Active immune attack identification method and charging device
A technology of attack identification and active immunity, applied in electric vehicle charging technology, charging stations, electric vehicles, etc., can solve problems such as grid resonance, public grid voltage fluctuation, and attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0083] The present invention will be described in further detail below in conjunction with the accompanying drawings and embodiments.
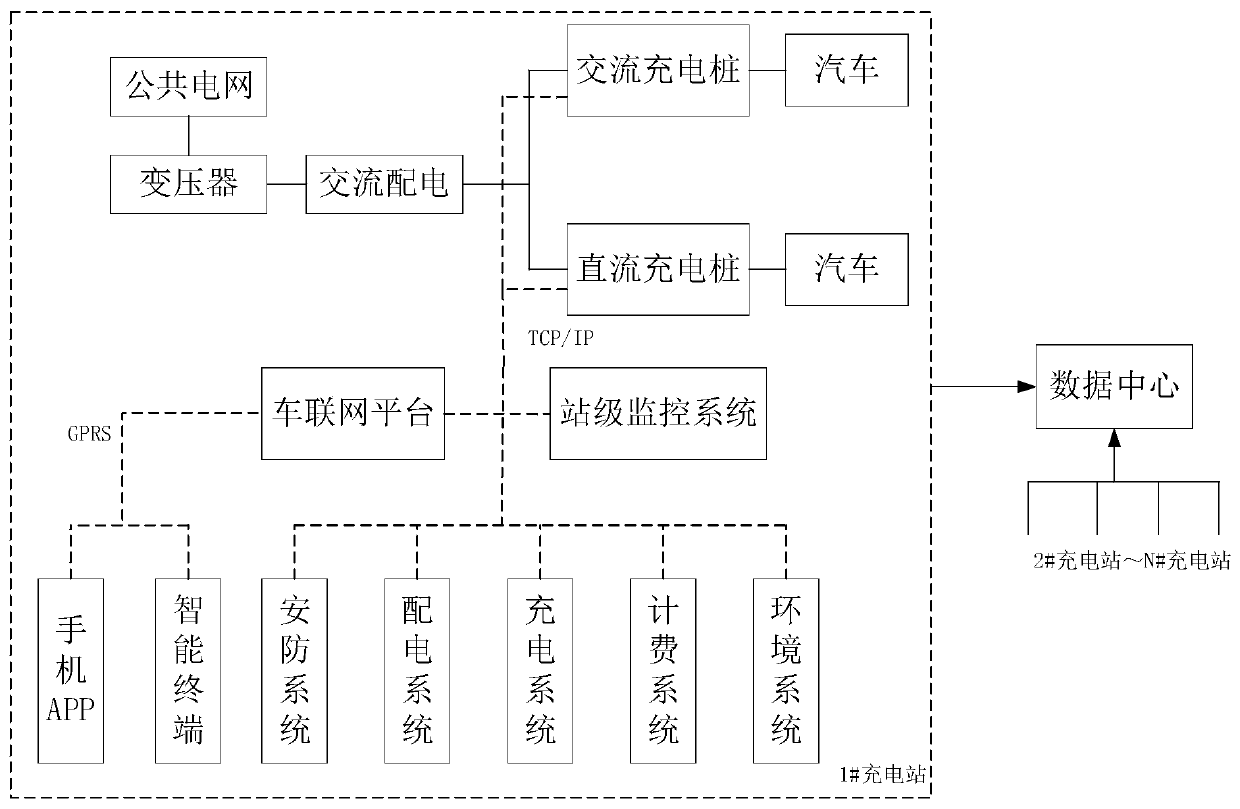
[0084] Such as figure 1 As shown, in the existing electric vehicle charging system, each power station is equipped with a station-level monitoring system, an Internet of Vehicles platform, a charging device, an AC power distribution system, a transformer, and a public power grid. The system communicates with the charging device (charging pile) through the TCP / IP protocol, and the charging device is connected with the AC power distribution system. Publish the current situation of the site in real time.
