Patents
Literature
40results about How to "Does not affect business" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
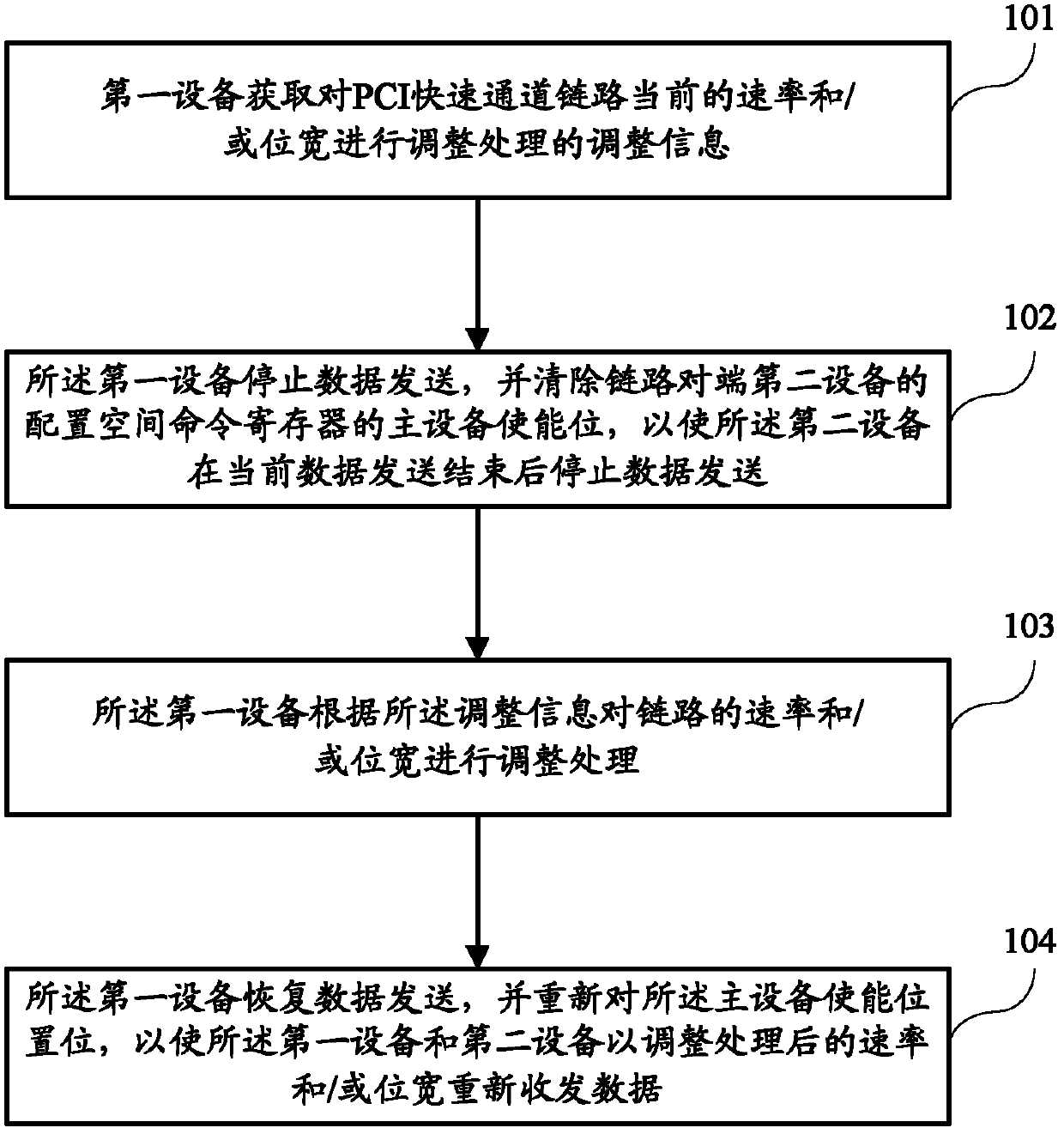
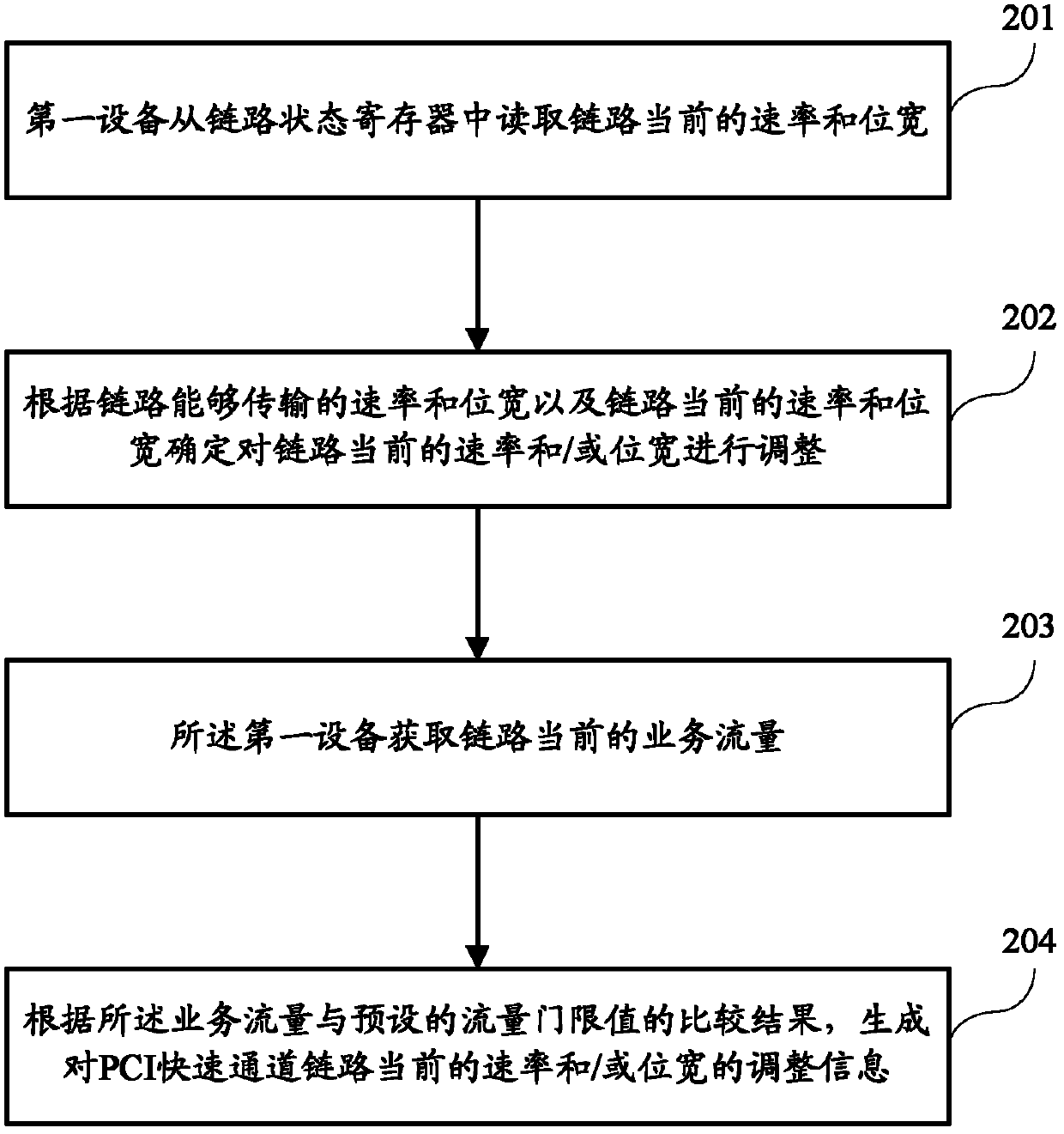
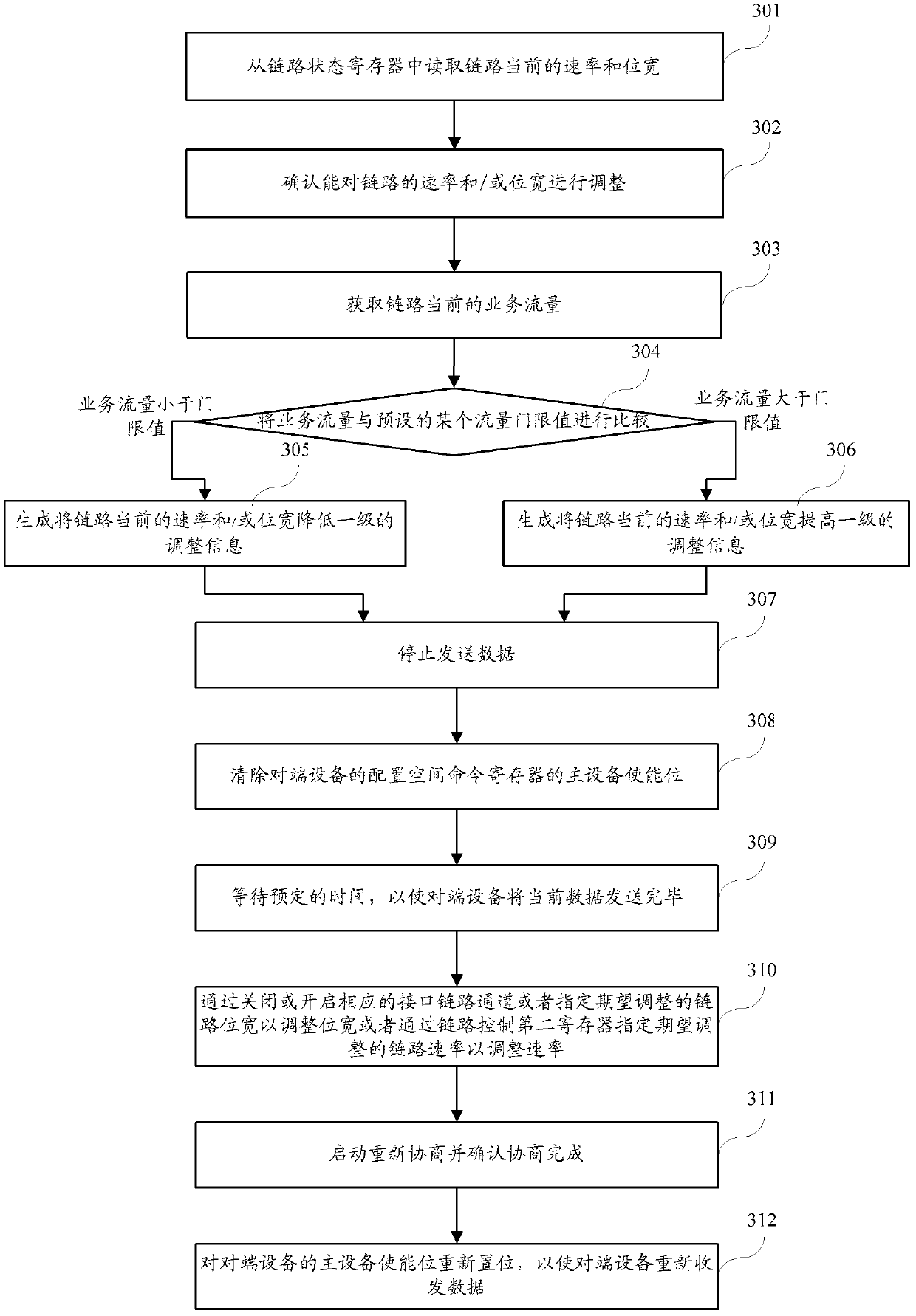
Pci fast channel device, link energy management method and system
ActiveCN102439916AEnable energy managementDoes not affect businessError preventionDigital data processing detailsProcessor registerData transmission
The embodiment of the invention discloses a PCI fast channel device, a link energy management method and a system; wherein, a PCI fast channel link energy management method comprises the steps of using a first device to obtain the adjustment information for adjusting the current speed and / or bit width of a PCI fast channel link; making the first device stop transmitting data and eliminating a main device enabling bit of a configuration space command register of a second device at the opposite end of the link to make the second device stop transmitting data after the current data is sent; using the first device to adjust the current speed and / or bit width of the link according to the adjustment information; making the first device recover data transmission and positioning the main device enabling bit again to make the first device and the second device adjust the processed speed and / or bit width to send and receive data again. The embodiment of the invention can guarantee that the dynamic regulation of the PCI fast channel during the link energy management can be realized while the businesses of the link are not affected.
