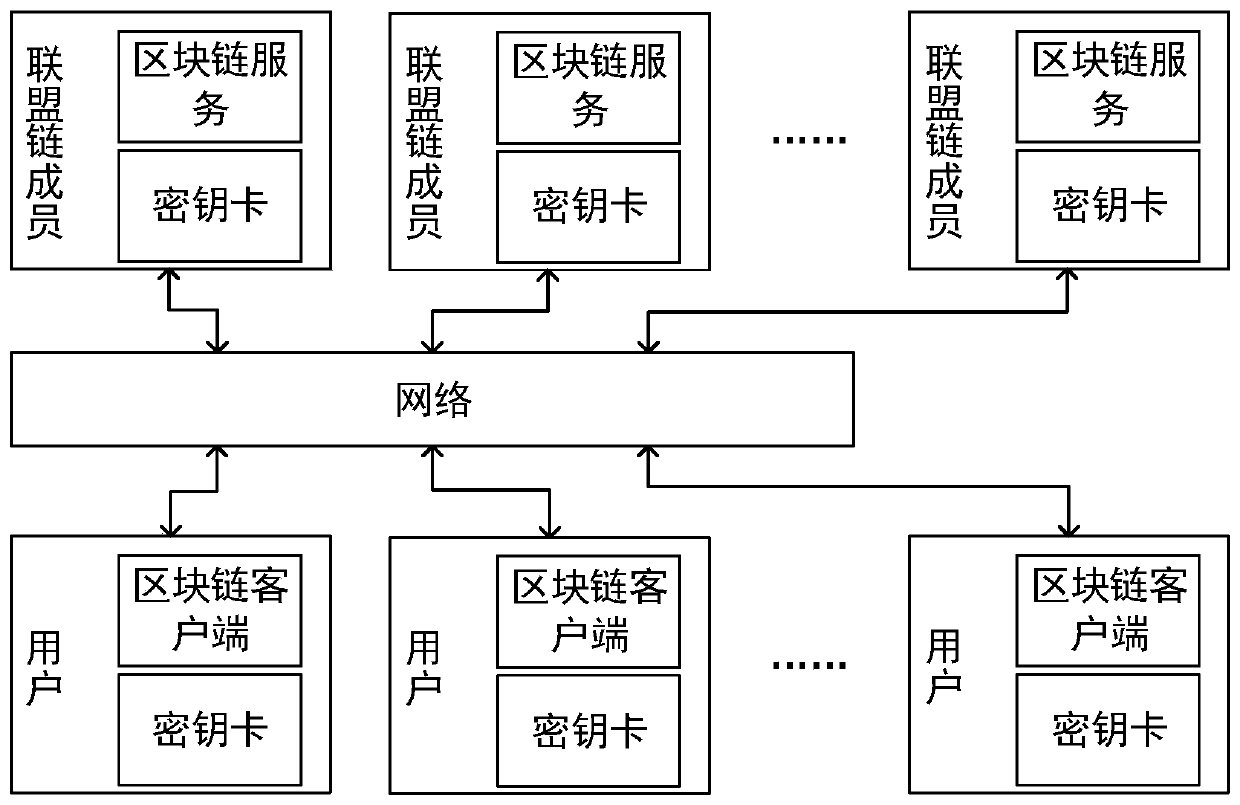
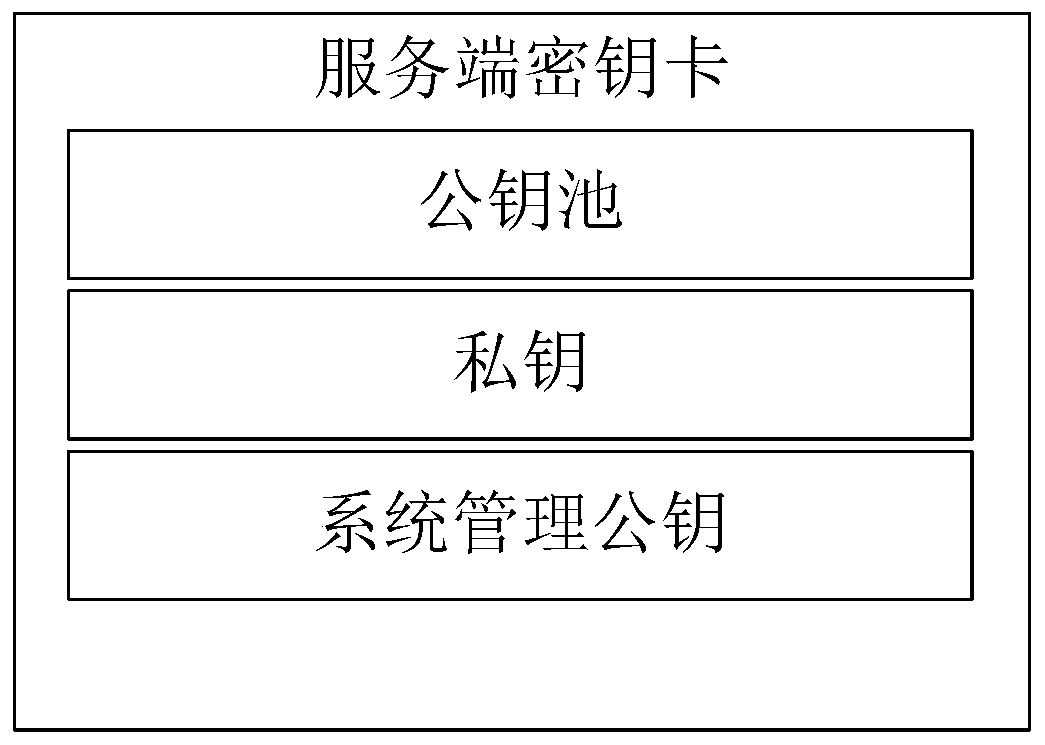
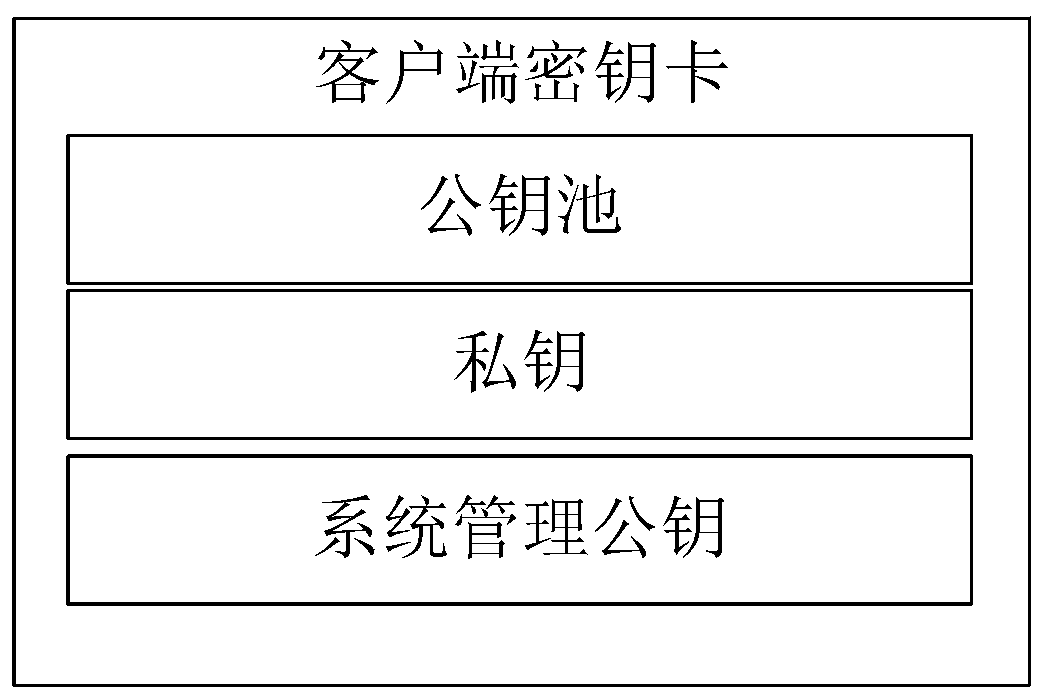
Anti-quantum computing private key backup, loss reporting and recovery method and system based on alliance chain and identity cryptography
An identity password and recovery method technology, applied in the field of loss reporting and recovery methods and systems, and anti-quantum computing private key backup field, can solve problems such as disappearance, inability to resist Trojan or hacker attacks, and core nodes being too large to avoid leakage.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0098] Example 1: Private key backup process:
[0099] Step 1: User proposes a transaction.
[0100] Suppose the ID value of the n backup key cards of the Client is IDUk, and the stored asymmetric key pair is PKUk / SKUk, 1≤k≤n. For each IDUk, take the public key pointer random number RUTk, get the public key random number from the public key pool through the pointer function and calculate the public key RUUTk. The client takes out the corresponding public key random number RUk in the key card of the IDUk, and this process is performed under safe conditions, such as copying through a secure storage medium or a secure data interface connection. Client obtains the public key PKUk corresponding to IDUk according to PKUk=H(RUk), and uses PKUk to encrypt the SKU based on ID cryptography (see references
[0101] "Identity-Based Encryption from the Weil Pairing"), that is, ENC (SKU, PKUk), to obtain the ciphertext (EUk, EVk).
[0102] Client sends transaction tx to n Endorsers, and ...
Embodiment 2
[0128] Example 2: Private key loss report and recovery process:
[0129] After the key card whose identity is IDU is lost, the user uses the key card whose identity is IDUi to execute this process.
[0130] When the private key SKU of the user Client is lost, use the kth key card (ID is IDUk, public and private key is PKUk / SKUk) to report the loss of the private key and recover the private key.
[0131] Find the corresponding public key random number RE in the key card according to the ID of the Endorser, obtain the public key PKE of the Endorser according to PKE=H(RE), and then use PKE to encrypt RUk based on ID cryptography to obtain the ciphertext txdata= ENC(RUk, PKE) = (txdataU, txdataV). Take the public key pointer random number RPKtxdataU, get the public key random number from the public key pool through the pointer function and calculate the public key PKtxdataU. Offset txdata to get txdata'=RPKtxdataU||(txdataU-PKtxdataU, txdataV).
[0132] Client sends transaction...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com