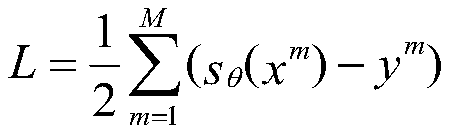Rapid network attack backtracking mining method based on convolutional neural network and application
A convolutional neural network and network attack technology, which is applied in the field of fast network attack backtracking mining, can solve the problem of lack of traceability and classification of network attacks, and achieve the effect of improving attack backtracking mining speed, saving reconstruction sequence time, and extensive engineering practical value
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
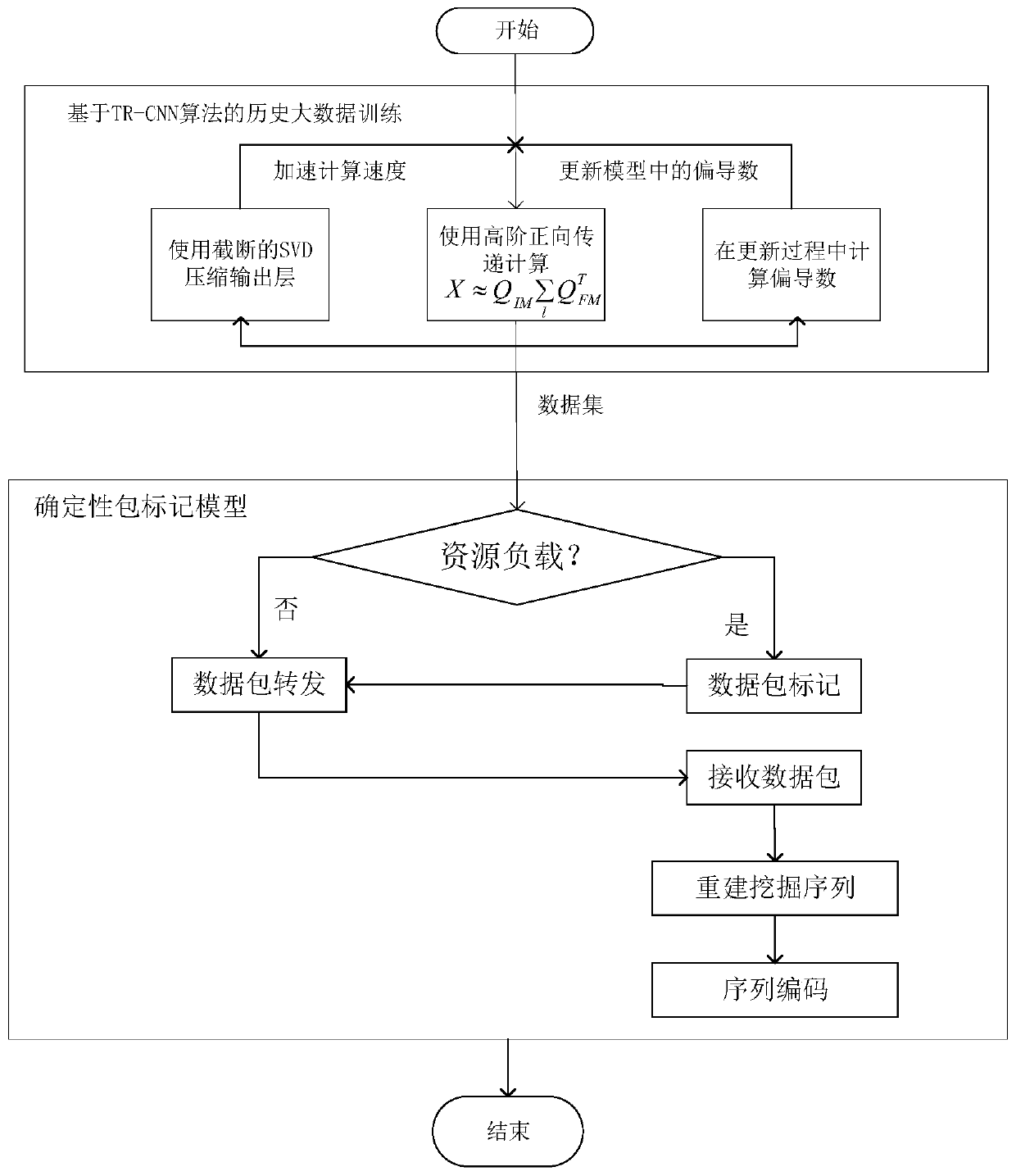
[0035] The backward fast backtracking algorithm based on the backward convolutional neural network (TR-CNN) comprises the following steps:
[0036] Step (1): Dataset construction. The truncated support vector machine is introduced in the convolutional neural network algorithm to speed up the training speed of high-dimensional big data analysis.
[0037] Step (2): Dataset training. First, we pre-train TR-CNN with high-order forward pass to obtain the output of each layer. Then, we construct the loss function and try to minimize it. Specifically, the loss function Expressed as:
[0038]
[0039] where (x; y) is a tensor object and s refers to the dimension. get the minimum First, we assign the tensor's weights as random numbers. Then, the tensor's weights will be updated.
[0040] Step (3): Solve the data load problem using a deterministic packet marking model to reconstruct the mining sequence.
