Efficient message transmission and authentication method based on mobile vehicle ad hoc network
A vehicle self-organizing network and authentication method technology, which is applied to services based on a specific environment, communication between vehicles and infrastructure, vehicle components, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0059] The technical solutions in the embodiments of the present invention will be described clearly and in detail below with reference to the drawings in the embodiments of the present invention. The described embodiments are only some of the embodiments of the invention.
[0060] The technical scheme that the present invention solves the problems of the technologies described above is:
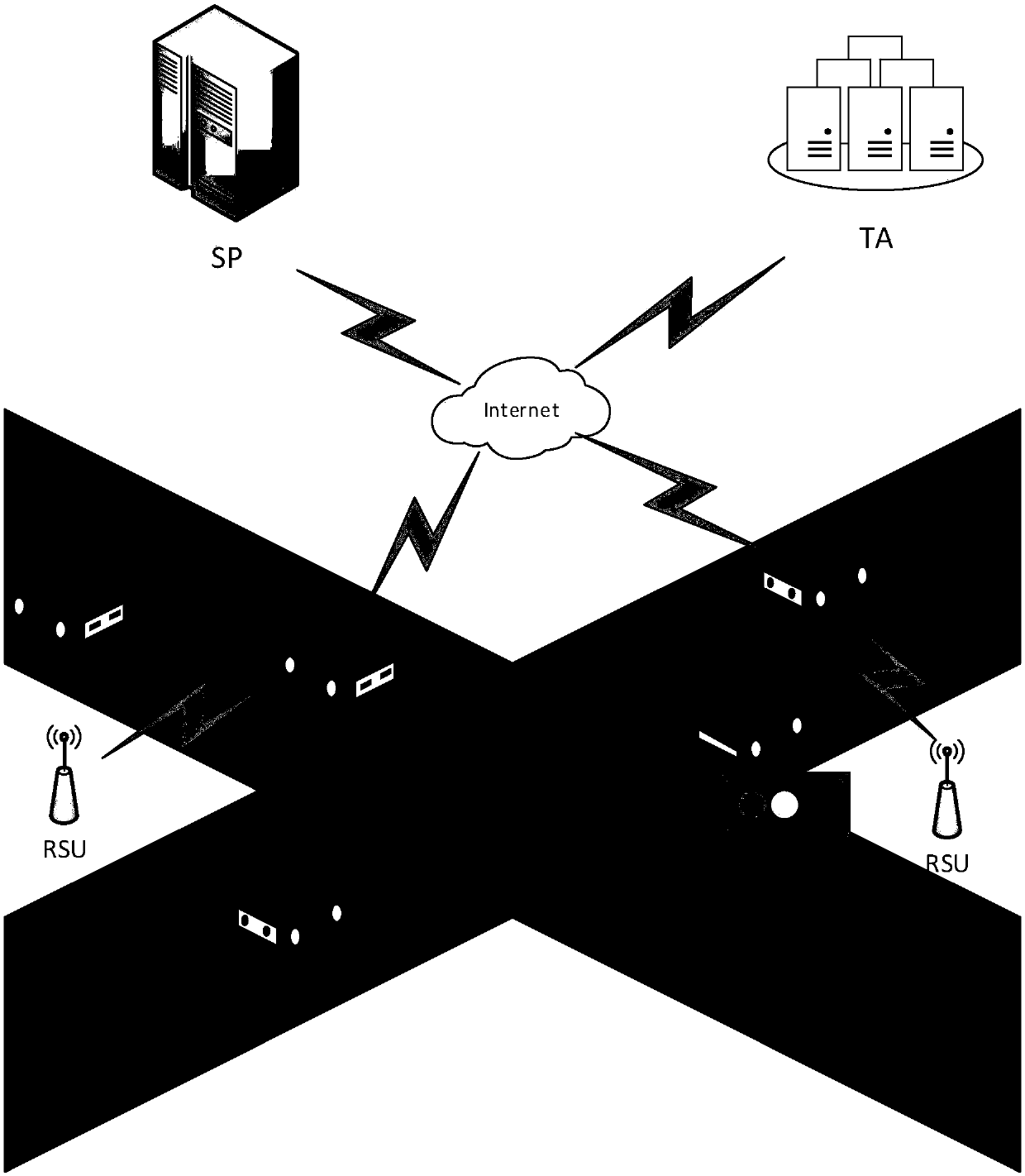
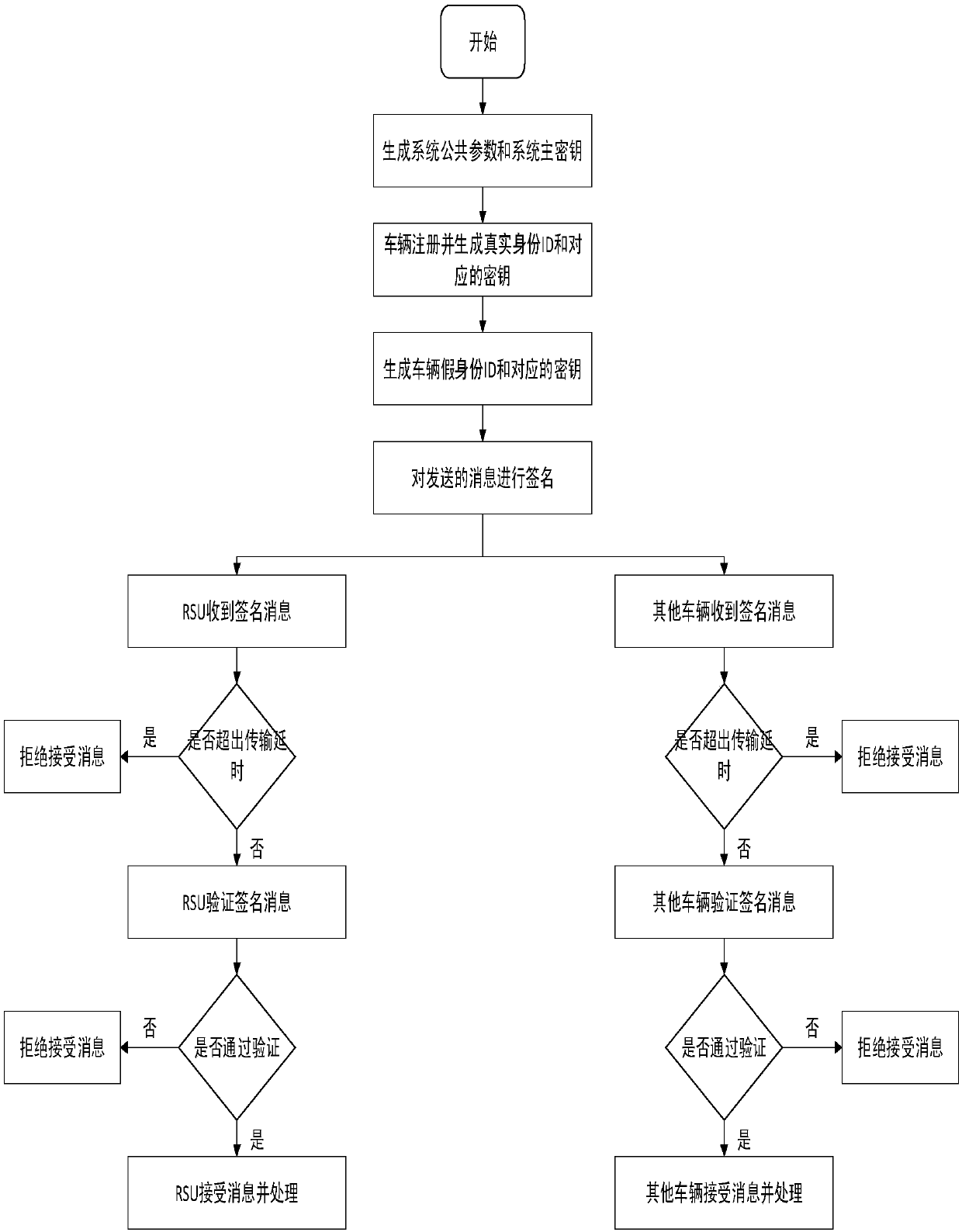
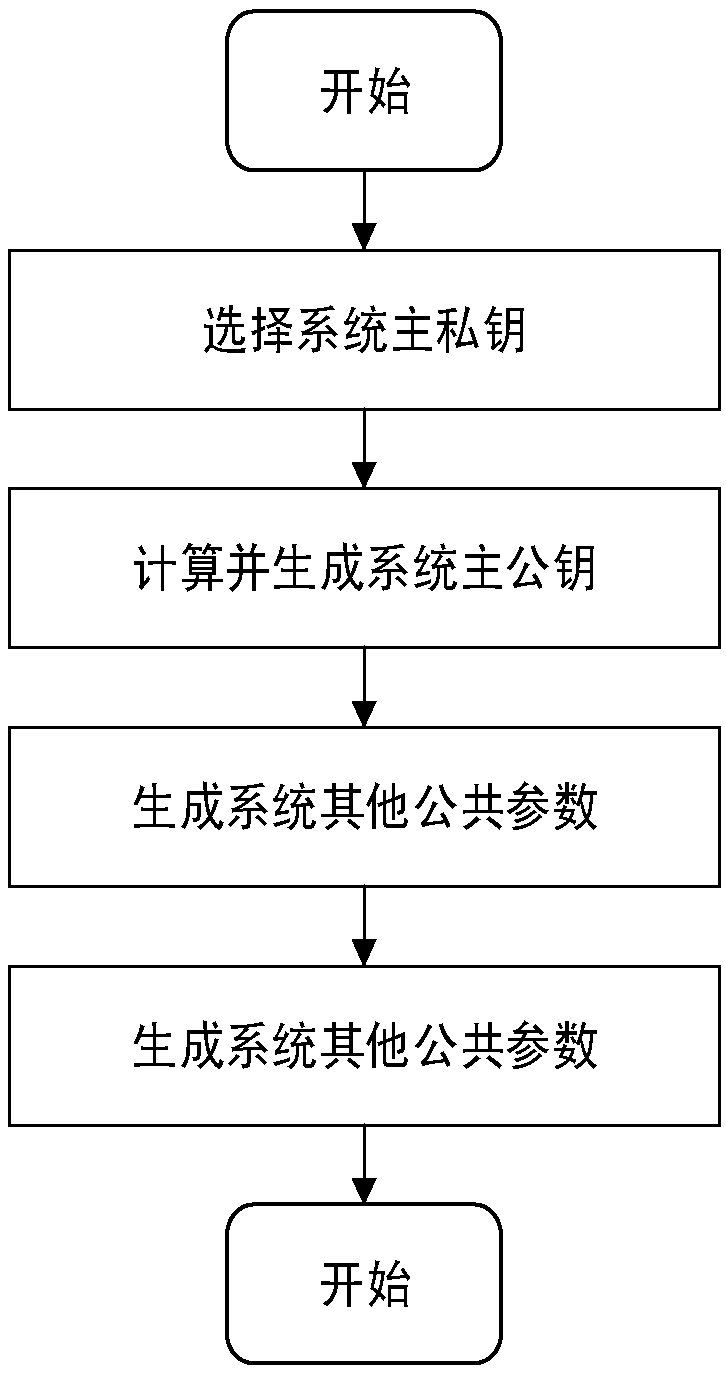
[0061] Based on the secure message delivery and authentication, the present invention proposes an efficient message delivery authentication mechanism in the Internet of Vehicles environment, which is suitable for message security delivery and fast authentication in the mobile vehicle ad hoc network.
[0062] In this mechanism, the vehicle first registers with the authority TA (trusted center), and TA generates a unique real identity ID and corresponding key for the vehicle. Secondly, the tamper-proof (anti-tampering device) installed on the OBU (on-board unit) generates a fake identity ID a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com