An industrial control abnormity detection and attack classification method based on deep learning
A deep learning and anomaly detection technology, applied in neural learning methods, neural architectures, biological neural network models, etc., can solve problems such as reduced detection performance, increased computing costs, and inability to detect potential attacks, achieving excellent performance.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0009] The present invention will be described in detail below in conjunction with specific embodiments shown in the accompanying drawings.
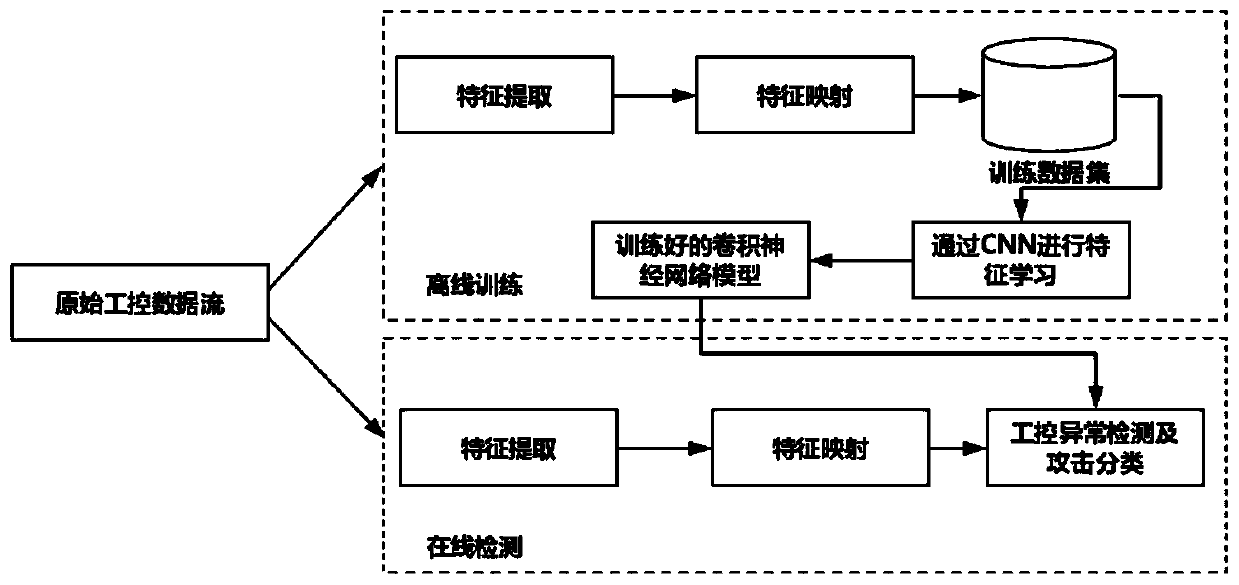
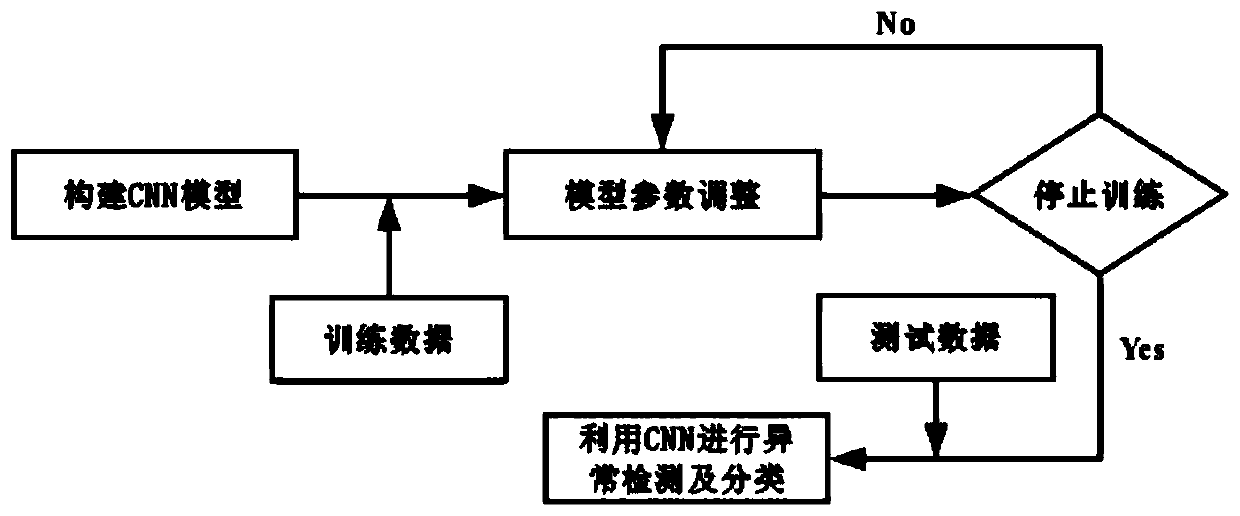
[0010] The overall structure diagram of the abnormality detection and classification method based on deep learning of the present invention is as follows figure 1 shown, including:
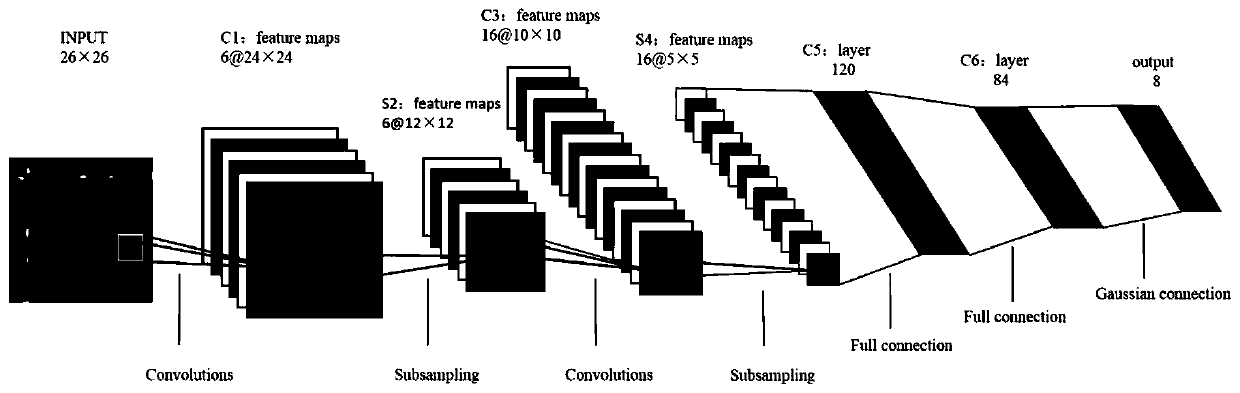
[0011] A feature mapping method for industrial control traffic based on Mahalanobis distance. This method takes into account the actual situation of industrial control systems, and uses the Mahalanobis distance between features for correlation measurement, which can convert the original one-dimensional flow data into a two-dimensional matrix used as the input of the convolutional neural network model.
[0012] Step 1. Put the i-th industrial control network data stream x i Expressed as where m is the number of feature variables contained in each data stream. and Indicates the value of the l-th feature in the i-th industrial control data stream.
[00...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com