A cloud platform and platform operation method for docking a quantum computer with a user
A quantum computer and operating method technology, applied in the field of quantum computing, can solve problems such as difficult popularization, incompatibility, and harsh operating environment of quantum computers, and achieve the effect of increasing computing efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
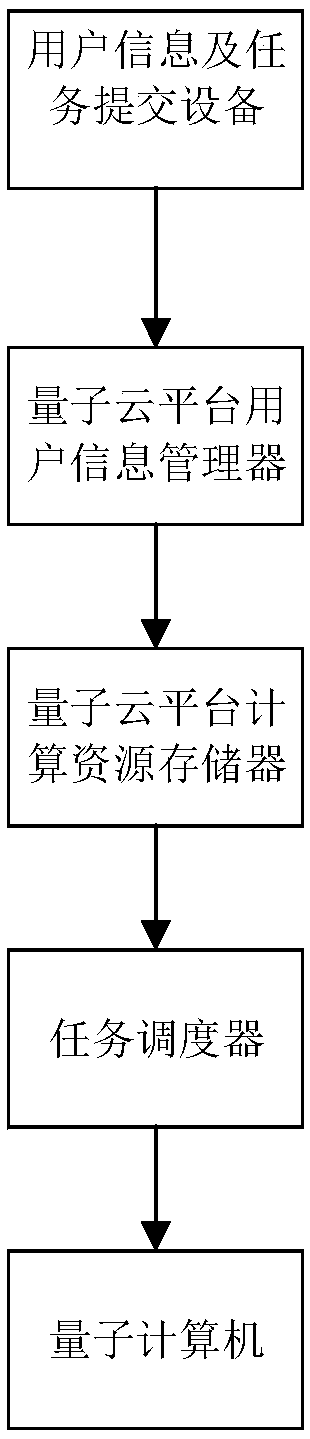
[0049] This solution proposes a cloud platform for connecting quantum computers and users, including sequentially connected user information and task interface modules, quantum cloud platform user information managers, quantum cloud platform computing resource storage, task schedulers, and quantum computers . Such as figure 1 The overall structure diagram of the quantum cloud platform system shown, each module operates independently, and the communication between each module is in the form agreed within the system. For example, the user information and task interface module and the quantum cloud platform user information manager can use the HTTPS protocol for communication;
