Internet of Things intrusion detection method based on machine learning
An intrusion detection and machine learning technology, applied in the field of Internet of Things security, can solve problems such as insufficient computing power, difficulty in meeting demands, and limited power supply energy, and achieve high computing efficiency, low false alarm rate, and high detection rate.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0048] The preferred embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings.
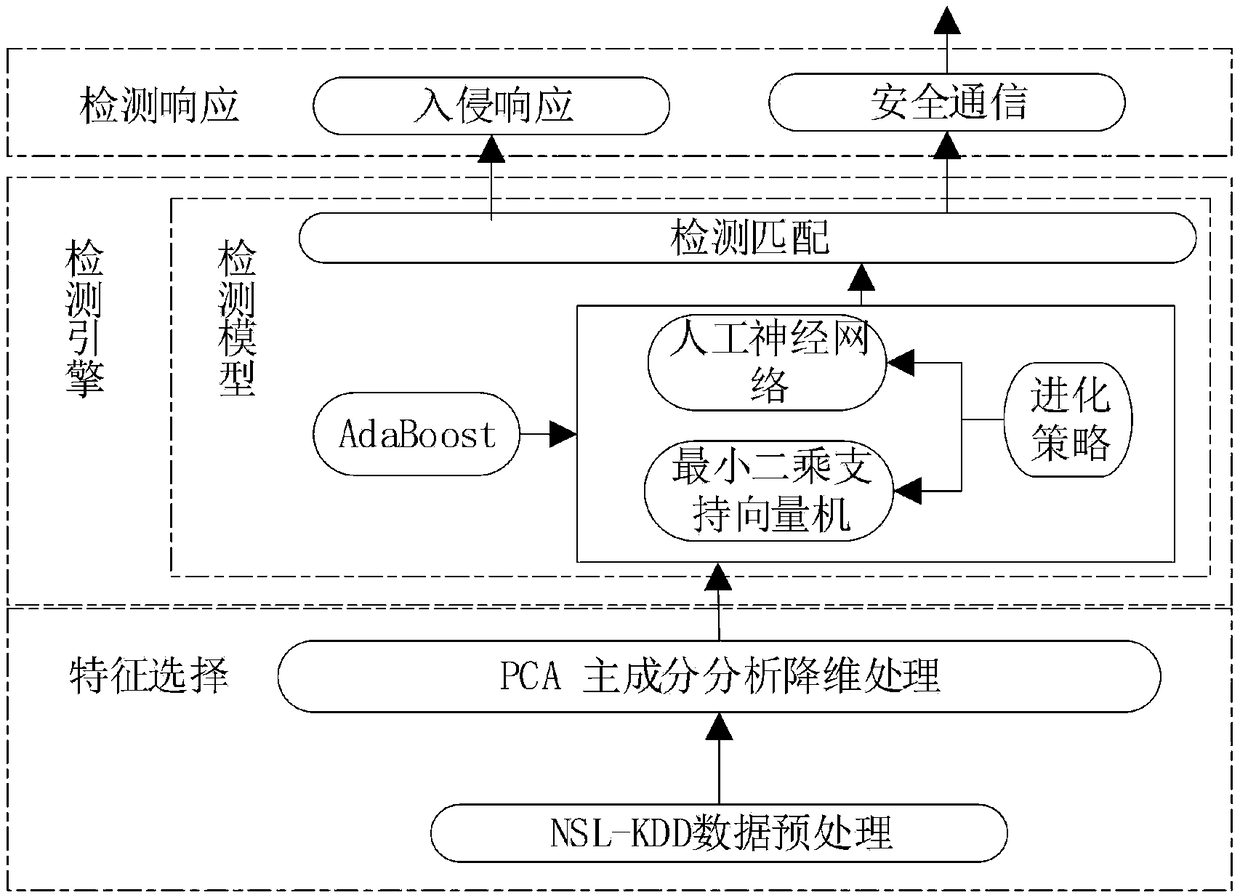
[0049] Reference figure 1 The detection flowchart shown in the embodiment of the present invention, a method for detecting intrusion of the Internet of Things based on machine learning, includes the following steps:
[0050] 101. In data preprocessing, digitize and standardize the NSL-KDD network intrusion data set;
[0051] 102. Divide the data set and reduce the dimensionality of the data: perform principal component dimensionality reduction on the processed data, so that the relevant feature values of the original data set are transformed into mutually independent or unrelated variables, so that the feature value is reduced and the calculation is reduced the complexity. The data set after dimensionality reduction is divided into training set and test set by cross-validation method.
[0052] 103. Construct a Least Squares Support Vector Mac...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com