Anomaly Detection Method for Integrated Electronic System Based on Deep Packet Analysis
A technology that integrates electronic systems and deep packet analysis. It is applied in transmission systems, digital transmission systems, electrical components, etc., and can solve problems such as less consideration of safety design, low memory and low CPU frequency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] The present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments. The process, conditions, experimental methods, etc. for implementing the present invention, except for the content specifically mentioned below, are common knowledge and common knowledge in this field, and the present invention has no special limitation content.
[0035] The implication that relevant technical term represents among the present invention is as follows:
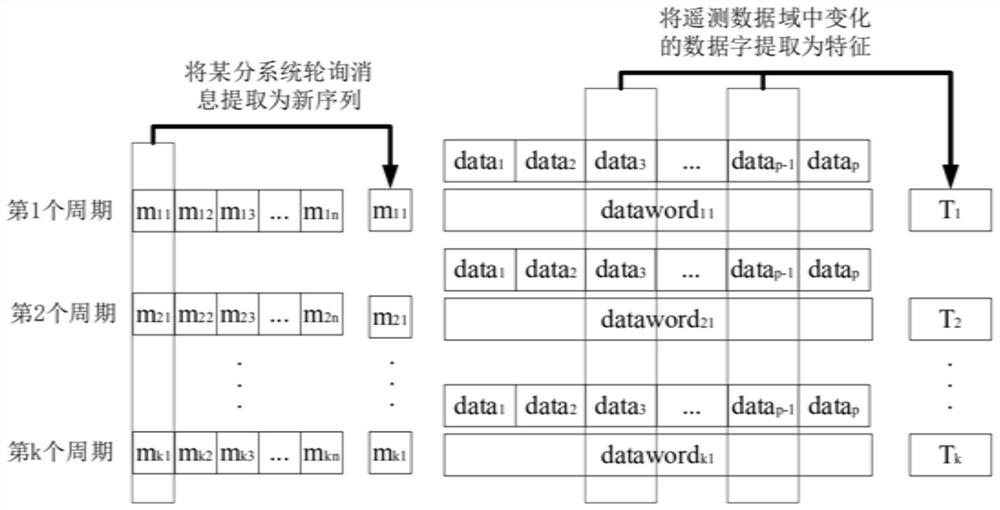
[0036] M represents a complete communication (message) in bus communication;
[0037] m ki Indicates the i-th word of the message of the k-th cycle;
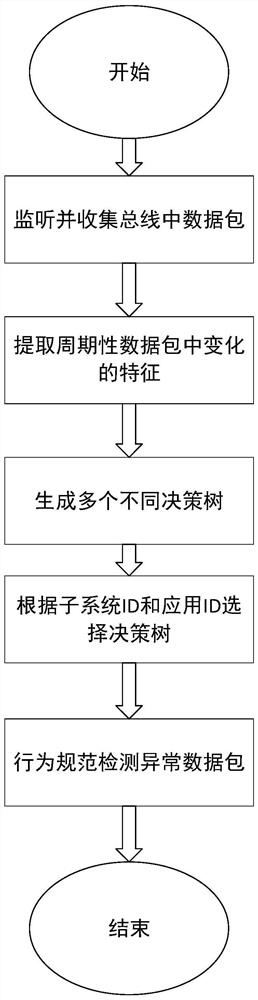
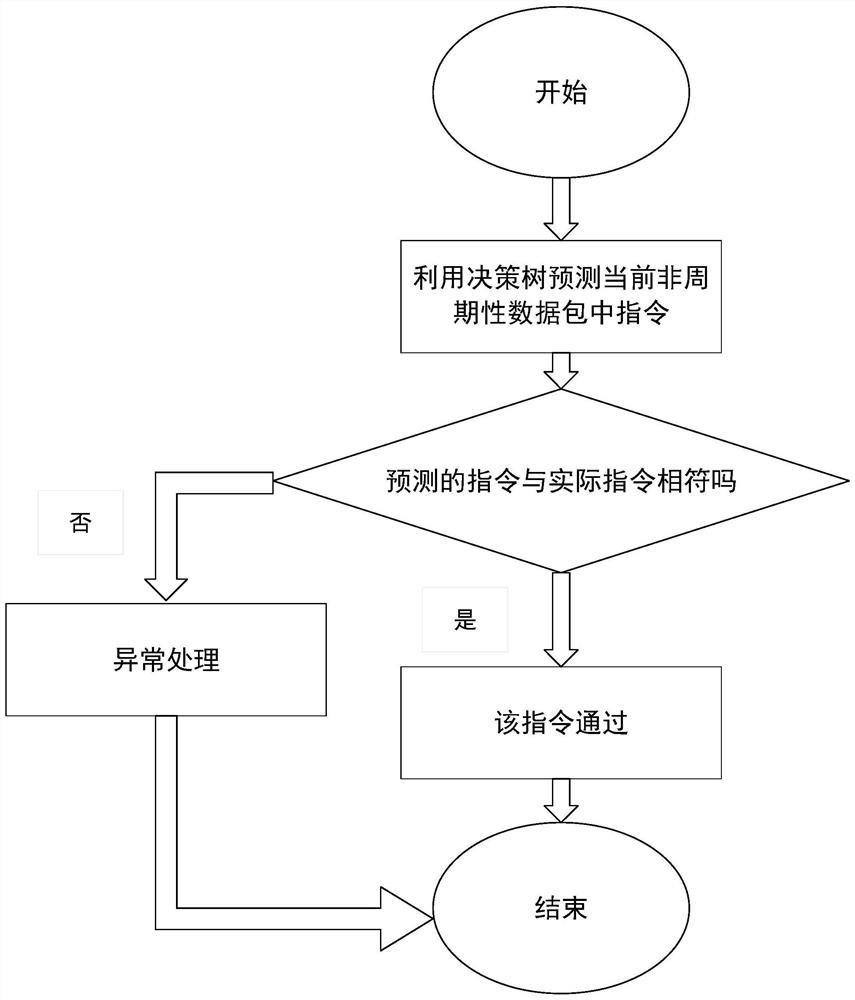
[0038] Such as figure 1 As shown, the present invention is based on the anomaly detection method for integrated electronic systems based on deep packet analysis and includes the following four stages:
[0039] The first stage: collect bus data stage: monitor and collect bus transmission data packets;
[0040] The seco...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com