A vehicle network RFID security authentication method based on key distribution center
A technology of key distribution center and security authentication, which is applied in the field of vehicle network RFID security certification based on the key distribution center, can solve problems such as insecure channel communication of the vehicle network RFID system, background server DoS attack, etc., to prevent forward security performance, preventing tracking attacks, and preventing retransmission attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
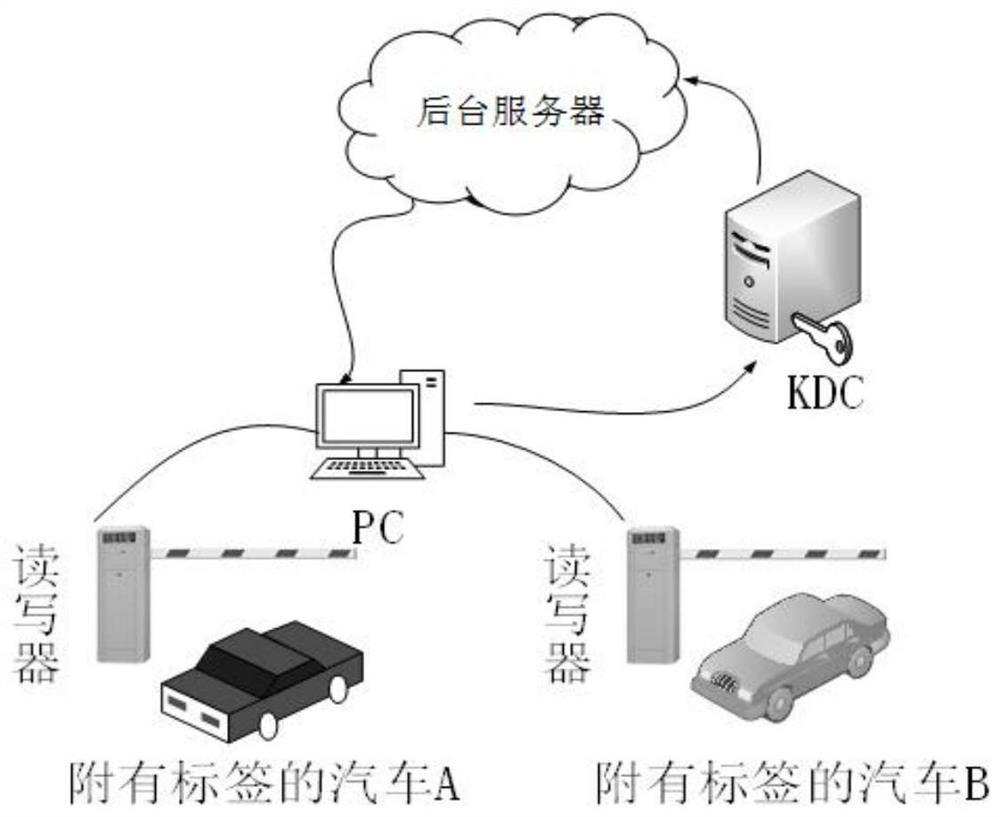
[0046] Such as figure 2 As shown, in the parking lot toll station scenario, the RFID security authentication method for the Internet of Vehicles based on the key distribution center, specifically.
[0047] A. Initialization
[0048] Each tag stores its ID i As its unique identity, the ID i Assigned by the background server, that is, only the tag and the back server share the ID i . id r It is the ID of the reader, and is shared by the reader and the background server. k i,j Represents identity as ID i The private key of the j-th session of the label is allocated and shared by the KDC. After each session is completed, the KDC and the label update the private key synchronously. KDC is the key distribution center, which stores a key authorization list L, when KDC receives the random number r sent by the reader r When , first combine the stored key authorization list L with the random number r r Perform the operation, and then refresh the key authorization list L. Befo...
