A data deterministic deletion method based on inversion of random positions of data blocks
A random position and deletion method technology, which is applied in the direction of electrical digital data processing, computer security devices, serial/continuous modification of data streams, etc., can solve the problems that attackers are not easy to obtain keys, huge overhead, and no small storage pressure , to achieve the effect of reducing data leakage, reducing possibility, and reducing overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
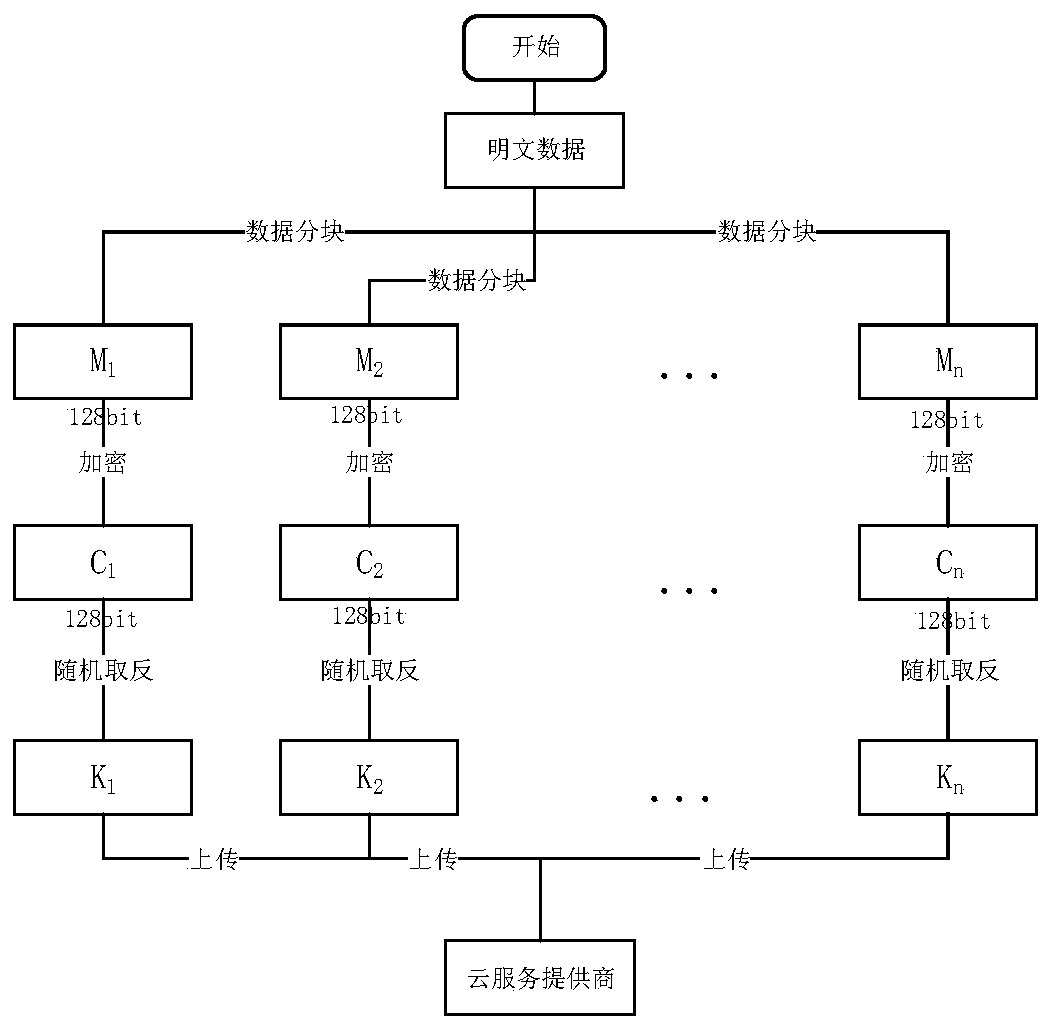
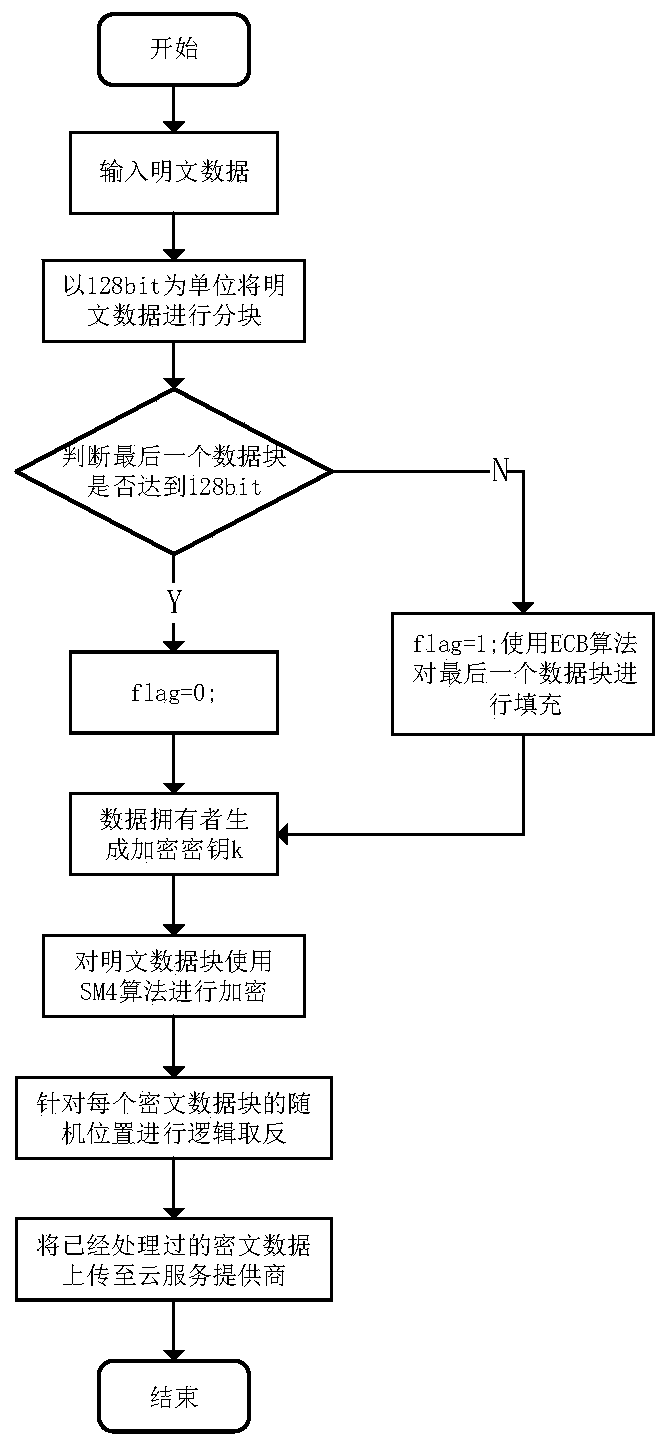
[0045] The following describes the data access process in the present invention in more detail in conjunction with the accompanying drawings:
