Safe and trusted image formation device and control method thereof and imaging system and method
An imaging control and image technology, applied in computer security devices, input/output process of data processing, electrical recording technology using charge graphics, etc., can solve image forming control program attacks, lack of security risks, and data leakage of image forming devices and other issues to avoid the impact of startup time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
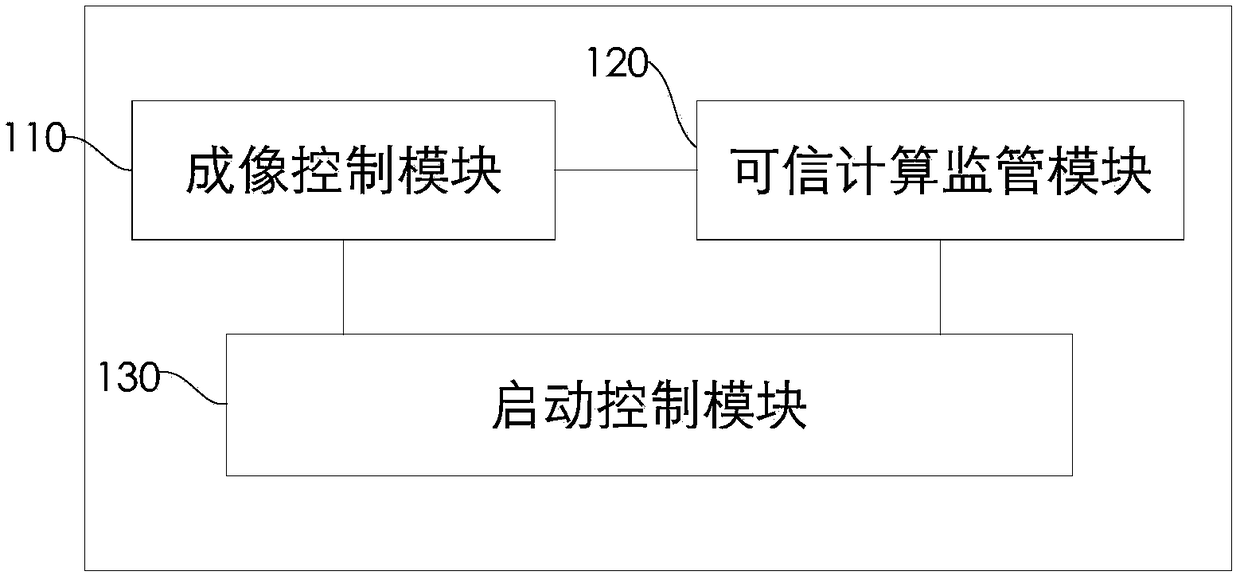
[0049] Such as figure 1 As shown, the embodiment of the present invention provides a safe and reliable image forming device, the image forming device includes:
[0050] The imaging control module 110 is used to control the imaging processing operation of the image forming device; the imaging control module 110 is used to perform processing operations related to data sending and receiving, command sending and receiving, and engine control, for example, how to call interface units through application programs (including but not limited to USB port, wired network port, wireless network port, etc.) to send and receive data, commands, status, etc., and can also obtain the received printing parameters through the application program, and parse them into commands that control the engine mechanism to perform specific functions, for example, LSU exposure parameters, pick-up roller rotation parameters, etc.; in addition, for image forming devices with user authority authentication or en...
