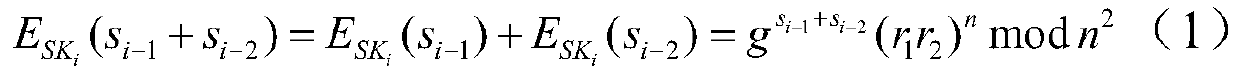Blockchain multi-party data sharing method based on secret sharing technology
A technology of data sharing and secret sharing, applied in the field of blockchain, it can solve problems such as the inability to achieve secure secret reconstruction and the inability to effectively guarantee the fairness of participants.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
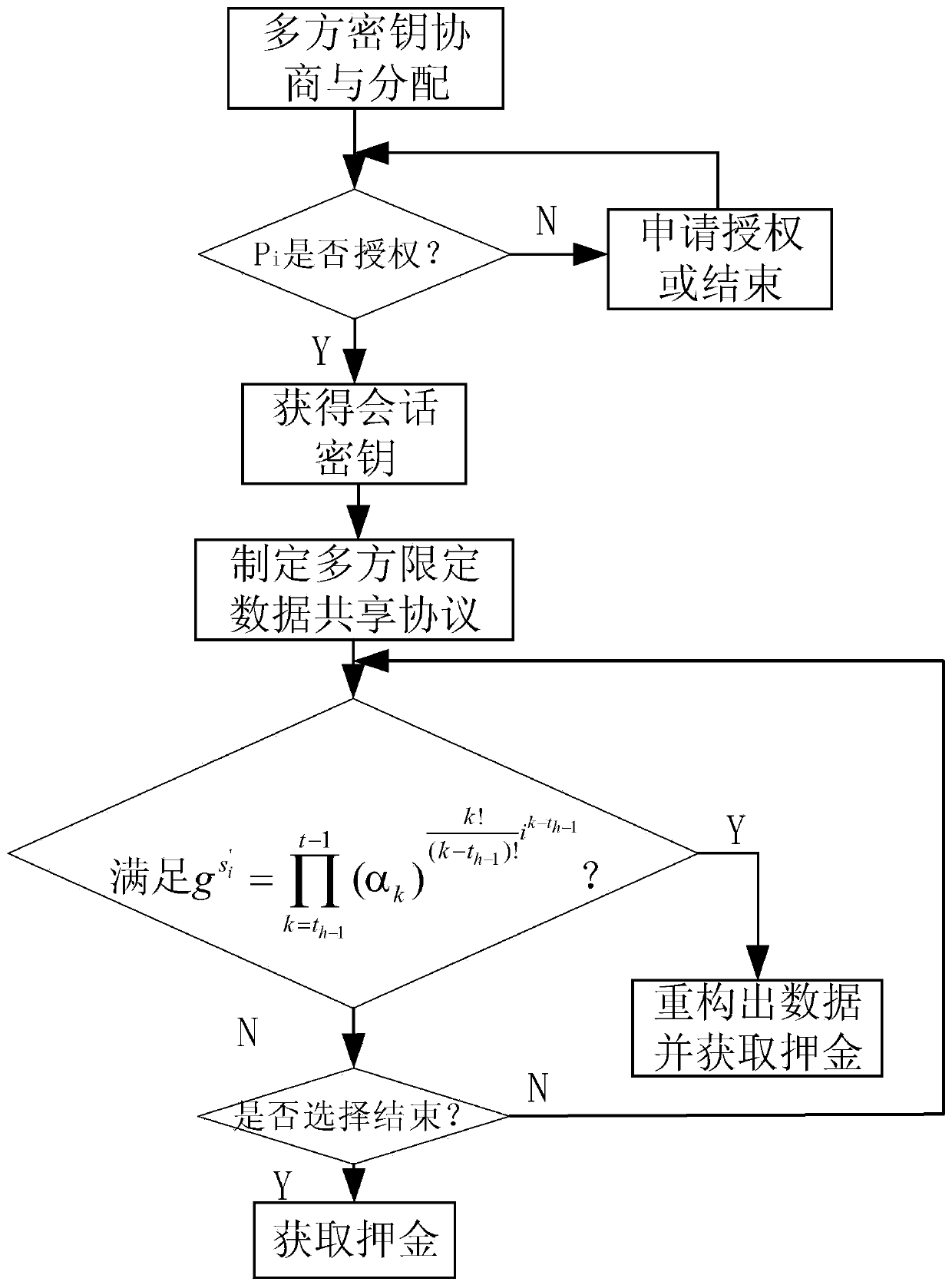
[0055] figure 1 It shows an implementation form according to the present invention, showing the main process of multi-party data sharing in blockchain based on secret sharing technology, and its main implementation steps include:
[0056] (1) Participant P i Multi-party key negotiation and distribution;
[0057] (2) Authorized P i get session key k i , unauthorized users apply for authorization or do not participate in this data sharing;
[0058] (3) According to the number of participants, formulate a multi-party limited data sharing agreement to ensure the stability and data security of the data sharing process;
[0059] (4) Using the homomorphic secret sharing method to realize the collaboration and sharing of data by multiple associated participants in the blockchain;
[0060] (5) The data is calculated by Verify the completion commitment status of each participant's shared data. Participants who meet the conditions can reconstruct the data and get a deposit. Partic...