Embodiment 2
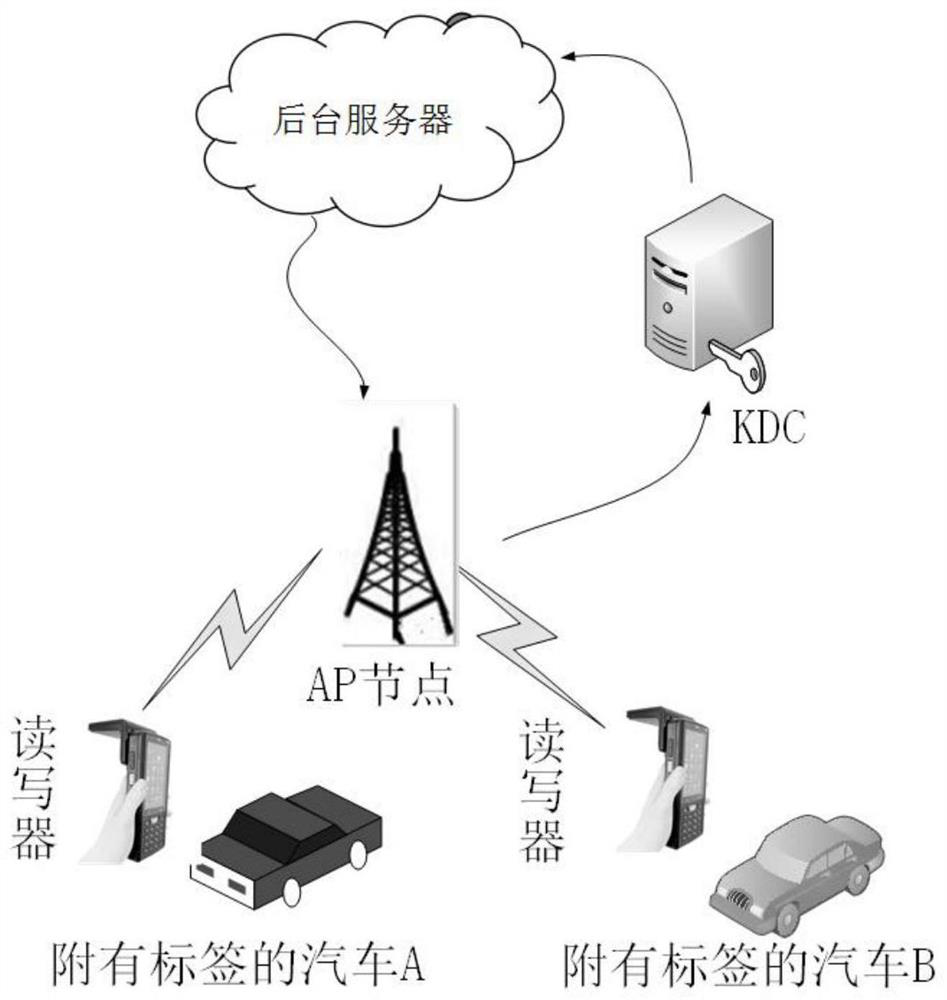
[0067] Such as image 3 As shown, in the mobile identification, the vehicle network RFID security authentication method based on the key distribution center, specifically.
[0068] A. Initialization
[0069] Each tag stores its ID i As its unique identity, the ID i Assigned by the background server, that is, only the tag and the back server share the ID i . id r It is the ID of the reader, and is shared by the reader and the background server. k i,j Represents identity as ID i The private key of the j-th session of the label is allocated and shared by the KDC. After each session is completed, the KDC and the label update the private key synchronously. KDC is the key distribution center, which stores a key authorization list L, when KDC receives the random number r sent by the reader r When , first combine the stored key authorization list L with the random number r r Perform the operation, and then refresh the key authorization list L. Before the tag can communicate...
Embodiment 3
[0086] Such as Figure 4 As shown, in the vehicle-road coupling system, the RFID security authentication method for the Internet of Vehicles based on the key distribution center, specifically.
[0087] A. Initialization
[0088] Each tag stores its ID i As its unique identity, the ID i Assigned by the background server, that is, only the tag and the back server share the ID i . id r It is the ID of the reader, and is shared by the reader and the background server. k i,j Represents identity as ID i The private key of the j-th session of the label is allocated and shared by the KDC. After each session is completed, the KDC and the label update the private key synchronously. KDC is the key distribution center, which stores a key authorization list L, when KDC receives the random number r sent by the reader r , first combine the stored list with the random number r r Perform the operation, and then refresh the key authorization list L. Before the tag can communicate wit...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com