Interactive key security authentication method and system
A technology of security authentication and authentication system, applied in the field of interactive key security authentication method and system, can solve the problems of terminal manufacturer's shutdown, inability to activate the terminal manufacturer's production, poor matching degree, etc., and achieve the effect of meeting the authentication requirements.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0049] A method for interactive key security authentication, comprising the steps of:
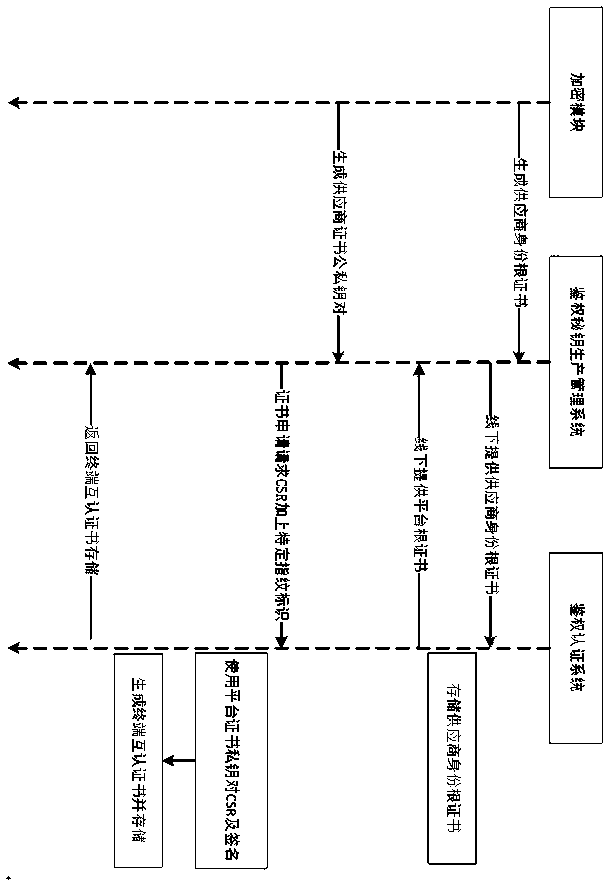
[0050] S10. Generate terminal mutual authentication certificate: respectively generate supplier identity public-private key pair and third-party certificate public-private key pair, authentication key production management system and authentication authentication system respectively Interactively verify the signature for the pair, generate the terminal mutual authentication certificate of the IoT terminal device, and the authentication authentication system synchronously stores the terminal mutual authentication certificate.
[0051] In this step, the terminal mutual authentication certificate is generated, such as figure 1 shown, including:
[0052] The offline authentication key production management system and the authentication certification system provide supplier identity root certificates and third-party root certificates respectively.
[0053] The encryption modules of the offline...
Embodiment 2
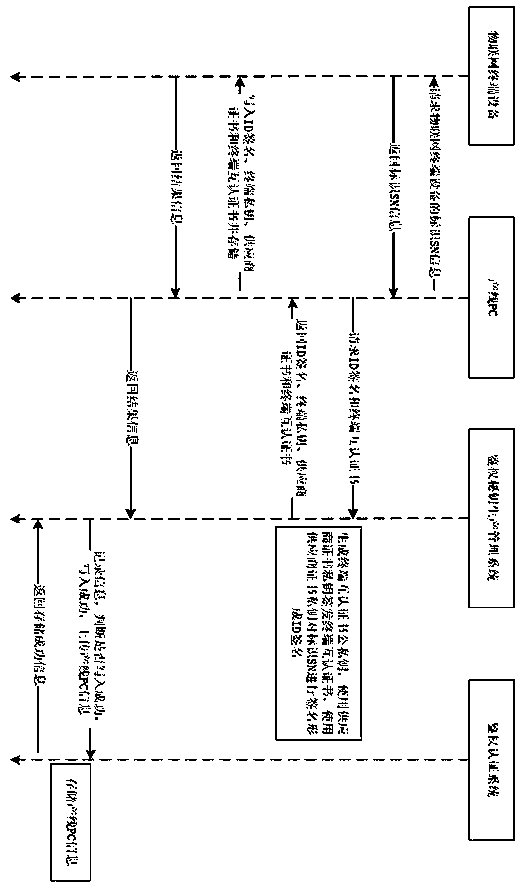
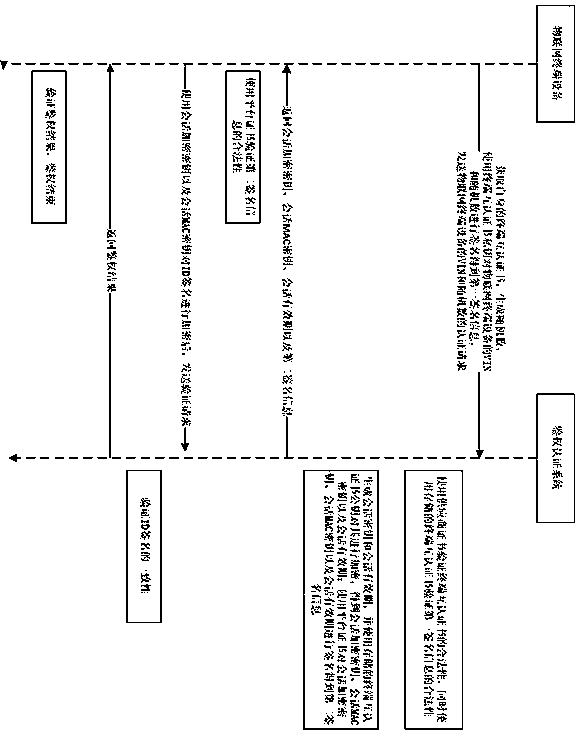
[0087] An interactive key security authentication system adopts the interactive key security authentication method described in Embodiment 1 to realize security authentication.
[0088] The system includes an interactive key generation module, a signature module and a verification module.
[0089] The interactive key generation module is used to generate the supplier identity public-private key pair, the third-party certificate public-private key pair and the certificate application request CSR according to the specified encryption algorithm.
[0090] The interactive key generation module includes a supplier's first encryption module and a third party's second encryption module.
[0091] The signature module is used to interactively verify the signature of the supplier identity public-private key pair and the third-party certificate public-private key pair, and generate the terminal mutual authentication certificate of the IoT terminal device.
[0092] The signature module in...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com