Block chain secret key recovering method based on multi-party security computing technology, and medium
A technology of key recovery and computing technology, applied in the field of blockchain key recovery, it can solve problems such as failure to meet customer needs, against the wishes of the entrusting party, and too large core nodes, so as to protect user rights and interests, backup and restore security, Achieve the effect of user identity management
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
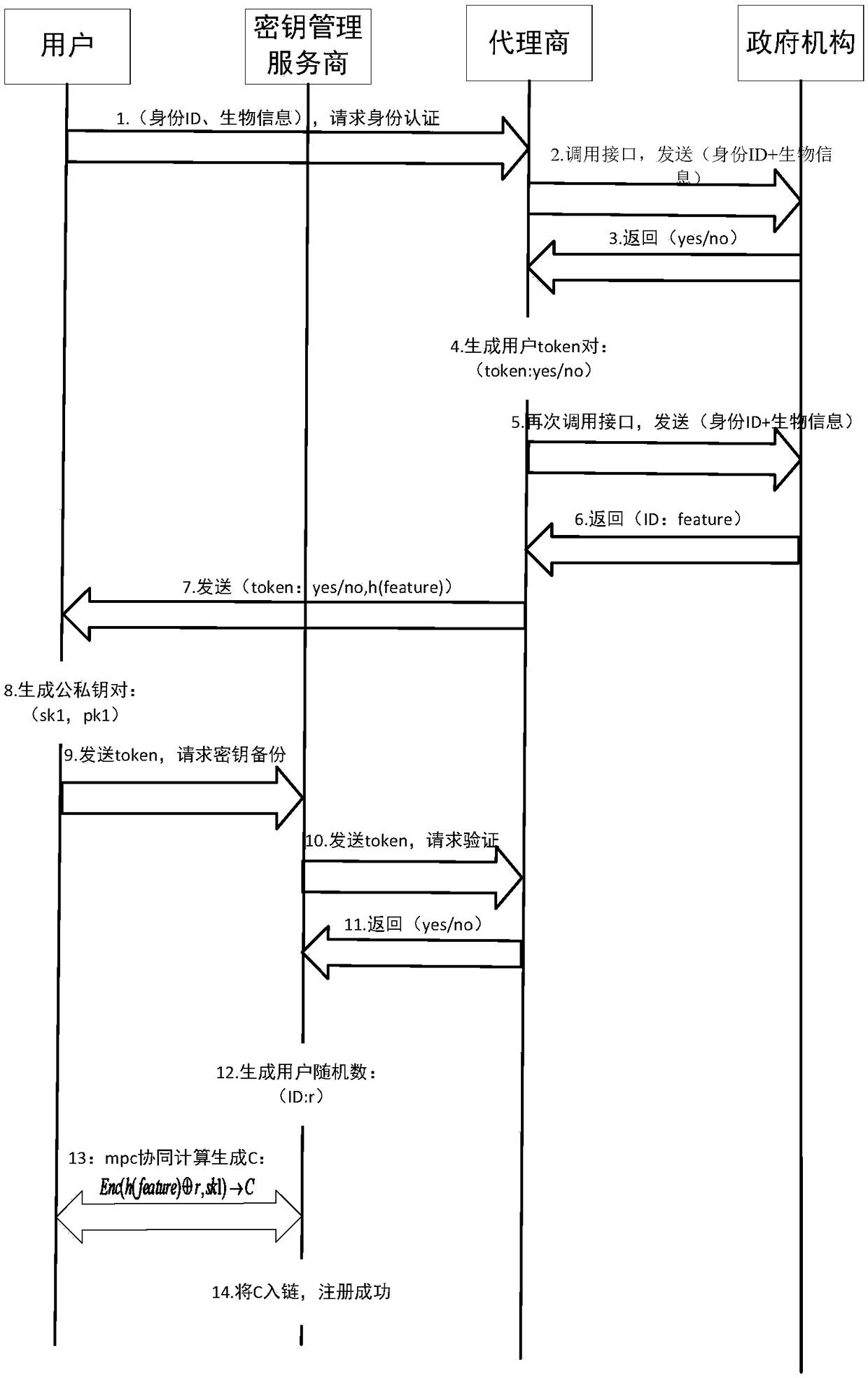