Embodiment 2
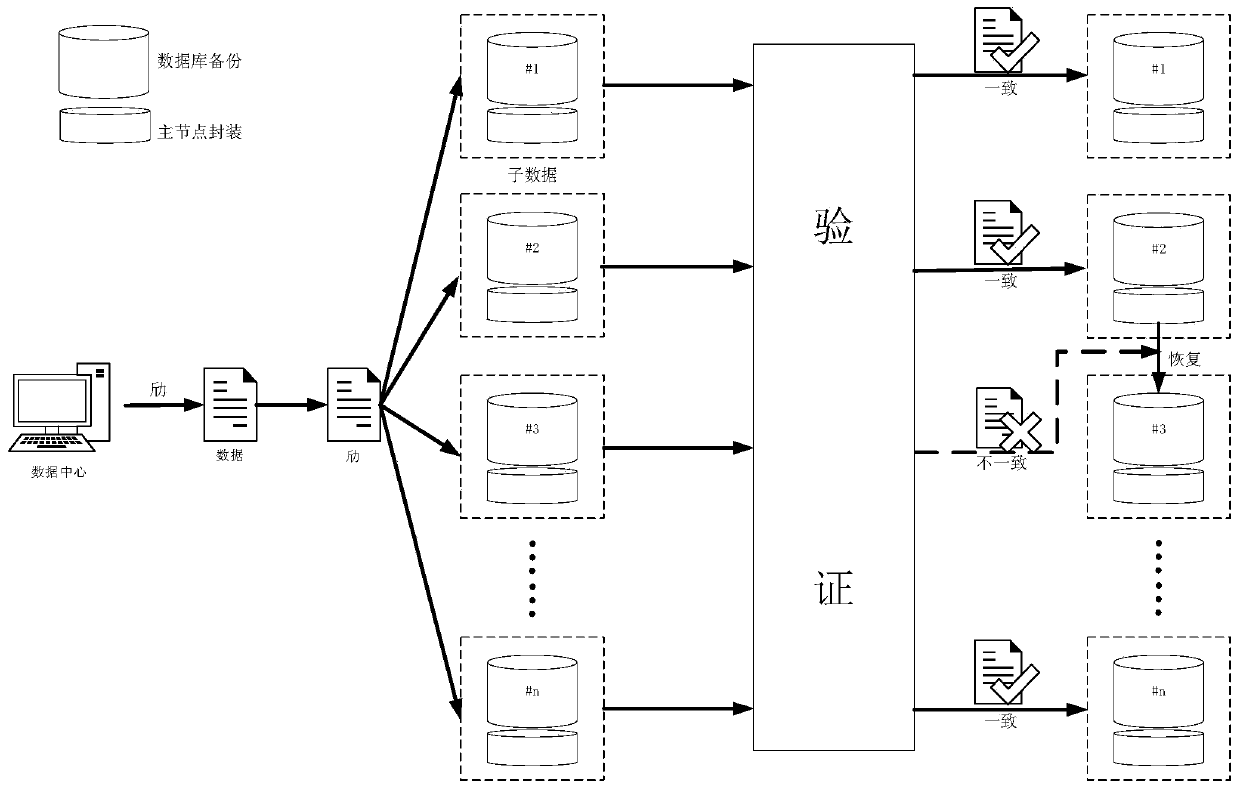
[0077] figure 2 It shows an implementation form according to the present invention, and shows that the process of verifying the sub-data is also included in the formulation of the data sharing agreement based on the above key encryption operation and completion, so as to ensure the correctness of the shared data. The root hash generated by the Merkle hash tree in the blockchain can be used as the unique identity proof of the data file in the current state on the one hand, and can also be used to prove the parameters of the integrity check of the data. The verification process is similar to common blockchain transaction verification. The present invention distributes a data as a whole into sub-data, and sub-data is easier to recover than the whole data, so the present invention also includes the operation of recovering damaged or lost data. The specific implementation process of data verification and recovery includes:
[0078] 1.1 Participant P i owns subdata share d i an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com