[0046] In the present invention, the data access process is divided into four stages: data block stage, encrypted upload stage, legal user data access stage and data owner deletion stage.
[0047] (1) In the system data plaintext data {M}, the data owner uses the Data(M) algorithm to block the plaintext data to obtain n plaintext data blocks {M i}.
[0048] (2) Each data block is 128 bits, and when the last block is less than 128 bits, it is filled with 0.
[0049] (3) A flag is introduced to record whether to perform filling operation for the nth data block. If the nth data block is filled with data, the flag value is set to 1, otherwise it is set to 0.
[0050] (4) The data owner generates the key k required for encryption.
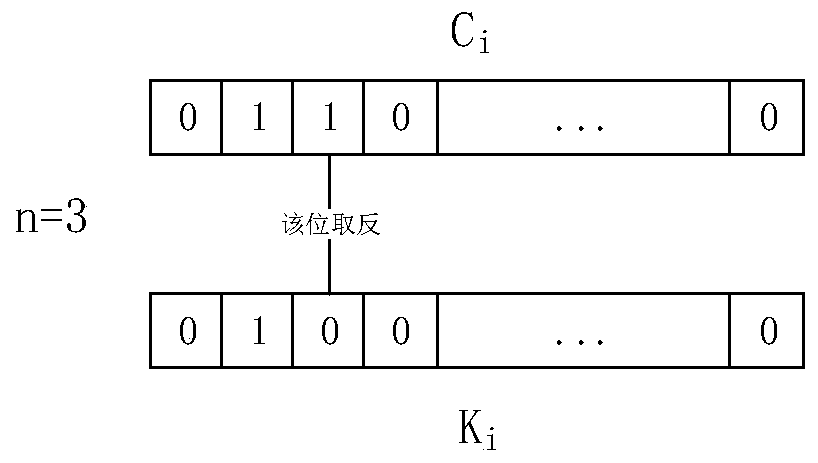
[0051] (5) Encrypt each plaintext data block. The plaintext data block encryption algorithm is expressed a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com