Social software monitoring system and social software protection method
A social software and monitoring system technology, applied in transmission systems, electrical components, etc., can solve problems such as easy to be exploited, lack of monitoring protection, and threats to user information and property security, so as to ensure security, privacy security, and information security Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
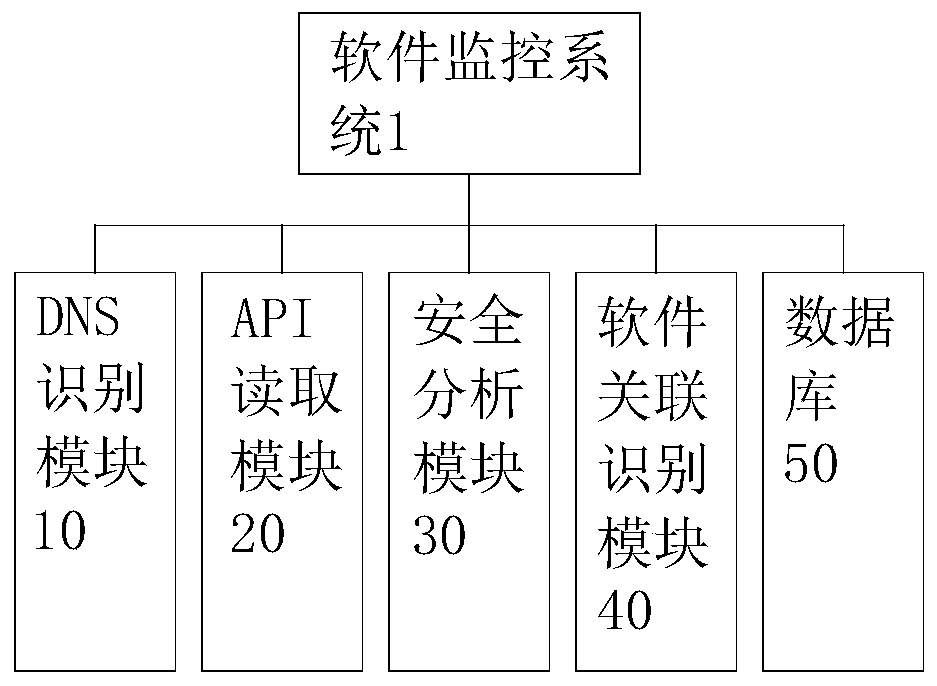
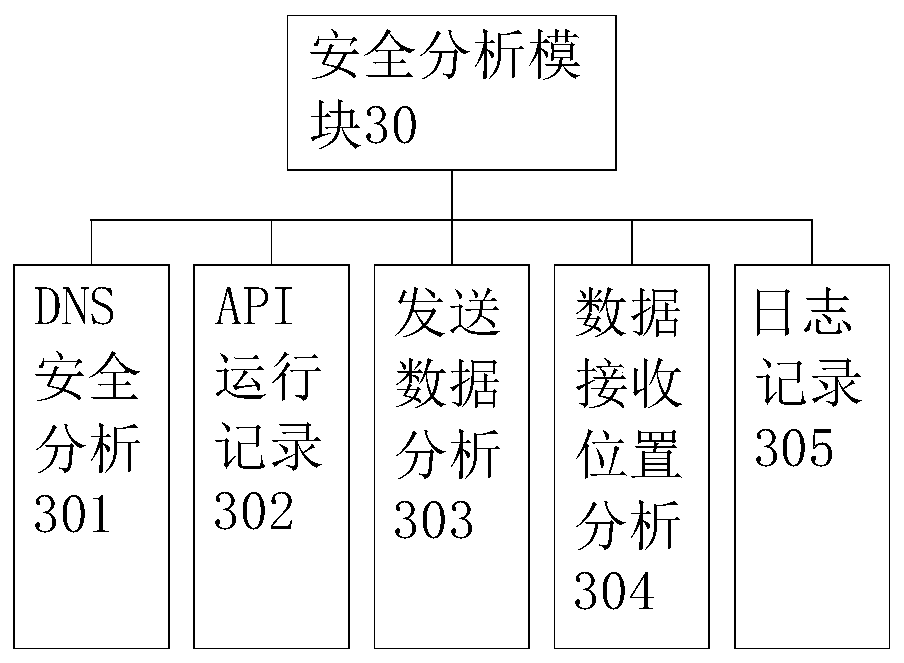
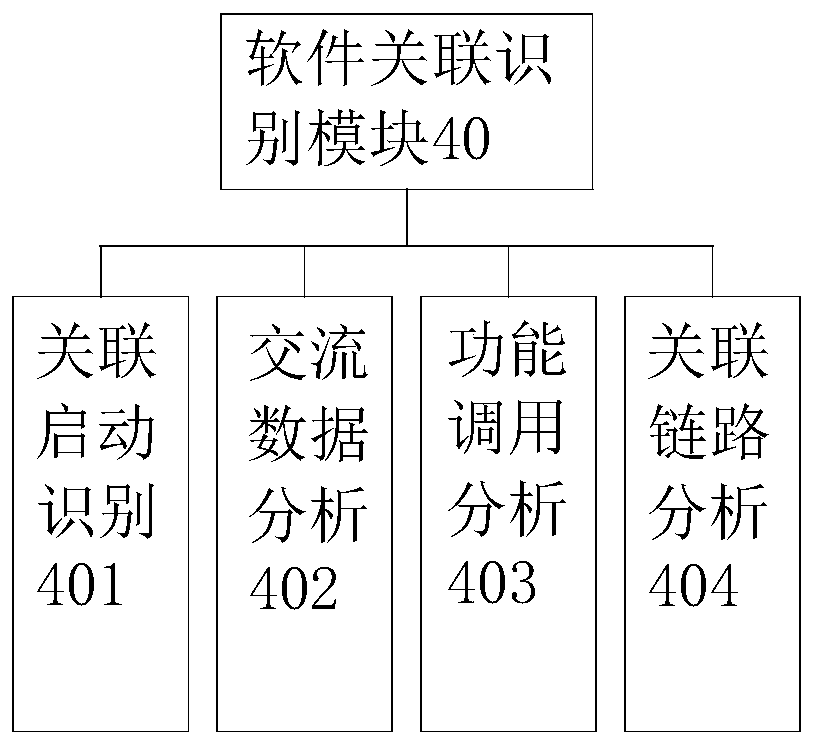
[0028] Example 1, please refer to Figure 1~2 And 4, a kind of monitoring system of social software, this software monitoring system 1 comprises DNS identification module 10, API reading module 20, safety analysis module 30, software association identification module 40 and database 50 constitute; Described DNS identification module 10 uses The DNS location data for data transmission between the identification software and the Internet is used to judge whether the DNS is a normal DNS list. The DNS list includes white list, black list and gray list. The white list is the DNS directory that has been verified and verified to be safe and problem-free. The blacklist is a DNS directory that has been verified and has security problems. Security problems include but are not limited to leakage of private data, account theft, software Trojan horse virus implantation, or excessive and abnormal occupation of system space. Verify the verified DNS directory, take operation prompts for the D...
Embodiment 2
[0036] Example 2, please refer to Figure 1~4 , a monitoring system for social software, the software monitoring system 1 includes a DNS identification module 10, an API reading module 20, a security analysis module 30, a software association identification module 40 and a database 50; the DNS identification module 10 is used to identify DNS location data for data transmission between the software and the Internet to determine whether the DNS is a normal DNS list. The DNS list includes whitelist, blacklist and graylist. The whitelist is the DNS directory that has been verified and verified to be safe and problem-free. That is, the DNS directory that has been verified and has security problems. Security problems include but are not limited to leakage of private data, account theft, software Trojan virus implantation, or excessive abnormal occupation of system space. The gray list has not been verified. The DNS directory in the gray list takes an operation prompt for the DNS in ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com