Secure cloud storage system
A cloud storage system and security technology, applied in the field of network security, can solve problems such as poor cloud storage security, and achieve the effects of reduced workload, complete coverage and high security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
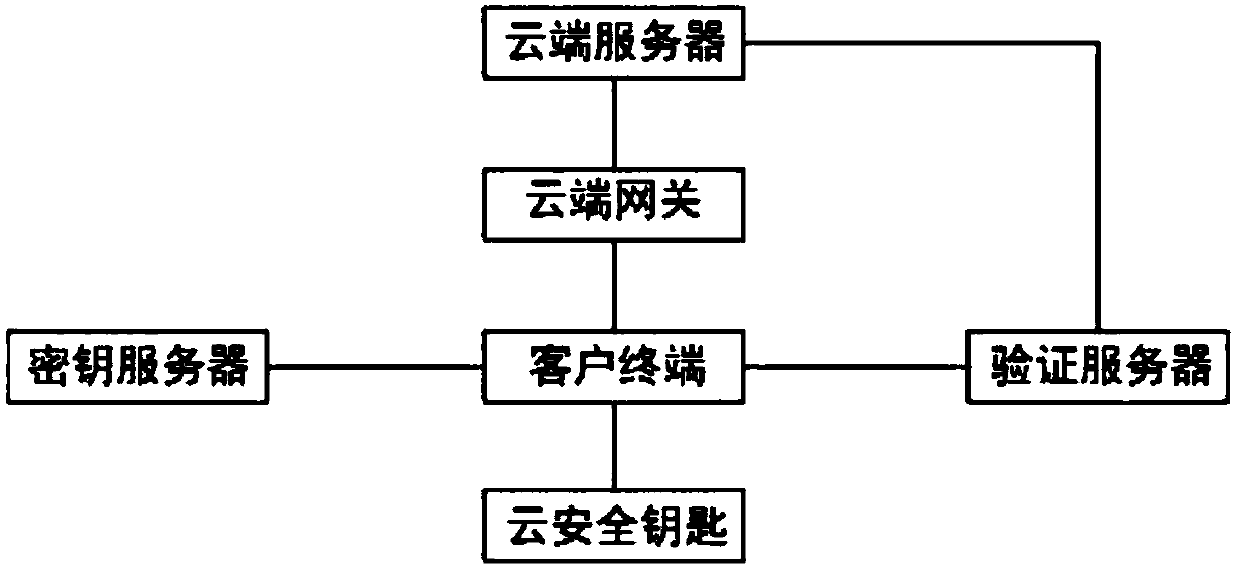
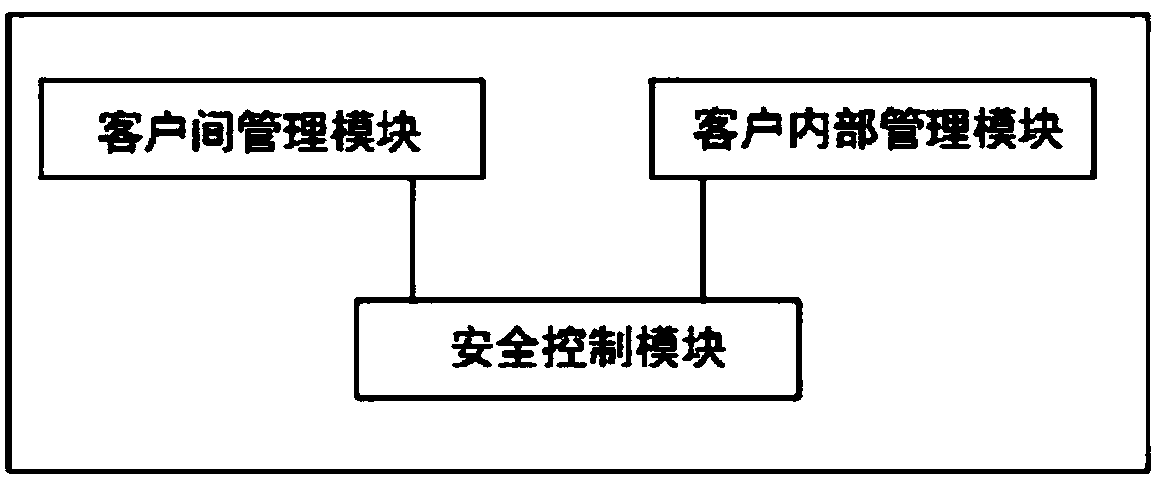
[0026] see Figure 1~2 , the secure cloud storage system includes a cloud server, a cloud gateway, a client terminal, and a verification server. The client terminal connects to the cloud server through the cloud gateway, and the verification server is respectively connected to the client terminal and the cloud server. Integrity of files in the server; the cloud gateway is equipped with an inter-client management module, an internal client management module, and a security control module. The inter-client security management module receives the security policy management commands of the cloud server and stores the policy management results in the inter-client security In the isolation policy, the customer internal management module receives security policy management commands from the customer, and stores the policy management results in the customer internal security policy, and the security control module authenticates the login user according to the security isolation policy ...