Owner:HUAWEI TECH CO LTD
Information sending method and device
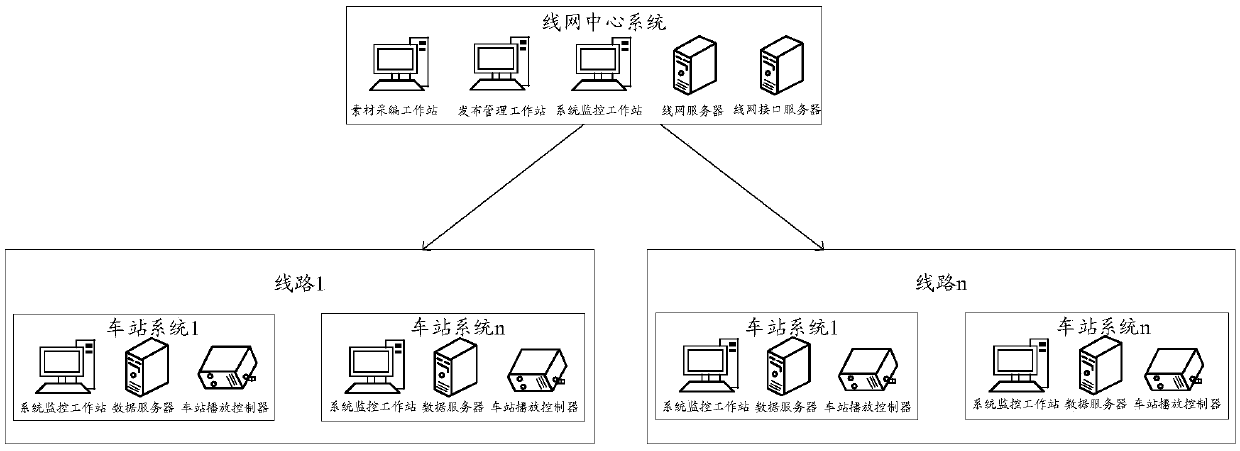
ActiveCN105501258ADoes not affect businessRailway traffic control systemsBroadcastingProcess information
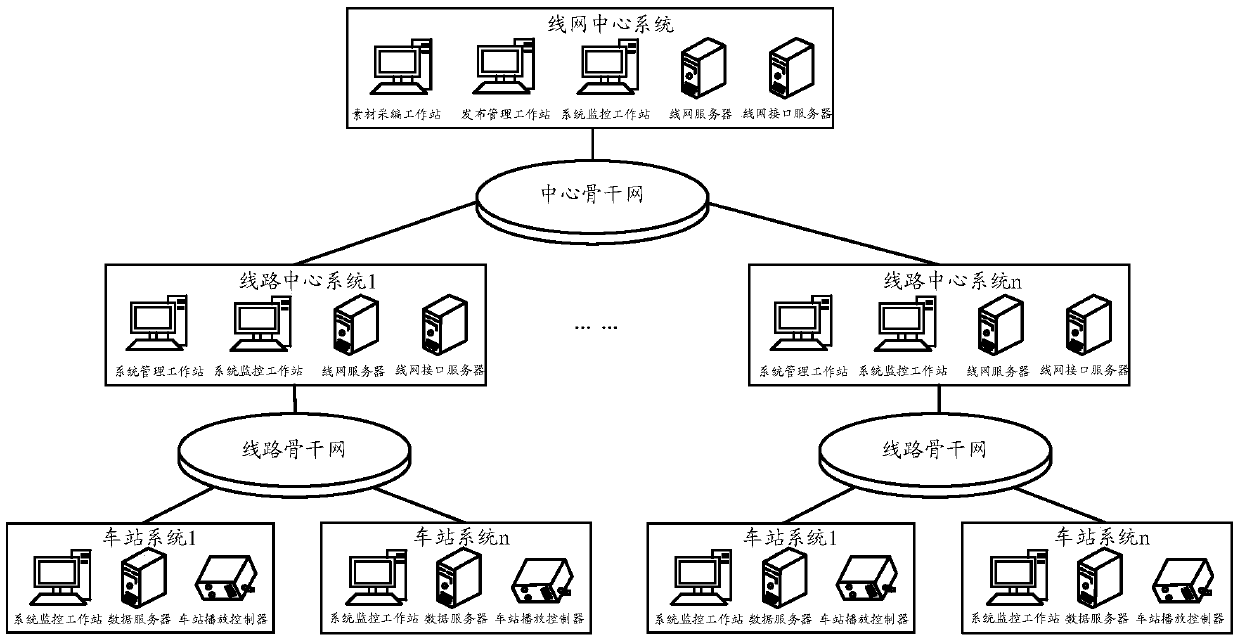
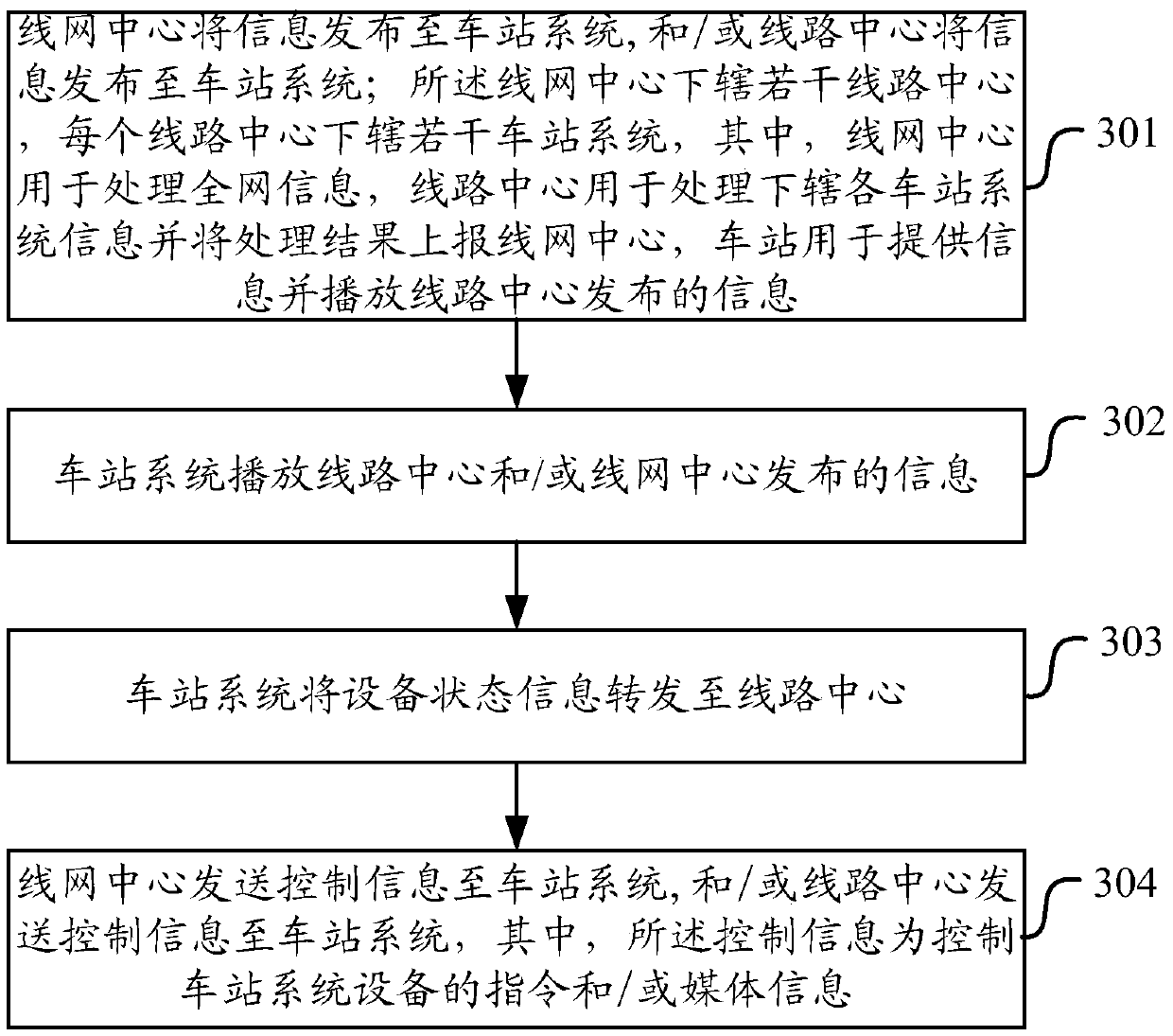
The invention discloses an information sending method and device. The information sending method comprises that a line net center issues information to station systems and / or line centers issue information to station systems; the line net center controls several line centers, each line center controls several station systems, the line net center is used for processing all net information, each line center is used for processing information of station systems controlled by the line center and reports the processing result to the line net center, and each station is used for providing information and broadcasting information issued by the corresponding line center; each station system broadcasts information issued by the corresponding line center and / or the line net center; each station system forwards equipment state information to the corresponding line center; the line net center sends control information to the station systems and / or the line centers send control information to the station systems, and the control information is an instruction for controlling the equipment of the station systems and / or media information. According to the invention, after the line net center is broken down, the line centers can replace the line net center to continue the work, and services are not affected.
