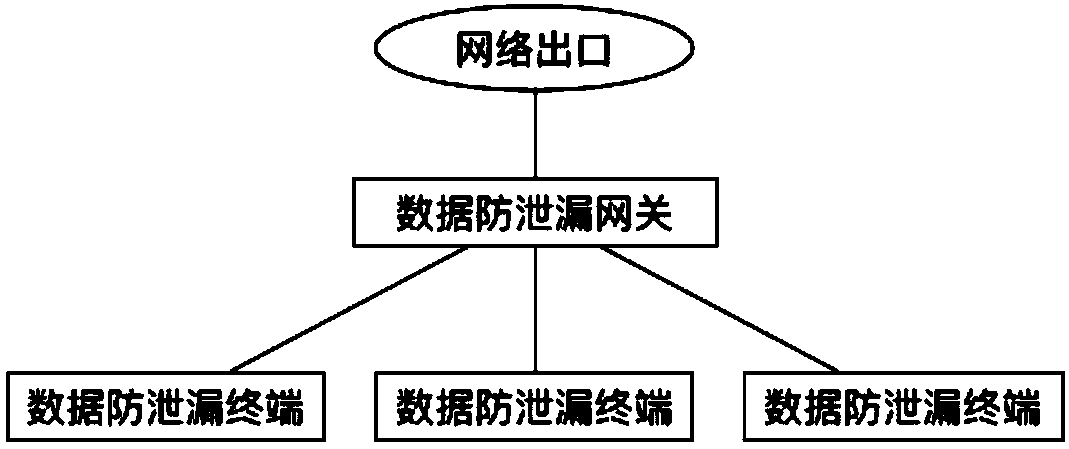
Collaborative data anti-leakage method and system
An anti-leak, data technology, applied in the field of data security, can solve problems such as affecting work efficiency, normal user operation interference, poor scalability, etc., to achieve the effect of improving comprehensive performance and avoiding data leakage incidents
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0063] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments, but the protection scope of the present invention is not limited thereto.
[0064]
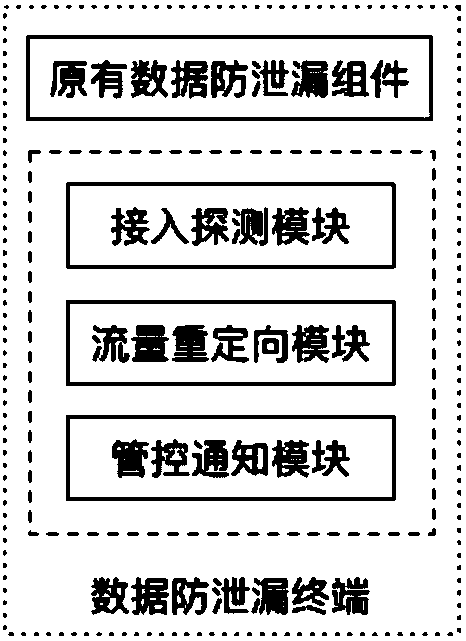
[0065] figure 2 It is the composition structure of the host-side terminal of the present invention. In addition to the original data leakage prevention components, the software also includes the access detection module required by the present invention, the flow redirection module (including functions such as SPI, Hook, drive and forwarding) and the user interface. A management and control notification module based on user notifications.
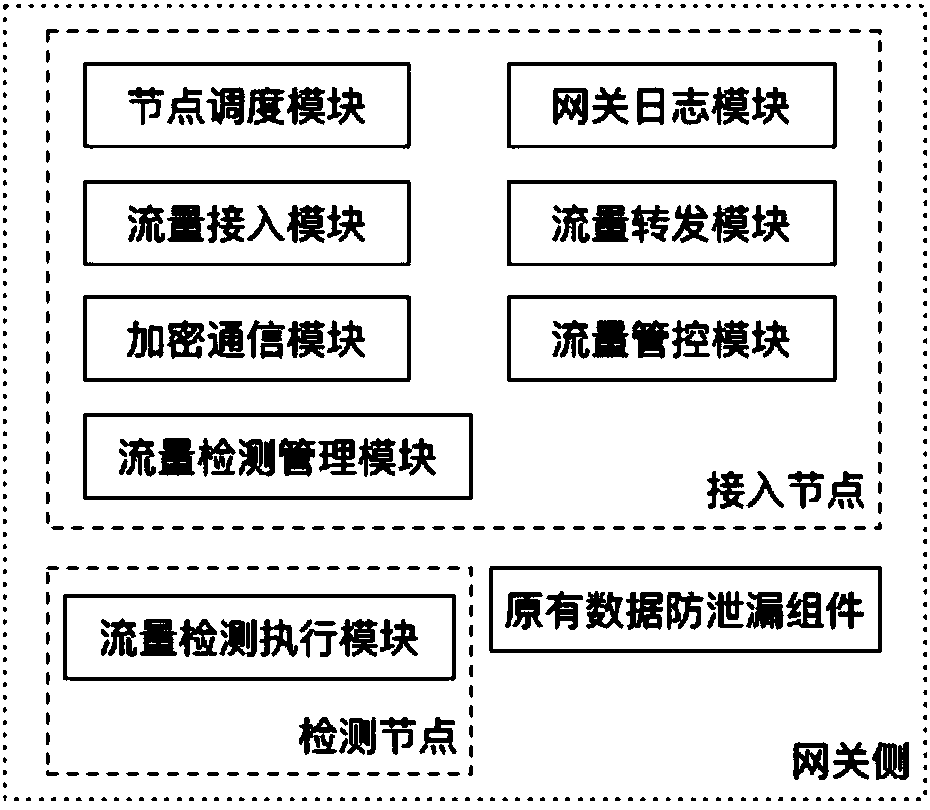
[0066] image 3 The composition structure of the gateway side of the present invention, in addition to the original data leakage prevention gateway component, also includes the access nodes (node scheduling module, flow access module, encrypted communication module, flow detection management module, flow forwarding module...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com