[0050] The user information and task interface module is connected to the user equipment, the user equipment is used to submit user information and calculation tasks, the user information and task interface module is used to receive the user information and calculation tasks submitted by the user equipme...
Embodiment 2
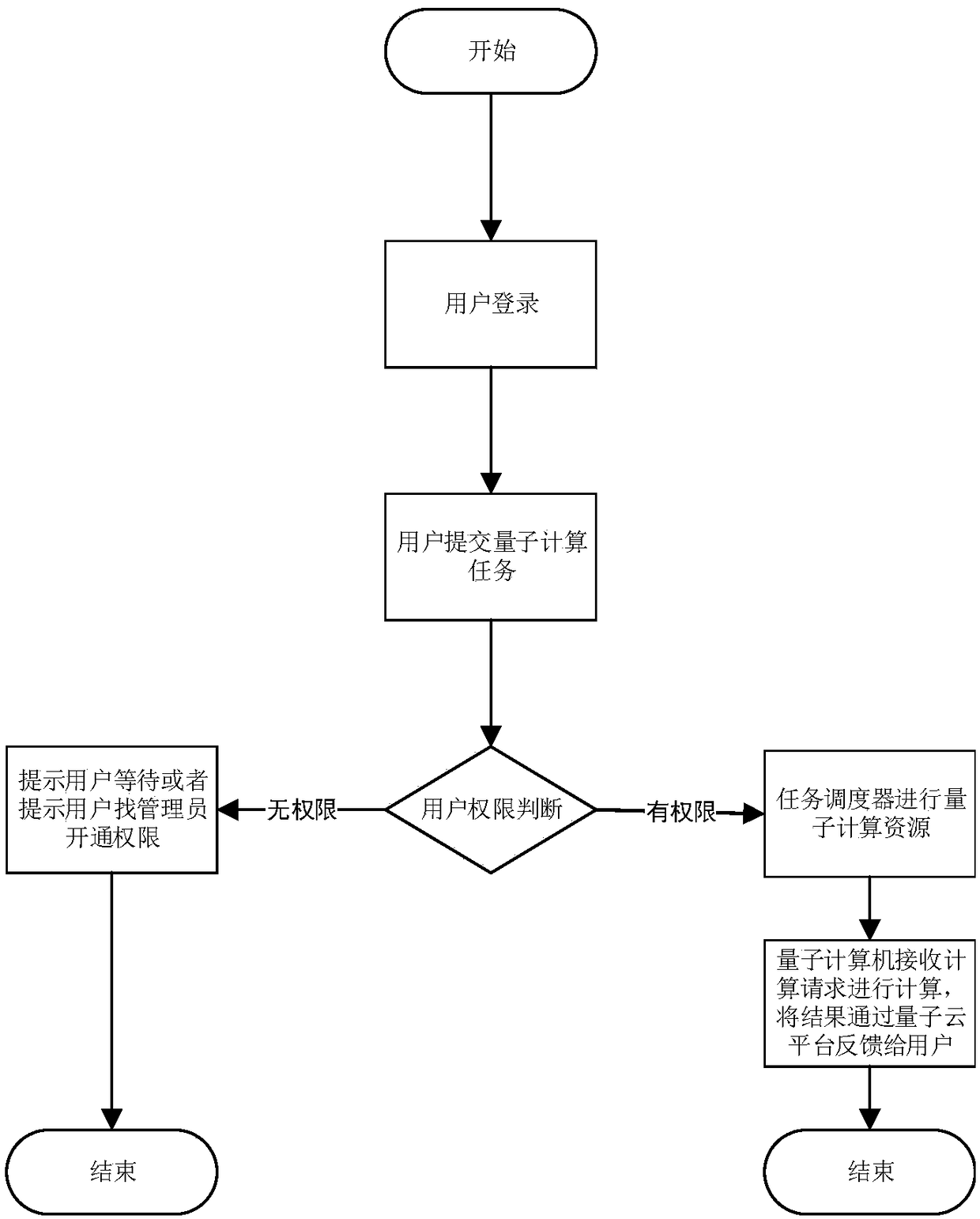
[0058] Such as figure 2 As shown in , it shows a running method of the cloud platform for docking quantum computers and users, and the steps are as follows:
[0059] Step 1, the user logs in, and the user requests identity authentication from the cloud platform through a browser, where the browser is the user information and task interface module, and the cloud platform queries relevant data through the quantum cloud platform user information manager to authenticate the data sent Whether the user has login authority, if not prompted to register as a new user.
[0060] The identity authentication described in step 1 refers to the desensitization of sensitive information such as the user’s unique identity logo, user name, and password before submitting the data to ensure the security of the user’s transmitted information. The authentication background is based on the agreed encryption and decryption algorithm. For decryption, the corresponding desensitization and decryption me...