[0041] In step (2), the loss function is used to measure the gap bet...
Embodiment 2
[0043] In order to improve the accuracy of TR-CNN training in step 1 in embodiment 1, preferably in the TR-CNN training process, the corresponding calculation of key steps is divided into three parts:
[0044] The first part is to compute the following sequence using a higher order forward pass:
[0045]
[0046] Then, the second is to compress the output layer using a truncated SVM to speed up training.
[0047] The last one is to compute the partial derivatives during the update. Higher-order partial derivatives are computed by efficiently designing higher-order backpropagation. Finally, raw data can be used for training as useful information, which helps keep intruders out of the network.
Embodiment 3
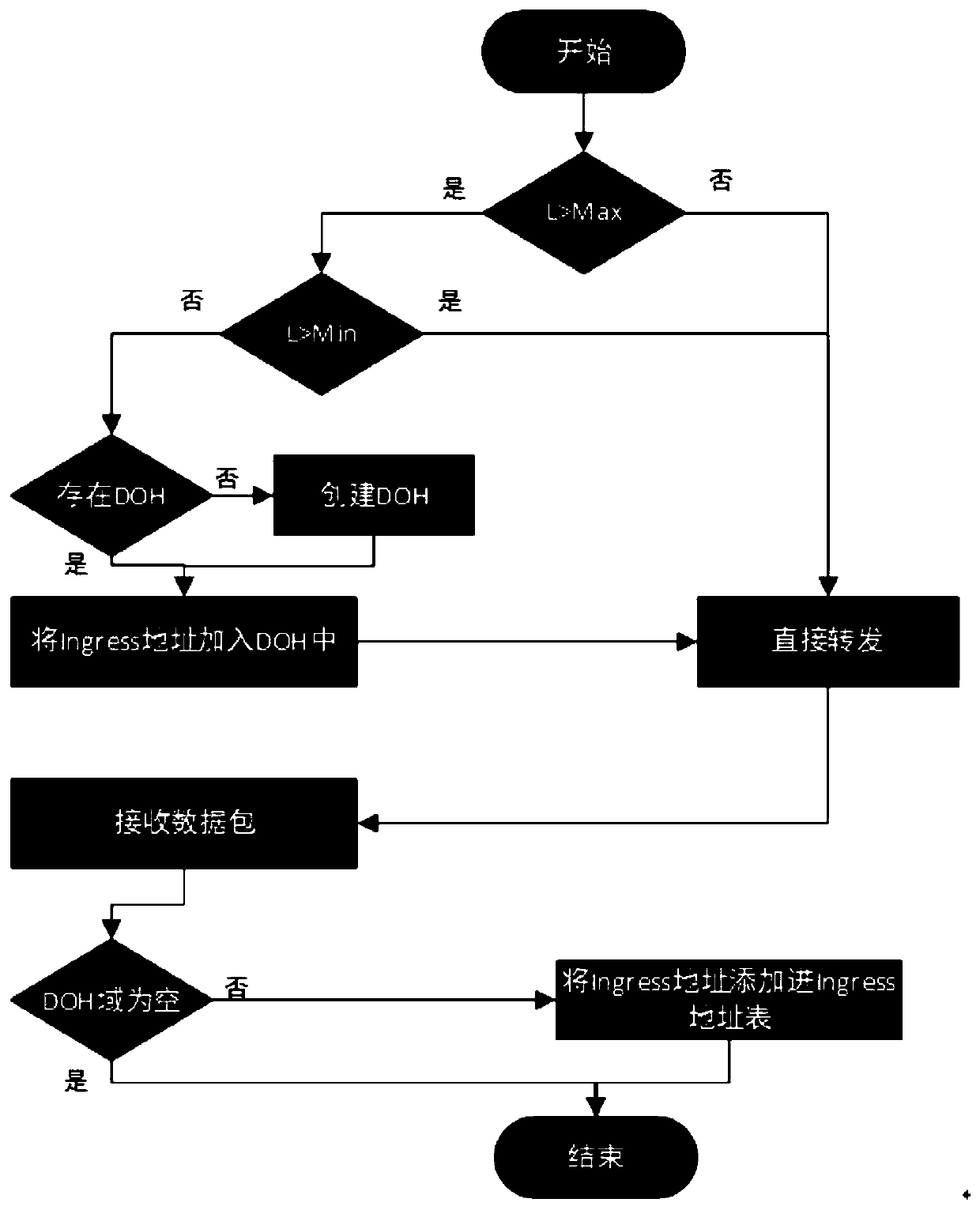
[0049] In order to improve the problem of data load in embodiment 1, as a preferred manner, the processing process of the deterministic packet marking model includes the following steps:
[0050] Step (1): Introduce two router load thresholds, Min and Max.
[0051] Step (2): If the load is below Min or above Max, the model will be marked as no packet; if the load is between Min and Max, every packet will be marked.
[0052] Step (3): Determine whether the Destination Options Header (DOH) exists, if it already exists, the router will only encode the ingress address, and then forward the data packet. If not present, the ingress address shall be encoded by creating a DOH, and the packet shall be transmitted.
[0053] Step (4): During the rebuilding process of the program, it should be decided whether to search for DOH according to the attacked host. If it exists, the attacked host will extract the address and put the address into the address table.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com