Distributed event collection probe, distributed event high-speed collection system and method
A technology for event collection and high-speed collection, which is applied in the field of network data and can solve the problems of data security hazards, log data collection and analysis solutions unable to meet requirements, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
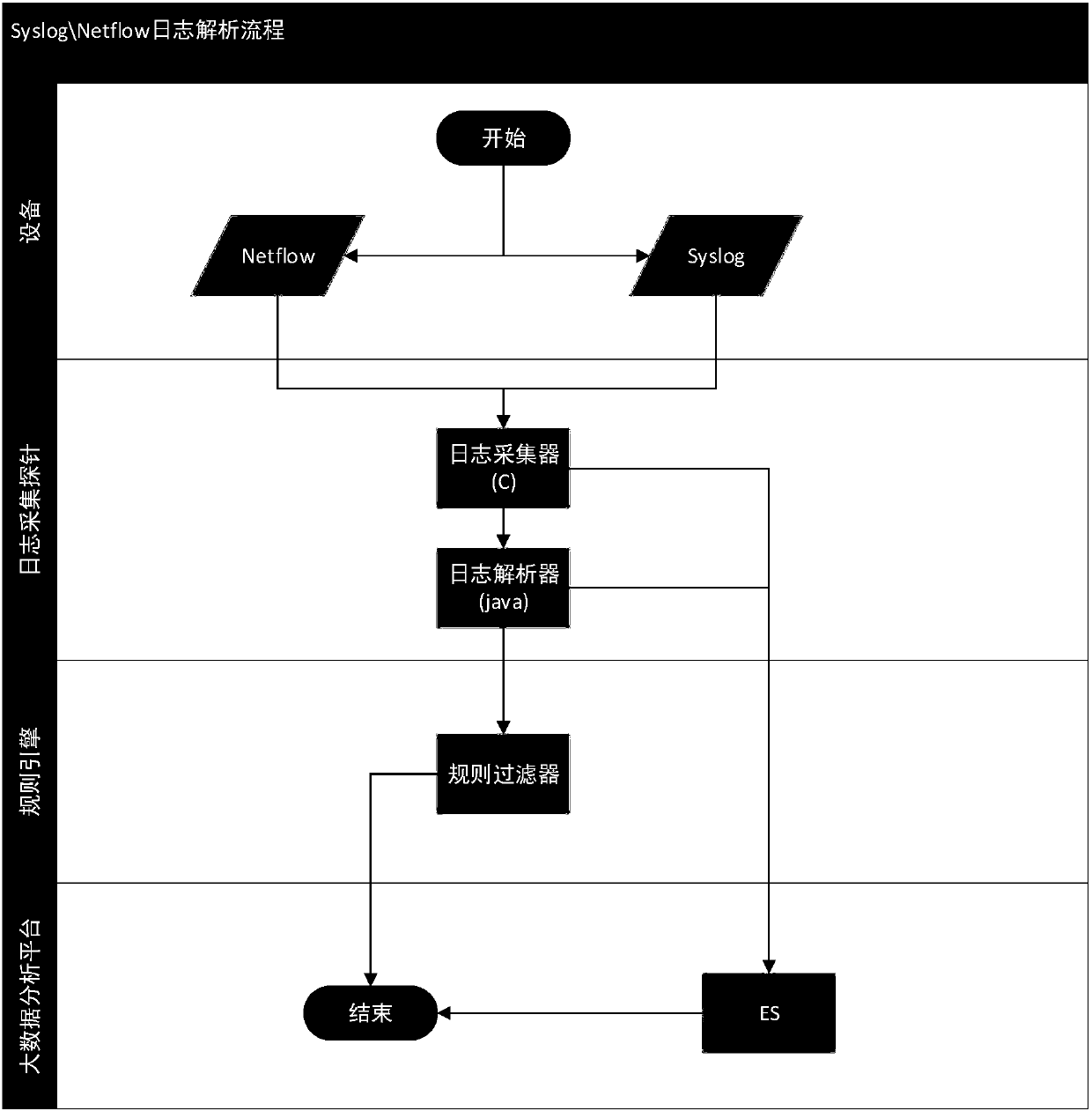
[0059] This example implements the collection of received Syslog and Netflow logs.
[0060] For most devices and Linux and Unix systems, you can configure to record logs of a specified type and level, and specify a server to receive the logs, so that the logs are sent to the server that receives the logs through the Syslog protocol. When deploying this example, the address of the server that receives the logs is set to the address of the event collection probe of the auditing and tracing platform, thereby realizing forwarding the logs to the event collecting probe of the auditing and tracing platform.
[0061] Accordingly, the types of device forwarding logs that this instance can receive include Syslog logs and Netflow logs. The log receiver is written in C language, and it is mainly responsible for receiving and forwarding logs.
