Microprocessor Privilege Escalation Attack Simulation Method
A microprocessor and privilege escalation technology, applied in the field of integrated circuit security, can solve the problems of slow speed and low efficiency, and achieve the effect of fast speed and no loss of flexibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0013] In order to enable those skilled in the art to better understand the technical solutions of the present invention, the specific implementation manners of the present invention will be further described in detail below in conjunction with the accompanying drawings.
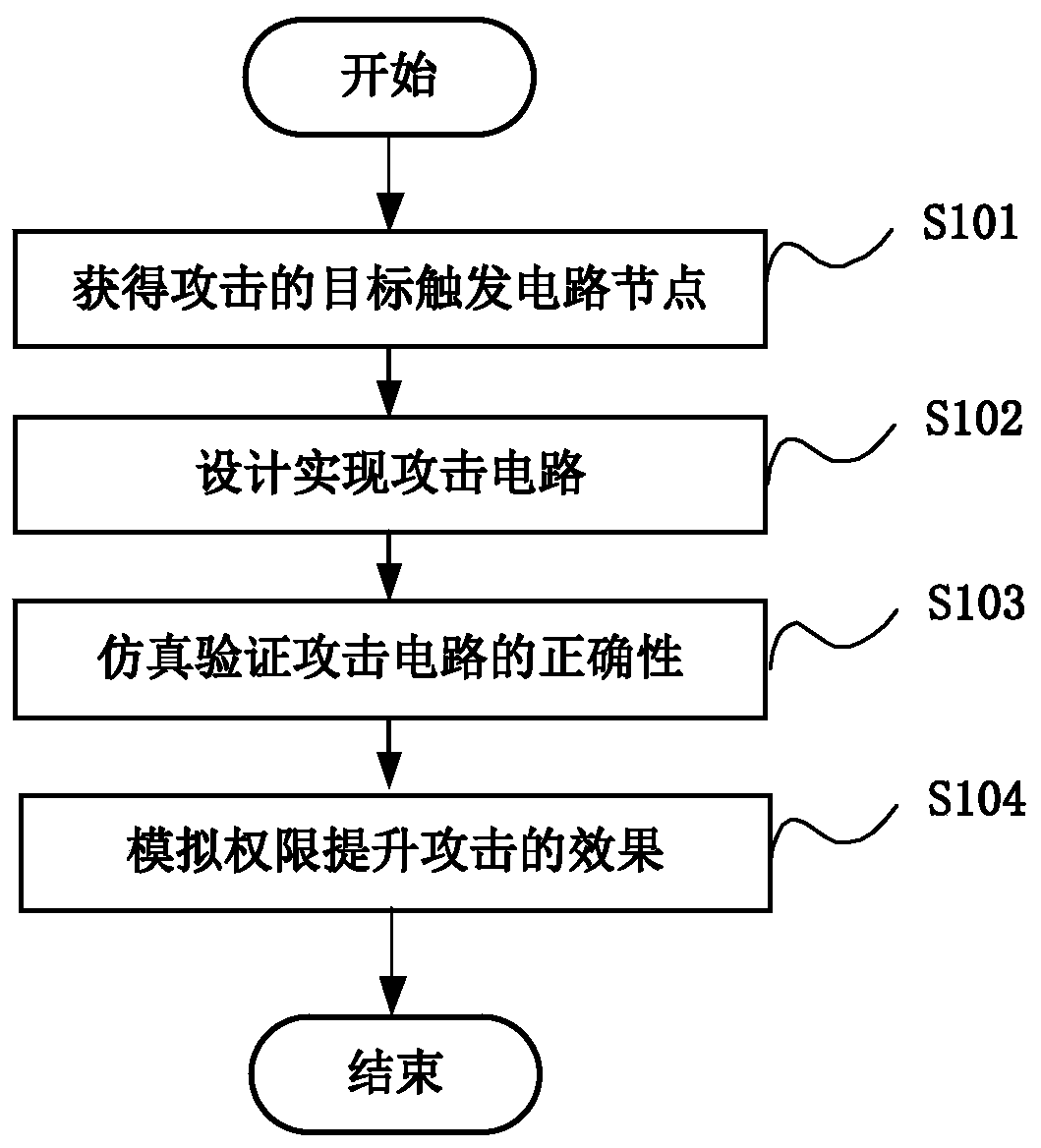
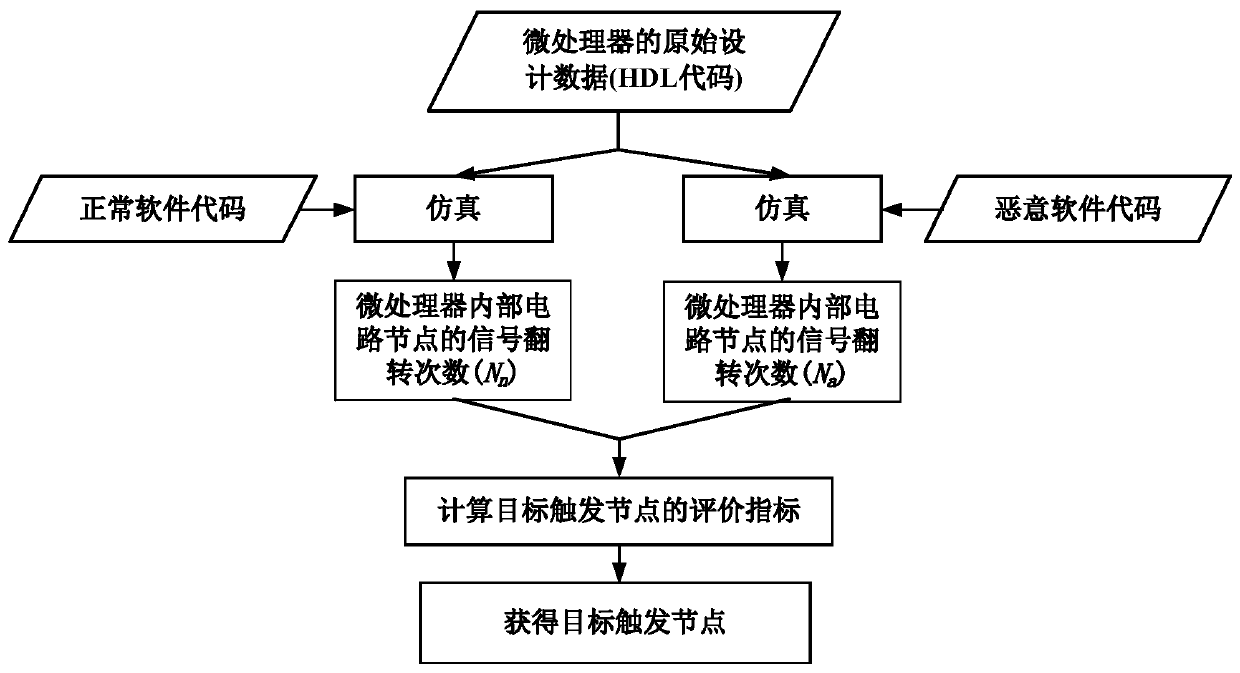
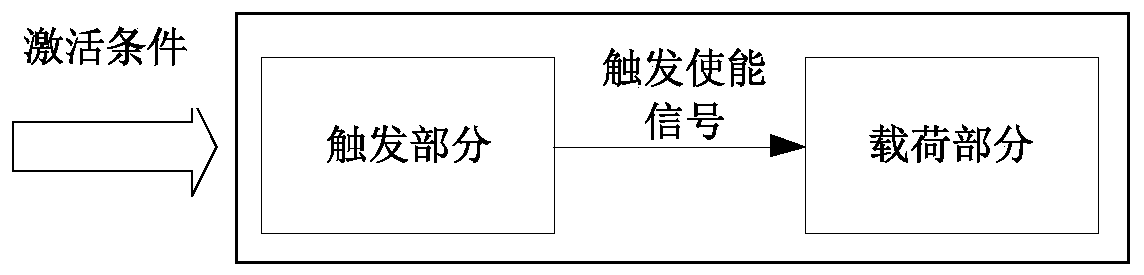
[0014] A microprocessor privilege escalation attack simulation method of an embodiment of the present invention firstly obtains the target trigger of the attack by simulating the original design data of the microprocessor, such as the original design HDL (Hardware Description Language, hardware description language) code. Circuit node; then design and realize the attack circuit at the circuit node; then use simulation or FPGA (Field Programmable Gate Array, Field Programmable Gate Array) to verify the correctness of the attack circuit function; finally use the above attack circuit to simulate the effect of privilege escalation attack , so as to detect and evaluate the ability of anti-privilege-escalation atta...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com