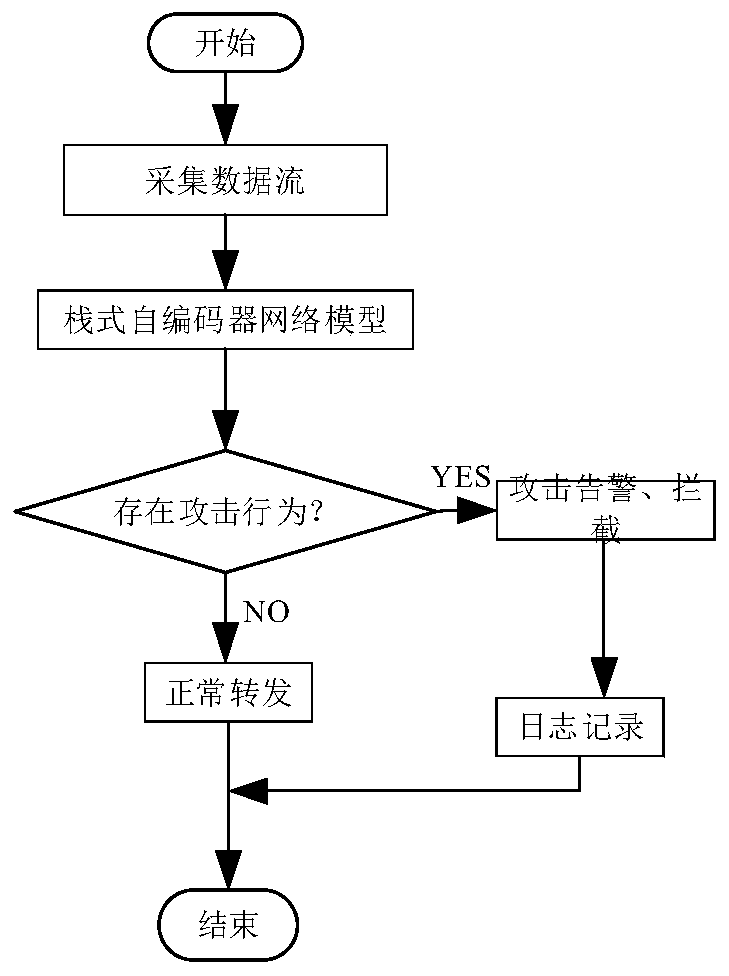
[0085] Such as figure 2 As shown, the present invention discloses a method for identifying an active immune attack, comprising the following steps:
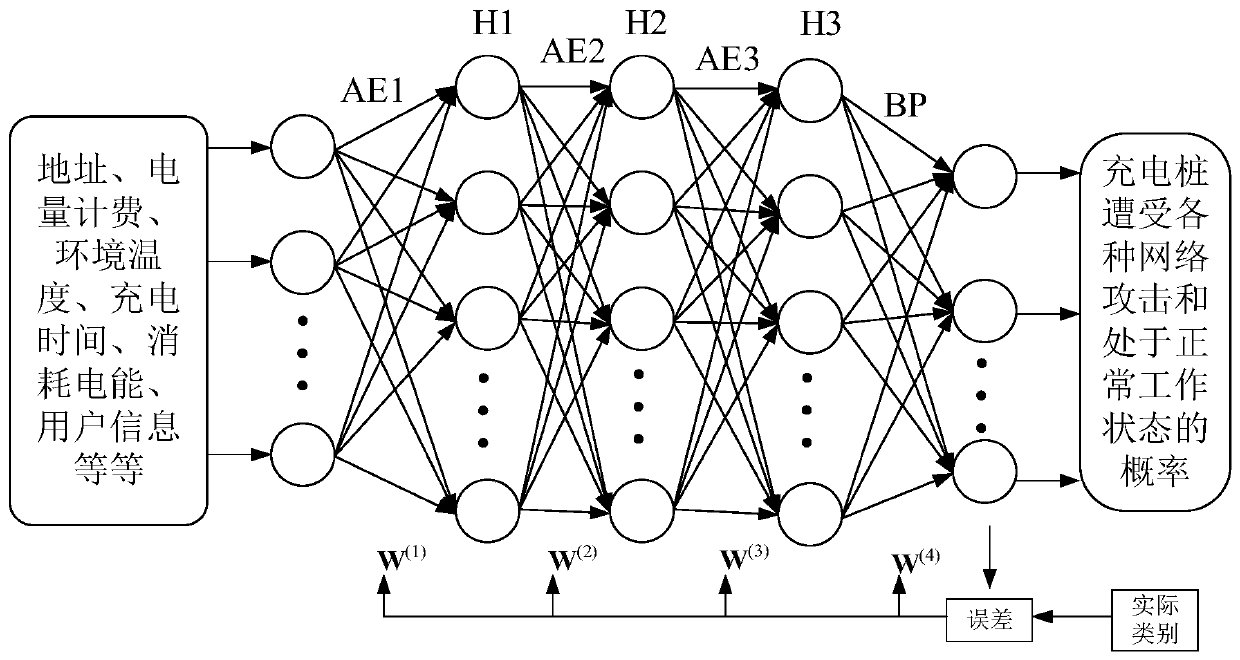
[0086] Step 1. Obtain the real-time data stream of the charging device. The data stream is characteristic data or influencing factors that can represent whether the data is attacked. The data ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com