Method for generating executable file, execution method and electronic equipment
A technology for executing files and electronic devices, applied in the computer field, can solve problems such as increasing development complexity and affecting user experience, and achieve the effects of reducing development complexity, reducing application costs, and ensuring code security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
[0067]
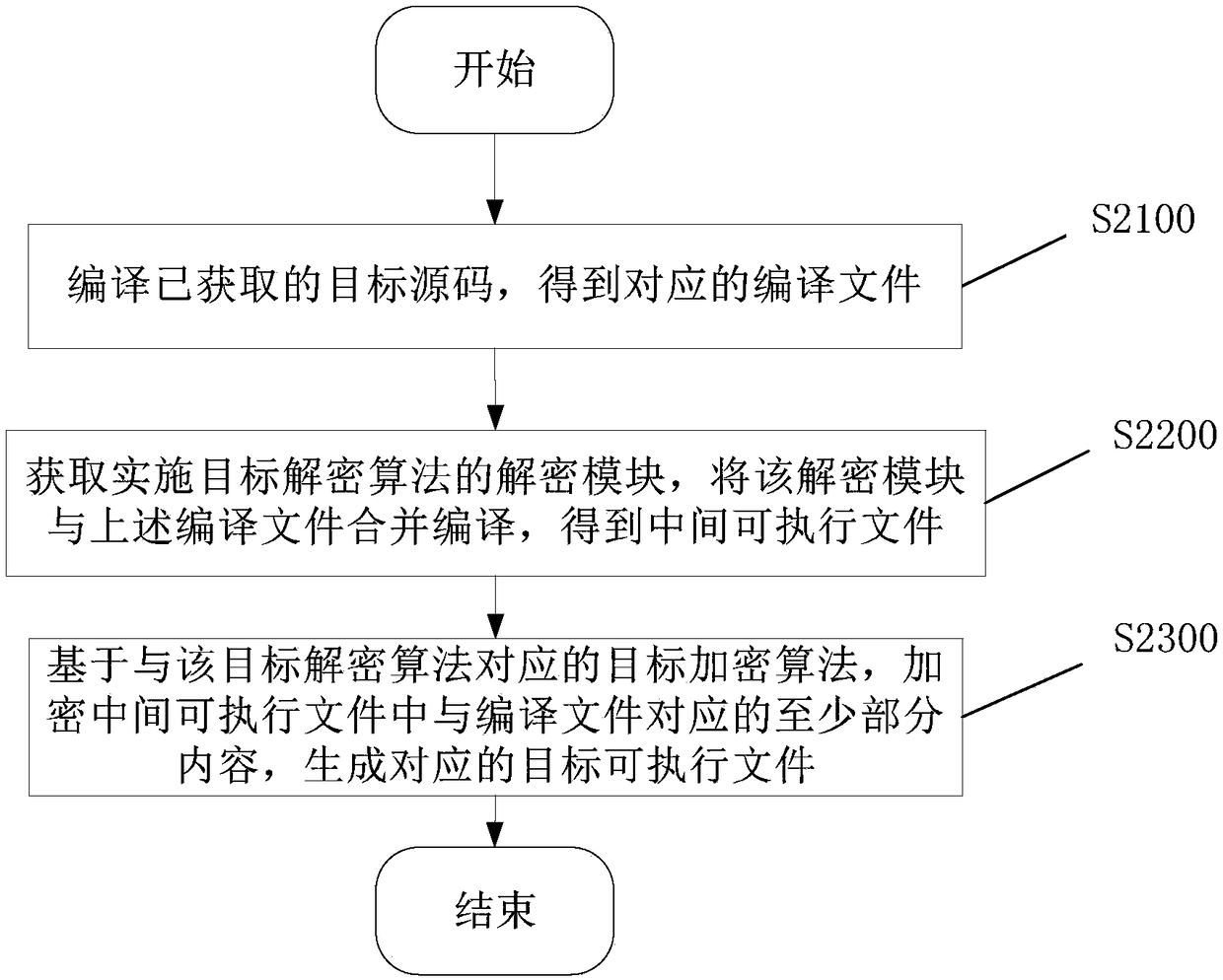
[0068] In this embodiment, a method for generating an executable file is provided, such as figure 2 As shown, it includes: steps S2100-S2200.
[0069] The executable file refers to a file that can be loaded and executed by the operating system. Executable files are presented differently under different operating system environments. Under the Windows operating system, the executable file can be a type of file such as .exe / .sys / .com.
[0070] Step S2100, compiling the acquired target source code to obtain a corresponding compiled file.
[0071] The target source code is code developed based on a certain programming language to provide corresponding application functions. Usually code development can be based on a certain programming platform. For example, the target source code can be code developed based on UCDA platform. CUDA (Compute Unified Device Architecture) is a computing platform launched by graphics card manufacturer NVIDIA. It adopts a general parallel...
no. 2 example
[0127]
[0128] In this embodiment, a method for running an executable file is provided, such as Figure 5 As shown, it includes: steps S3100-S3200.
[0129] Step S3100, obtaining the target executable file.
[0130] The target executable file is generated by the method for generating an executable file provided in the first embodiment, which will not be repeated here.
[0131] Step S3200, run the decryption module in the target executable file, implement the corresponding target decryption algorithm through the decryption module, and decrypt the part contained in the target executable file that is encrypted based on the target encryption algorithm corresponding to the target decryption algorithm content to get the decrypted target executable file and run it.
[0132] The target executable file contains identification information indicating part of the encrypted content, such as the function name, file name or specific storage location of the target source code correspondi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com