Owner:QINGDAO HISENSE TRANS TECH
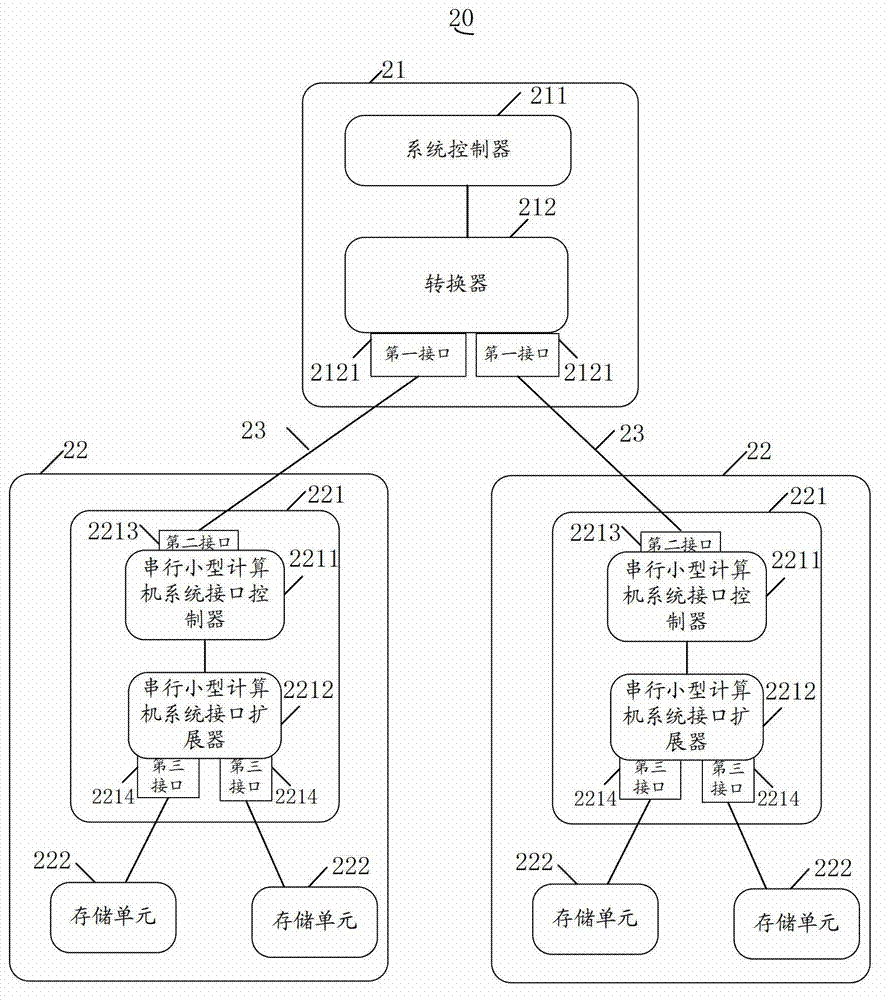
Storage system, storage appliance and control appliance
ActiveCN102968280AReduce access latencyEasy to expandInput/output to record carriersAccess timeStorage cell
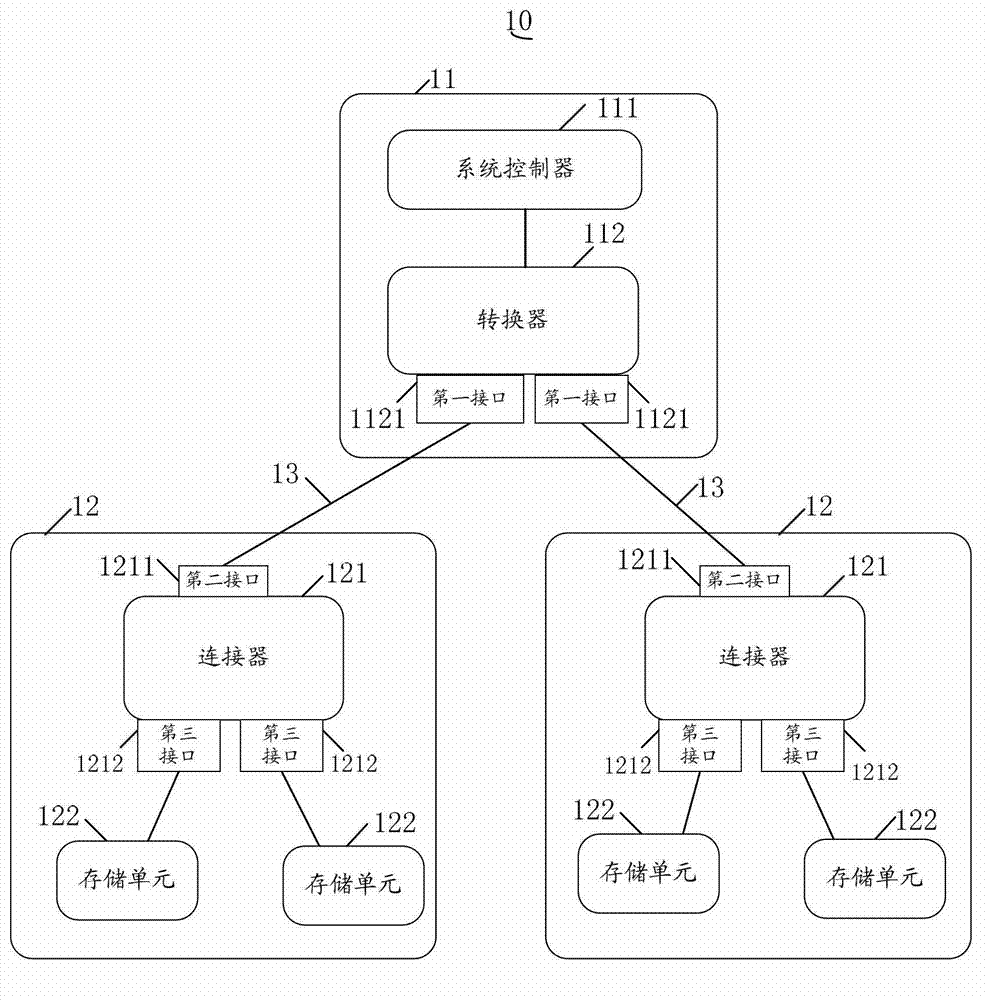
The invention discloses a storage system, a storage appliance and a control appliance. The storage system comprises the control appliance and at least two storage appliances, wherein the control appliance comprises a system controller and a converter, the converter is connected with the system controller, and in addition, the converter is provided with at least two first interfaces, wherein at least two first interfaces are single-passage serial microcomputer system interfaces, or at least two first interfaces are peripheral element expansion x1 interfaces, each storage appliance comprises a connector and a storage unit, each connector comprises a second interface and a third interface, the second interface of each connector is connected with a first interface of the converter, and a third interface of the connector is connected with the storage unit, so the two storage appliances are parallelly connected with the control appliance. Through adopting the mode, the parallel connection of the storage appliance to the control appliance can be realized, the access time delay of the partial storage appliance is reduced, and the storage volume expansion of the storage system is convenient.
Owner:HUAWEI TECH CO LTD
Method, apparatus and device for controlling data recovery speed
ActiveCN108958975ADoes not affect businessRedundant operation error correctionData recoveryReal-time computing
The invention discloses a method, an apparatus, a device and a computer-readable storage medium for controlling the data recovery speed. The method comprises the following steps: determining a corresponding cluster recovery speed based on the current busy degree of a distributed system; determining a corresponding cluster recovery speed based on the current busy degree of the distributed system; determining any storage node to recover data as a target node, multiplying the ratio of the number of data to be recovered by the target node and the number of data to be recovered by the distributed system by the cluster recovery speed to obtain the recovery speed of the corresponding node, and determining the number of tokens allocated to the target node in a unit time as the currently availablenumber of tokens based on the recovery speed of the node; when the data recovery request is received, judging whether the number of tokens allocated to the target node in the current unit time reachesthe currently available number of tokens, if so, refusing issuing of the token to the target node, if not, issuing the token to the target node to indicate that the target node realizes the data recovery. The invention achieves the purpose of controlling the speed of data recovery based on the current situation of the distributed system.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
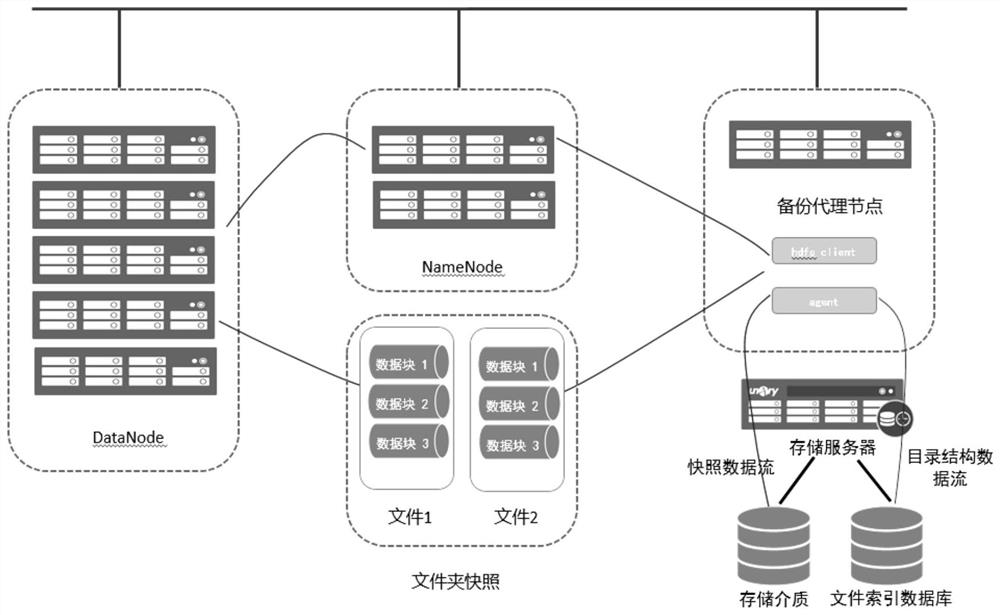
Data backup method and system based on Hadoop distributed file system
PendingCN112800019AAvoid disasterPromote recoveryDigital data protectionDigital data authenticationData integrityExternal storage
The invention discloses a data backup method and system based on a Hadoop distributed file system. The method comprises the steps that a file folder is backed up in a snapshot mode through an HDFS client side, a time point snapshot of the file folder is generated through the client side, and data in the file folder is stored in an external storage medium. The system comprises an HDFS system and a storage server connected with the system, wherein the storage server comprises a storage medium and a file index database; the storage medium is used for storing system file data, and the file index database is used for storing system file metadata. According to the method, the security of the data in the HDFS can be improved, the Hadoop cluster is prevented from disasters, the system data can be automatically and quickly recovered, and the integrity and consistency of company data are protected.
