Abnormality detection method and device for detecting abnormal operation of a work system
An operating system and anomaly detection technology, which is applied in the field of information security and can solve the problem of wasting system computation.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
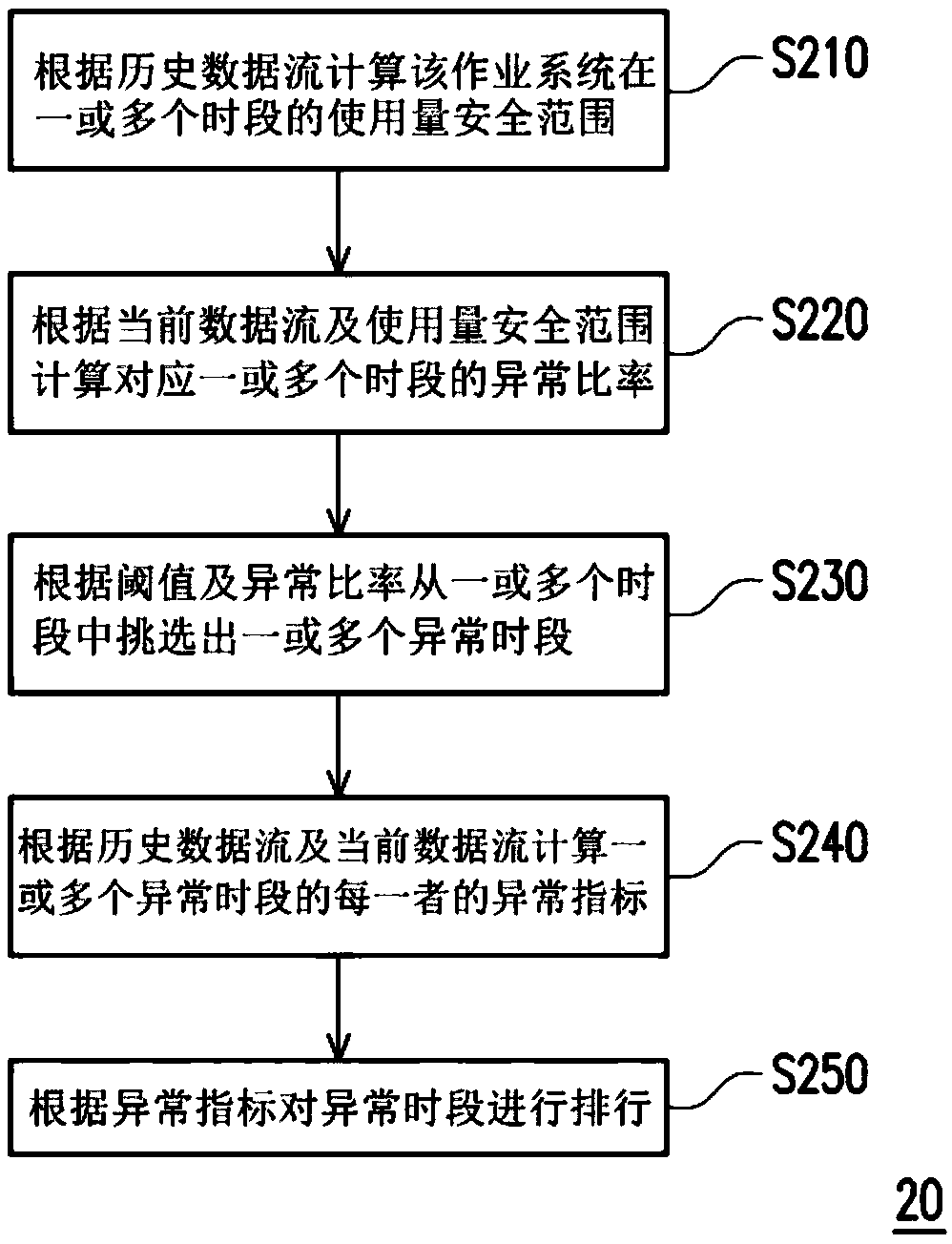
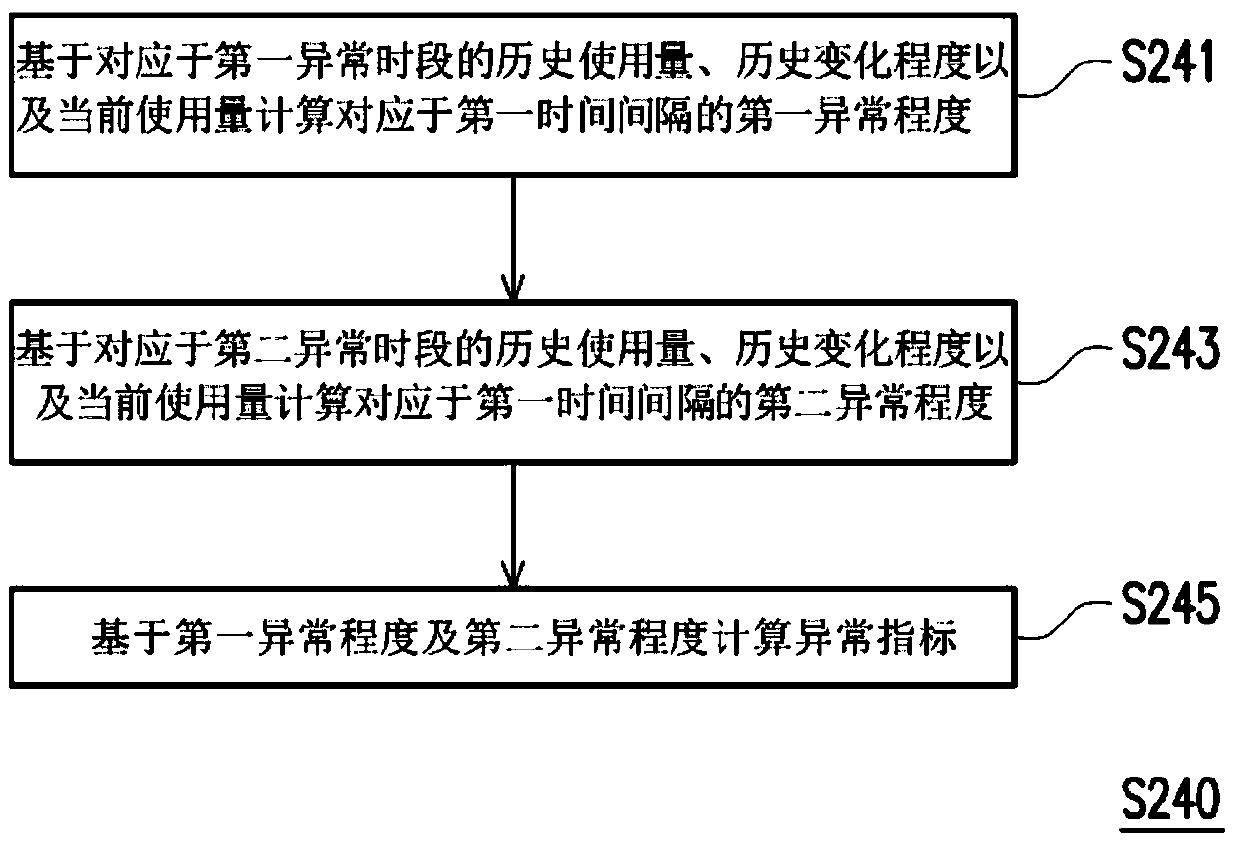
[0021] In order to help users quickly understand the abnormal peak period of the operating system or the degree of abnormality of the operating system at different time intervals, the present invention provides an abnormal detection method and device for detecting abnormal operation of the operating system. Readers will be able to understand the creative spirit of the present invention through the following contents.
