Data encryption method, system and terminal in transaction process
A technology of data encryption and encryption, applied in the field of data security, can solve the problems of data leakage, data security, hidden dangers, etc., and achieve the effect of reducing the scope of assessment, reducing the workload and cost of security certification, and reducing the workload of development
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
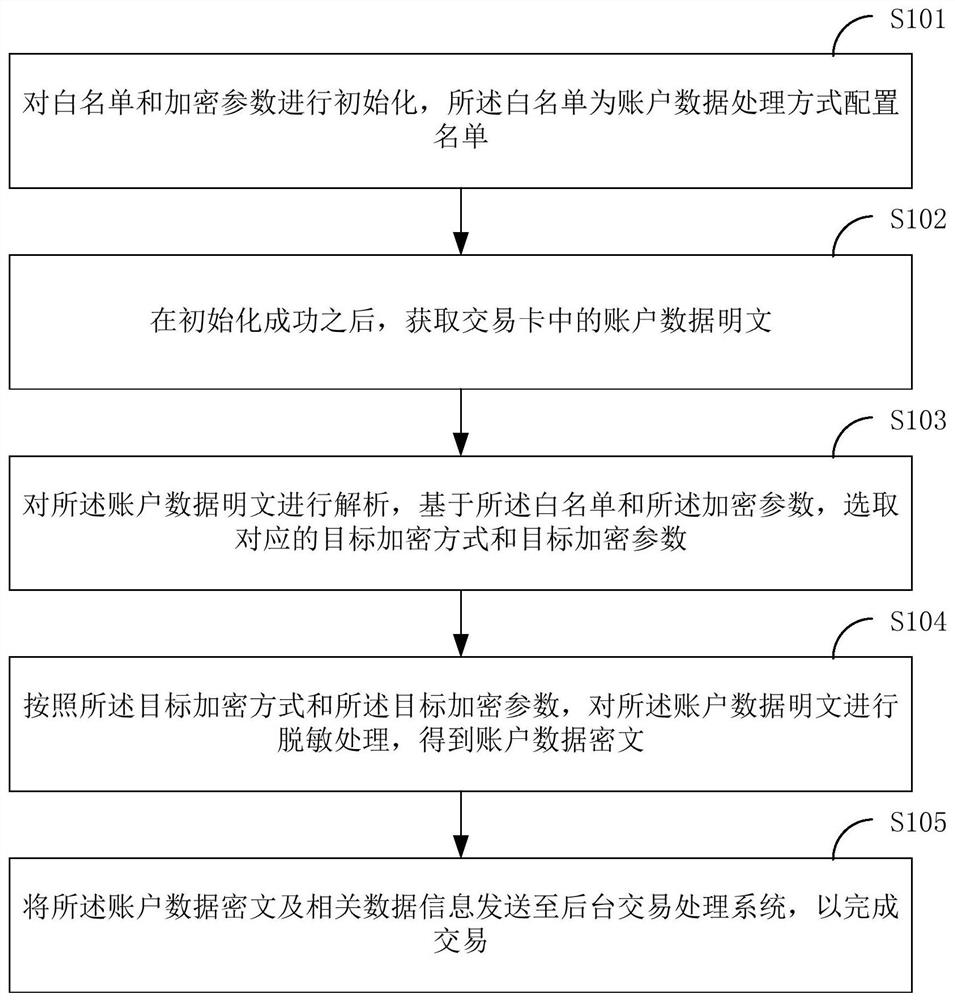
[0029] figure 1 It shows an implementation process of a data encryption method in a transaction process provided by an embodiment of the present invention, and the subject of execution of the process in this embodiment may be a terminal, such as a POS terminal.
[0030] Such as figure 1 As shown, a data encryption method in a transaction process provided by an embodiment of the present invention includes:
[0031] In step S101, a white list and encryption parameters are initialized, and the white list is a list for configuring account data processing methods.
[0032] In this embodiment, after the whitelist is established and before the account data in the transaction card is processed, the process of initializing the whitelist (namely, the account data processing mode configuration list) and encryption parameters is completed. After the initialization is successful, step S102 can be executed to obtain the plaintext of the account data. If the initialization of the whitelis...