[0062] see figure 1 , which shows the flow chart of receiving Syslog and Netflow logs in this example. As can be seen from the figure, the proc...
example 2
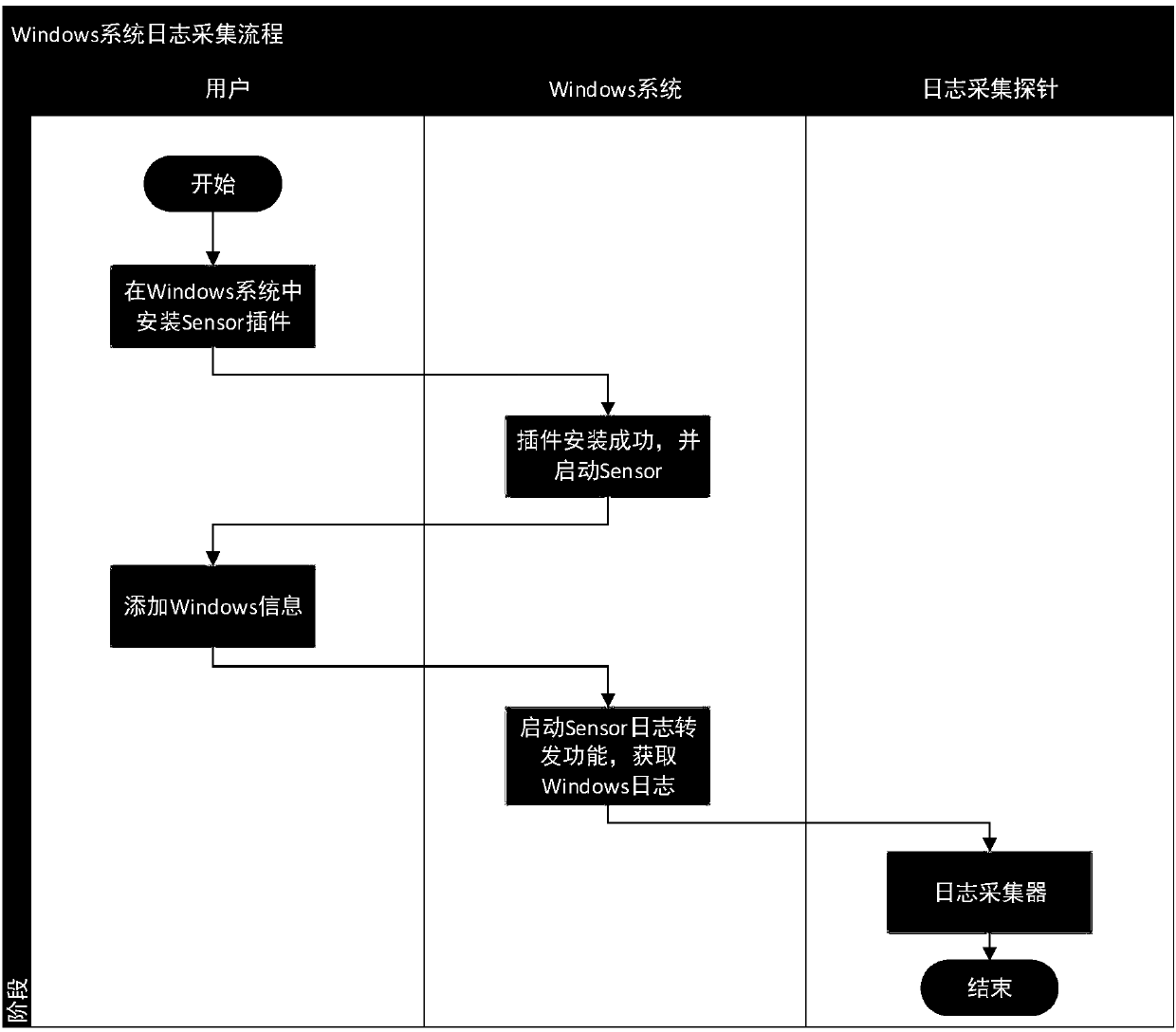
[0068] This example implements obtaining Windows host logs through the WMI service.
[0069] The Windows system itself does not support log forwarding. To obtain Windows log information, you usually use a plug-in installed on the Windows system to forward or open the Windows system WMI service, and obtain it by calling the corresponding interface of the WMI service. The event collection probe supports obtaining Windows logs through the WMI service of the Windows system. When configuring, you need to enable the Windows WMI service and provide the necessary access rights for the collection probe.
[0070] To collect Windows system logs, you need to install the Sensor plug-in; the plug-in obtains logs through the WMI service interface and forwards the logs to the log collector.
