Sensitive data detection system for large-scale SSL/TLS encrypted session flow
A technology of sensitive data and detection system, applied in the field of network security, can solve the problems of inability to adapt to large-scale encrypted session stream processing, high task processing delay, affecting host business performance, etc., to improve the ability of rapid detection and processing, and improve parallelism The effect of processing power
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] The present invention will be further described below in conjunction with the accompanying drawings.
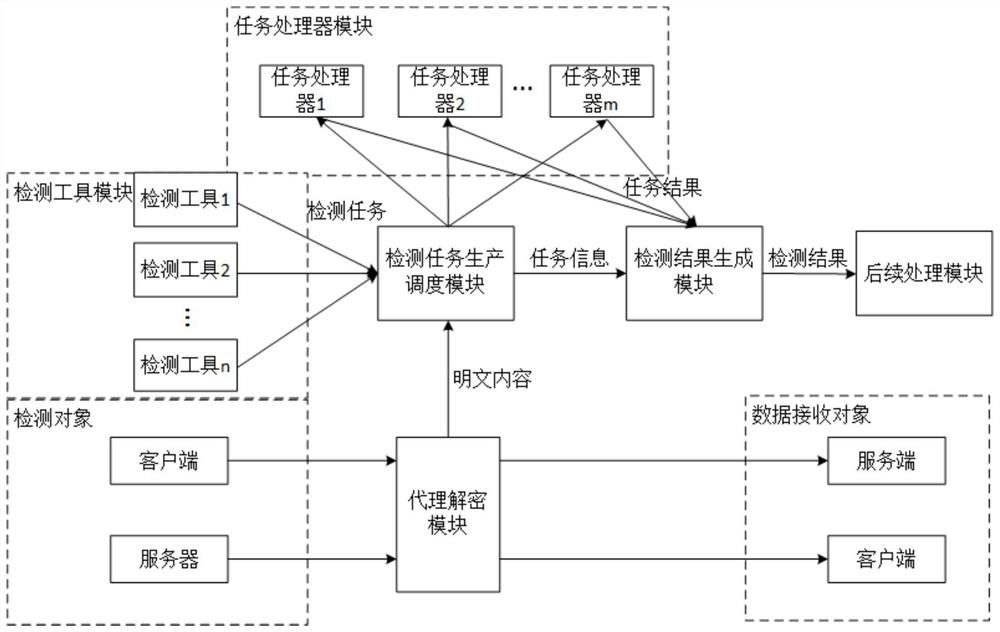
[0033] like figure 1 As shown, a kind of sensitive data detection system facing large-scale SSL / TLS encrypted session flow of the present invention includes:
[0034] The proxy decryption module is set at the Internet entry and exit gate of the detection object, and acts as an intermediate proxy for the SSL / TLS encrypted data transmission process, and outputs plain text content;
[0035] The detection task production scheduling module calls the detection tool to generate the detection task and task information, and schedules the task processor to execute the detection task, and at the same time sends the task information to the detection result generation module;
[0036] The task processor module is used to perform detection tasks and generate task results;
[0037] Detection tool module, used to detect sensitive data contained in plaintext content;
[0038] The de...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com