Embodiment 2
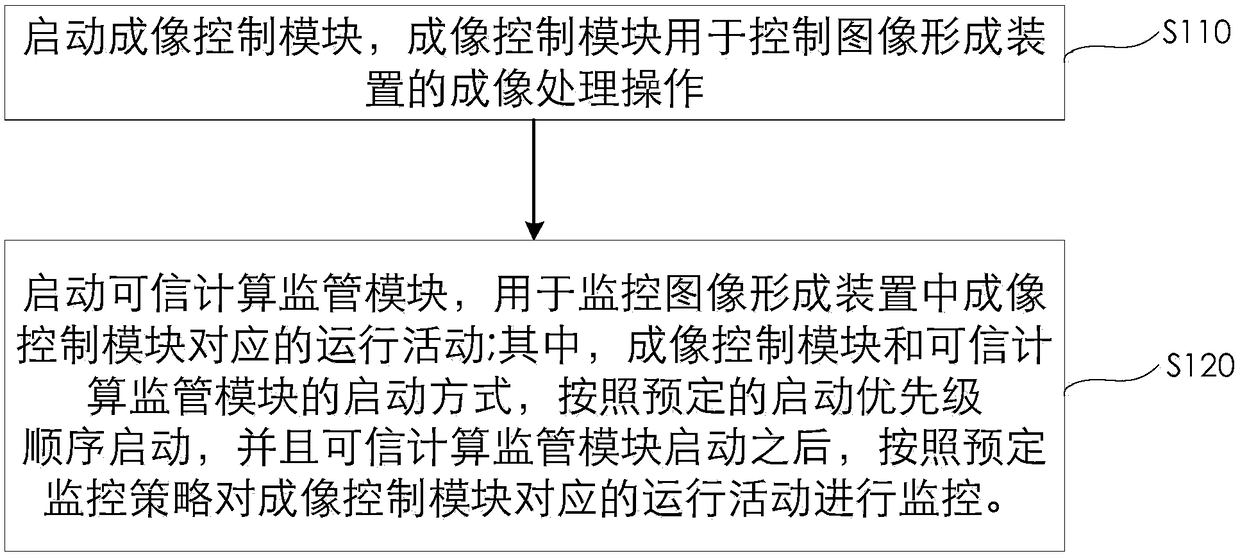
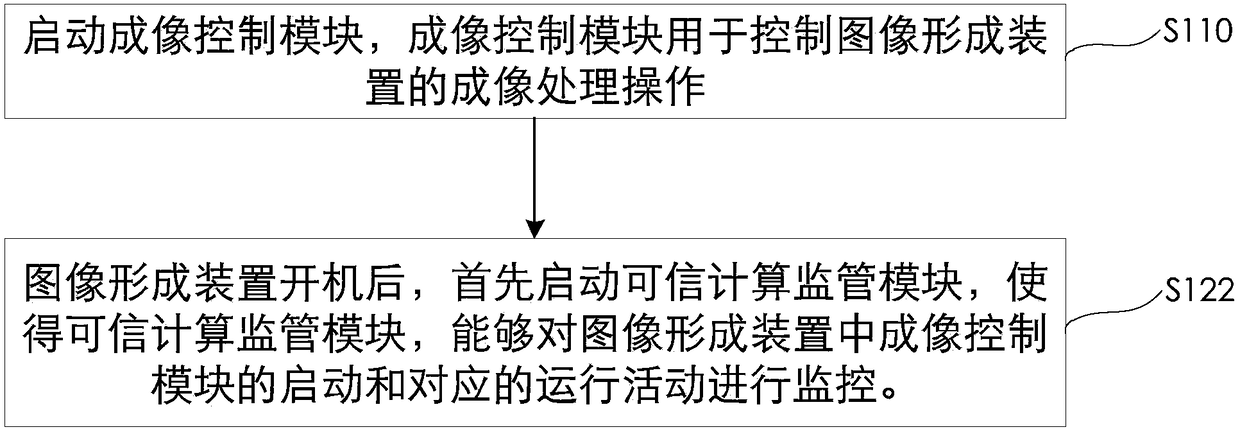
[0064] Such as figure 2 As shown, this embodiment provides a safe and credible image formation control method, the control method comprising:
[0065] S110, start the imaging control module, the imaging control module is used to control the imaging processing operation of the image forming device; that is, start the imaging control module in the image forming device, and generate corresponding running activities corresponding to the image processing operation;
[0066] S120. Start the trusted computing supervision module, which is used to monitor the operation activities corresponding to the imaging control module in the image forming device; that is, start the trusted computing supervision module to generate corresponding operation activities corresponding to the trusted computing supervision; , the startup mode of the imaging control module and the trusted computing supervision module is started according to the predetermined startup priority order, and after the operation ...
Embodiment 3
[0085] Such as Figure 5 As shown, the present embodiment provides an imaging system, which includes:
[0086] One or more secure and trusted image forming devices as mentioned in Embodiment 1, for example, the first image forming device 100, ... the Nth image forming device 200;
[0087] The trusted monitoring server 300, the trusted monitoring server 300 can update the monitoring policy in the image forming device.
[0088] Preferably, when the trusted computing supervision module in the image forming apparatus 100, 200 monitors that there is an imaging control module (imaging control sub-module) in the image forming apparatus that does not conform to the monitoring strategy and / or the corresponding operation activity is running, it prevents the current imaging The control module (imaging control sub-module) and corresponding operation activities are executed, and the abnormal activity information is uploaded to the trusted monitoring server 300 .
[0089] Specifically, im...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com