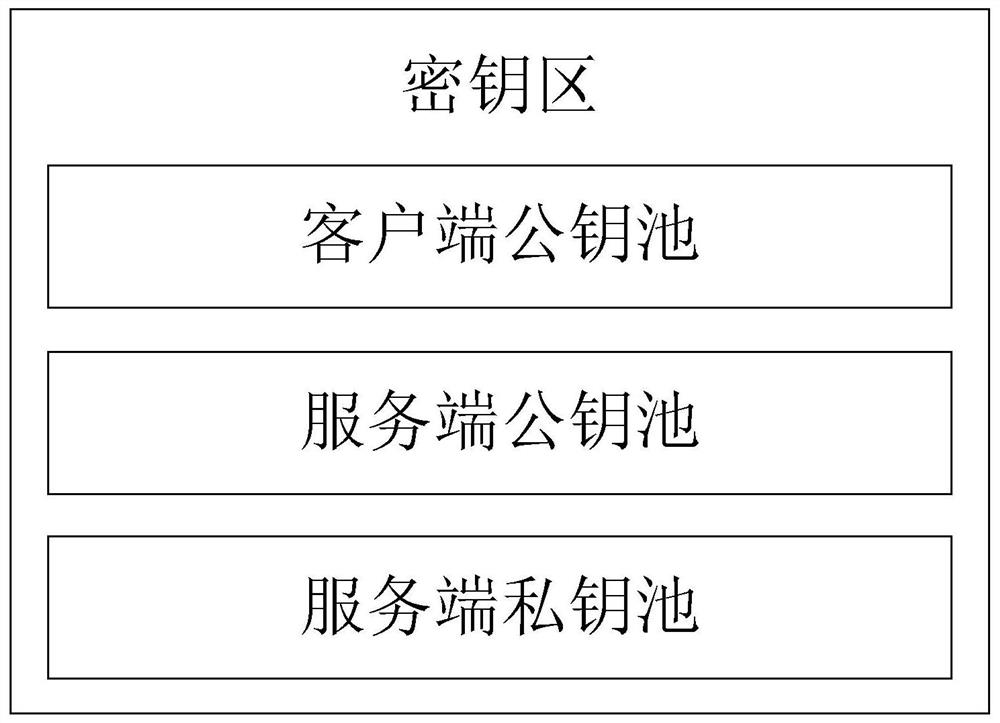
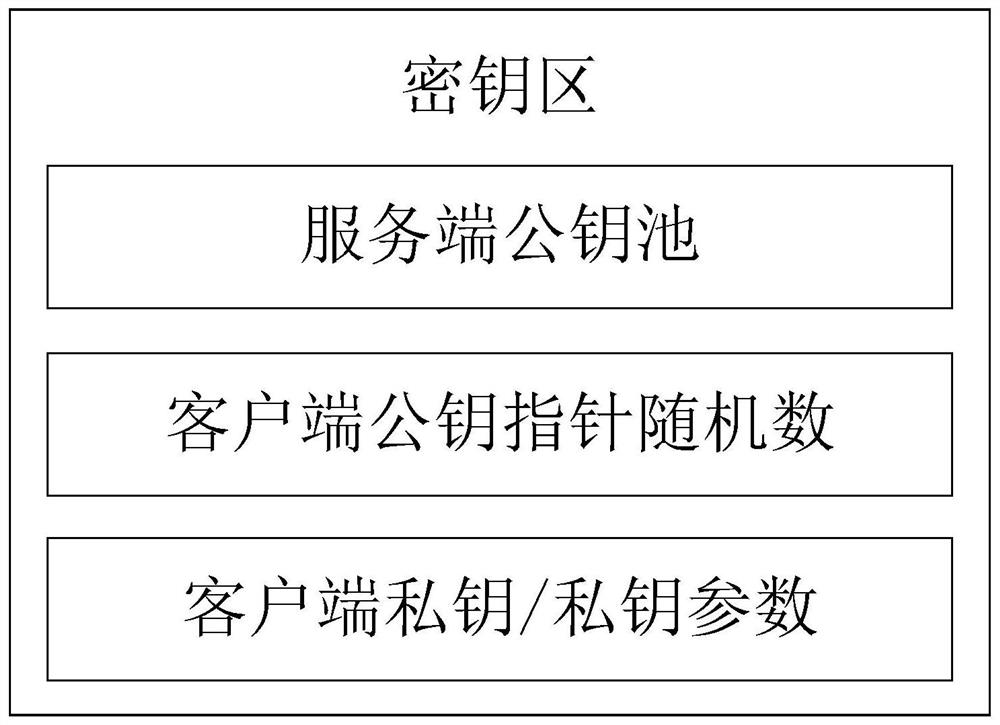
Quantum Communication Server Secure Communication Method and System Based on Asymmetric Key Pool and Implicit Certificate
An implicit certificate, confidential communication technology, applied in the field of quantum communication server confidential communication, can solve the problem of large key capacity, large capacity, unable to store the key card of the server, etc., to ensure communication security, reduce storage costs, The effect of improving safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0098] systems mannual
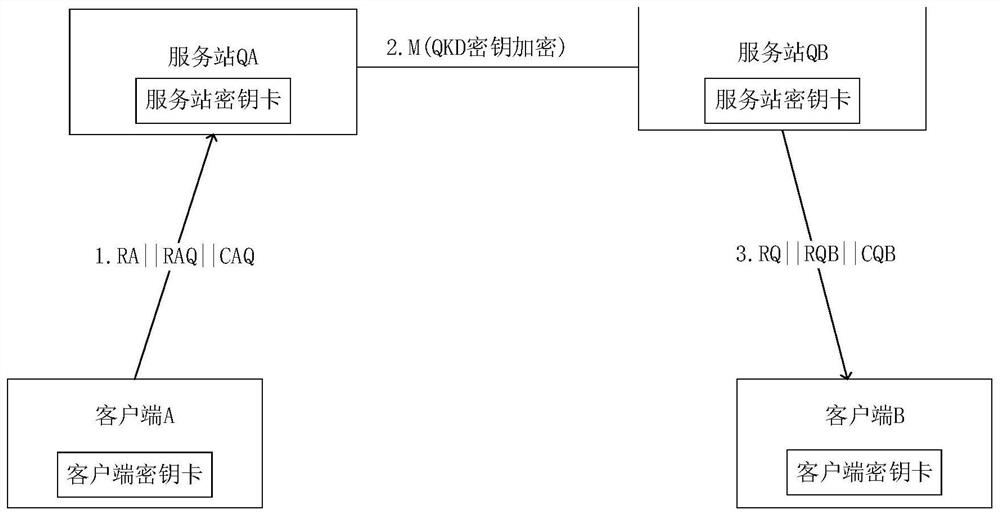
[0099] This embodiment includes client A, client B, server QA and server QB, the structure is as image 3 shown. QA and QB have their own key management servers respectively. QA and QB have QKD lanes. Client A and client B are equipped with client key cards, and server QA and server QB are equipped with server key cards. The above-mentioned client A belongs to the server QA, that is, the key card of A is issued by the key management server of QA, and the client A and the server QA share an asymmetric key pool pair. Client B belongs to server QB, that is, B's key card is issued by QB's key management server, and client B and server QB share an asymmetric key pool pair.
[0100] step 1:
[0101] Client A generates random number RA according to the random number generator in the matching key card. The random number RA is combined with the pointer function f1 to obtain the pointer PA1, and the public key PKQA1 is taken out from the server public key poo...
Embodiment 2
[0127] This embodiment includes client A, client B and server Q, the structure is as follows Figure 4 shown. Server Q has a key management server. Client A and Client B are equipped with client key cards, and server Q is equipped with server key cards. Both client A and client B above belong to server Q, that is, the key cards of client A and client B are issued by the key management server of server Q, and client A and server Q share asymmetric Key pool pair, client B and server Q also share an asymmetric key pool pair.
[0128] step 1:
[0129] Client A generates random number RA according to the random number generator in the matching key card. The random number RA is combined with the pointer function f1 to obtain the pointer PA1, and the public key PKQA1 is taken out from the server public key pool through PA1. The random number RA is combined with the pointer function f2 to obtain the pointer PA2, and the public key PKQA2 is taken out from the public key pool of the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com