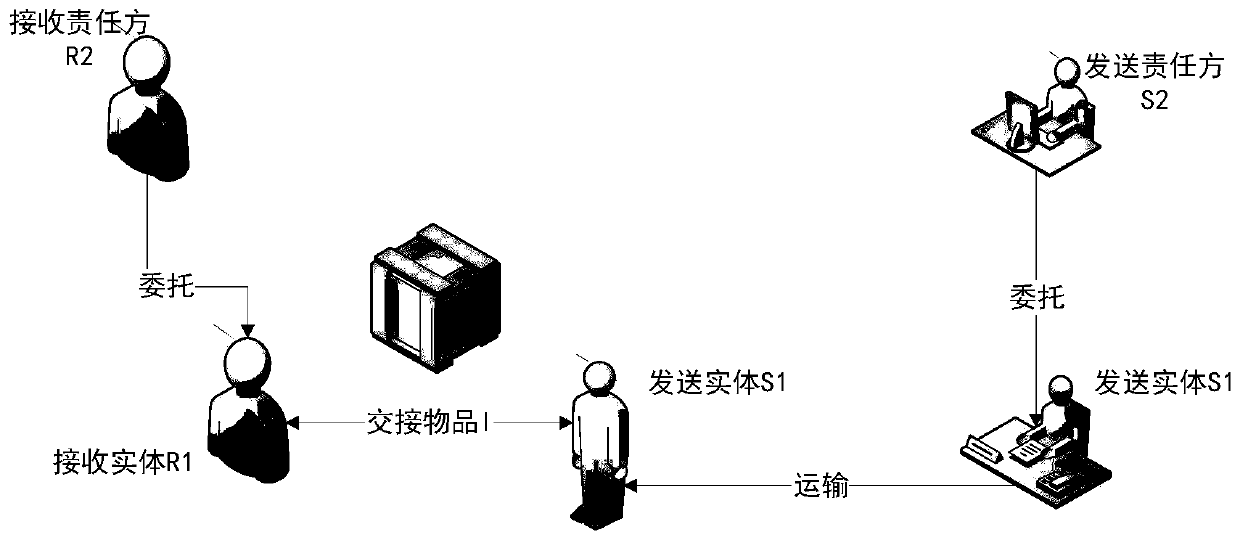
An intelligent item interaction system and method applied to the entrance of private space
A private space and smart item technology, applied in the field of smart item interaction system, can solve problems such as signing for items and difficulty in meeting the reliability requirements of item interaction
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach
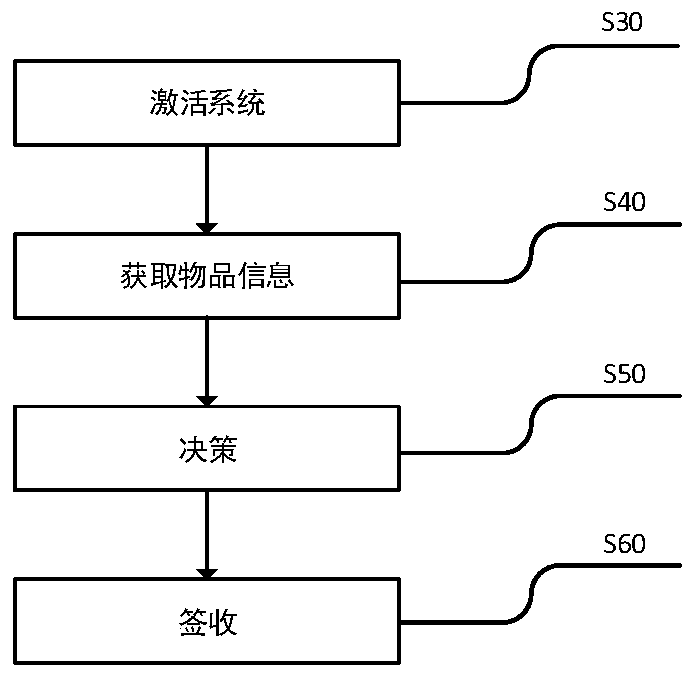
[0083] image 3 A flow chart of the method is provided for the present invention. Such as Figure 4 Shown, the embodiment of the inventive method is as follows:
[0084] S30. Activate the system. In order for an interaction to be accountable, the entity that can successfully activate the system must be accountable.
