Blockchain consensus method and system
A blockchain and consensus technology, applied in the blockchain field, can solve problems such as failure, achieve low transaction delay, save computing resources, and improve the effect of low security margins
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
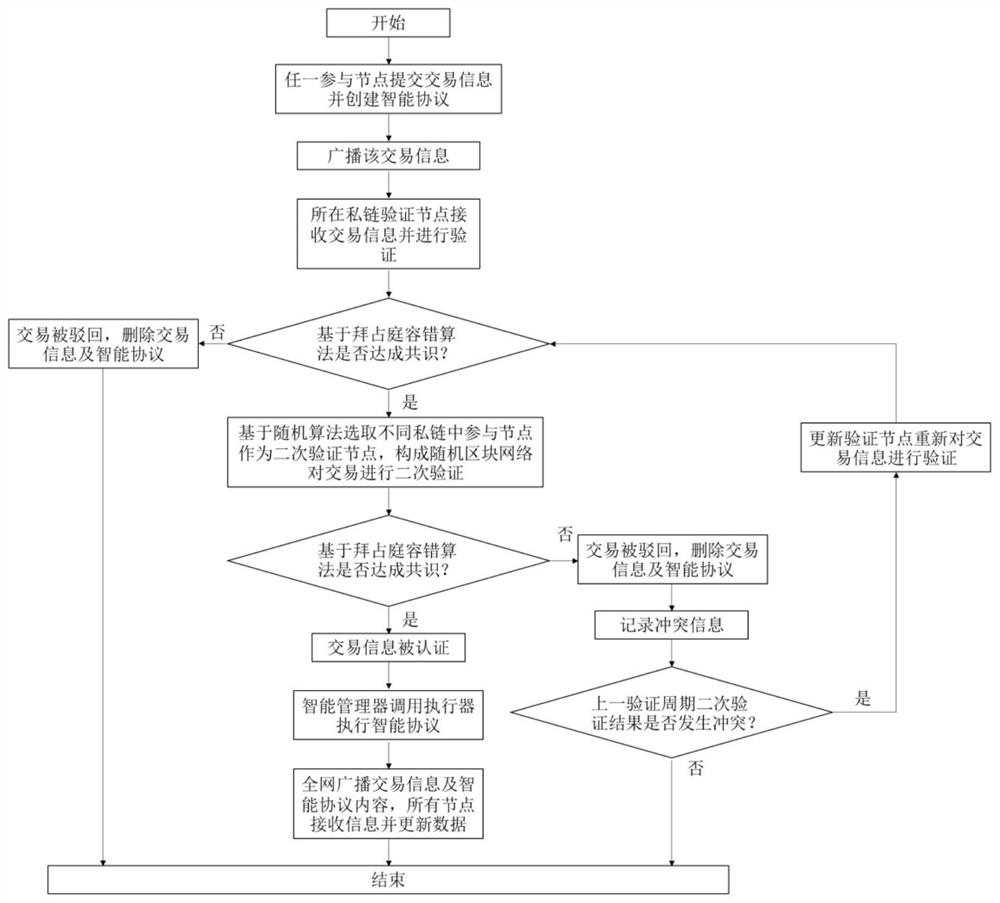
[0026] First, when any participating node submits a request information, the information is transmitted to the blockchain network, and a new block is generated. The new block contains the request information and digital agreement, and the request information contains specific transaction content, such as A pays a certain currency to B. The corresponding digital agreement includes the operations that participants in the trader should perform after the transaction is authenticated, such as confirming that A pays B, and B provides A with corresponding goods or gives corresponding feedback. The request information is broadcast in the private chain, and the verification node verifies the request information, and verifies whether the digital signature sending the request information comes from a legal participating node. Then verify the legitimacy of the requested operation. If the verification node cannot reach a consensus based on the Byzantine fault-tolerant algorithm, the reque...
Embodiment 2
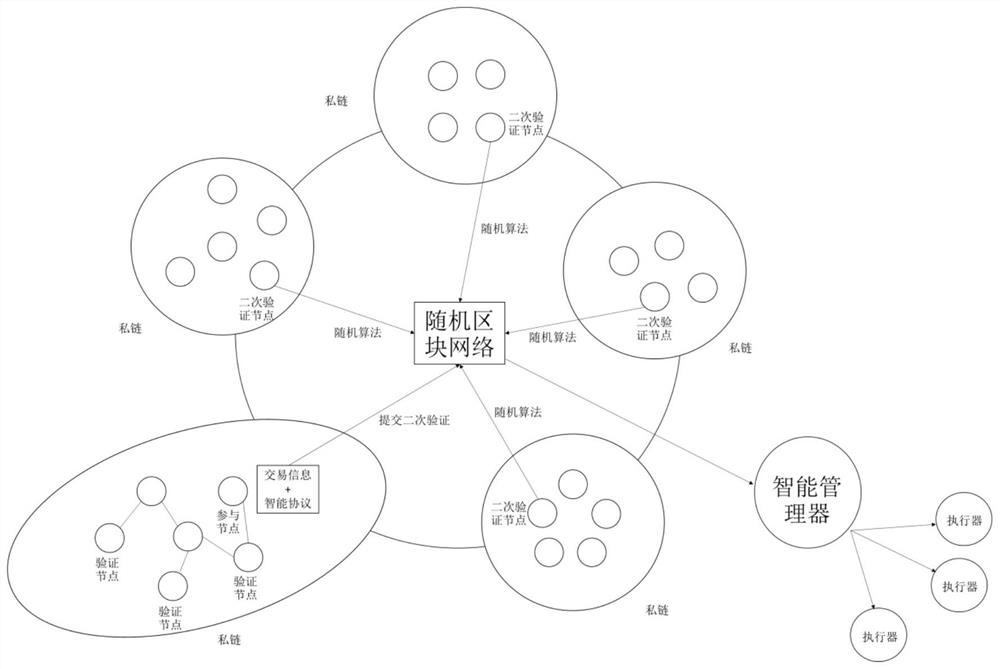
[0028]First, use the same procedure as in Example 1 to initiate a transaction. If the private chain verification nodes based on the Byzantine fault-tolerant algorithm reach a consensus, the requested information will pass the preliminary verification. At this time, the security boundary of the verification result is that no more than 33% of the nodes are attacked or If there is malicious collusion, the verification result is reliable. If there are N malicious nodes in the network, the reliability of the results can only be guaranteed when the total number of nodes is greater than or equal to 3N+1. In order to improve the security and reliability of the network, after the request information passes the preliminary verification, it is submitted to the public chain, and the secondary verification nodes are selected in different private chains based on random algorithms to form a random block network to perform secondary verification of the request information . During the second...
Embodiment 3
[0030] First, use the same procedure as in Example 1 to initiate a transaction. If the private chain verification nodes based on the Byzantine fault-tolerant algorithm reach a consensus, the requested information will pass the preliminary verification. At this time, the security boundary of the verification result is that no more than 33% of the nodes are attacked or If there is malicious collusion, the verification result is reliable. If there are N malicious nodes in the network, the reliability of the results can only be guaranteed when the total number of nodes is greater than or equal to 3N+1. In order to improve the security and reliability of the network, after the request information passes the preliminary verification, it is submitted to the public chain, and the secondary verification nodes are selected in different private chains based on random algorithms to form a random block network to perform secondary verification of the request information . If a consensus i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com