Embodiment 2
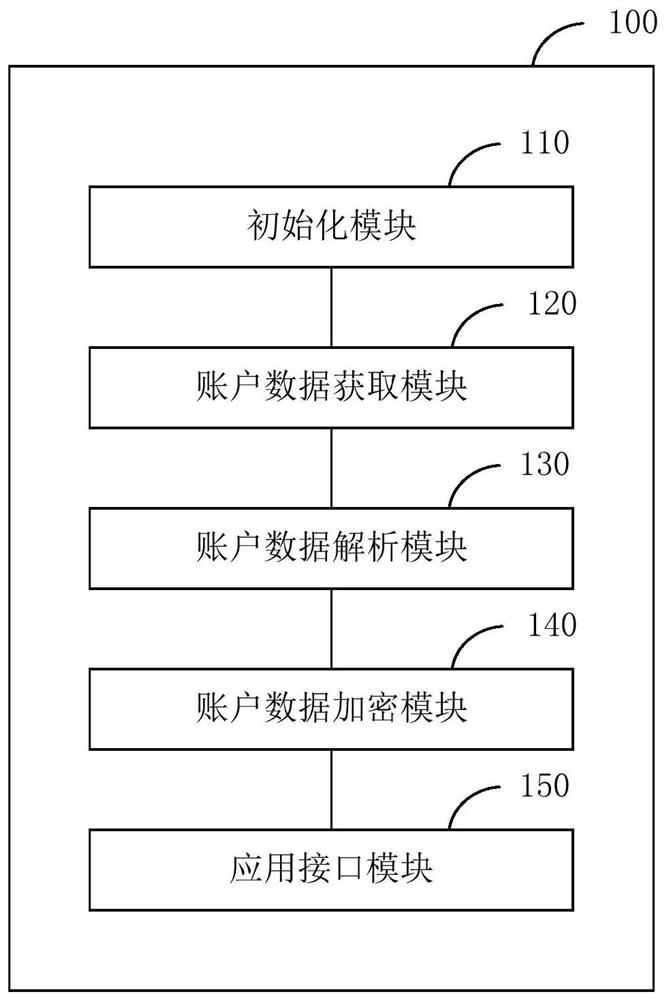
[0083] Such as image 3 As shown, the data encryption system 100 in the transaction process provided by an embodiment of the present invention is used to perform figure 1 The method step in the corresponding embodiment, it comprises:
[0084] The initialization module 110 is configured to initialize a white list and encryption parameters, the white list is a configuration list of account data processing methods.
[0085] The account data obtaining module 120 is configured to obtain the clear text of the account data in the transaction card after the initialization is successful.
[0086] The account data analysis module 130 is configured to analyze the plaintext of the account data, and select a corresponding target encryption method and target encryption parameters based on the white list and the encryption parameters.
[0087] The account data encryption module 140 is configured to desensitize the plaintext of the account data according to the target encryption method and ...
Embodiment 3
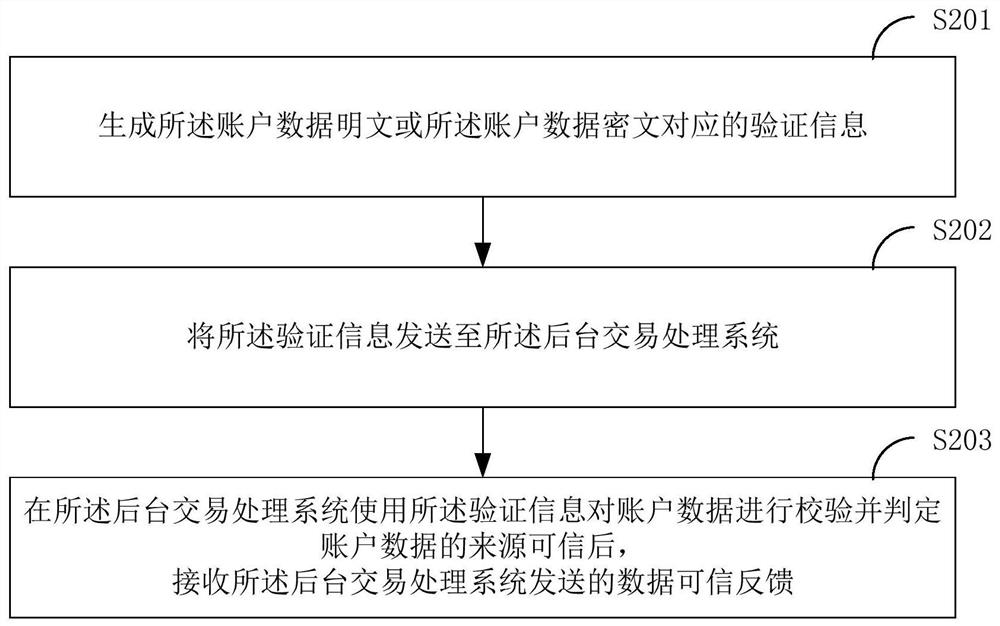
[0103] Figure 4 It is a schematic diagram of a terminal provided by an embodiment of the present invention. Such as Figure 4 As shown, the terminal 4 in this embodiment includes: a processor 40 , a memory 41 and a computer program 42 stored in the memory 41 and executable on the processor 40 . When the processor 40 executes the computer program 42, it realizes the steps in each embodiment as described in Embodiment 1, for example figure 1 Steps S101 to S105 are shown. Alternatively, when the processor 40 executes the computer program 42, it realizes the functions of each module / unit in each system embodiment as described in Embodiment 2, for example image 3 The functions of the modules 110 to 150 are shown.
[0104] The terminal 4 refers to a terminal with data processing capabilities, including but not limited to POS terminals, computers, workstations, and even smart phones with excellent performance, palmtop computers, tablet computers, personal digital assistants (PD...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com