System secure starting method and device, set top box and storage medium
A technology of system security and startup instructions, applied in the computer field, can solve the problems of large space consumption, waste, and consumption of storage space, and achieve the effect of occupying less storage space and avoiding consumption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
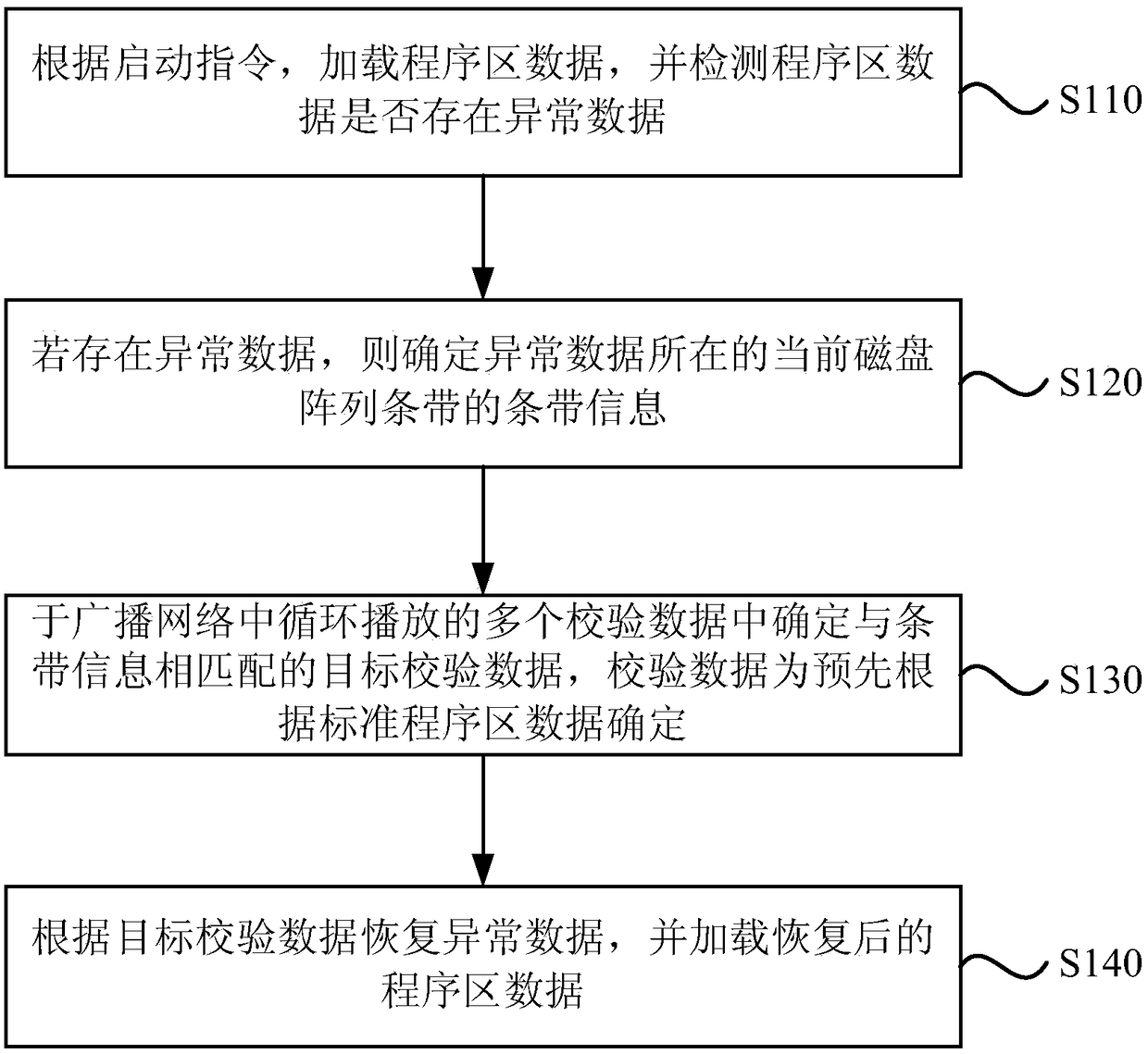
[0030] figure 1 It is a flow chart of a method for securely starting a system provided by Embodiment 1 of the present invention. This embodiment is applicable to the secure startup of an embedded system in a smart terminal, especially for the secure startup of an embedded system in a smart set-top box. The method can be executed by the device for system security startup provided by the embodiment of the present invention, and the device can be realized by software and / or hardware. The method specifically includes:
[0031] S110. According to the startup instruction, load the data in the program area, and detect whether there is any abnormal data in the data in the program area.
