Verification processing method and system based on behavior analysis
A behavior analysis and behavior technology, applied in the field of verification code processing, can solve the problems of complex verification code, low defense effect, poor user experience, etc., and achieve the effect of good user experience, reduced operation difficulty, and high cracking difficulty.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
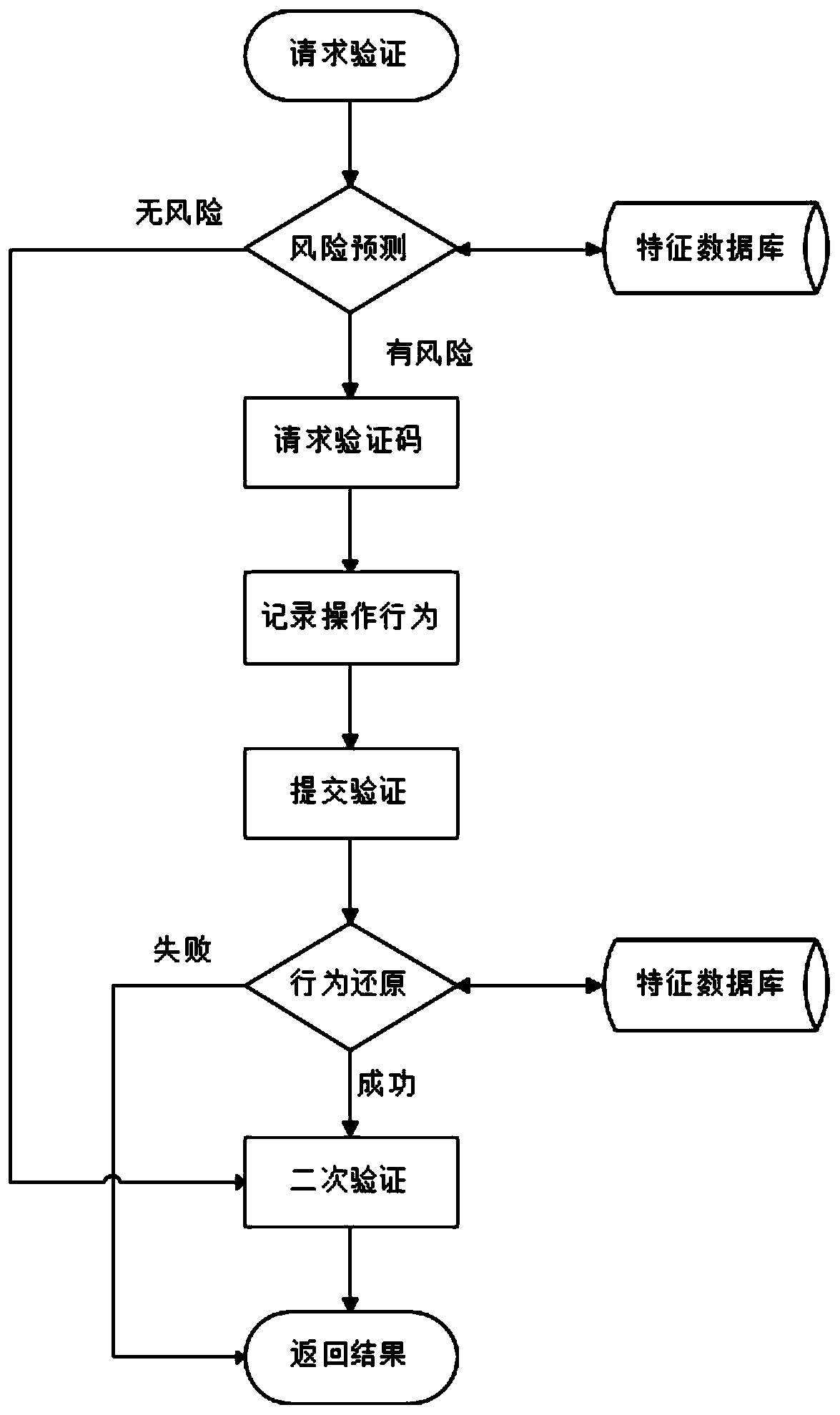
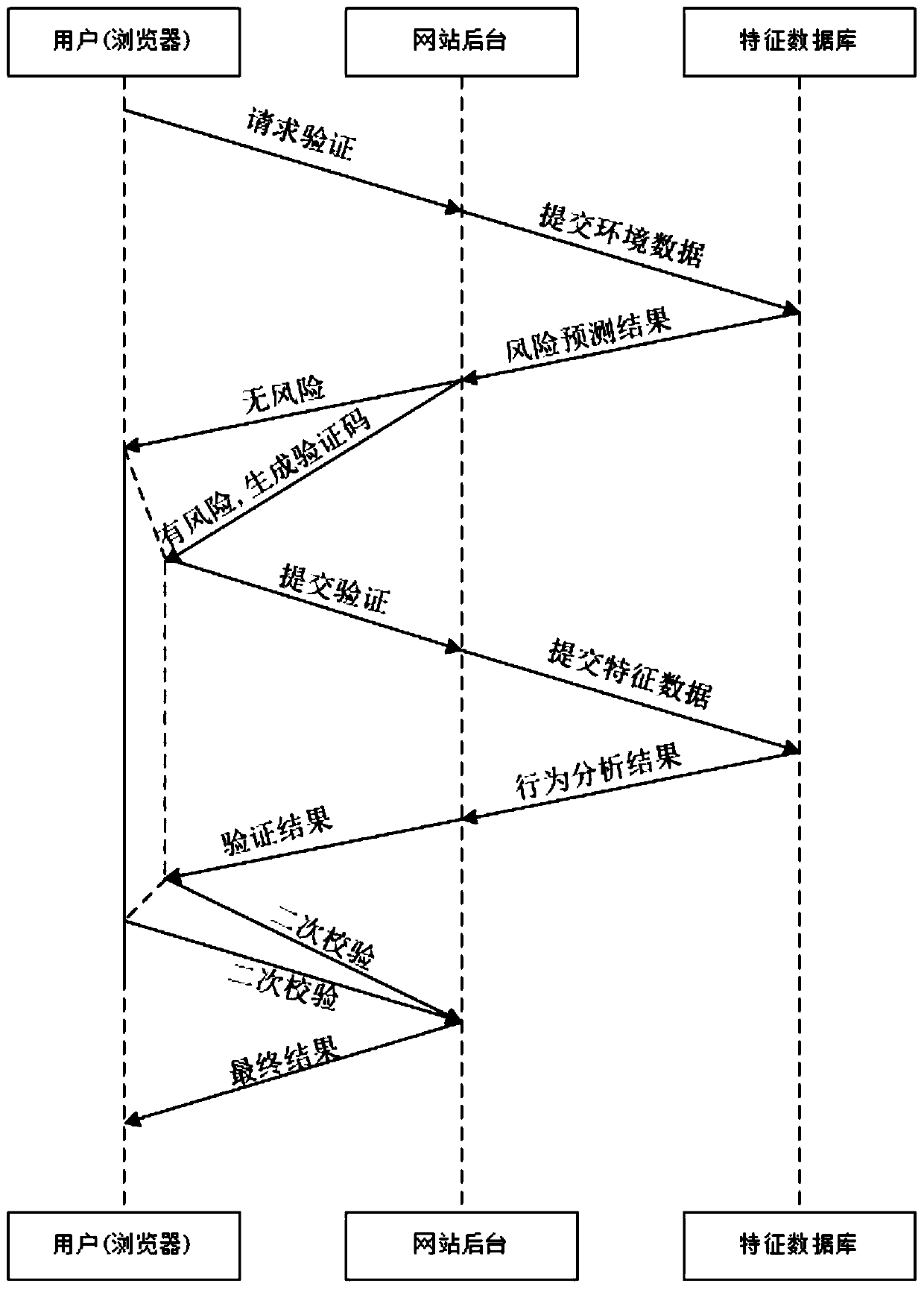
[0034] The present invention provides a verification processing system based on behavior analysis, including a client, a server and a feature database,
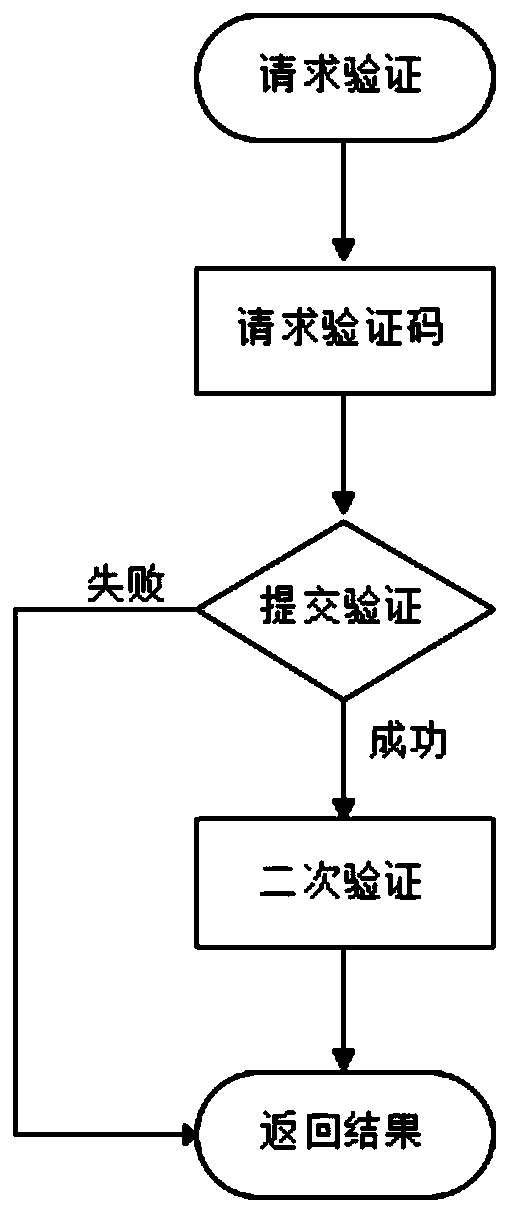
[0035] The client initiates a verification request and sends user environment information to the server, and the server returns the operation behavior verification code to the client.
[0036] The client submits the user verification operation behavior information to the server,
[0037] The server uses the characteristic database to analyze the user's operation behavior, and matches with the human operation characteristic data in the characteristic database. If the matching is successful, it is considered as the user's real operation, and the result information is returned to the client.
[0038] The client initiates a verification request to the server again for secondary verification.
[0039] At the same time, a verification processing method based on behavior analysis corresponding to the above system is provided, and a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com