A client-side deduplication method for encrypted data blocks supporting data update
A technology for encrypting data and updating data, which is applied in the computer field, and can solve problems such as low efficiency in decrypting file block ciphertext, inability to support users to update file blocks, and no method for file ownership authentication.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0084] The present invention will be described in further detail below in conjunction with the accompanying drawings.
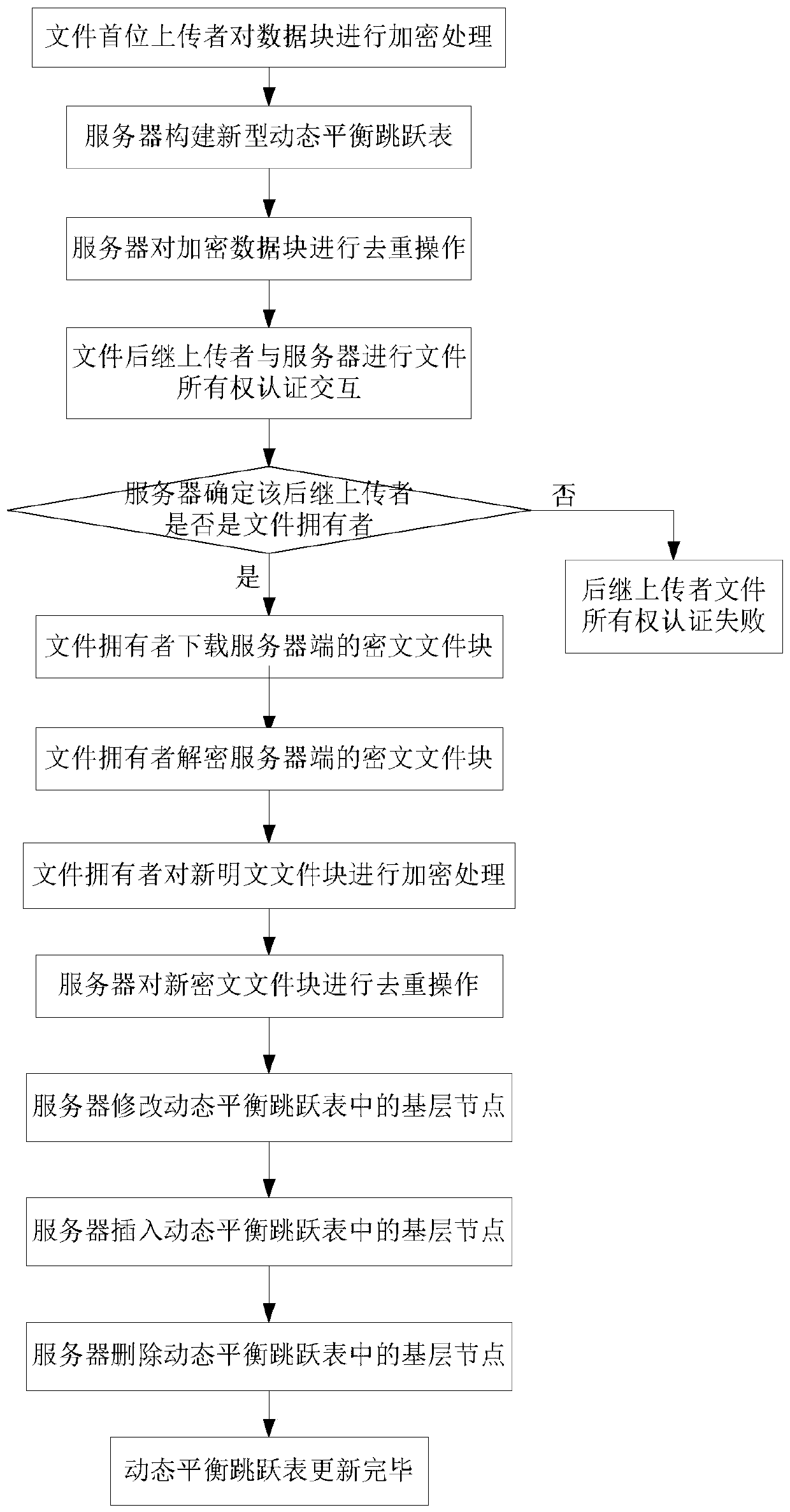
[0085] Attached below figure 1 Further detailed description is made on the steps realized by the present invention.
[0086] Step 1, the first uploader of the file encrypts the data block.
[0087] The first uploader of the file uses the 256-bit secure hash algorithm SHA256, takes the plaintext file as input, calculates the key of the plaintext file, and uses the key of the plaintext file as input to calculate the label of the plaintext file.
[0088] The 256-bit secure hash algorithm SHA256 refers to: the 256-bit one-way hash algorithm SHA256 specified in the federal information processing standard FIPS PUB 180-3 issued by the National Institute of Standards and Technology, applicable to 64 Binary message.
[0089] The first uploader of the file divides the plaintext file into blocks with a length of 4kb to generate multiple plaintext file blocks.
[009...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com