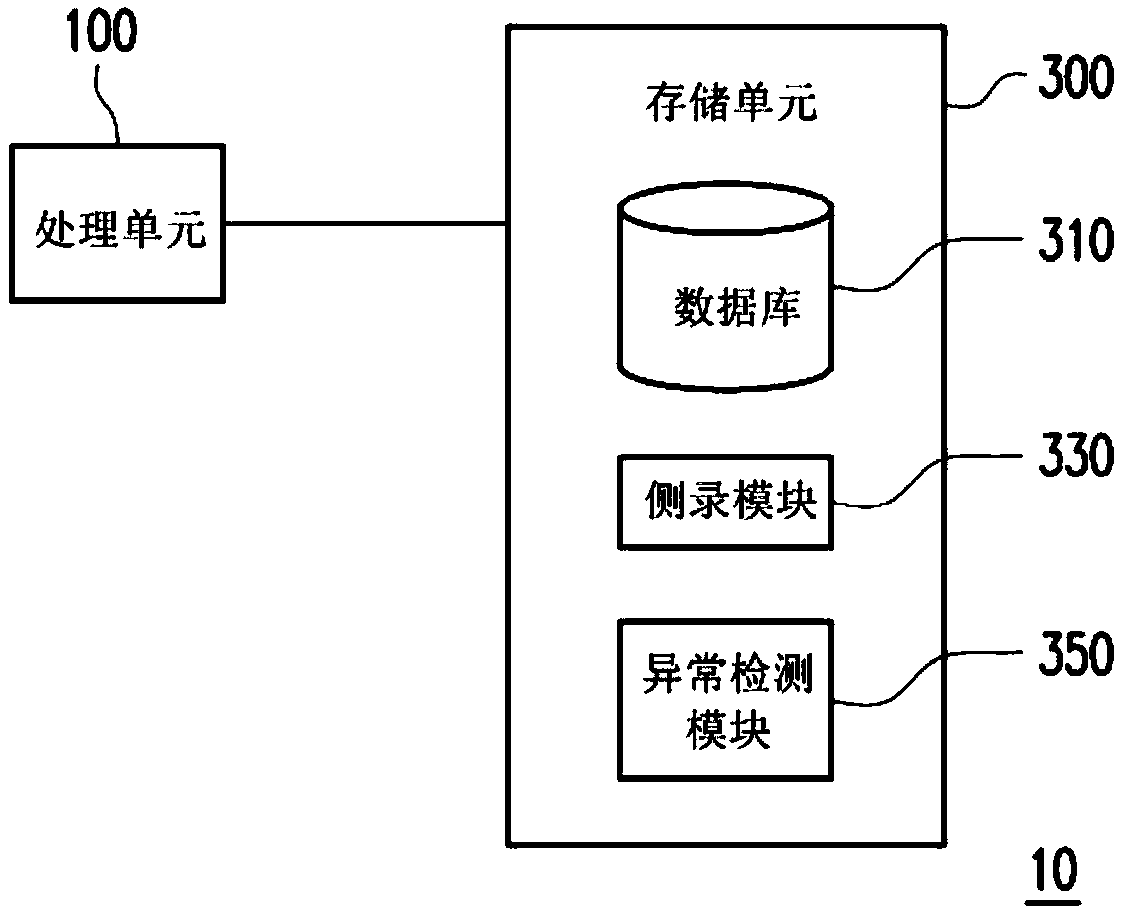
[0022] figure 1 It is a schematic diagram showing an abnormality detection device 10 according to an embodiment of the present invention. The device 10 may include a processing unit 100 and a storage unit 300 .
[0023] The storage unit 300 is used for storing various software, data and various program codes required for the operation of the device 10 . The storage unit 300 can be, for example, any form of fixed or removable random access memory (Random Access Memory, RAM), read-only memory (Read-only Memory, ROM), flash memory (Flash Memory), hard disk ( Har...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com