Intrusion detection system based on software defined security architecture
An intrusion detection system and a software-defined technology, applied in the field of network information security, can solve problems such as the inability to realize unknown attack identification and detection, and achieve the effect of flexible acquisition and collection of network information
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
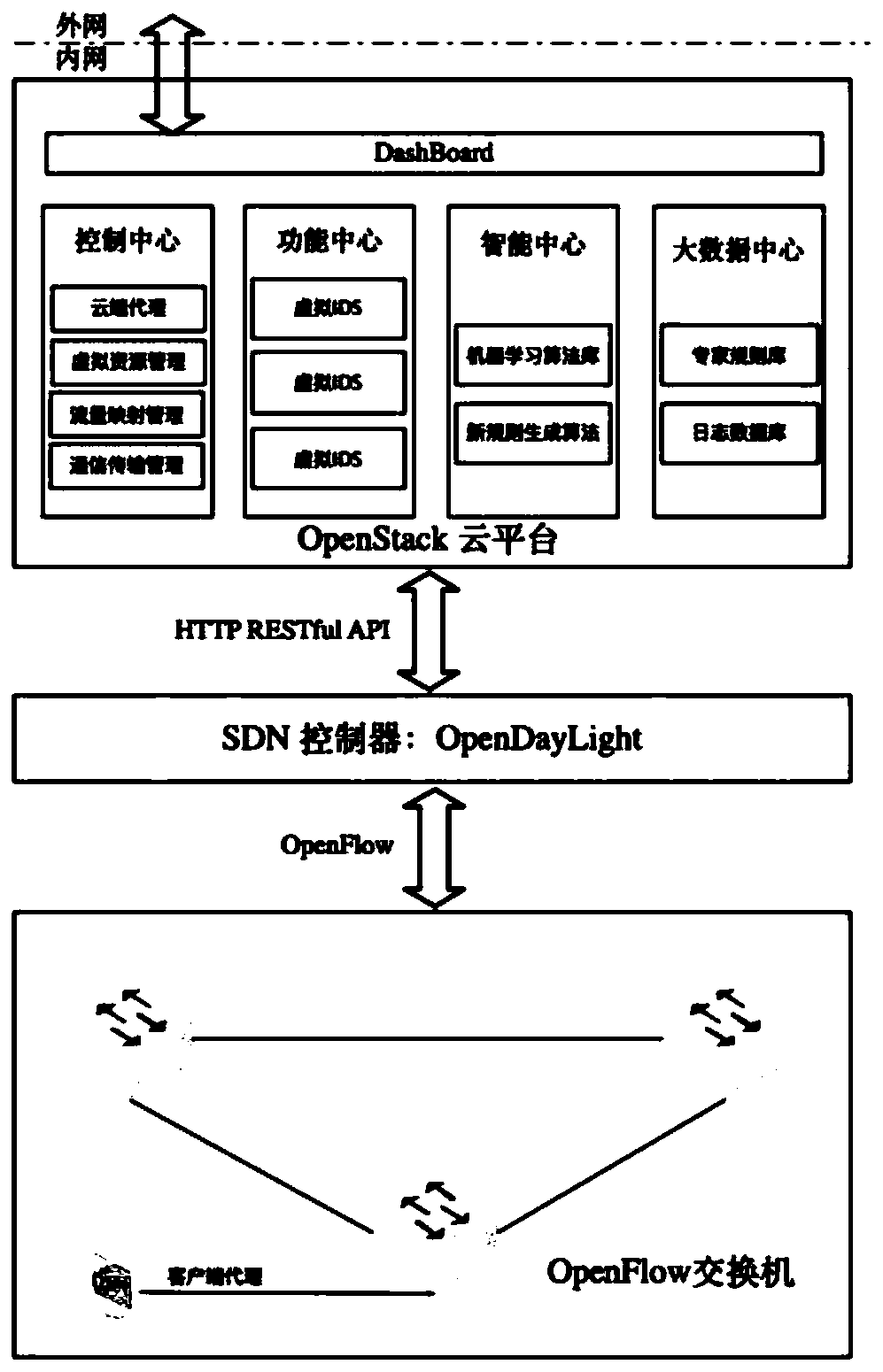
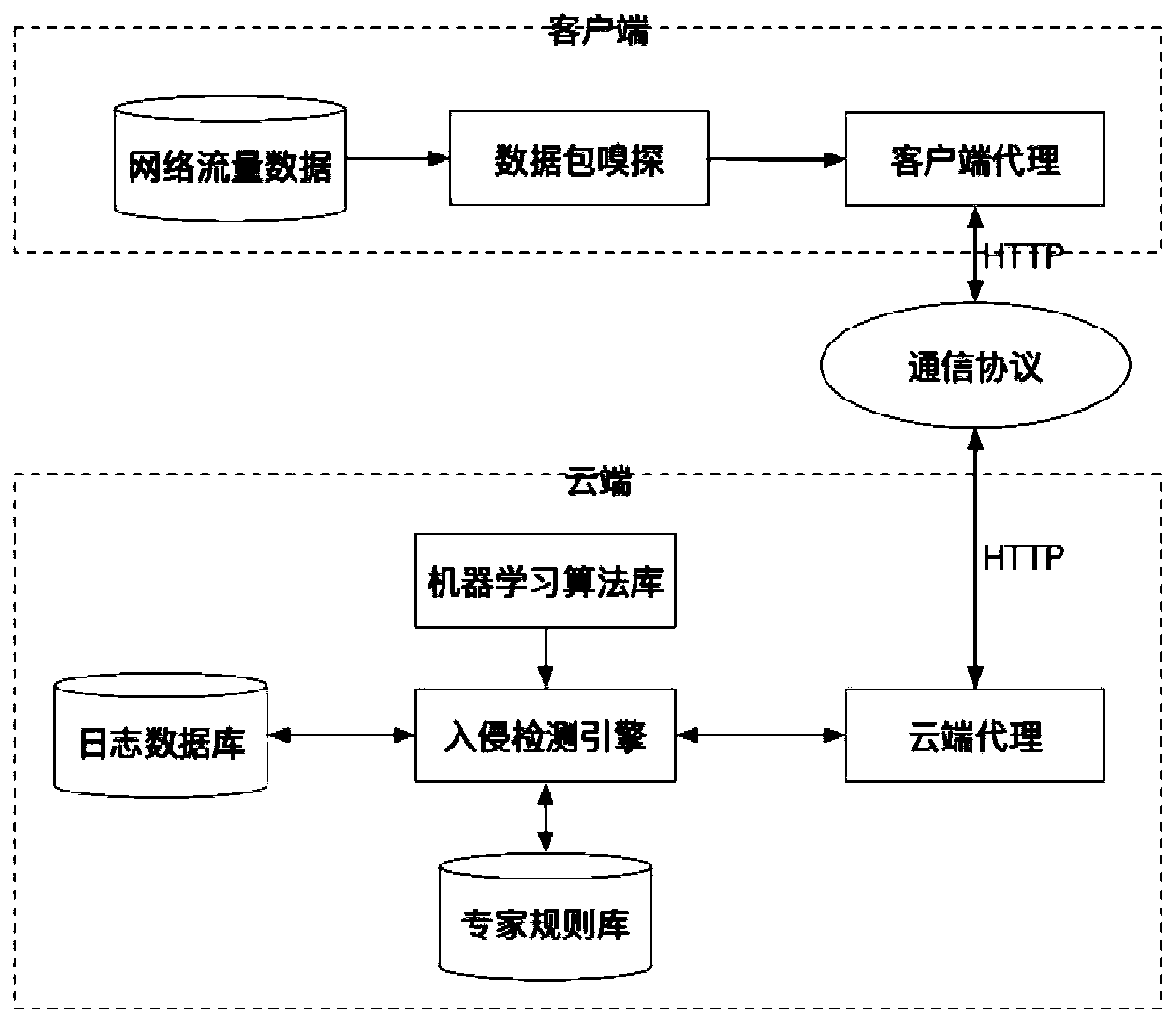