[0032] Wherein, the starting instruction may be an instruction generated by turning on a power switch on the device, where the device may be a set-top box. After the set-top box receives the startup instruction, it starts to load the data in the program area, wherein the data in the program area ref...
Embodiment 2
[0052] image 3 It is a schematic structural diagram of a system security startup device provided in Embodiment 2 of the present invention, and the device specifically includes:
[0053] The data loading module 210 is used to load the program area data according to the startup instruction;
[0054] An abnormal data detection module 220, configured to detect whether there is abnormal data in the data in the program area;
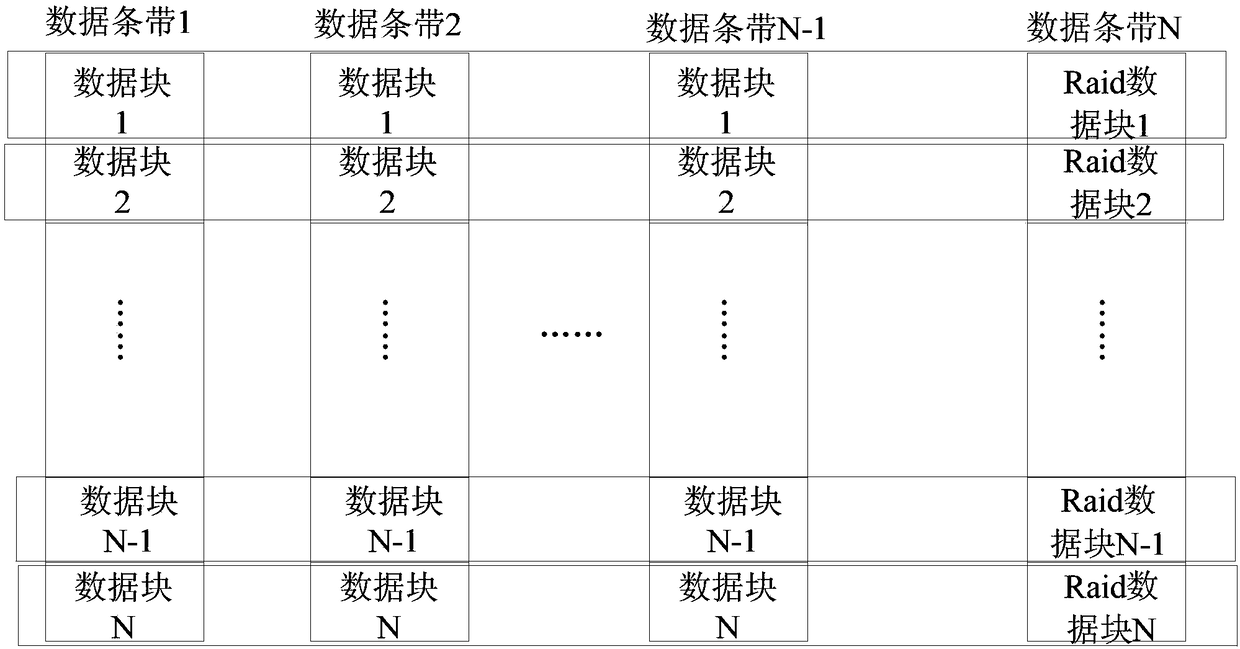
[0055] The stripe information determination module 230 is configured to determine the stripe information of the current disk array stripe where the abnormal data is located if there is abnormal data;
[0056] The target verification data determination module 240 is used to determine the target verification data that matches the stripe information among the plurality of verification data that are cyclically played in the broadcast network, and the verification data is determined in advance according to the standard program area data;
[0057] A data recovery...
Embodiment 3
[0071] The third example of this embodiment provides a set-top box. Figure 4 It is a schematic structural diagram of a set-top box provided in Embodiment 3 of the present invention. see Figure 4 , the set-top box includes:
[0072] one or more processors 310;
[0073] memory 320, for storing one or more programs;
[0074] When the one or more programs are executed by the one or more processors 310, the one or more processors 310 implement the system security boot method proposed in the embodiment of the present invention.
[0075] Figure 4 Take a processor 310 as an example; the processor 310 and the memory 320 can be connected through a bus or in other ways, Figure 4 Take connection via bus as an example.
[0076] The memory 320, as a computer-readable storage medium, can be used to store software programs, computer-executable programs and modules, such as program instructions / modules corresponding to the system security startup method in the embodiment of the prese...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com