Embodiment 2
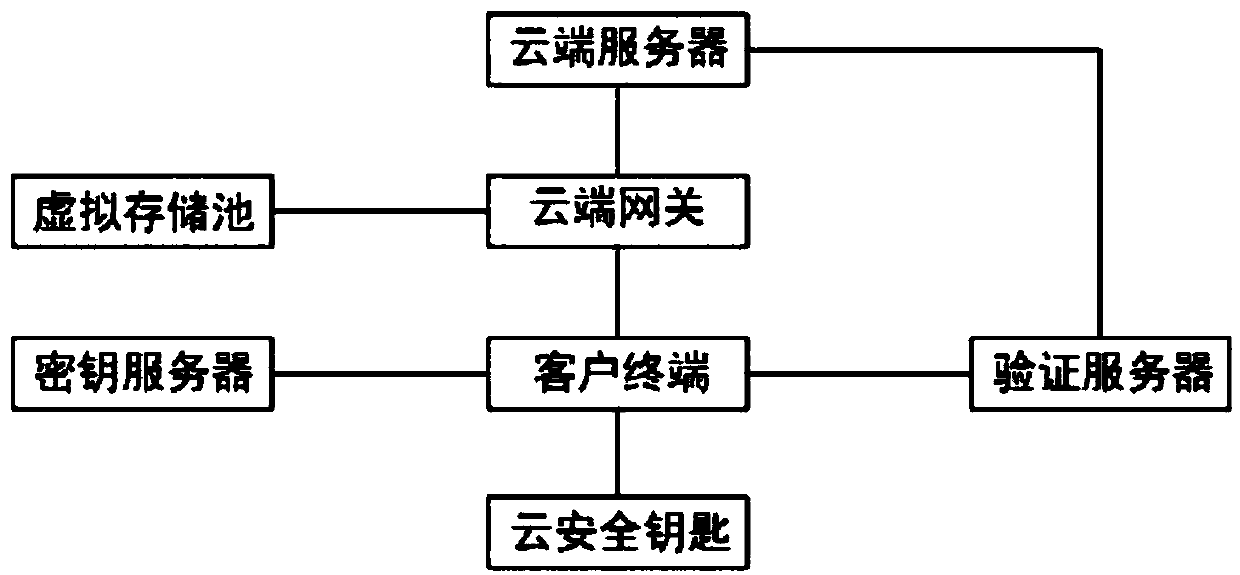
[0030] see Figure 3-4 , the cloud storage system also includes a virtual storage pool, which is connected to the cloud gateway; the cloud gateway also has a frequency evaluation module and a backup module, the frequency evaluation module is used to evaluate the access frequency of files in the virtual storage pool, and the backup module will access Infrequent files are backed up to cloud servers. The present invention decides whether to store the files on the cloud server by judging the access frequency of the files, thereby reducing the cost of hardware storage, and at the same time frequently used files are stored in the local virtual storage pool, which has higher security.
[0031] There is also an update module in the cloud gateway, which is used to update the status of the backed-up data to be transferred when the backup module backs up the data whose temperature is cold. After the backed-up data is backed up to the cloud server, the update is The status of the backup ...
Embodiment 3
[0033] see Figure 5 , the cloud gateway also has an attack judgment module and an attack analysis module, the attack judgment module is used to judge the type of attack scene; the attack judgment module judges the type of attack scene includes:
[0034] Identify whether the attack feature is a multi-step attack feature or a single-step attack feature;
[0035] When the attack feature is identified as a single-step attack feature, it is judged that the type of attack scenario is a simple attack process;
[0036] When the attack feature is identified as a multi-step attack feature, it is judged that the type of attack scenario is a complex attack process;
[0037] The attack analysis module is used to analyze the security event flow by using a character string matching-based model when it is determined that the type of the attack scene is a simple attack process. The analysis module uses a model based on string matching to analyze security event streams, including:
[0038] ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com