Owner:STATE GRID GANSU ELECTRIC POWER CORP +3
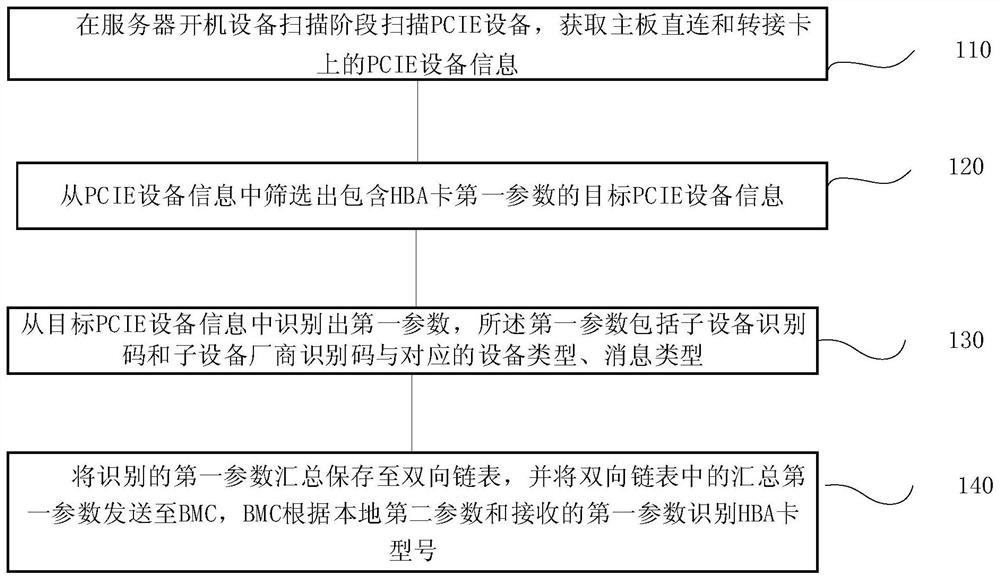
Server HBA card model identification method and system, terminal and storage medium
ActiveCN113626276ADoes not affect running statusEfficient use ofHardware monitoringEnergy efficient computingSoftware engineeringMessage type
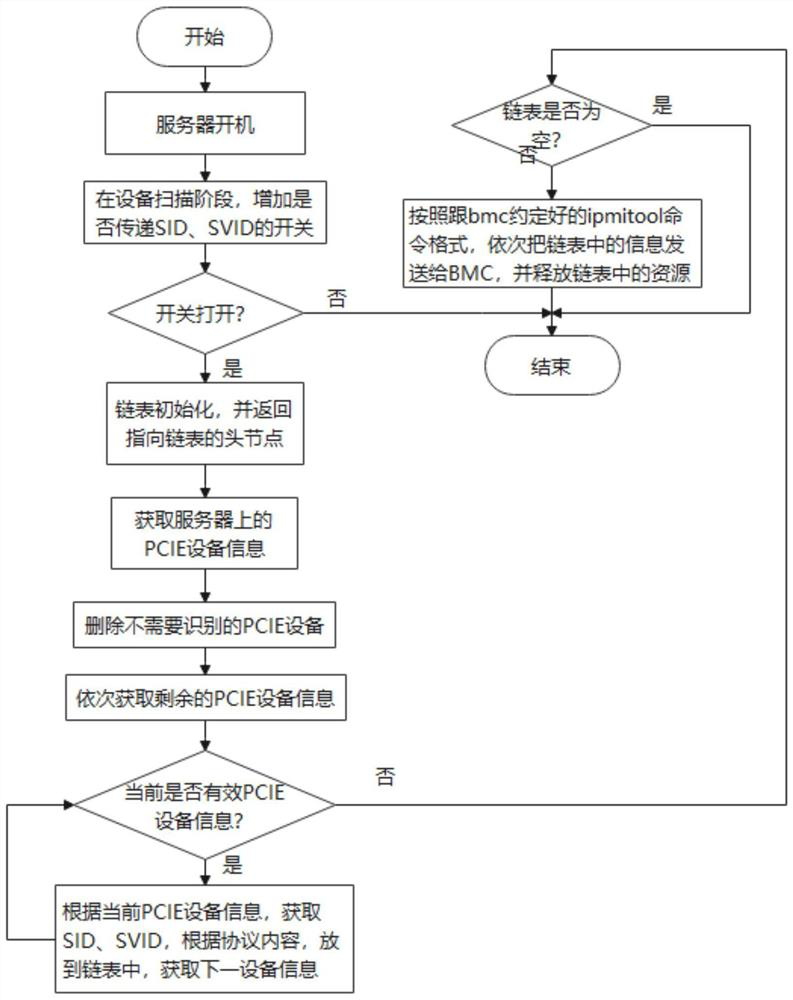
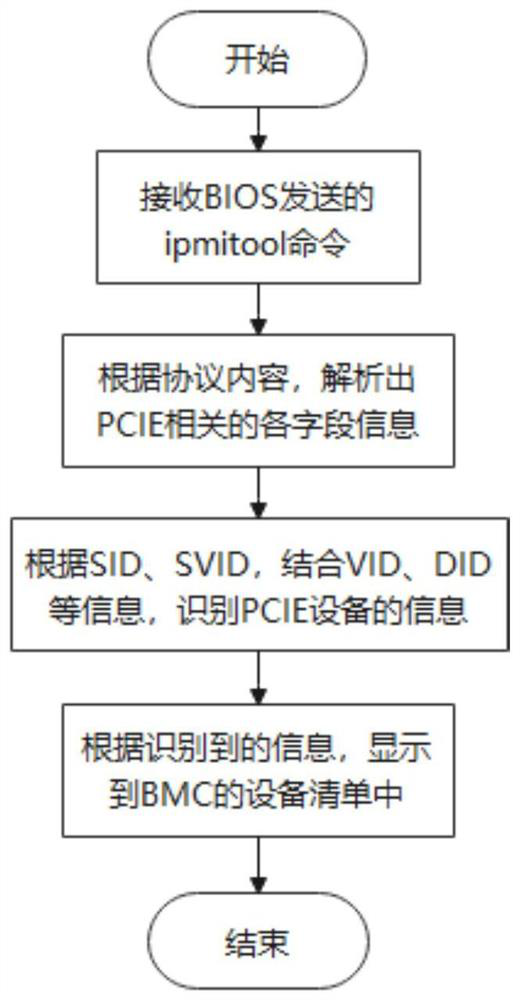
The invention provides a server HBA card model identification method and system, a terminal and a storage medium, and the method comprises the steps: scanning PCIE equipment in a scanning stage of server startup equipment, and obtaining the information of the PCIE equipment on mainboard direct connection and an adapter card; screening out target PCIE equipment information containing the first parameter of the HBA card from the PCIE equipment information; identifying a first parameter from the target PCIE equipment information, wherein the first parameter comprises a sub-equipment identification code, a sub-equipment manufacturer identification code, and a corresponding equipment type and message type; collecting and storing the recognized first parameters in a double linked list, sending the collected first parameters in the double linked list to a BMC, and enabling the BMC to recognize the HBA card model according to the local second parameters and the received first parameters. According to the invention, the detailed model information of the HBA card can be obtained without influencing the running state of the server and the service, so that the HBA card is effectively utilized.
Owner:INSPUR SUZHOU INTELLIGENT TECH CO LTD
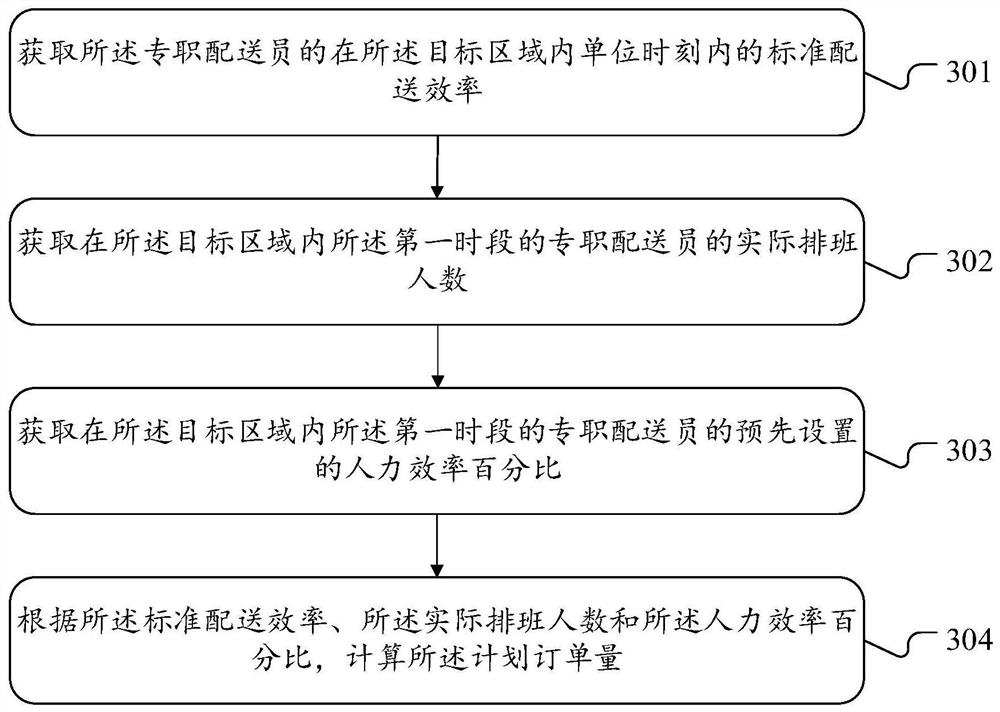
Order scheduling method and device, equipment and storage medium
PendingCN112862319AGuaranteed stabilityDoes not affect businessForecastingResourcesOrder schedulingIndustrial engineering
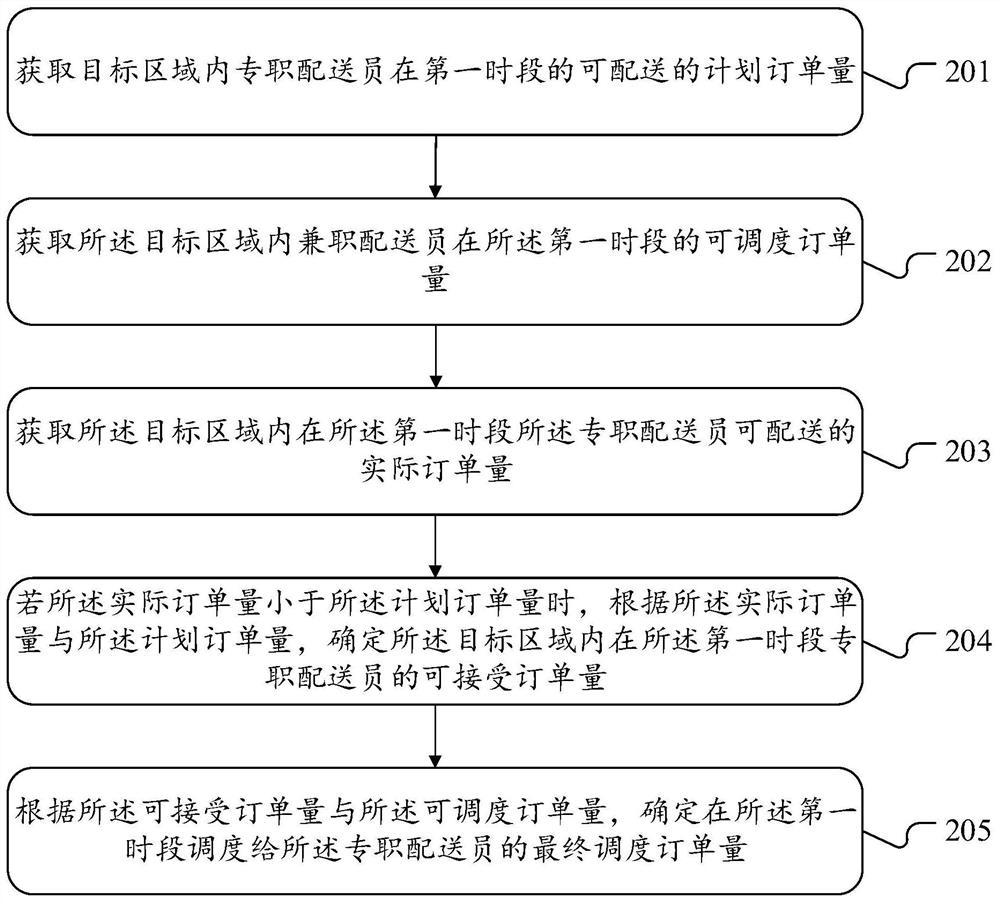
The invention provides an order scheduling method and device, equipment and a storage medium. The order scheduling method comprises the steps of obtaining a dispatchable planned order quantity of a full-time deliveryman in a first time period in a target area; obtaining the dispatchable order quantity of the part-time deliveryman in the target area in the first time period; obtaining an actual order quantity which can be delivered by the full-time deliveryman in a first time period in the target area; if the actual order quantity is smaller than the planned order quantity, according to the actual order quantity and the planned order quantity, determining the acceptable order quantity of the full-time deliveryman in the first time period in the target area; and according to the acceptable order quantity and the dispatchable order quantity, determining a final dispatched order quantity dispatched to the full-time deliveryman in the first time period. According to the invention, part of orders can be dispatched from the part-time deliveryman to the full-time deliveryman, and the delivery efficiency of the full-time deliveryman is improved under the condition that the part-time delivery business is not affected basically.
