Security authentication method and system based on security chip and security chip
A security chip and security certification technology, applied in the field of secure communication, can solve problems affecting and affecting information security, and achieve the effect of improving information security and increasing the cost of cracking
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
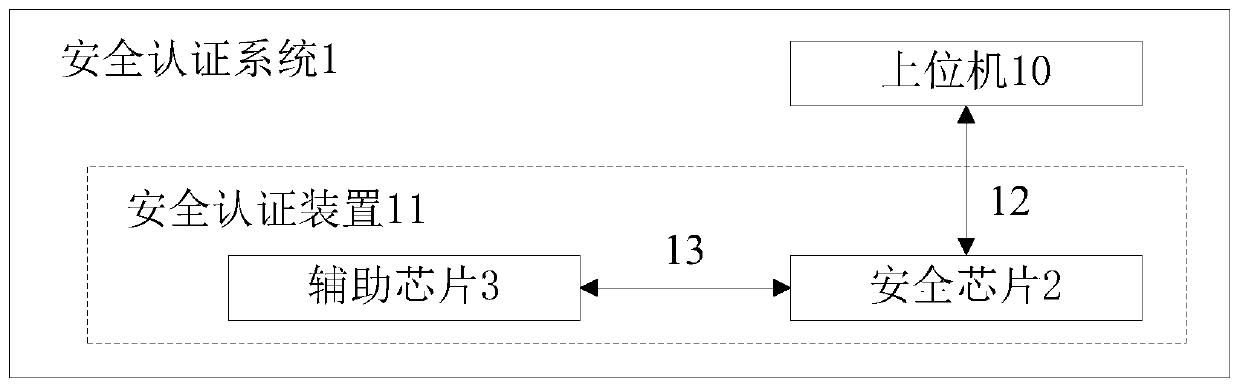
[0052] see figure 1 The security authentication system 1 of the present invention includes a host computer 10 and a security authentication device 11 coupled to the host computer 10; the security authentication device 11 includes a security chip 2 coupled to the host computer 10 and an auxiliary chip 3 coupled to the security chip 2 .
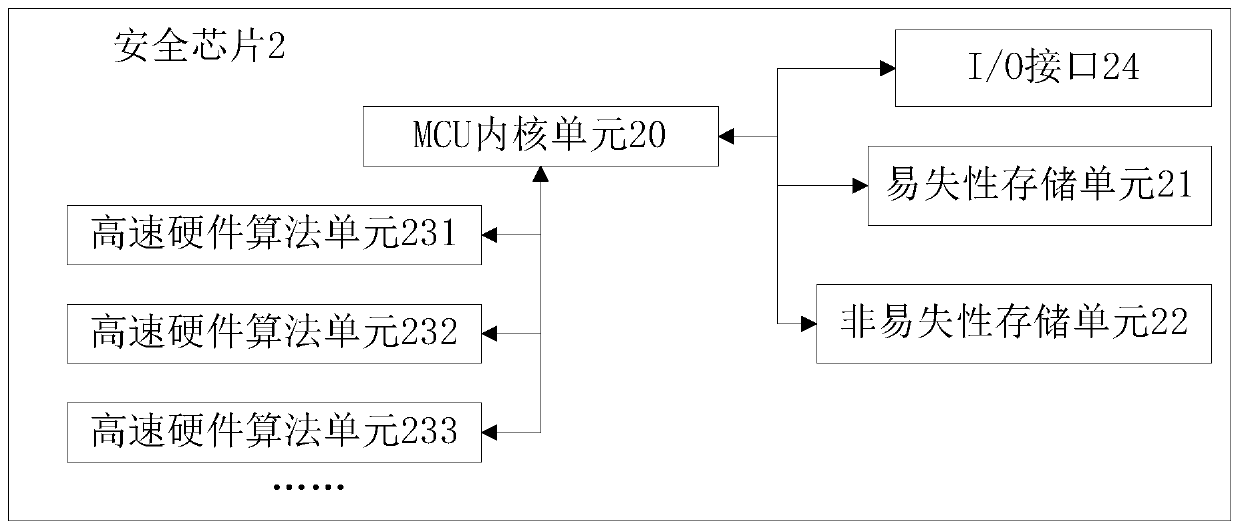
[0053] see figure 2 , the security chip 2 includes an MCU core unit 20, a volatile storage unit 21, a nonvolatile storage unit 22, an I / O interface 24, and a high-speed hardware algorithm unit; wherein, the high-speed hardware algorithm unit includes a high-speed hardware algorithm unit 231, a high-speed hardware algorithm unit A plurality of high-speed hardware arithmetic units such as the hardware arithmetic unit 232 and the high-speed hardware arithmetic unit 233 . The MCU core unit 20 is mainly used for internal control and calculation of the chip, usually a general-purpose MCU core such as MSP430, CORTEX-M0; the volatile storage unit 21...