[0071] see figure 2 , which shows the flow chart of Windows system log collection in this example. As can be seen from the figure, the process of collecting Windows system logs in this example is as f...
example 3
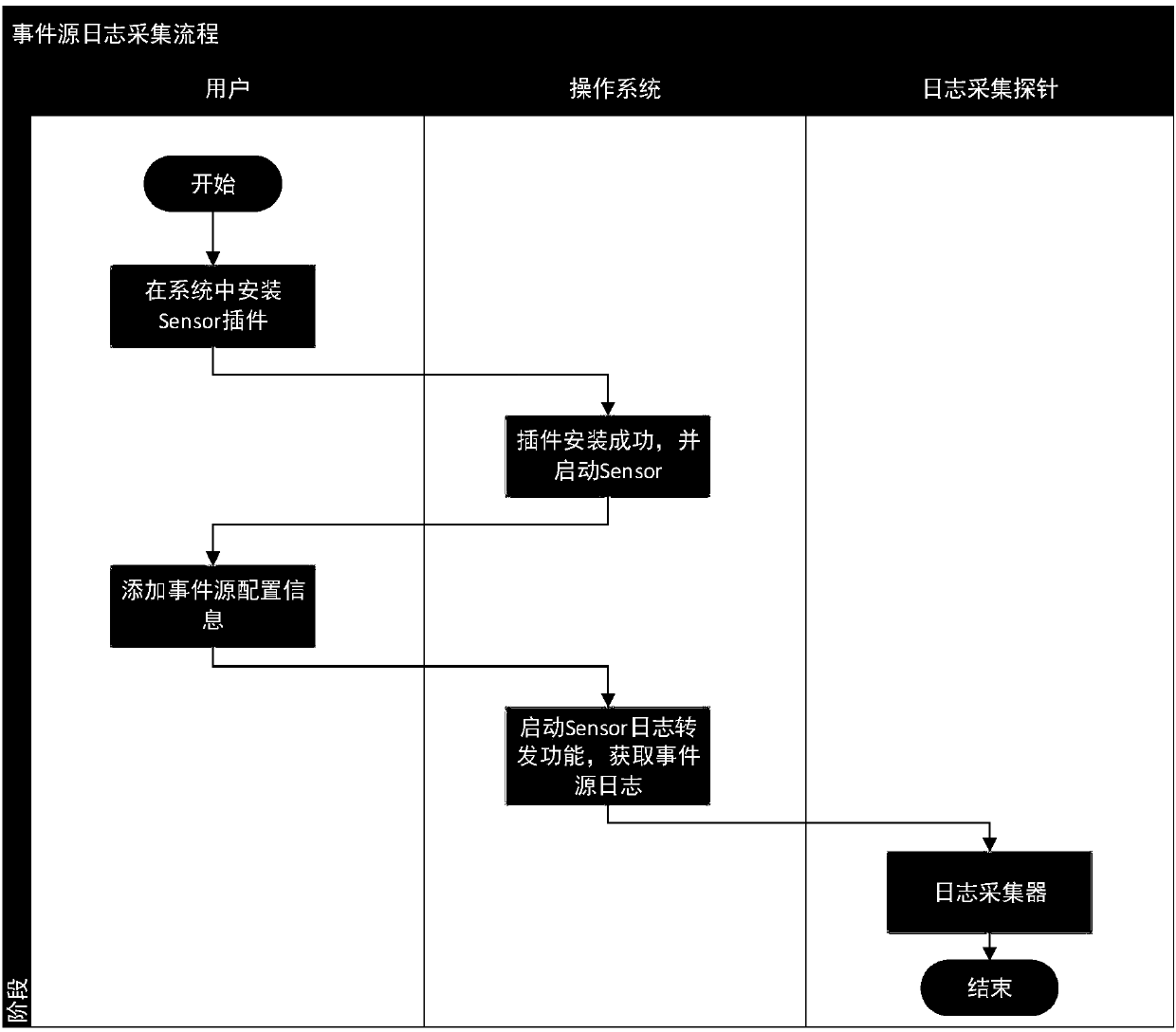
[0079]This example realizes reading the local log file of the event source.
[0080] In this example, some devices or systems do not support log forwarding, but save logs in local log files, and may set a policy to use these files in rotation. The plug-in needs to be installed in the device where the event source is located. The plug-in polls the log file regularly, and judges the new log by timestamp or event ID (depending on the event source device or system implementation method), and reads the new log through Syslog The protocol is forwarded to the event collection probe.
[0081] In this case, when this instance reads the local log files of the event source, the Sensor plug-in needs to be installed; the plug-in forwards the log files of the event source to the log collector by configuring the event source information.
[0082] The event source monitoring here supports event source directory monitoring and event source log file monitoring; in directory monitoring, you nee...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com