Owner:北京顺达同行科技有限公司
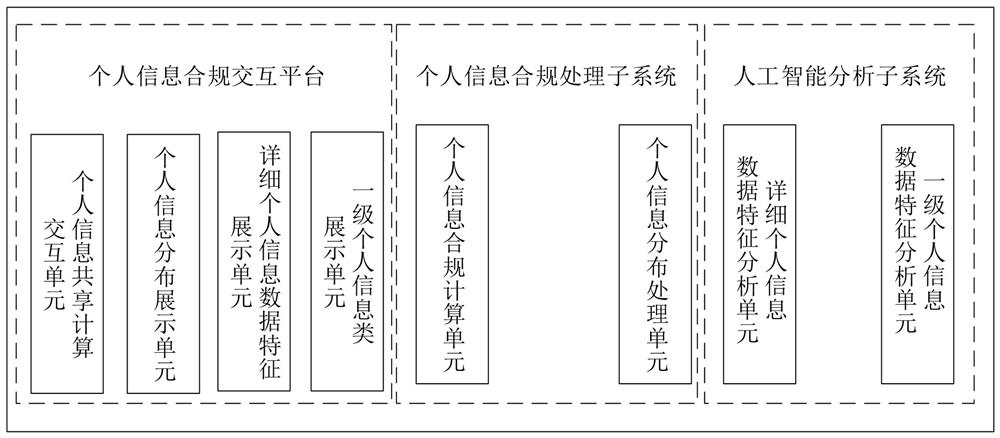
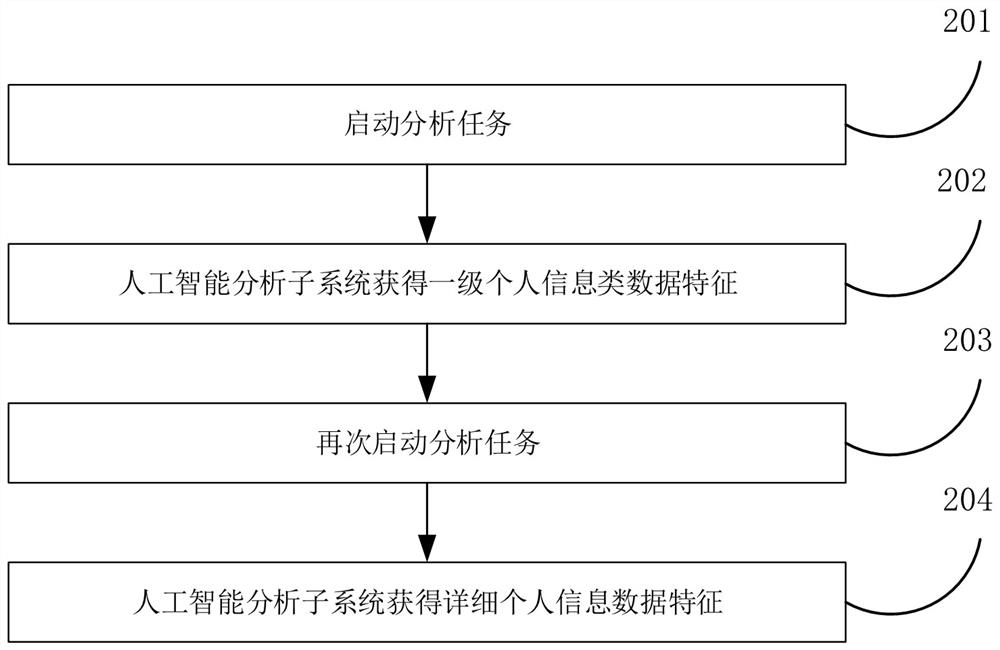
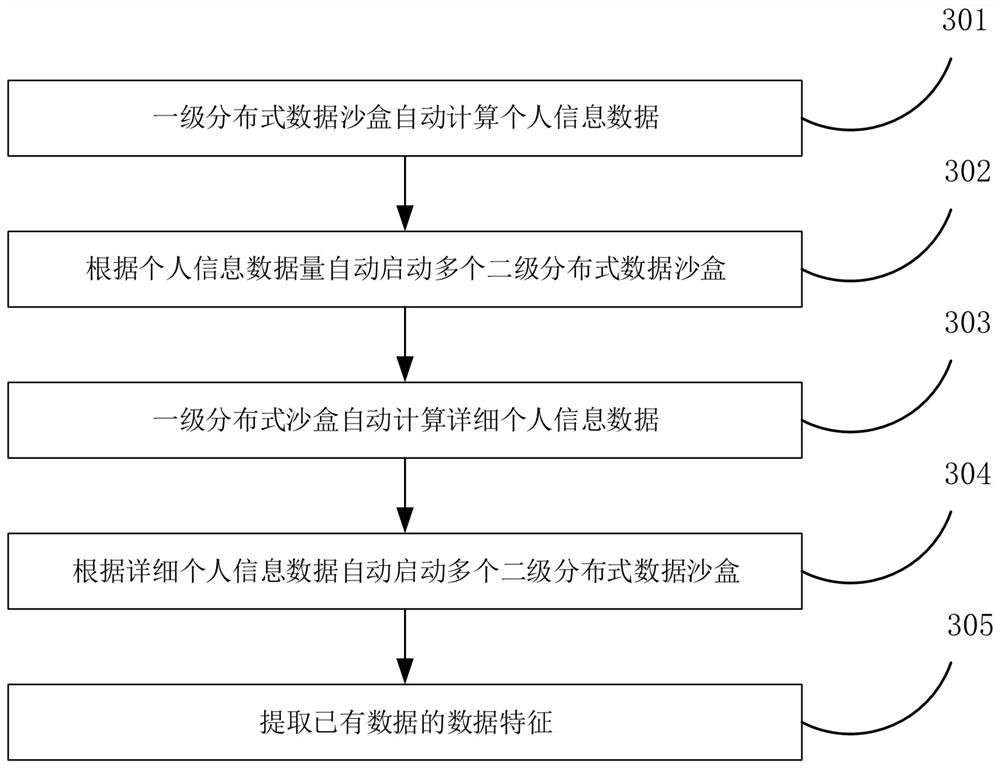
Personal information compliance method and device based on distributed data sandbox
ActiveCN113065126AConvenience to followAddress compliance issuesDigital data protectionPlatform integrity maintainanceEngineeringIntelligence analysis
The invention discloses a personal information compliance method and device based on a distributed data sandbox. An administrator performs primary classification on big data through artificial intelligence, obtains data belonging to a personal information class from the big data and establishes data features of the personal information class. Personal information detailed data feature analysis is carried out on personal information data through artificial intelligence analysis and a distributed data sandbox, and detailed personal information data features are rapidly obtained from large-scale multi-type big data. Furthermore, the compliance of the personal information of the big data, including the distribution compliance of the personal information and the sharing calculation compliance of the personal information, can be further completed through the distributed data sandbox and the data features of the detailed personal information grasped by the administrator. According to the method, the technical problems of distribution and sharing calculation required by personal information compliance in a big data related technology are solved.
Owner:北京数安行科技有限公司
Medical antibacterial elevator panel auxiliary control device
PendingCN112079218AEasy to useDoes not affect normal economic operationLavatory sanitoryElevatorsControl cellStructural engineering
The invention relates to a medical antibacterial elevator panel auxiliary control device. The medical antibacterial elevator panel auxiliary control device comprises a disinfection bottle, a bearing plate and a control panel, wherein control units are arranged on the control panel; each control unit is aligned and matched with one key on an elevator panel; the control units comprise transmission pressing keys, suction cylinders and piston connecting pieces; the transmission pressing keys are matched and opposite to the keys on the elevator panel; when the transmission pressing keys are pressed, the transmission pressing keys can move corresponding to the control panel, and press and trigger the corresponding keys on the elevator panel; the suction cylinders further comprise one-way liquidinlet switches and antibacterial nozzles; the one-way liquid inlet switches communicate with suction cavities and guide cavities; liquid spraying directions of the antibacterial nozzles are towards the transmission pressing keys; and after users finish pressing, return pieces reversely pull back piston ends, and the piston ends reversely slide in the suction cylinders. The device can quickly and conveniently update elevators, can timely disinfect the keys after pressing use each time, and effectively reduces bacterial propagation.
