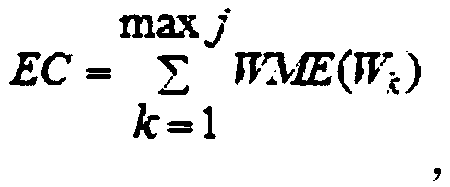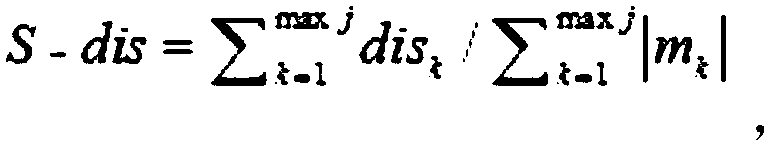Digital watermark embedding and protection methods for database
A digital watermark and database technology, applied in the field of data security, can solve problems such as difficult to be detected and difficult to find
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0065] A database digital watermark embedding method, comprising:
[0066] Step 1. Score the attribute columns of the target database, and select the embedded attributes according to the scoring results, including:
[0067] Step 11, calculate the digital watermark embedding capacity
[0068]
[0069] where WME(W k ) is calculated as, if dis k L , then WME(W k )=1; if dis k ≥2 L , then WME(W k )=0.
[0070] where dis k The calculation method of is, if k=0, then dis k = 2 Lev ; if k≠0, then dis k =|m k-1 -m k |.
[0071] Among them, Lev is the number of layers of the binary tree, m k is the original value of the Kth tuple in the attribute, j is the tuple number, and max j is the maximum tuple number.
[0072] Step 12, calculate the distortion rate of the data to be embedded in the attribute relative to itself
[0073]
[0074] Judgment|m k -m k-1 |Lev Whether it is established, if so, then dis k =|m k -n k |, if not, then dis k =0, where, n k is the ...
Embodiment 2
[0094] A method for protecting a database, comprising:
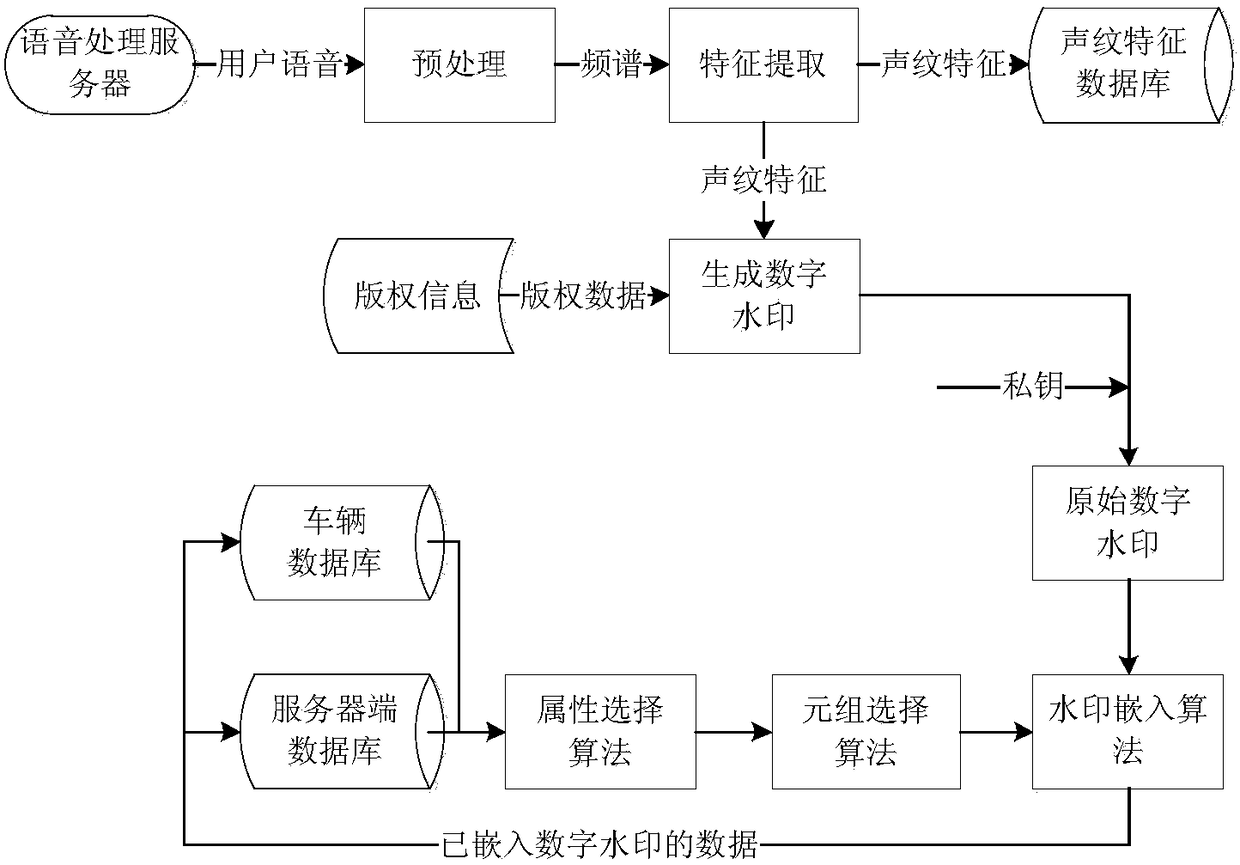
[0095] Step 1, obtaining data information of users and objects to be protected;
[0096] Step 2, generating a digital watermark from the data information through a hash function;
[0097] Step 3, using the digital watermark embedding method described in Embodiment 1 to embed the digital watermark into the target database to be protected;
[0098] Step 4, encrypt the target database information (position information matrix, original watermark and information used to generate the watermark) embedded with the digital watermark in step 3, and store it in the information database.
[0099] Preferably, the data information includes the user ID and user voiceprint information corresponding to the user ID one-to-one, and the method for extracting the user voiceprint information includes: extracting the audio information of the user voice password from the background of the voice cloud, and performing Mel on the audio informatio...
Embodiment 3
[0101] A watermark generation and embedding method for an Internet automobile database, the data information also includes vehicle information.
[0102] In step 2 of this embodiment, the digital watermark generated by the data information through the hash function is
[0103] H=hash(CarInfo||VoiceInfo||CustomerID||CompanyID||DatabaseInfo)
[0104] Among them, CarInfo is vehicle information, VoiceInfo is user voiceprint information, CustomerID is user ID, CompanyID is vehicle company information, and DatabaseInfo is target database information.
[0105] A method based on voiceprint features and digital watermarking is used to perform copyright identification, copyright tracking, and integrity verification on the Internet version of the background database of vehicle models, so as to achieve the purpose of improving the above problems.
[0106] The steps of the technical solution in this paper are as follows:
[0107] 1. Obtain the voiceprint characteristics corresponding to t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com