Method and system for actively cutting off hidden channels to cope with cache side channel attacks
A channel attack, covert channel technology, applied in the direction of inter-program communication, multi-program device, instrument, etc., can solve the problem of not being able to read with malicious system registers, and achieve the effect of flexible implementation, prevention of leakage, and low defense cost.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
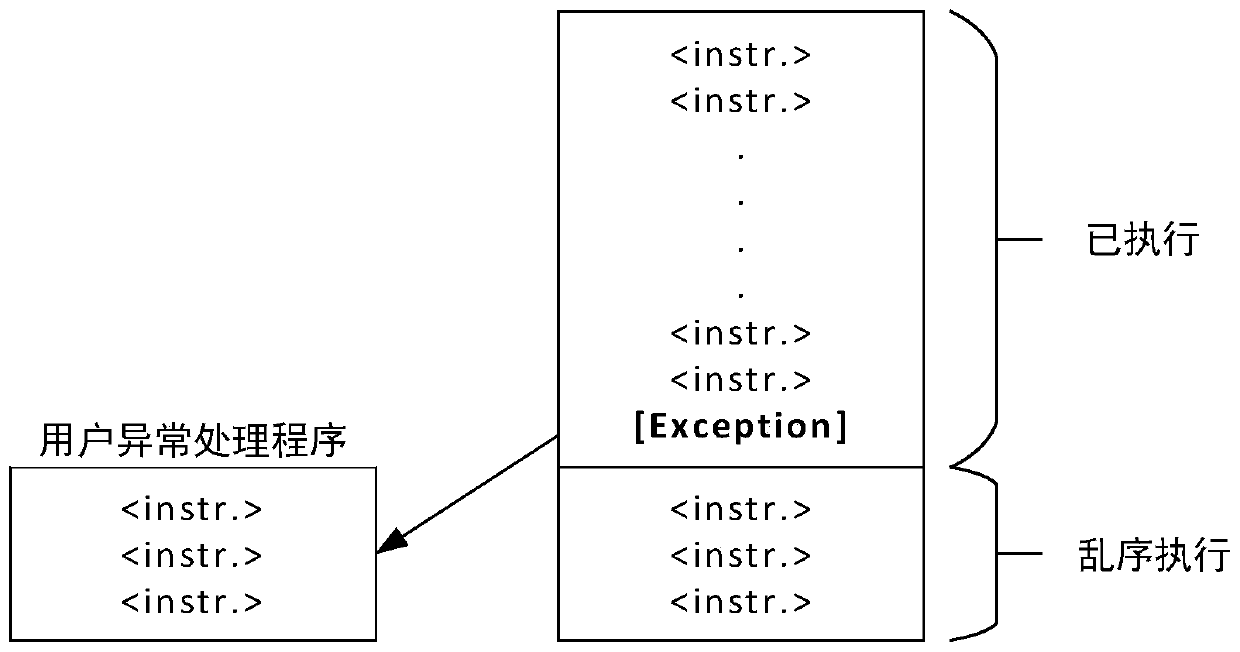
[0050] To defend against cache side-channel attacks including meltdown attacks, it is necessary to analyze the principles of cache side-channel attacks including meltdown attacks in detail. To perform a meltdown attack, the attacker will repeat the following three steps. In the first step, registers are loaded with inaccessible kernel addresses or privileged system registers. In the second step, transient instructions perform memory accesses to allocate cache lines based on registers loaded with sensitive content. In the third step, the attacker uses FLUSH+RELOAD to extract sensitive information encoded in the timing channel of the memory location accessed in the second step. In the first step, accessing a privileged resource from a userspace program ends up throwing an exception because its privilege level does not allow it to do so. However, under out-of-order execution, there are many instructions in the small time window before an exception is finally thrown. Hence, a r...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com