Owner:王丽萍
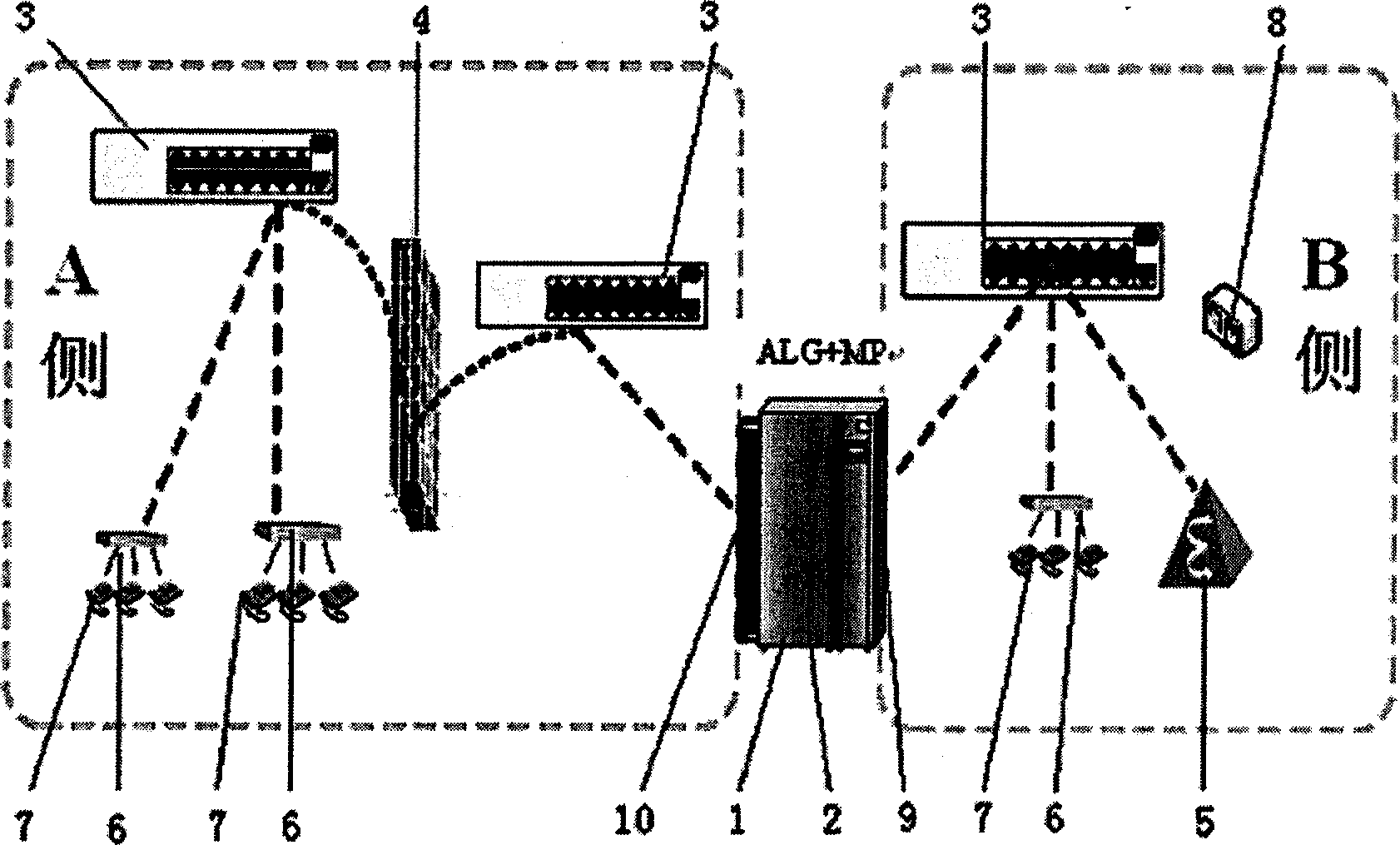
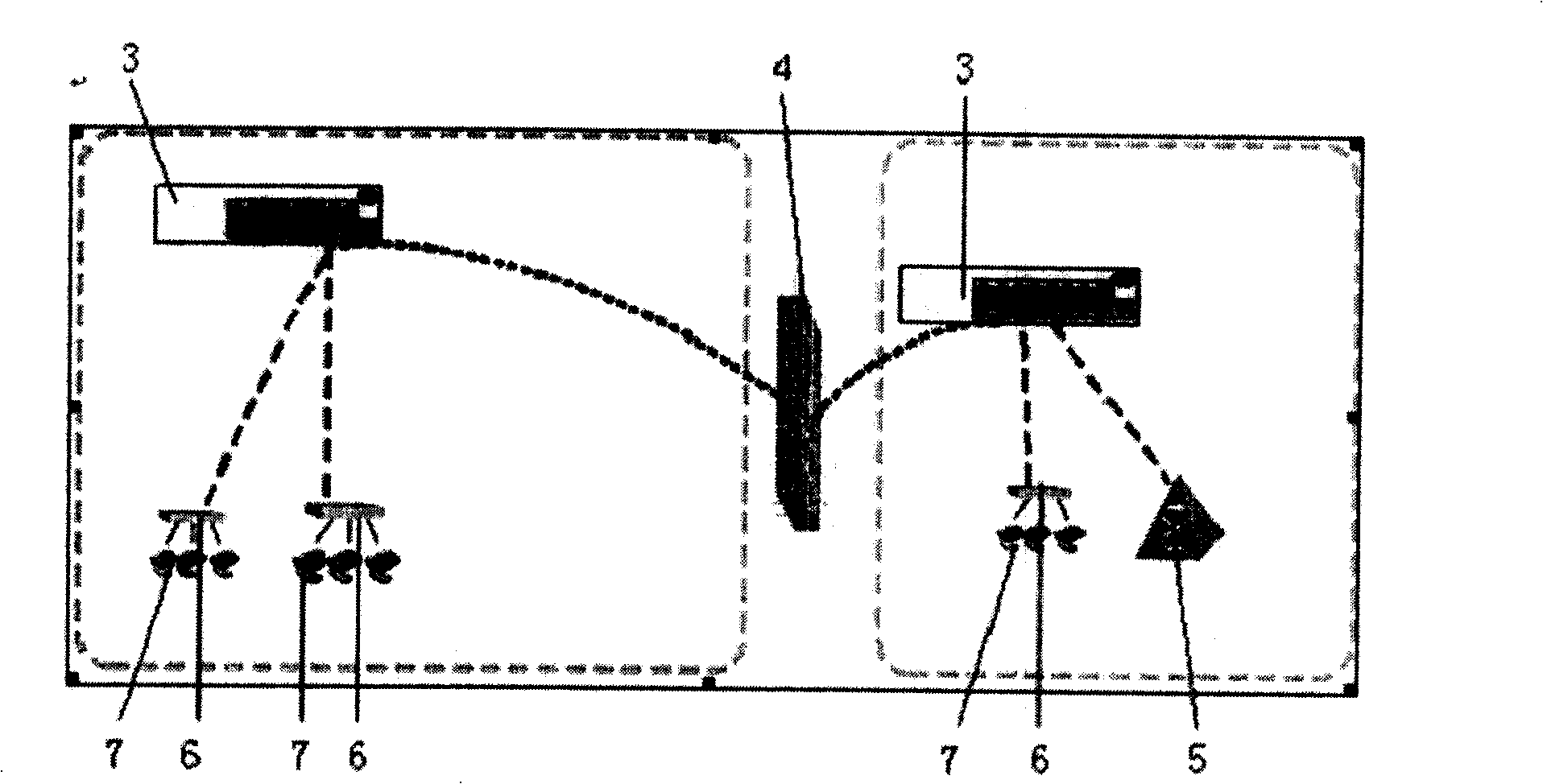
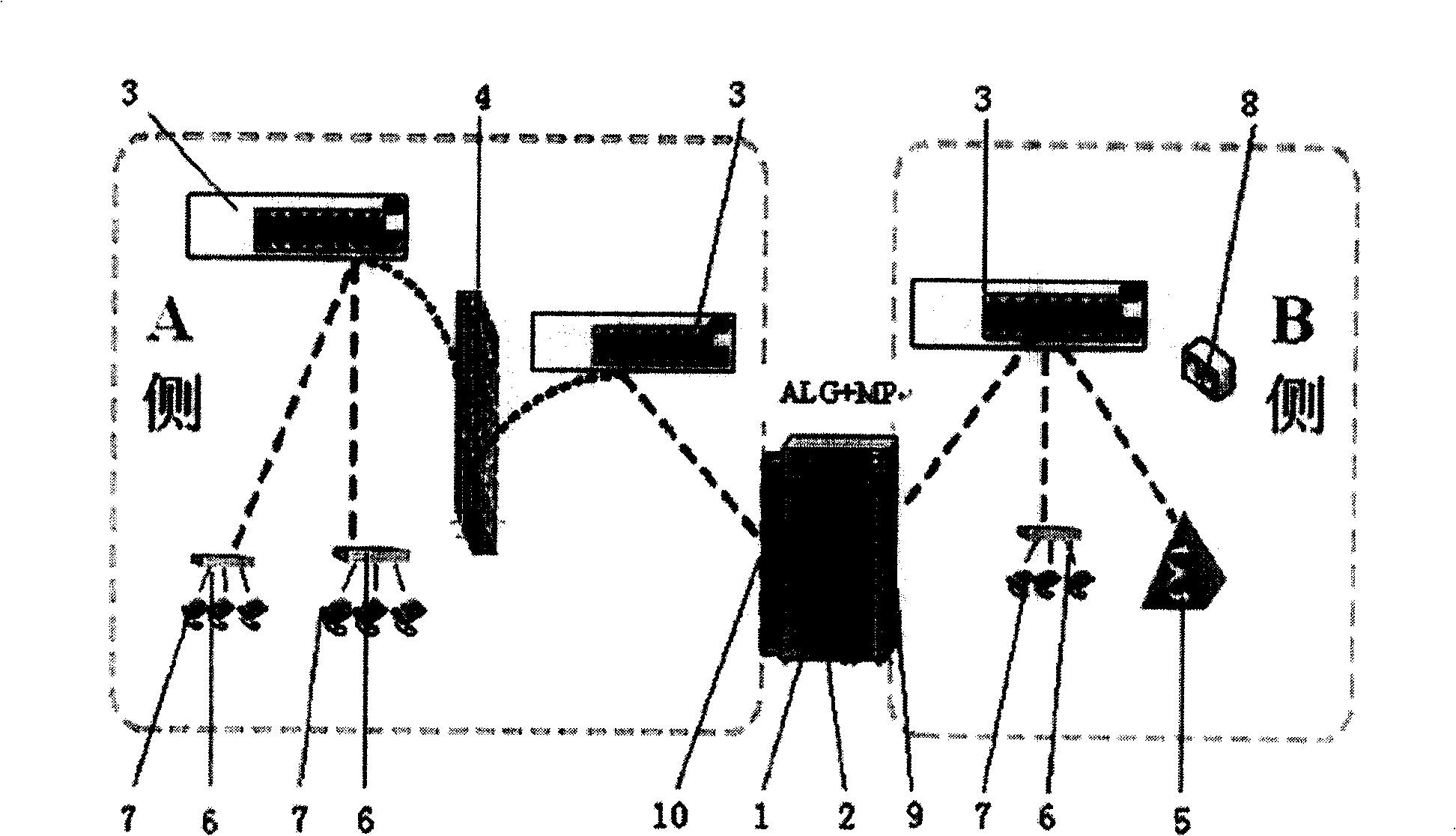
System of soft exchange network passing through firewall based on ALG+MP and its method
InactiveCN1794698ASingle functionImprove shielding effectData switching networksSoftswitchExchange network
This invention discloses a system and a method for passing through fire walls based on the ALG+MP soft exchange network composed of an ALG1, MP2, LAN exchanger3, FW4, MGC5, IAD6, an ordinary phone set 7 and SPY 8, in which, the ordinary phone set is accessed into LAN exchanger3 then to IP by IAD6 to call controlled by MGC5 and matches with MGC5 to finish the penetration of FW4 by ALG1 and MP2, ALG1 sets up the communication connection between terminals and MP2 to realize communication among terminals by the forward of medium flows of MP2.
