An integrated circuit for defending hardware Trojan horse and an encryption method thereof
A technology of integrated circuit and encryption method, which is applied in the direction of logic circuit with logic function, internal/peripheral computer component protection, platform integrity maintenance, etc., which can solve excessive timing, area and power consumption overhead, and protection measures are easy to be attacked The problem of cracking by the attacker and sufficient protection of function output can achieve the effect of good encryption effect, resistance to hardware Trojans, and high security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0046] The present invention will be described in further detail below in conjunction with specific examples, but the embodiments of the present invention are not limited thereto.
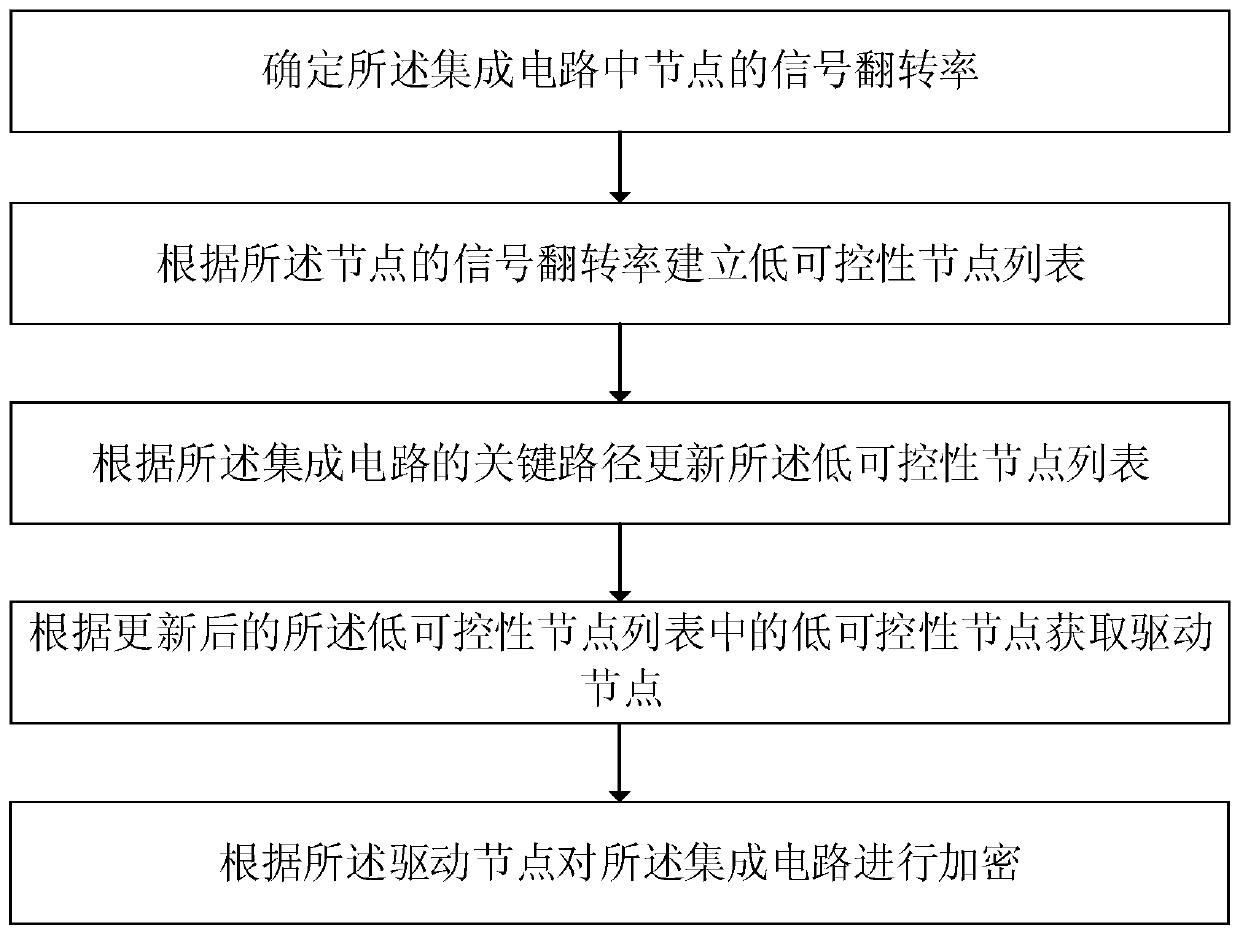
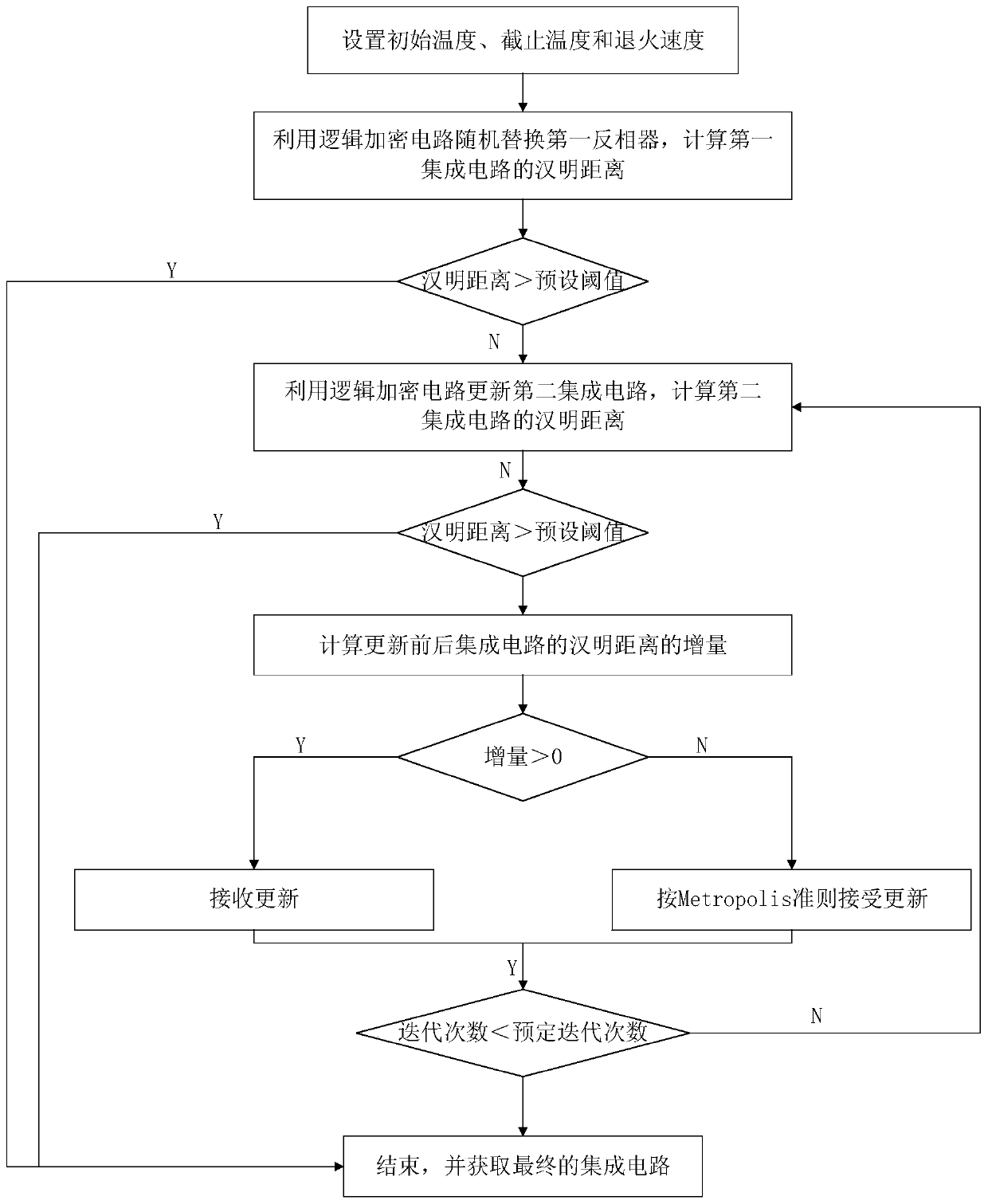
