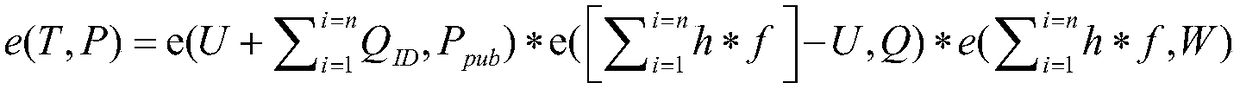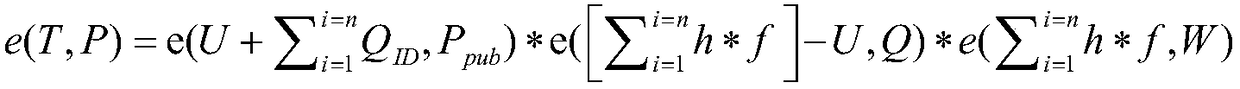Polymer electronic signature method of fixed signature length
An electronic signature and aggregated electronic technology, applied in the field of communication, can solve the problems that users cannot receive messages correctly and affect the efficiency of electronic signature verification, and achieve the effect of overcoming low verification efficiency, reducing calculations, and ensuring privacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
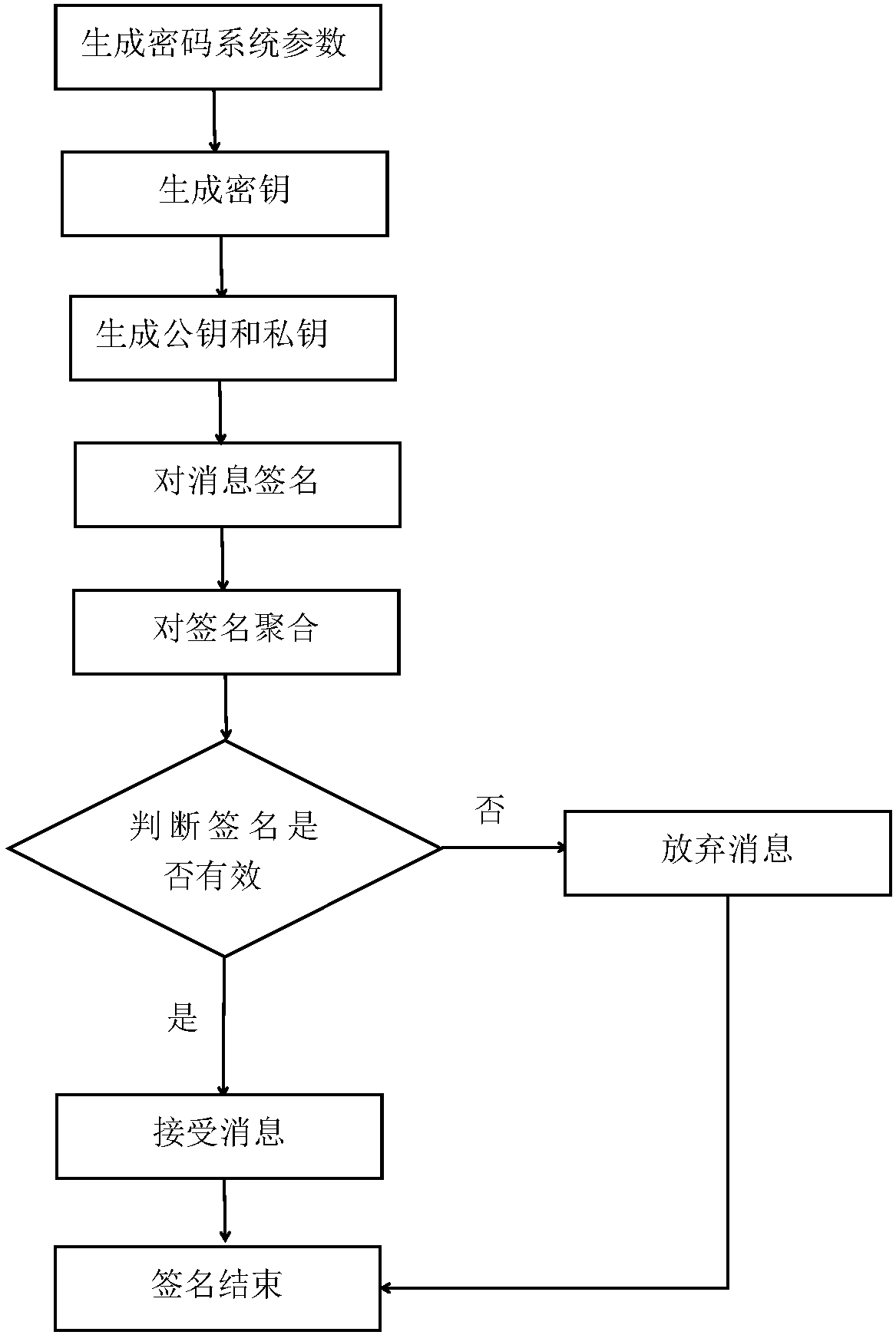
[0042] Attached below figure 1 The present invention is further described.
[0043] Step 1, generate cryptographic system parameters.
[0044] The key generation center selects a large prime number i according to the security parameter z of the cryptographic system, where z64 and i>2 z .
[0045] The key generation center constructs two additive cyclic groups G of order i 1 and G 2 , at G 1 Randomly select a generator from .
[0046] The key generation center respectively constructs the first hash function H 1 : {0,1} * →G 1 ; the second hash function H 2 : {0,1} * →G 1 ; the third hash function H 3 : {0,1} * → Z q * ; The fourth hash function H 4 : {0,1} l →G 1 .
[0047] The remaining group Z whose key generation center is at order q q Randomly select the master key of a cryptosystem from .
[0048] The product of the master key of the cryptosystem and the generator of the additive cyclic group is used as the master public key of the cryptosystem.
[00...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com