Owner:武汉市中光通信公司
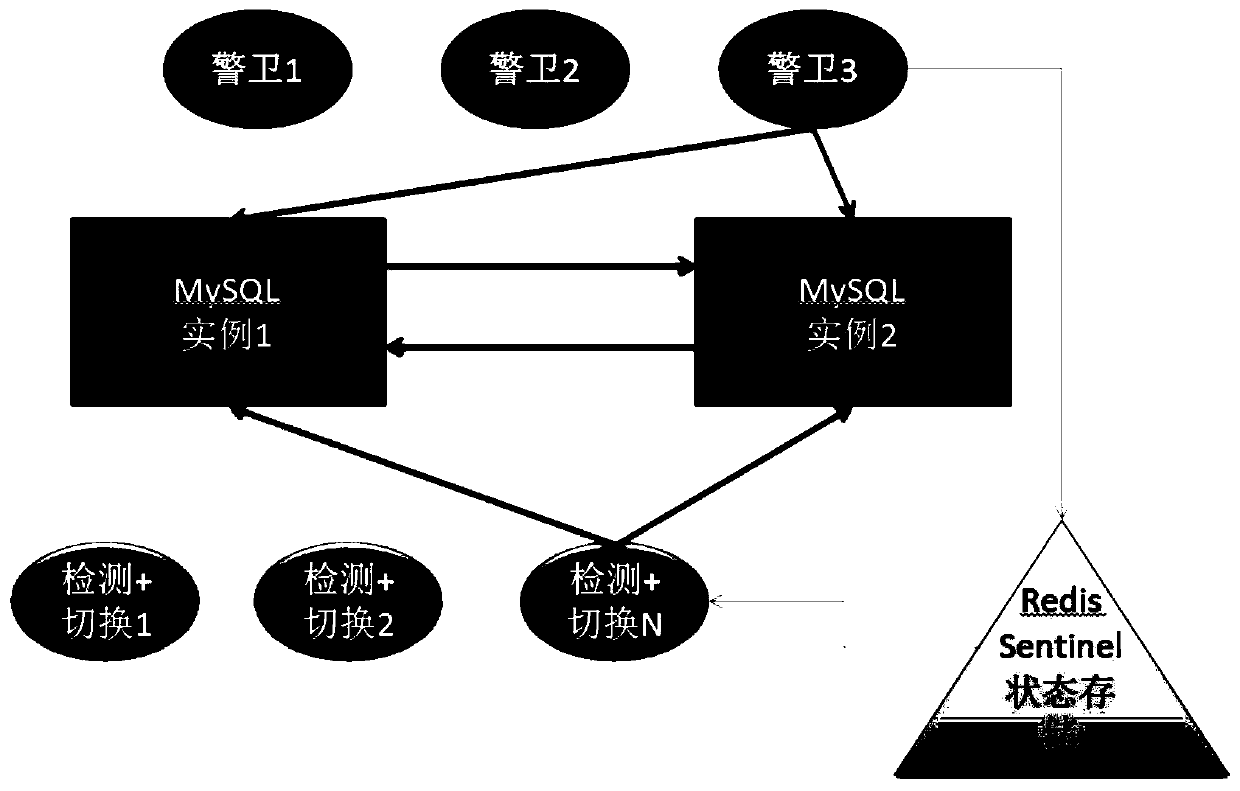
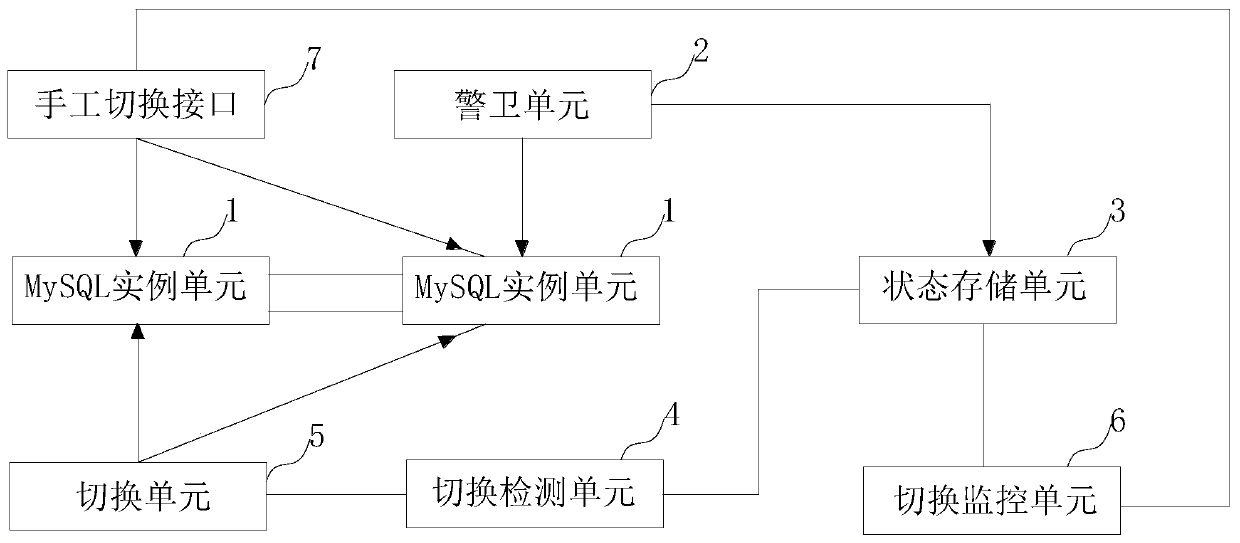
MySQL application layer high-availability system and method suitable for various cloud environments
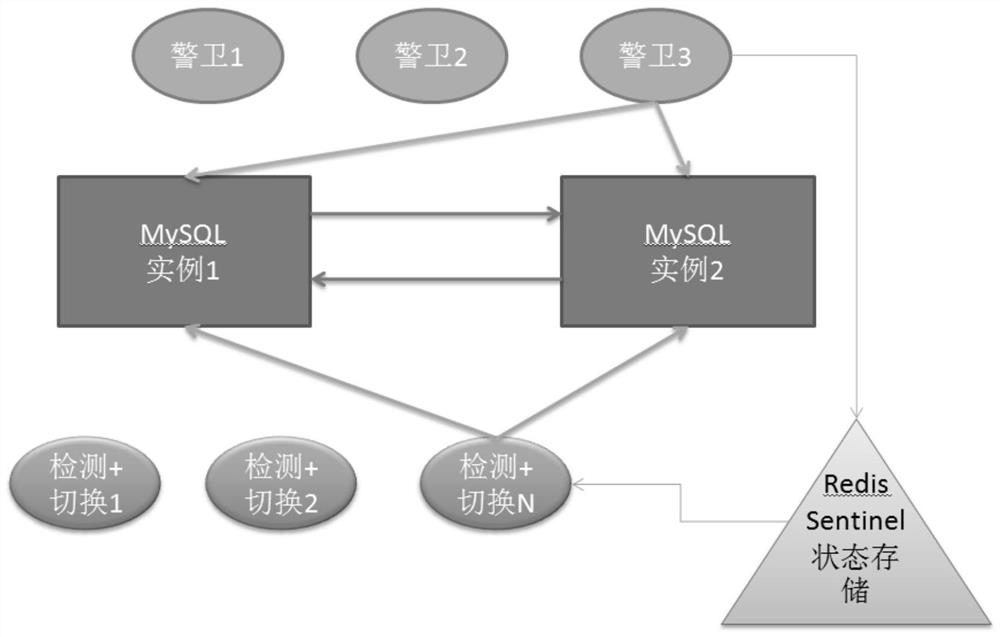
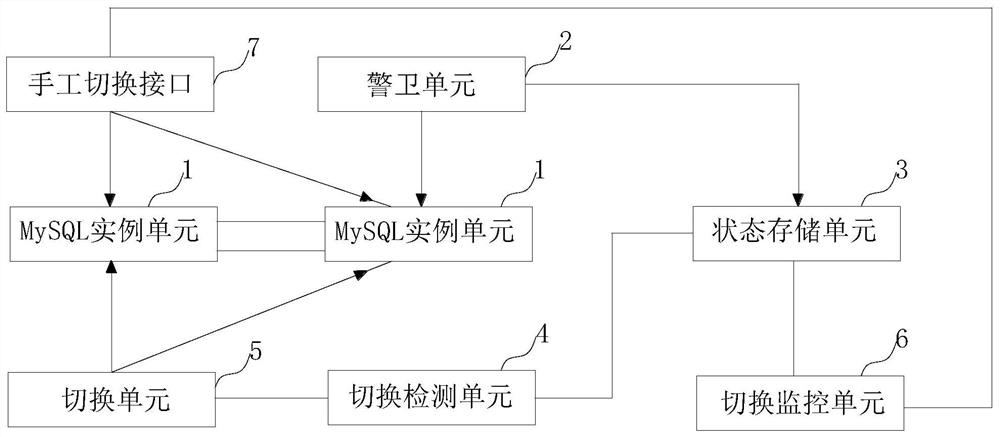
ActiveCN110569303AInsensibleSimple structureDatabase management systemsDatabase distribution/replicationHigh availabilityPattern perception
The invention discloses a MySQL application layer high-availability system and method suitable for various cloud environments. The system comprises a plurality of MySQL instance units; a guard unit used for checking whether the MySQL instance units are healthy or not; a state storage unit used for storing the state information of the MySQL instance unit according to the inspection result of the guard unit, and setting a switching mark if the MySQL instance unit is unhealthy; a switching unit used for closing the connection of the unhealthy MySQL instance units and creating the connection of the healthy MySQL instance units; and a switching detection unit used for detecting the switching sign at regular time, and calling the switching unit to trigger switching if the switching sign is found. MySQL high availability, simple architecture, dual-node-based dual-master replication, adaptation to various cloud environments, online use in a plurality of cloud machine rooms, rapid switching, noinfluence on services and no perception of users are realized in the application layer.
