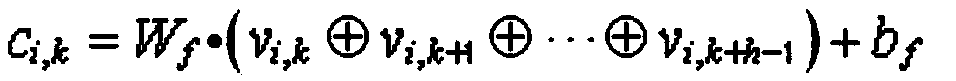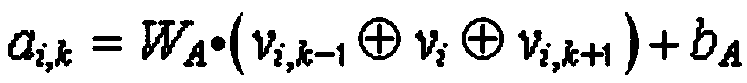Method and system for detecting and locating network anomaly
A technology of network anomaly and positioning method, applied in the field of network anomaly detection and positioning method and system, can solve the problems of false negative attack, increased false negative rate, inability to locate malicious code area, etc. The effect of preventing overfitting
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] The technical solutions in the embodiments of the present invention will be described clearly and in detail below with reference to the drawings in the embodiments of the present invention. The described embodiments are only some of the embodiments of the invention.
[0046] The technical scheme that the present invention solves the problems of the technologies described above is:
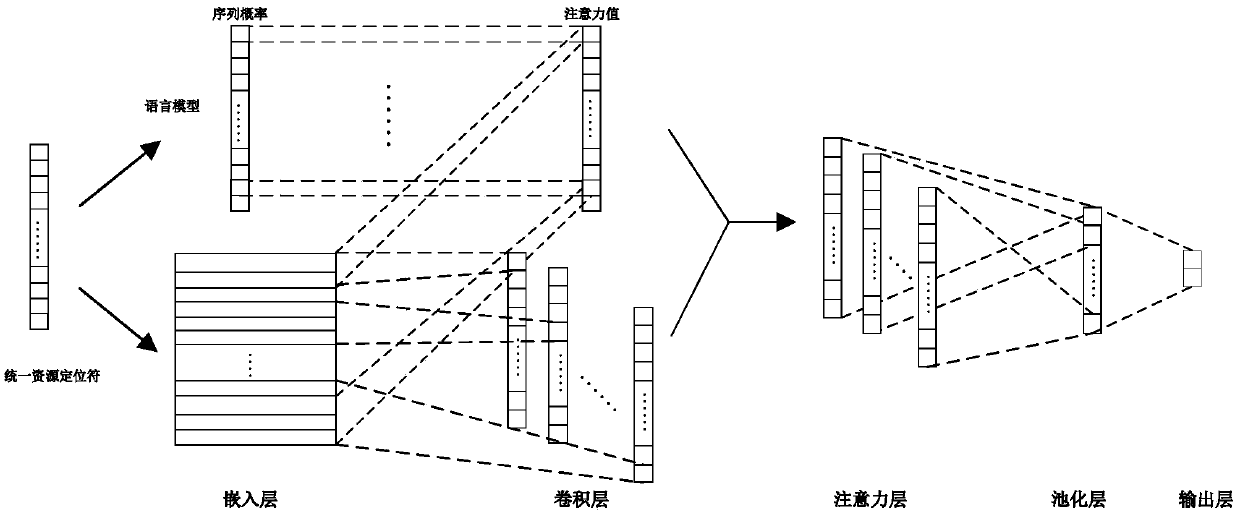
[0047] The main design concept of the technical solution of the present invention is to detect abnormal URLs in the network, using normal URLs and local file inclusion (LFI), SQL injection, cross-site scripting (XSS) and command injection attacks (COM) The data set composed of common types trains the convolutional neural network anomaly detection method based on the sequence attention mechanism proposed by the invention. The invention can better detect abnormal URLs with a high detection rate, and can also mark and visualize malicious code parts in abnormal URLs, effectively avoiding the di...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com