Power grid virtual data injection attack detection method based on deep belief network
A technology of deep trust network and virtual data, applied in the detection field of virtual data injection attack in power grid, can solve the problems of strong threshold dependence and single attack mode, and achieve the effect of overcoming the dependence of detection threshold
Pending Publication Date: 2020-03-17
GUANGDONG UNIV OF TECH
View PDF7 Cites 14 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
[0004] In order to overcome the defects of strong dependence on the threshold value of the grid attack detection method and a single detected attack mode in the above-mentioned prior art, the present invention provides a detection method for power grid virtual data injection attack based on a deep trust network
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
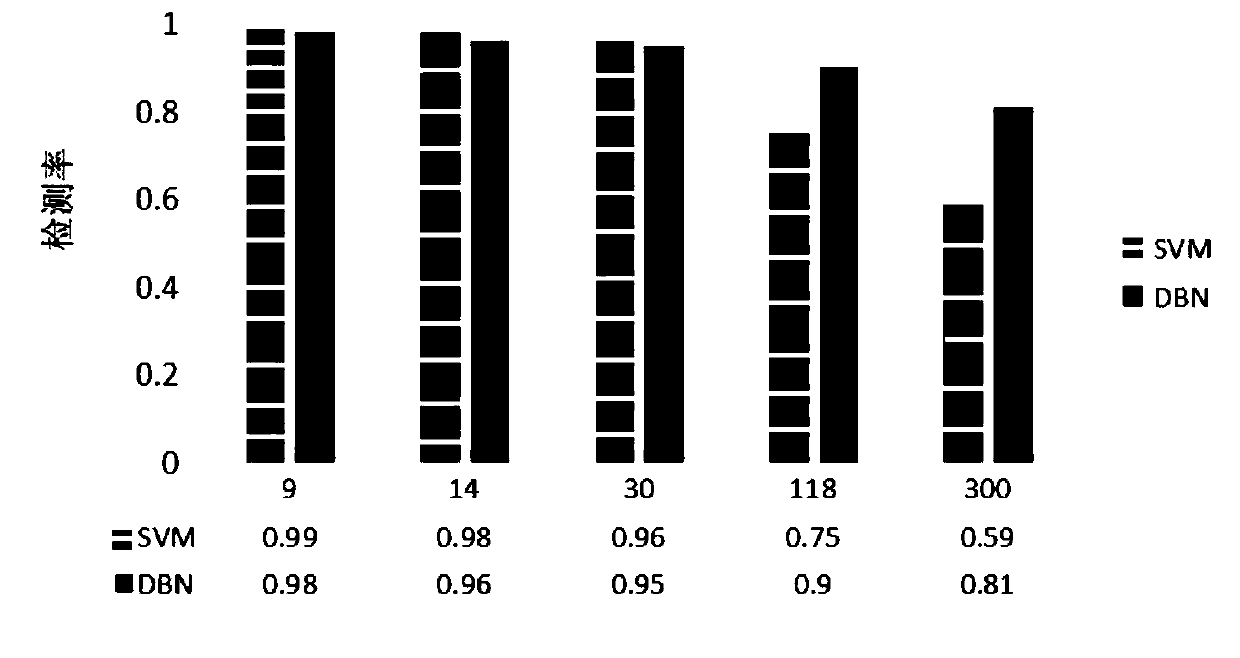
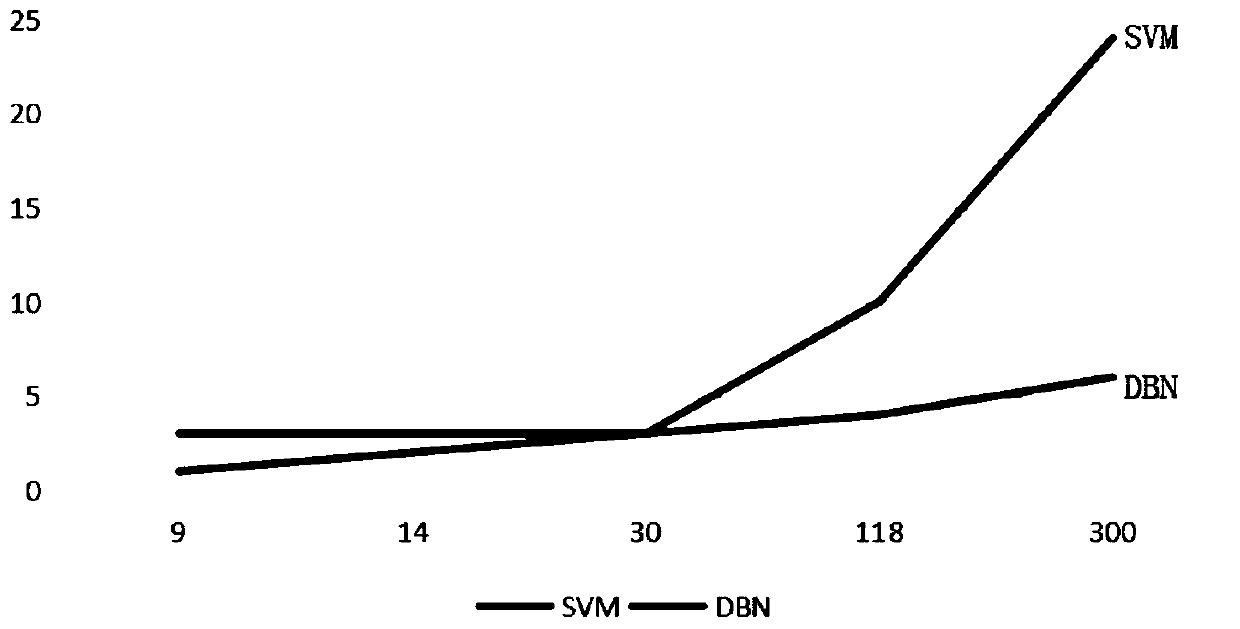
Comparison scheme
Effect test
Embodiment 1
[0030] Explanation of terms and principles
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More PUM
 Login to View More
Login to View More Abstract
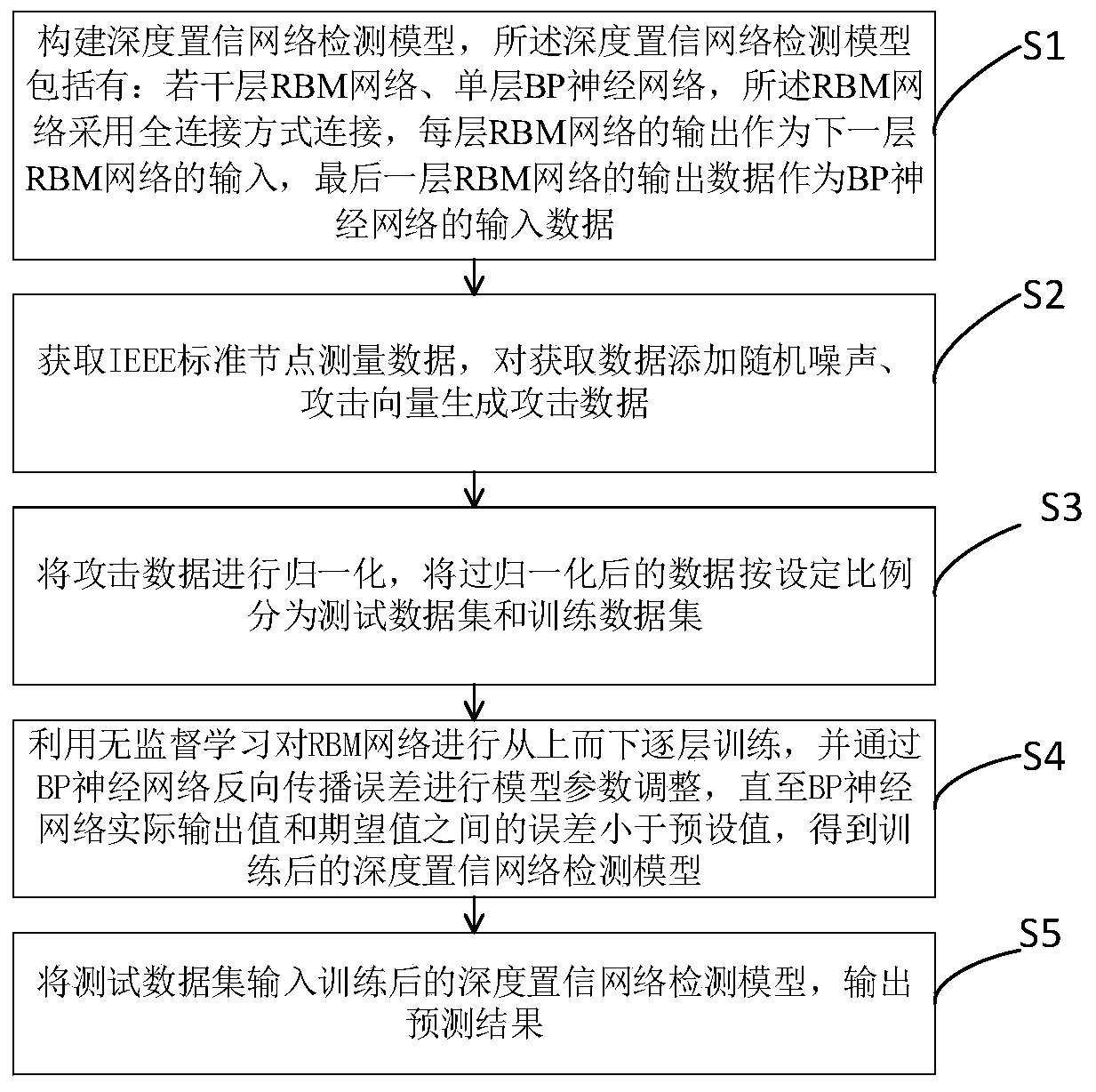
