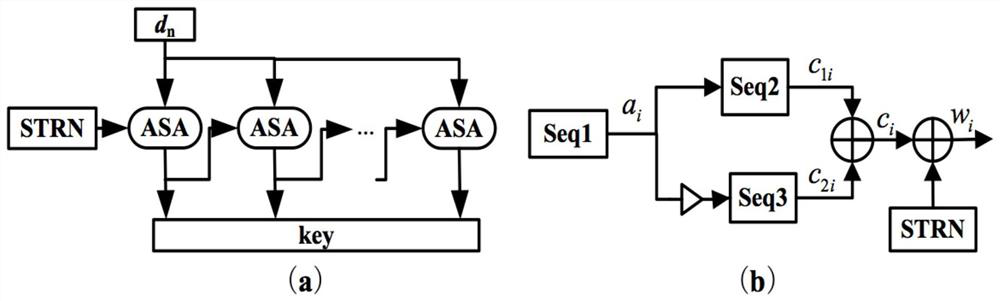
A chaotic security key distribution method and system based on post-processing
A security key and distribution system technology, which is applied in the field of secure communication systems, can solve problems such as limiting the rate of synchronous random number generation, and achieve the effects of increasing the difficulty of eavesdropping, ensuring security, and increasing the output rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
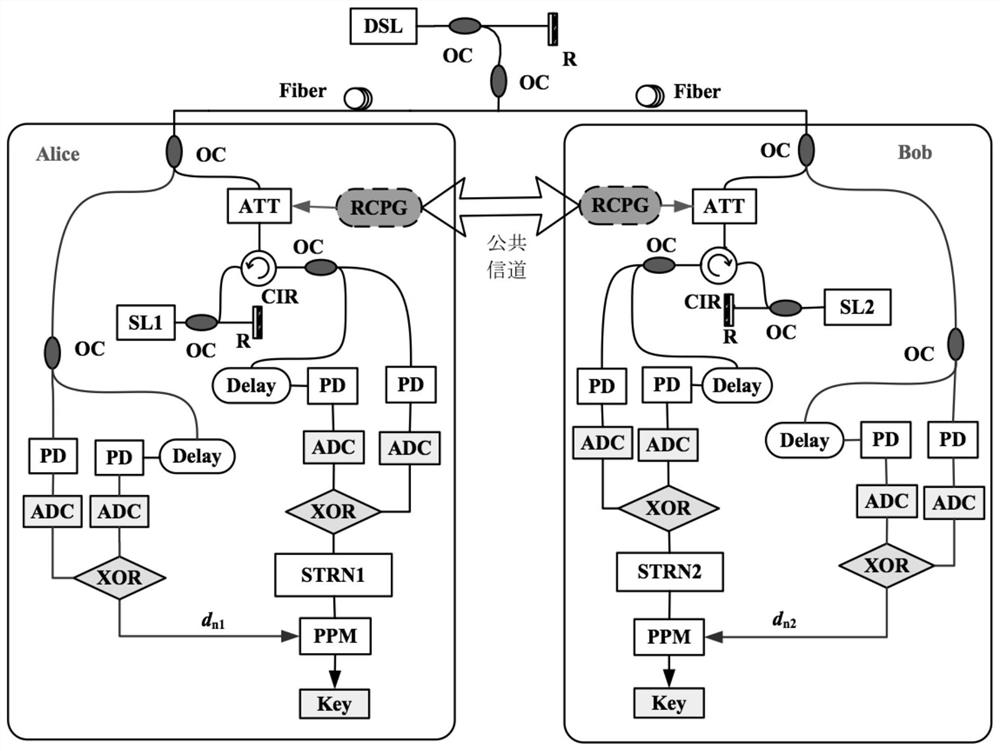
[0050] The present invention is further described below.
[0051] DSL works around 1550nm, and the frequency deviation from SL1 / 2 is 10GHz. The threshold current of both DSL and SLs is I th =14.7mA, the working current is 2I th and 1.5I th , the feedback time and strength of DSL are 3ns and 10ns respectively -1 , the delay of DSL injection to SLs is 0ns (assumed), and the feedback time and intensity of SL1 / 2 itself are 2ns and 5ns respectively -1 . Both the sender and the receiver sample the timing signals output by SL1 and SL2 at a sampling frequency of 2GHz.
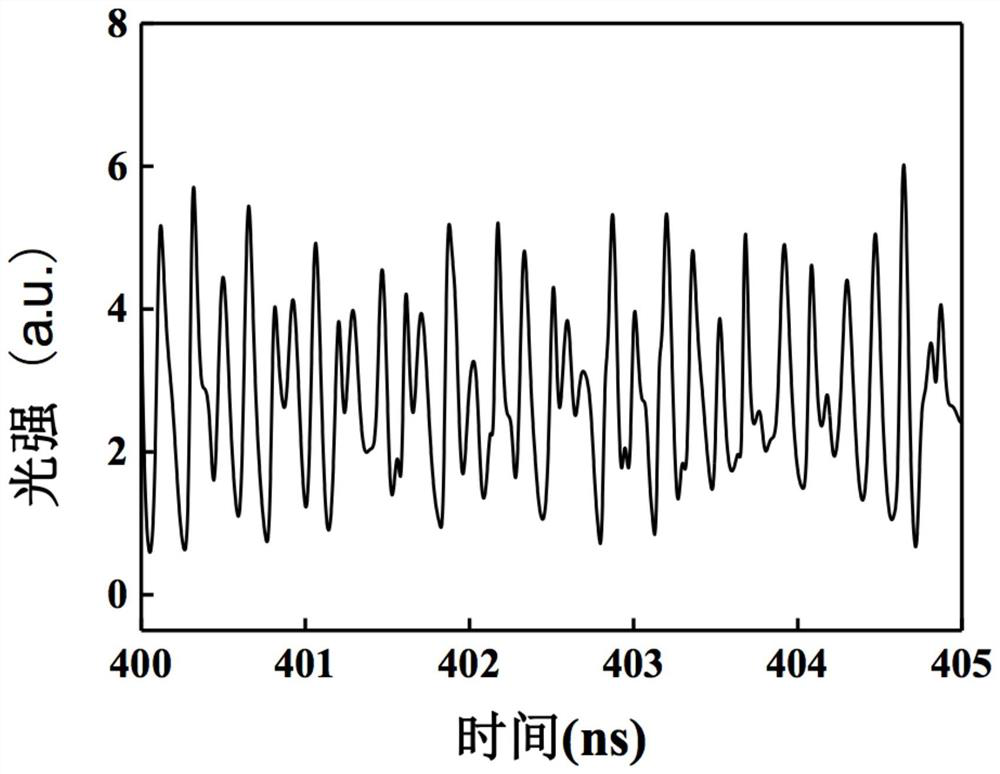
[0052] image 3 is the initial chaotic laser signal generated by DSL under the action of external cavity feedback.
[0053] Figure 4 is the injection intensity k in =40ns -1 When , the chaotic laser signal generated by SL1, Figure 5 is the injection intensity k in =40ns -1, the chaotic laser signal generated by SL2 can be seen from the figure, the output timing signals of SL1 and SL2 have the same dynami...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com