Embodiment 3
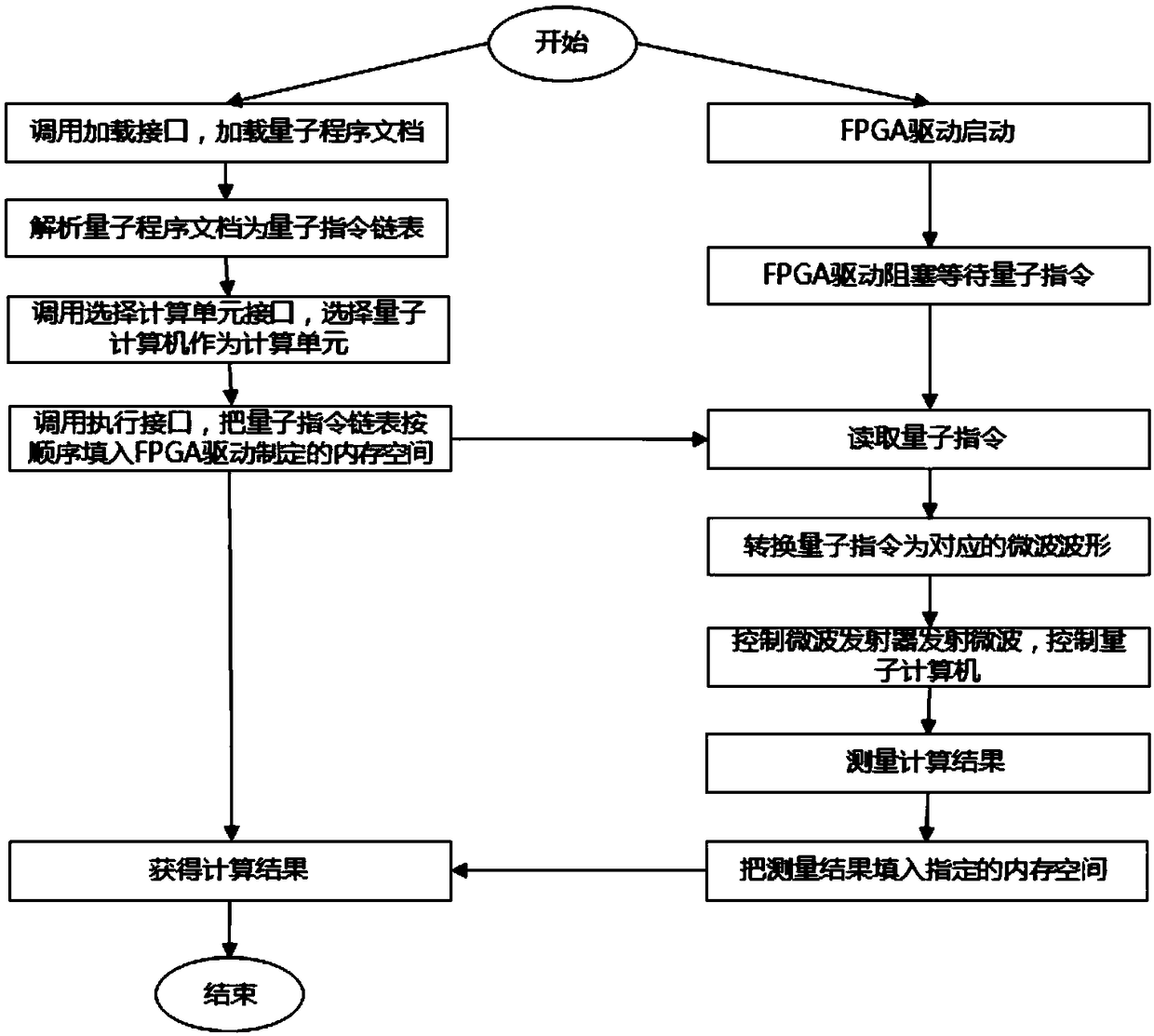
[0066] Such as image 3 As shown, in order to facilitate developers to use ordinary computers for code input without quantum computers, and after the development of quantum programs is completed, they can be reused to quantum computers without modification. The user information and task interface module includes an external interface module, and the external interface module is connected to the quantum computer.
[0067]The external interface module includes: loading interface, connected with the external traditional computer system, loading the quantum program input by the traditional ordinary computer corresponding to the input of the external computer user equipment; the interface system analysis module, analyzing the quantum program as a quantum instruction linked list, and analyzing the quantum program; The program consists of a quantum instruction set, which corresponds to various quantum logic gates. The interface system analysis module will analyze the quantum program...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com