3D texture model encryption method based on chaotic mapping
A technology of texture model and encryption method, which is applied in the field of information security cryptography, can solve problems such as not suitable for 3D content, and achieve the effect of simple and reliable method, easy implementation, and simple structure
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0039] The present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
[0040] The logistics chaotic map is described by formula (1):
[0041]
[0042] Among them, μ∈[0,4] is called the Logistic parameter. When the value of μ meets the condition of 3.56994560 The initial value obeys the formula (1), the chaotic map x n The output of will appear chaotic and suitable for generating random sequences.
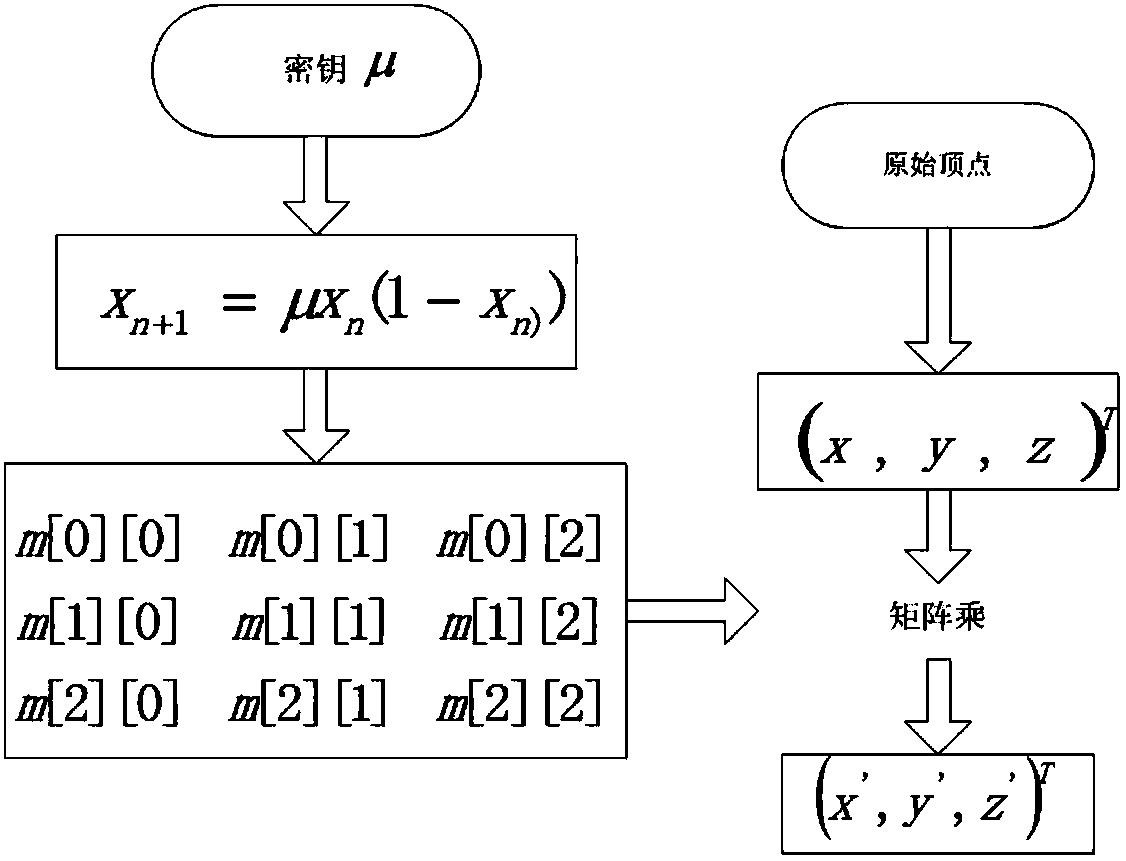
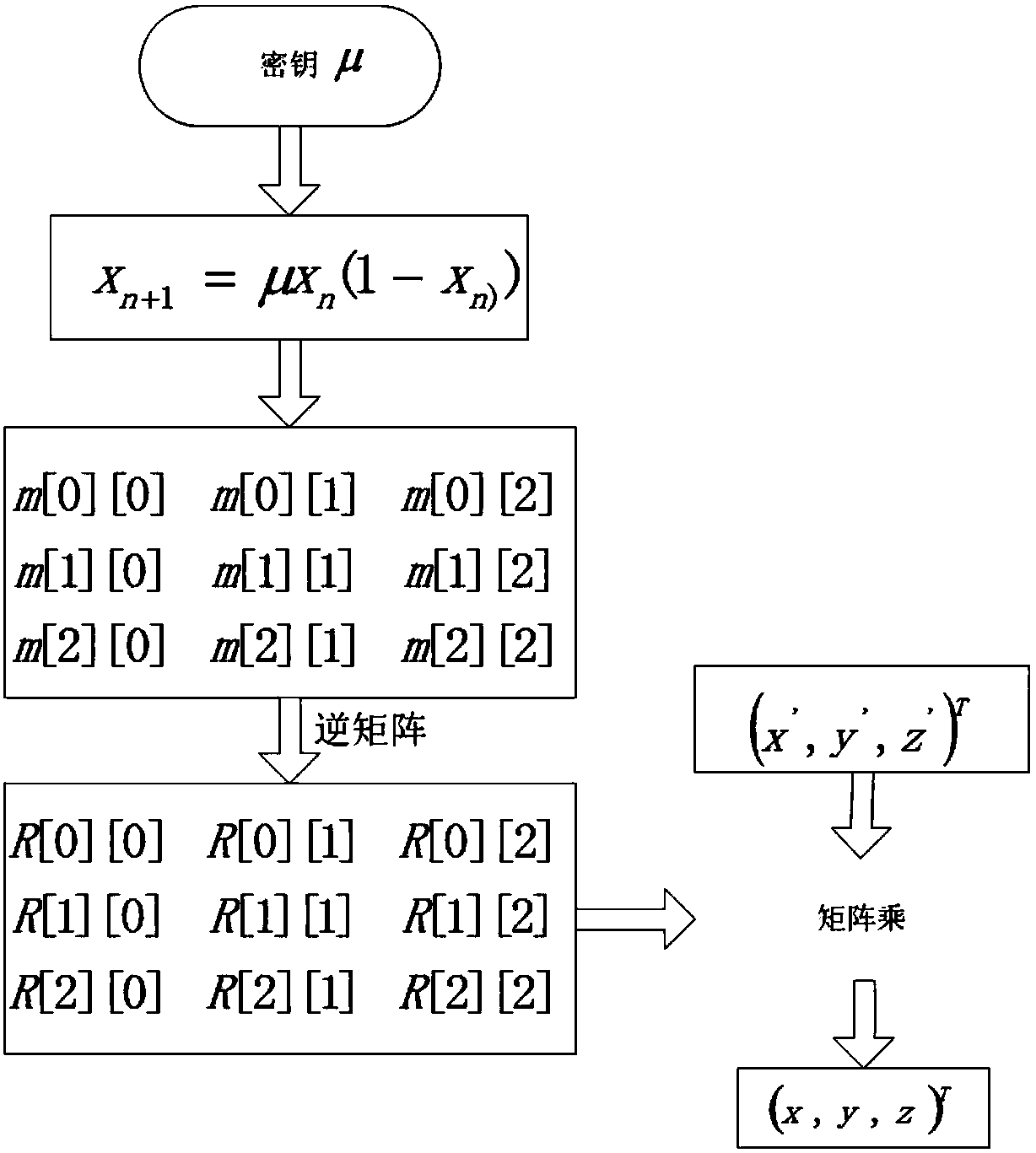
[0043] refer to figure 1 Vertex encryption flow chart, the vertex encryption process of the present invention can be divided into the following three steps:
[0044] (1) Key generation
[0045] The initial value x of the Logistic chaotic map 0 And the parameter μ is used as the key to generate a pseudo-random number sequence corresponding to the midpoint of the texture model.
[0046] (2) Generation of reversible matrix
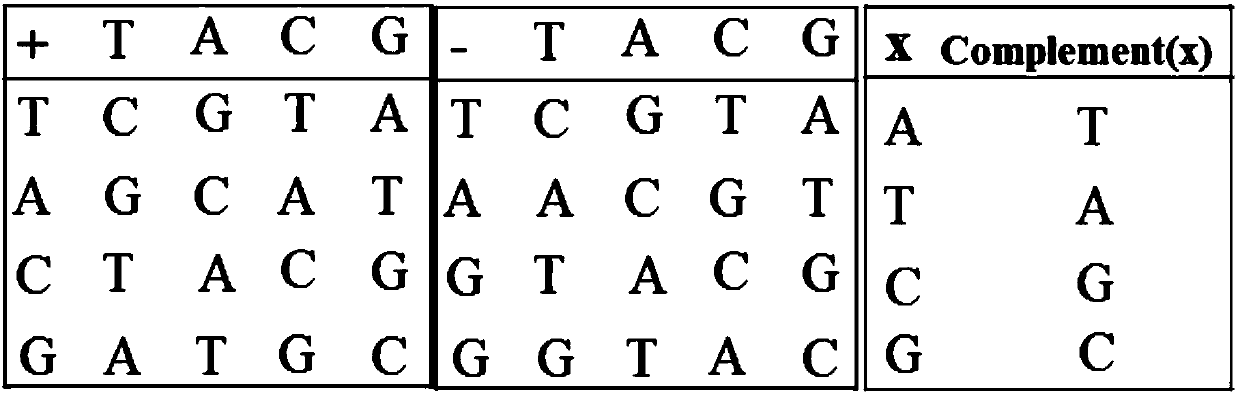
[0047] The 1st to 6th digits in the sequence generated by the previous step, nam...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com