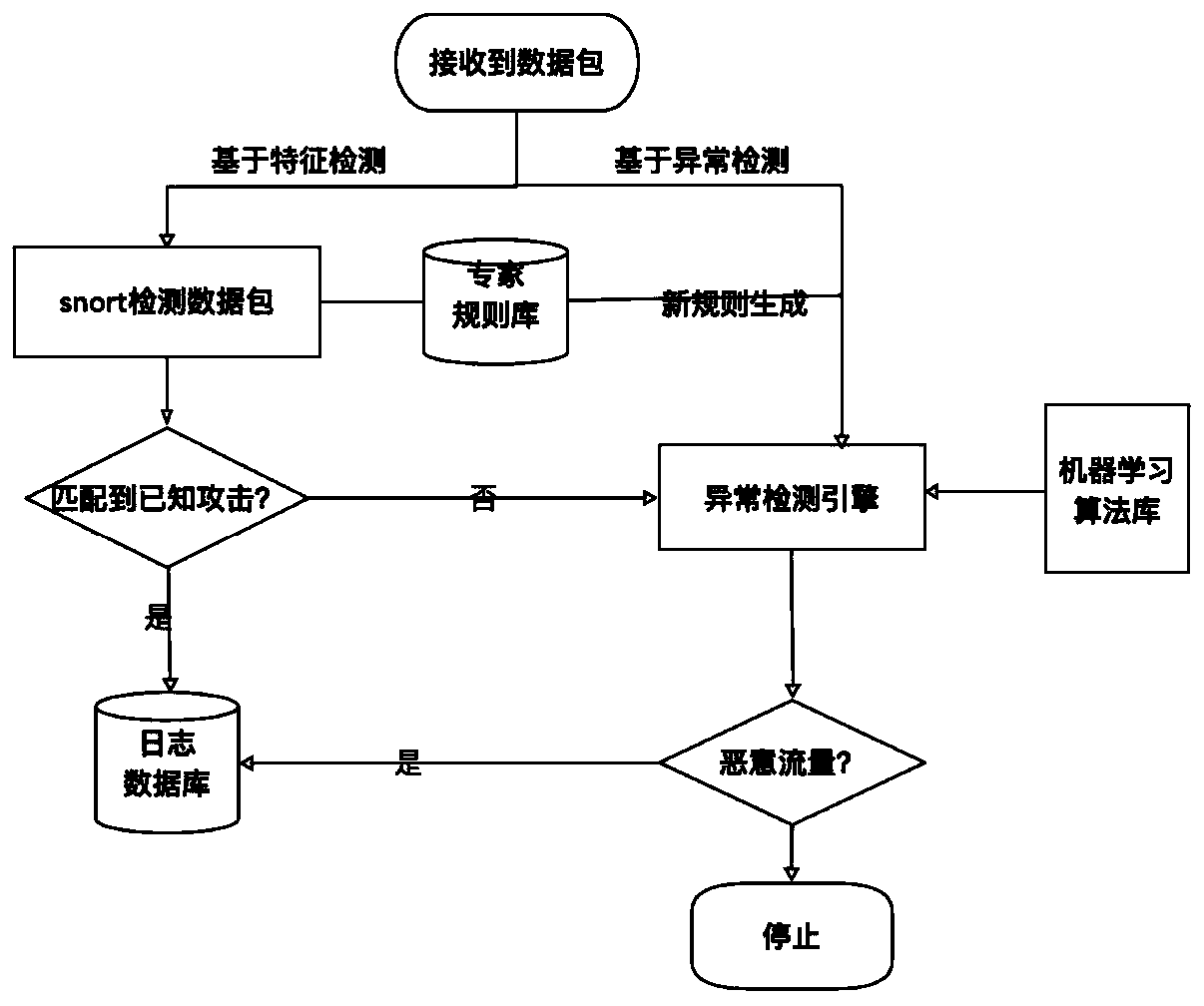
[0024] The design and implementation of the OpenStack cloud platform, the design and implementation of the client, the design and implementation of the cloud, and the design and implementation of the communication pipeline between the client and the cloud will be described in detail with specific embodiments.
[0025] 1. Design and implementation of OpenStack cloud platform
[0026] This solution adopts the OpenStack multi-node construction mode of 1 master node, 1 controller node, and 2 compute nodes. Both the controller node and the compute node provide block storage and network services, and are deployed centrally on physical servers. For cloud platform network planning and design, there are three network cards, namely:
[0027] eth0 (OpenStack cluster management network, CIDR is 10.20.0.1 / 24), used to manage cluster nodes;
[0028] eth1 (external network / floating IP network, CIDR is 172.16.0.1 / 24), used for cluster public network and providing virtual machine floating IP ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com