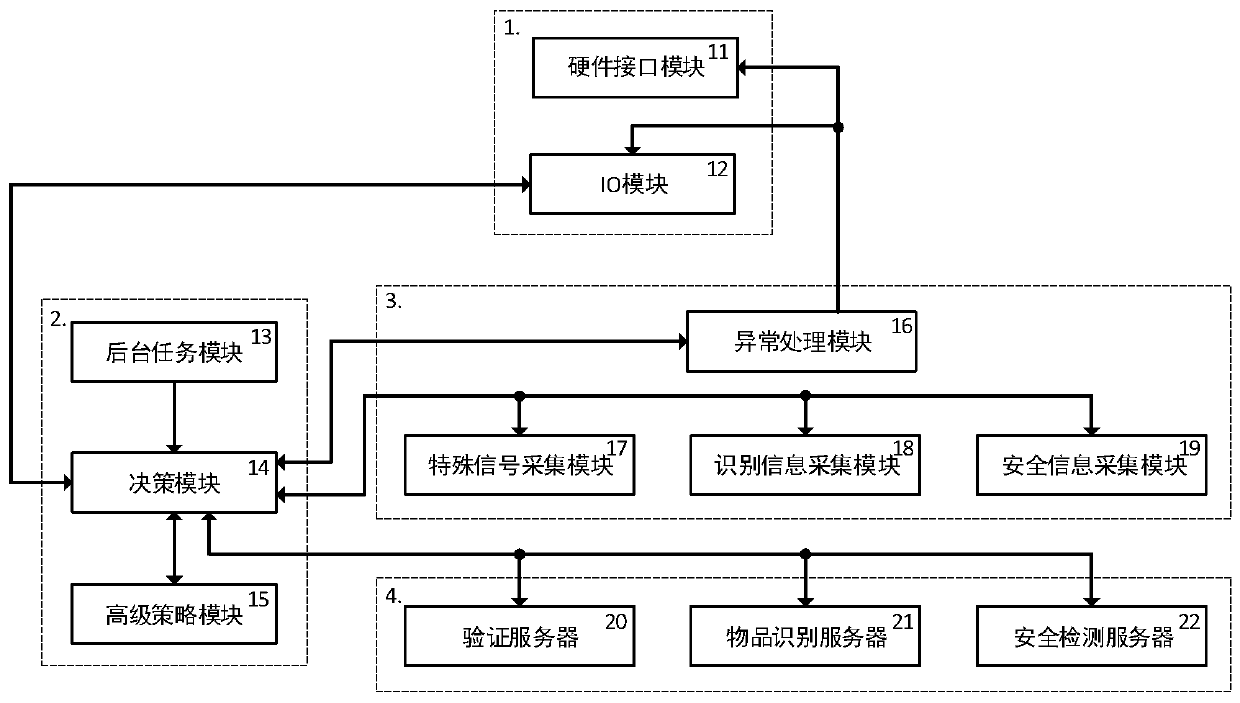
[0085] S301. At the beginning, S1 uses its ID information (which can be fingerprint, face, barcode, etc.) to try to activate the system through the IO module 12, and the IO module 12 provides corresponding software and hardware interfaces. The IO module 12 may also have video input / output, audio input / output and other components for information interaction with S1, such as providing an active interrupt button, which will enter the interactive interrupt process after pressing the key, and the interactive interrupt process may include displaying Cause of outage, delivery report, system recovery, etc.
[0086] S302. Identity verification. The IO module 12 reads...
example 1
[0097] S502. Implement a strategy. According to the above assumptions in the information analysis stage, a strategy can be drawn up: in a certain interaction, if and only if the interaction has logical security, the interacted item I has the security of the source of the item, and the item I itself has security . When the item identification and verification is passed, the interaction has the security of the interaction process, and the security of each aspect reaches a certain threshold, the sign-in will be implemented; otherwise, the item interaction will be interrupted, the reason for the interruption of the interaction will be displayed, and the corresponding interruption of the interaction will be processed. In this interaction interruption process, the decision-making module 14 can first send a report to R2, and if R2 modifies the decision-making result to sign-in through the interface provided by the advanced policy module 15 within a certain period of time, then turn to...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com