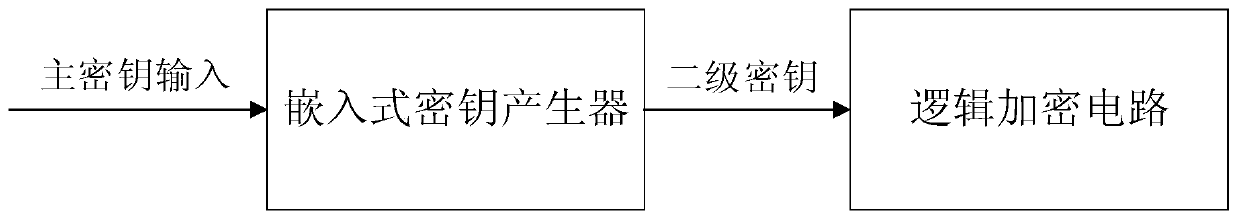
[0047] See figure 1 with figure 2 , figure 1 It is a schematic flowchart of an encryption method for an integrated circuit for defending against hardware Trojan horses provided by an embodiment of the present invention, figure 2 It is a schematic flowchart of another encryption method for an integrated circuit for defending against hardware Trojan horses provided by an embodiment of the present invention. An integrated circuit encryption method for defending against hardware Trojan horses provided by an embodiment of the present invention includes:
[0048] Step 1, using the logic encryption circuit to obtain the first integrated circuit;
[0049] 1.1. Set the three parameters of initial temperature, cut-off temperature and annealing speed;
[0050] In this embodiment, when using the algorit...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com