The invention discloses a power grid virtual data injection attack detection method based on a deep belief network, and the method comprises the steps: S1, building a deep belief network detection model which comprises a plurality of layers of RBM networks and a single-layer BP neural network, wherein the RBM networks is connected in a full connection mode; S2, acquiring IEEE standard node measurement data, and adding random noise and attack vectors to the acquired data to generate attack data; s3, dividing the normalized attack data into a test data set and a training data set according to aset proportion; s4, training the RBM network layer by layer from top to bottom by using unsupervised learning, and performing model parameter adjustment through BP neural network back propagation errors to obtain a trained deep belief network detection model; and S5, inputting the test data set into the trained deep belief network detection model, and outputting a prediction result. According to the invention, the dependence of the traditional detection method on the detection threshold is overcome, and the detection of various attack modes is realized.
Description
technical field [0001] The invention relates to the field of smart grids, and more specifically, to a detection method for grid virtual data injection attacks based on a deep belief network. Background technique [0002] As a typical cyber-physical system, smart grid integrates communication, computing and control. While this integration greatly improves the management level of the power system, it also brings greater risks to the system. Power system security incidents have occurred frequently in recent years and have caused great damage. [0003] False data injection attack (FDIA) is an emerging method of data integrity attack. On the basis of a certain understanding of the power network topology, the attacker tampers with the sensor, and the energy management system (EMS) receives this information. The purpose of changing the state estimation result is achieved. Under the action of FDAA, attackers can control the smart devices in the system and manipulate key informati...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More Patent Type & Authority Applications(China)
IPC IPC(8): G06F21/55G06K9/62G06N3/04G06N3/08G06Q50/06
CPCG06F21/55G06N3/084G06Q50/06G06N3/045G06F18/2411
Inventor 刘明相孟伟付敏跃鲁仁全
Owner GUANGDONG UNIV OF TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com