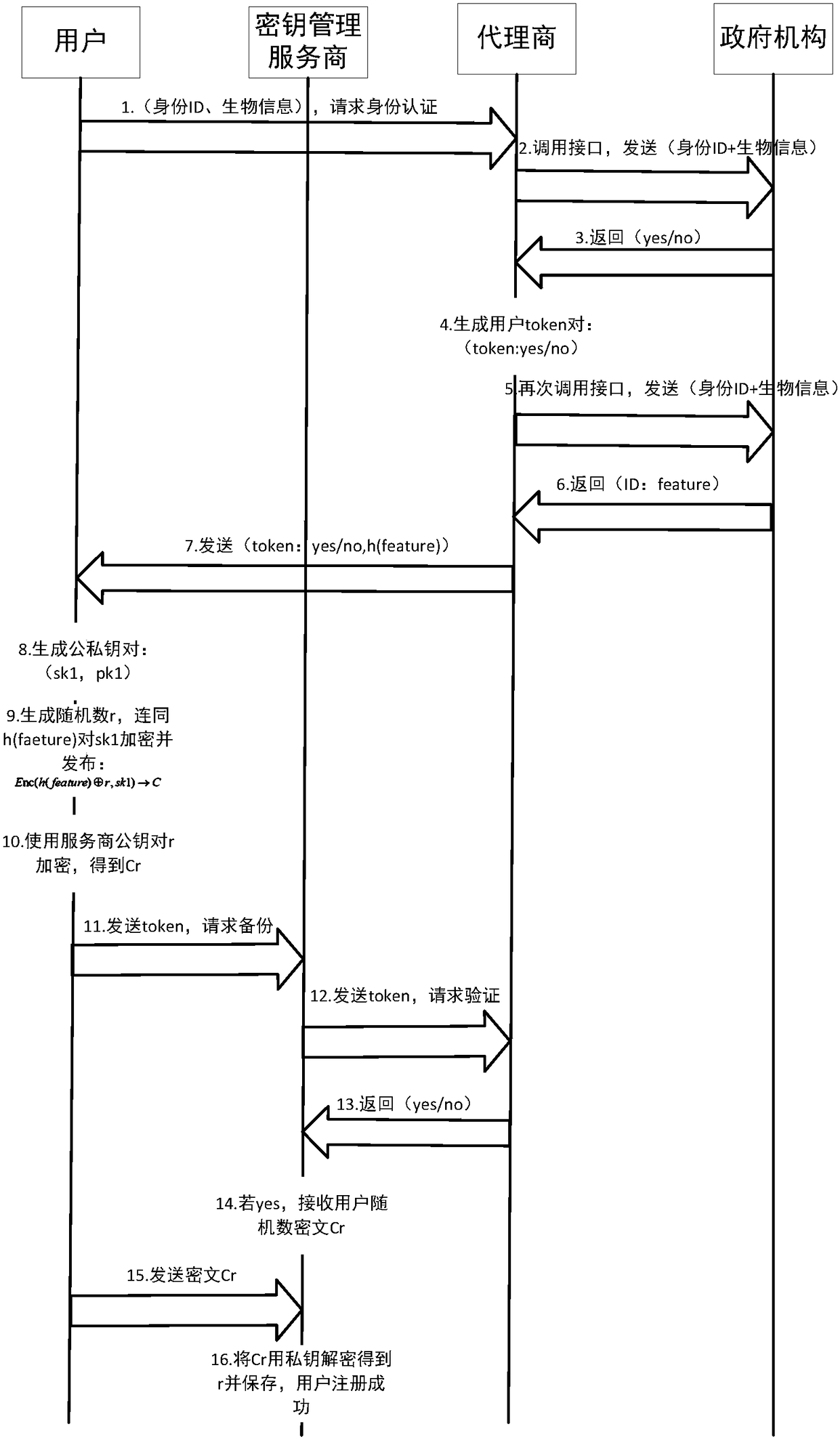
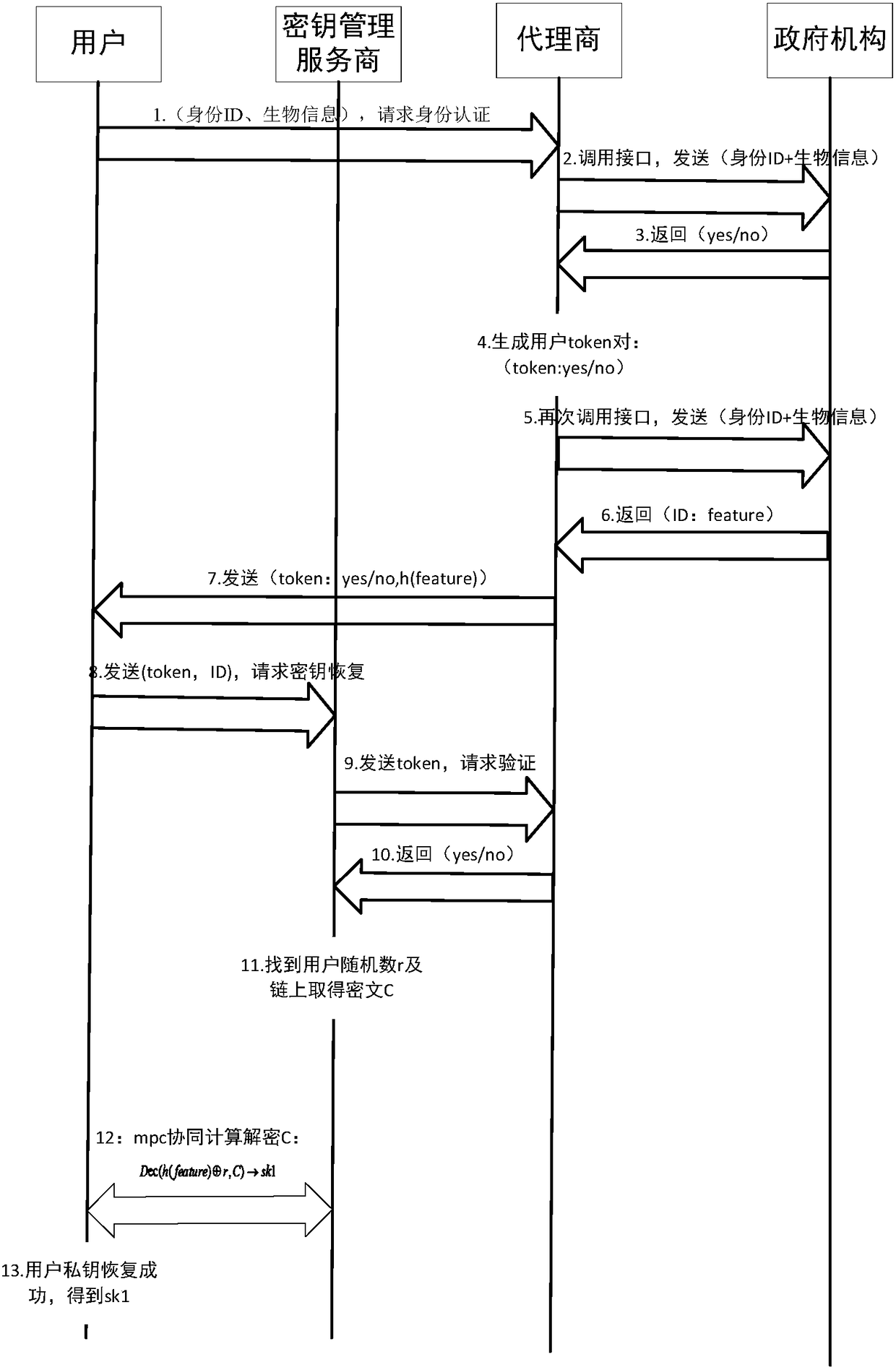
[0030] The present invention will be described in detail below in conjunction with the accompanying drawings and specific embodiments. Note that the aspects described below in conjunction with the drawings and specific embodiments are only exemplary, and should not be construed as limiting the protection scope of the present invention.
[0031] Traditional centralized institutions, such as banks, can use real-name authentication and other means. If the USB-shield representing the user’s identity is lost or the password is forgotten, the system can re-bind a new USB-shield (private key) through account verification. Realize the freezing and recovery of relevant account assets, and recover digital assets to a certain extent. The account and the private key are logically bound, and the centralized bank operates under the requirements of risk control.
[0032]In order to solve the technical problems proposed by the present invention, the present invention refers to the idea of ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com