Verifiable post quantum electronic voting system and implementation method thereof
An electronic and quantum technology, applied in the field of information security, can solve problems such as being unable to resist quantum computer attacks and unable to verify the legitimacy of votes
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
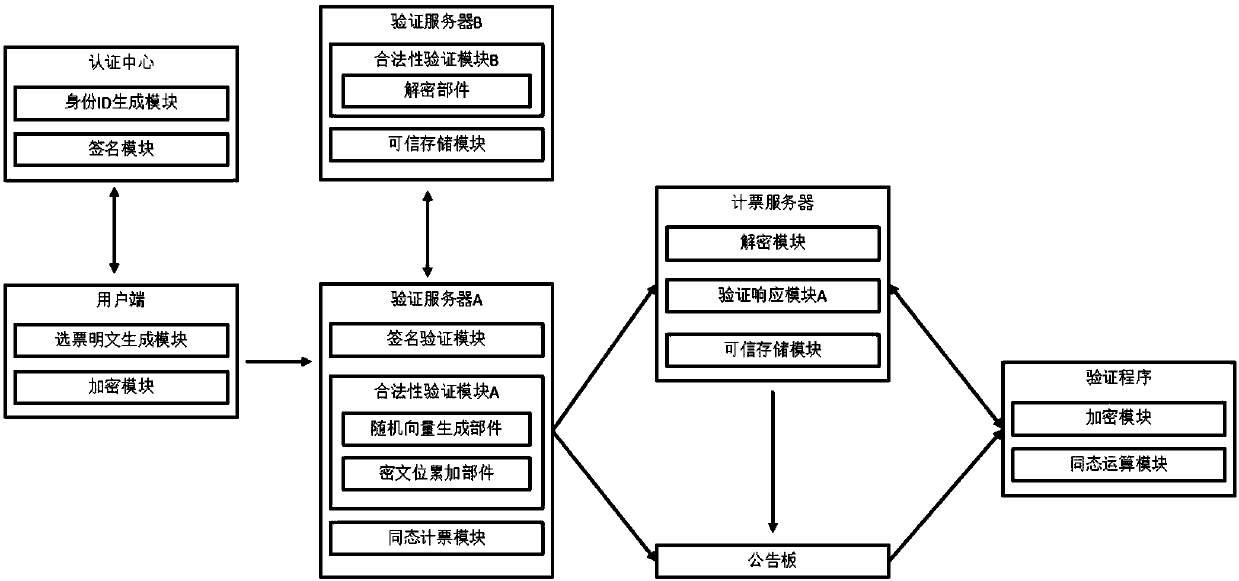
[0127] like figure 1 As shown, a verifiable post-quantum electronic voting system includes an authentication center, a client, a verification server, a vote counting server, a verification program, and a bulletin board;
[0128] The authentication center is used to verify the identity of the user, and generates an identity ID for each legal user and signs it; the authentication center includes an identity ID generation module and a signature module, and is provided with a public and private signature module. key pair;
[0129] The user end proves its identity to the authentication center, receives the identity ID signature, encrypts its own ballot, and sends the ballot ciphertext and the identity ID signature to the verification server; the user end includes a ballot plaintext generation module and an encryption module; when starting to vote, the user first sends his own identity certificate to the authentication center, and obtains his ID signature after the authentication i...
Embodiment 2
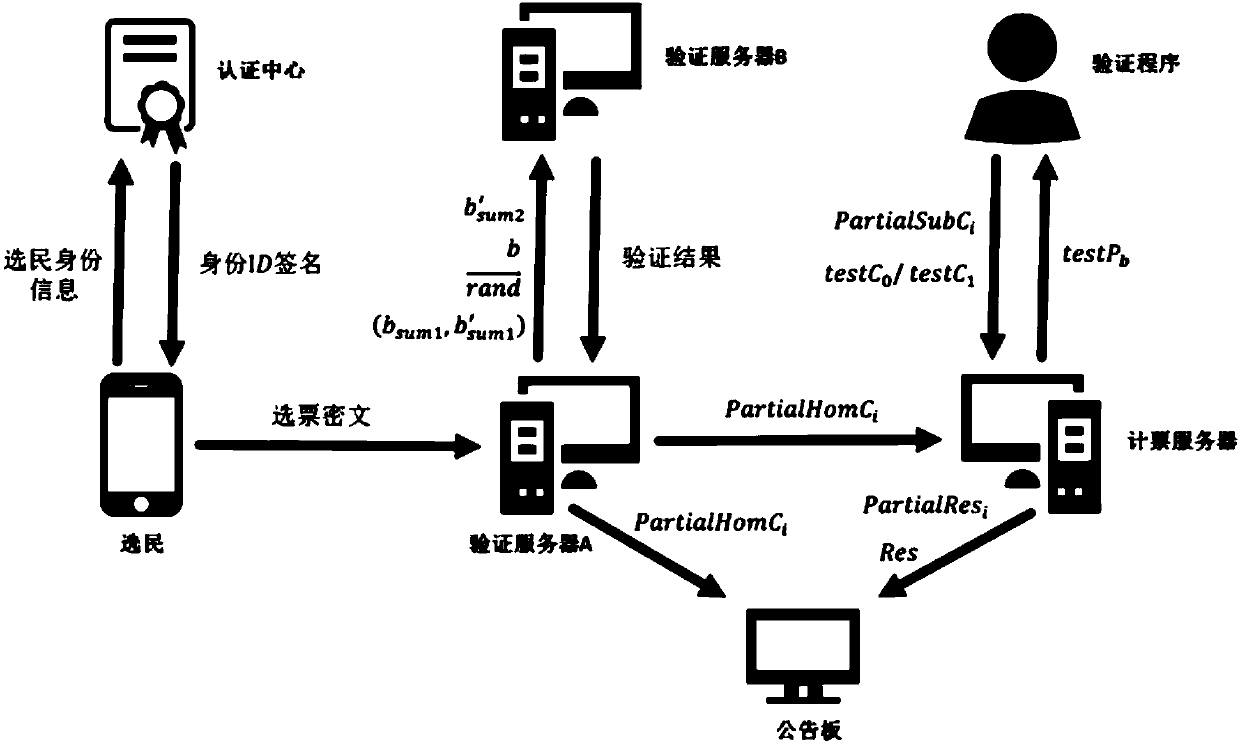
[0145] A verifiable implementation of a post-quantum electronic voting system such as figure 2 The voting process shown includes the following steps:
[0146] S1, the system initialization step, this step is specifically:
[0147] S11. Select and generate public parameters; select LWE encryption system parameters n, l, q, α, and homomorphic vote counting upper limit VHom max , where n is the security parameter of the LWE encryption system; l is the length of the ballot plaintext string, representing the number of candidates; q represents the modulus, since the homomorphic operation is a finite field operation, the operation result should be modulo q operation, α It is a parameter used in Gaussian sampling, which is related to the square difference of sampling; VHom max Indicates the maximum number of times that VSA can perform homomorphic addition operations for each partial homomorphic vote counting;
[0148] S12. According to the public parameters, generate the public-pr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com