Embodiment 2
[0104] In the description of this embodiment, only the difference between the information processing processes of the two chips is described as an example, that is, only the difference from the above-mentioned embodiment 1 is described, and the symbols of each unit continue to be used in embodiment 1. label.
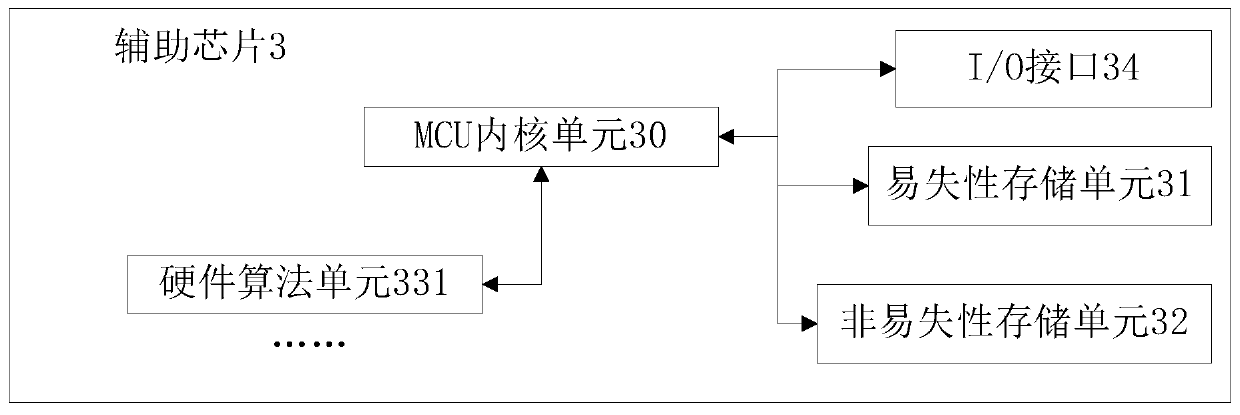
[0105] In the non-volatile storage unit 32 of the auxiliary chip 3, the security key information that has already been encrypted is stored, that is, the first ciphertext data in Embodiment 1 is stored, and is used to decrypt the first ciphertext data. The first decryption key is pre-stored in the non-volatile storage unit 22 of the security chip 2 .
[0106] That is, in this embodiment, the first ciphertext data is generated by encrypting the security key data required for security authentication, and the key required for its decryption is the aforementioned first decryption key, without the need for the security chip 2 to generate the first random key. Number and perfo...
Embodiment 3
[0109] In the description of this embodiment, only the difference between the information processing processes of the two chips is described as an example, that is, only the difference from the above-mentioned embodiment 1 is described, and the symbols of each unit continue to be used in embodiment 1. label.
[0110] After the auxiliary chip 3 receives the wake-up instruction, it generates a pair of public key and private key based on the asymmetric encryption and decryption algorithm, the private key is stored in the volatile storage unit 31, and the public key is sent to the security chip 2, specifically , the public key can be used as the response information for the wake-up command. The security chip 2 uses the public key to encrypt the first random number using an asymmetric encryption and decryption algorithm to obtain the second ciphertext data and send it to the auxiliary chip 3. The chip uses the private key stored in the volatile storage unit 31 to decrypt, and then ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com