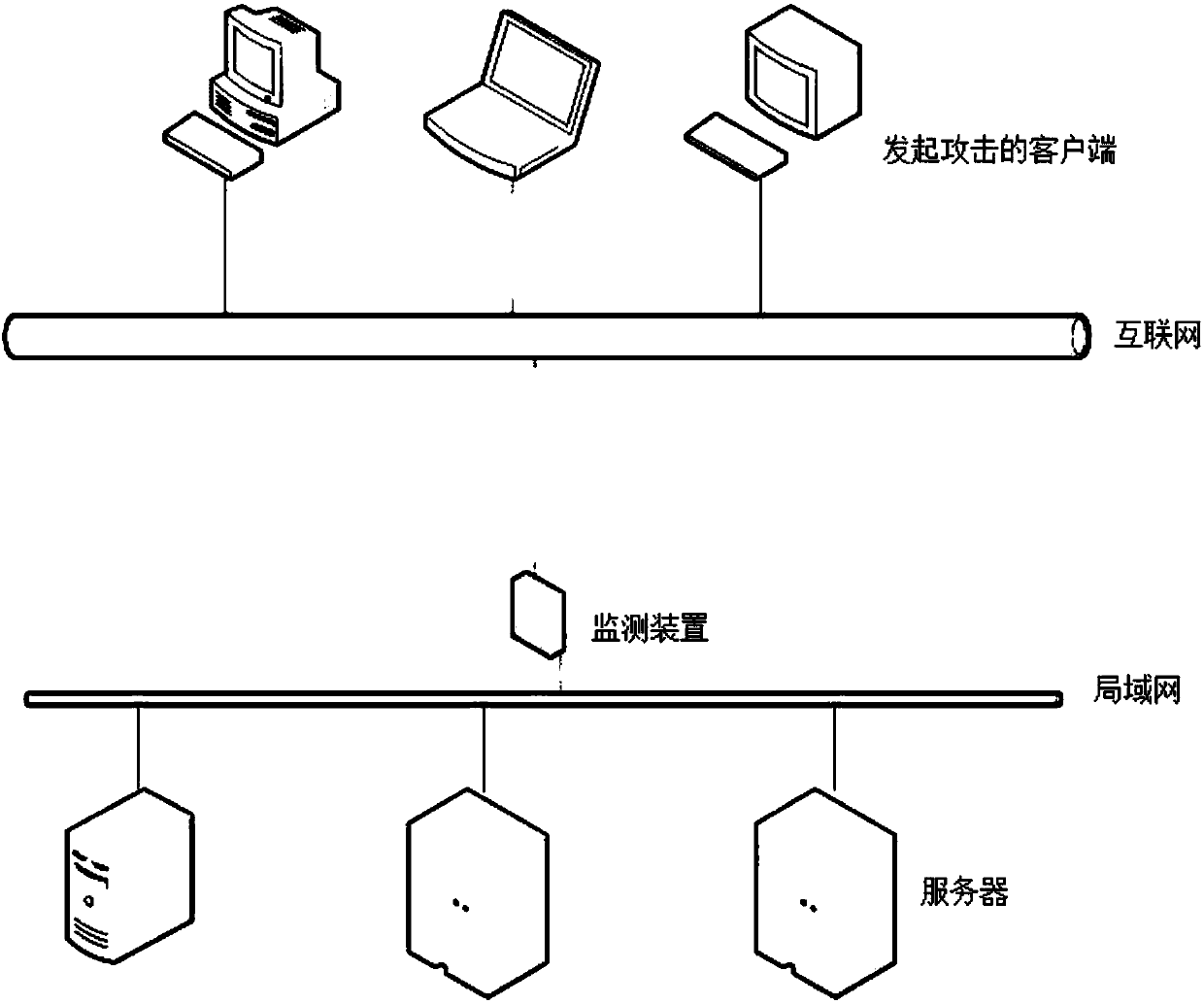
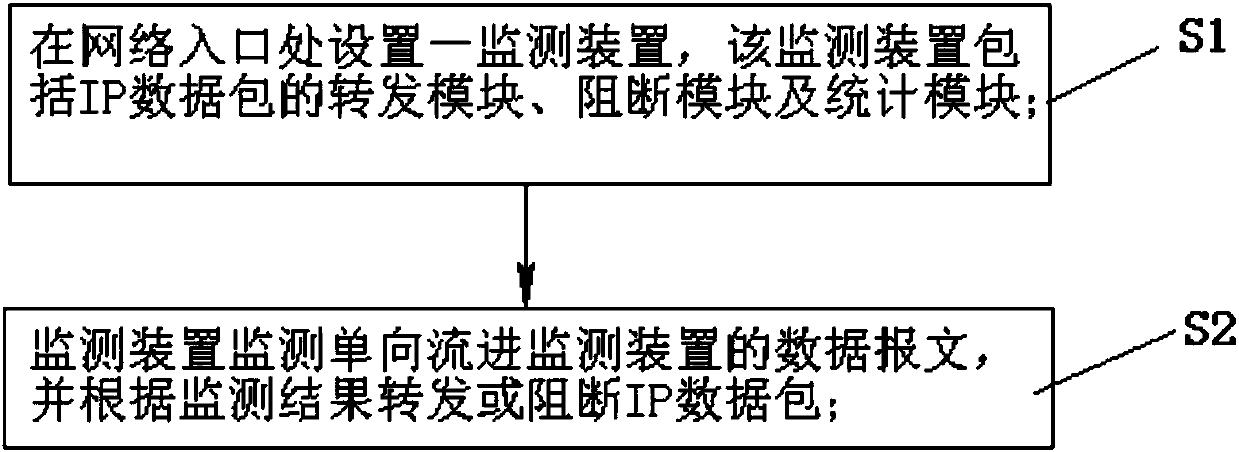
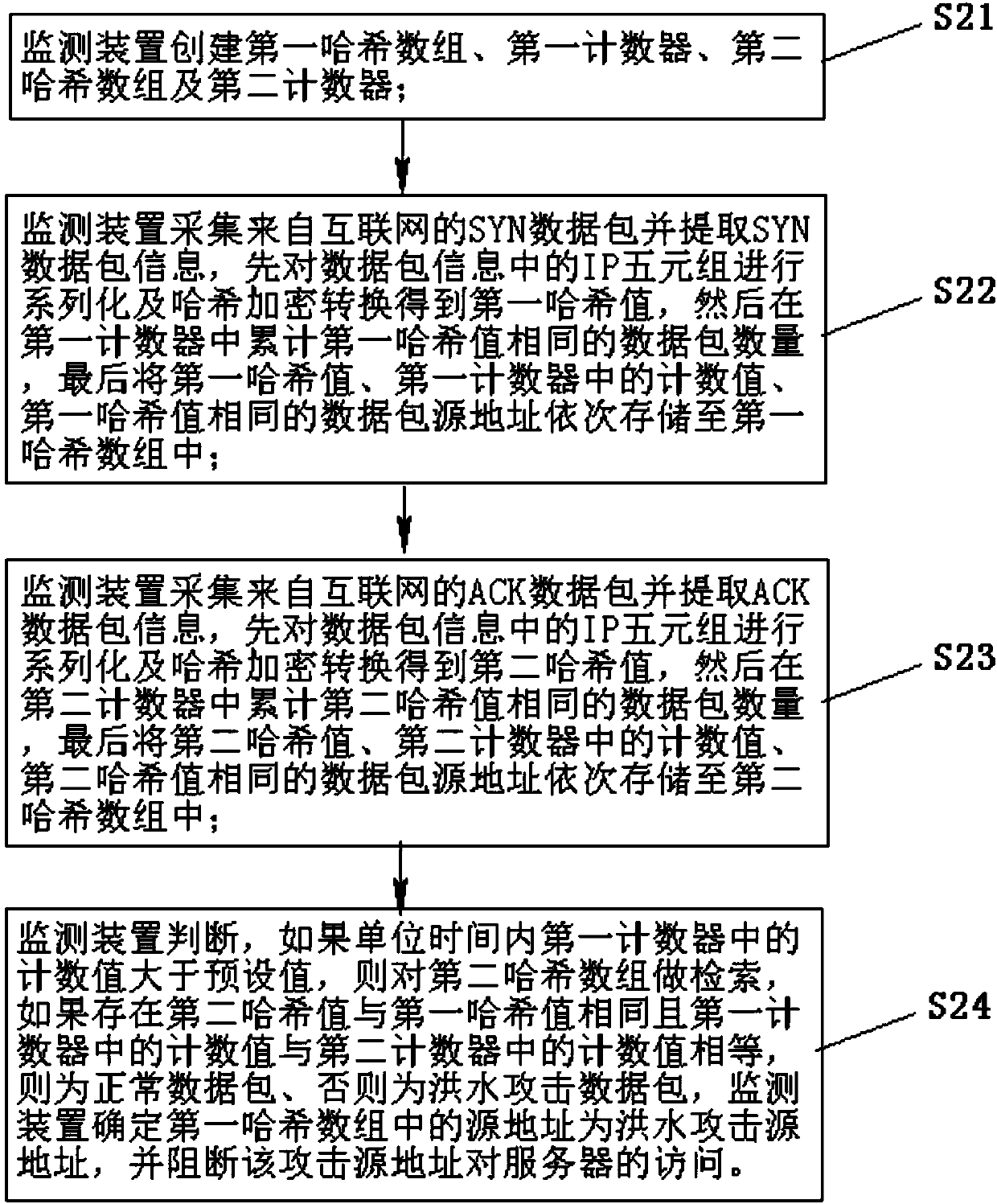
[0020] Please also see Figure 1 to Figure 3 , figure 1 is a schematic diagram of the network topology deployed by the monitoring device in the present invention, figure 2 is a flowchart of the present invention, image 3 yes figure 2 The flowchart of step S2 in.
[0021] See figure 1 and figure 2 , a flood attack detection method for accurately determining attack characteristics, comprising the following steps:
[0022] S1: Set up a monitoring device at the entrance of the network. The monitoring device includes a forwarding module, a blocking module, and a statistical module for IP data packets. The data packet blocking and statistics module at the terminal monitors and counts various data packets entering the monitoring device;
[0023] S2: the monitoring device monitors the data message of the unidirectional flow into the monitoring device, and forwards or blocks the IP packet according to the monitoring result, and this step S2 includes the following steps (see ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com