Owner:杭州衣科信息技术股份有限公司
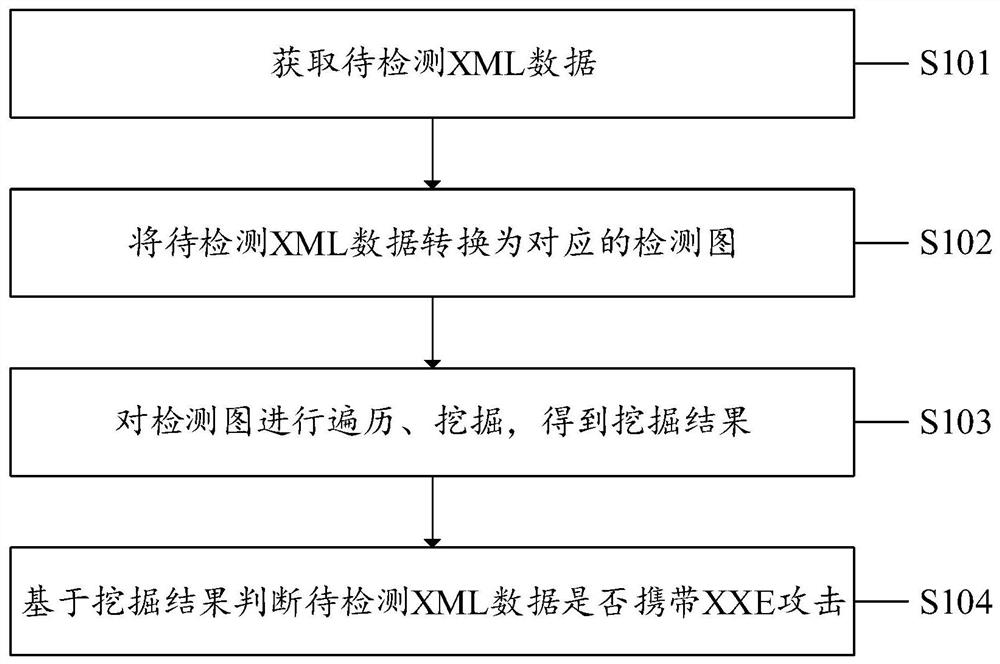
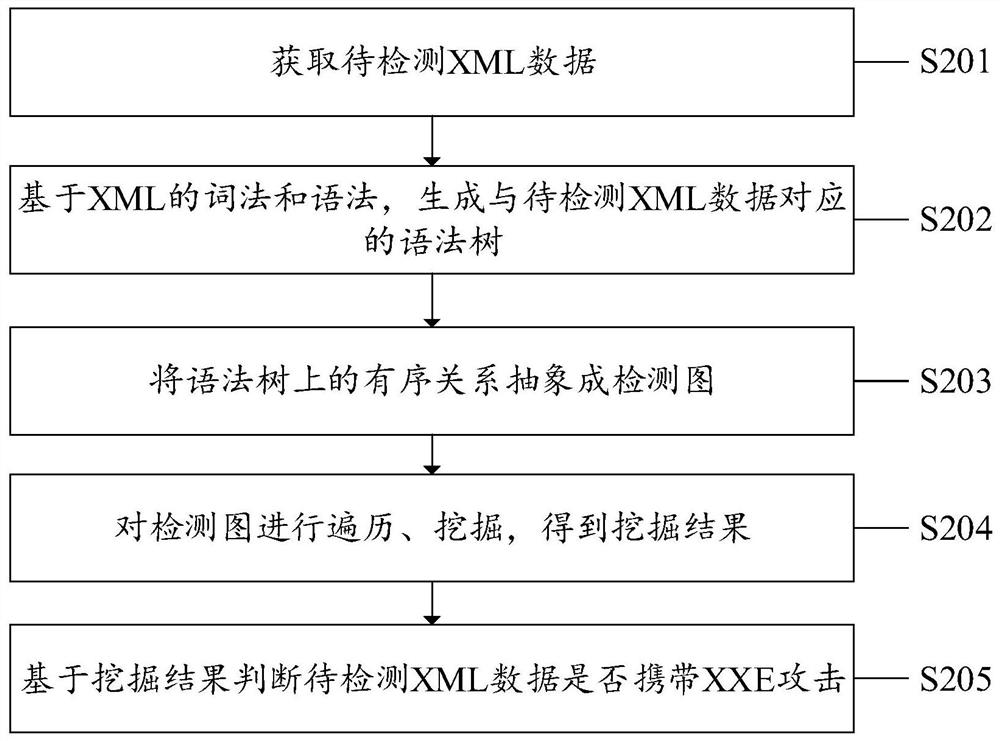
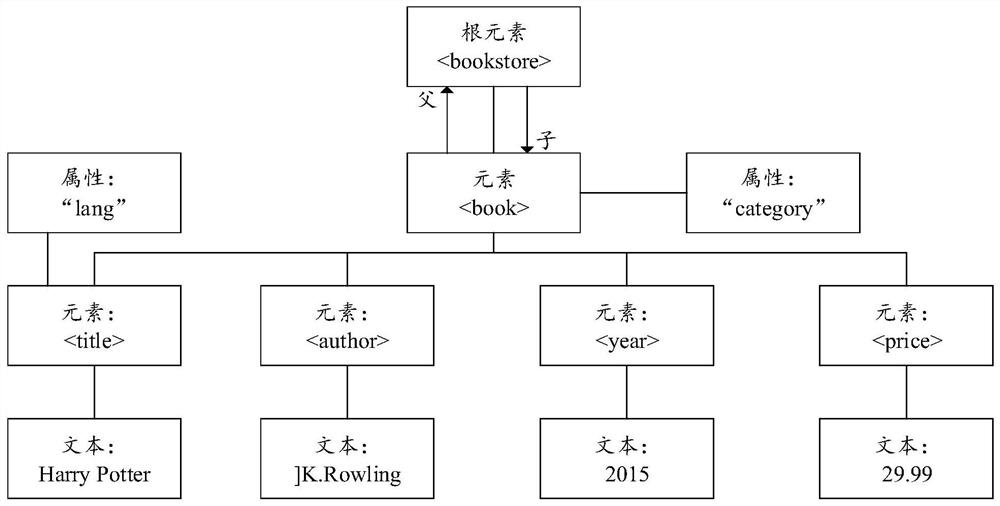
XXE attack detection method, system and device and computer storage medium
PendingCN113111345ADoes not affect businessImprove detection accuracyNatural language data processingPlatform integrity maintainanceData transformationAttack
The invention discloses an XXE attack detection method, system and device and a computer storage medium. The method comprises the steps of obtaining to-be-detected XML data; converting the XML data to be detected into a corresponding detection graph; traversing and mining the detection image to obtain a mining result; and judging whether the to-be-detected XML data carries the XXE attack or not based on the mining result. According to the method, the to-be-detected XML data is converted into the corresponding detection graph, and due to the connectivity and transitivity of the graph, even if the to-be-detected XML data carries the hidden attack information, the original attack information corresponding to the hidden attack information can be obtained by traversing and mining the detection graph, so that the hidden attack information can be detected, and the hidden attack information can be detected. The hidden attack information in the to-be-detected XML data can be judged together, so that the detection accuracy of the XXE attack is improved, and the XML service is not influenced. According to the XXE attack detection system and device and the computer readable storage medium provided by the invention, the corresponding technical problems are also solved.
Owner:SANGFOR TECH INC
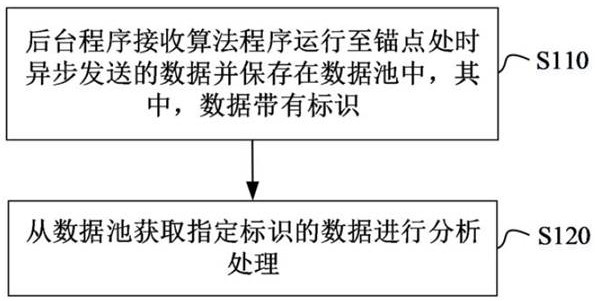
Method and apparatus for analyzing algorithm program data
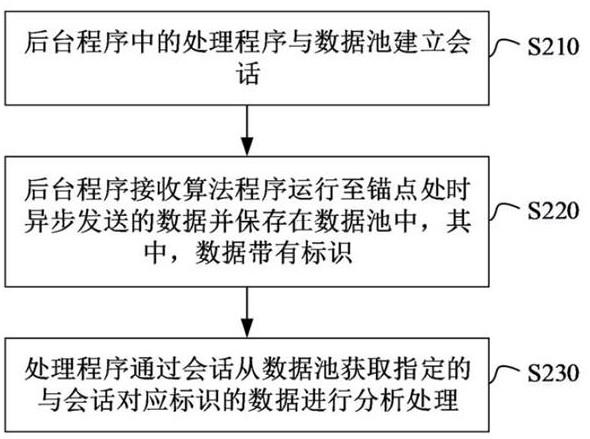
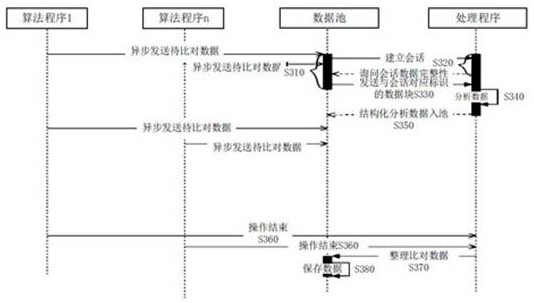
ActiveCN113312272BReal-time troubleshootingDoes not affect businessSoftware testing/debuggingAlgorithmTest algorithm
The invention discloses a method and device for analyzing algorithm program data. The method includes: a background program receives data asynchronously sent when an algorithm program runs to an anchor point, and saves it in a data pool, wherein the data has an identifier; and acquires data with a specified identifier from the data pool for analysis and processing. The device includes: a receiving unit for receiving data asynchronously sent when an algorithm program runs to an anchor point, wherein the data has an identifier; a data pool for saving the data received by the receiving unit; a processing unit for using Analyzing and processing the data with the specified identifier obtained from the data pool. The method and device can not only compare algorithms running on different machines by analyzing and comparing intermediate data, but also check algorithm errors in real time. The tested algorithm program has no perception of the data analysis process, does not affect the business, and saves large-scale Cluster test algorithm debugging and analysis time.
Owner:3CLEAR SCI & TECH CO LTD
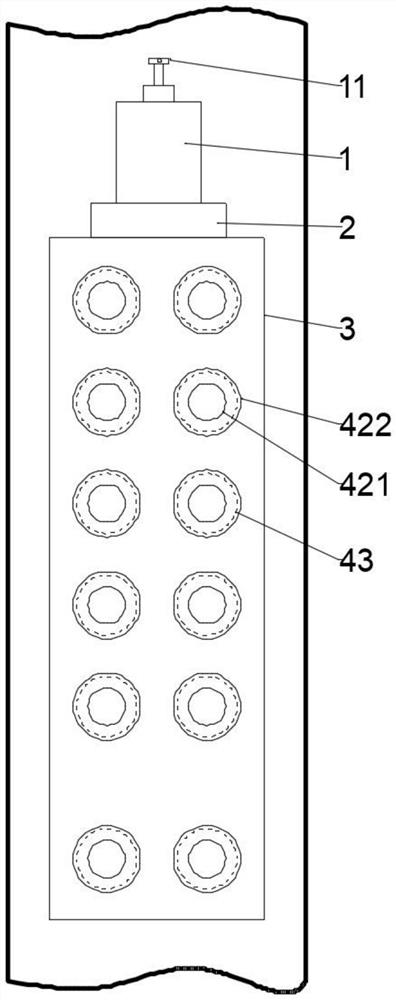
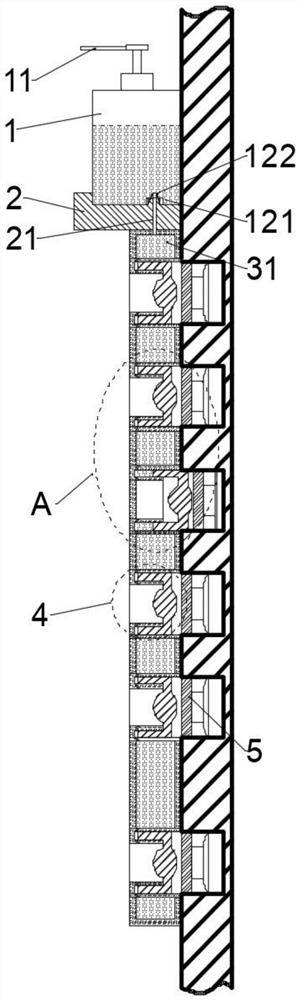
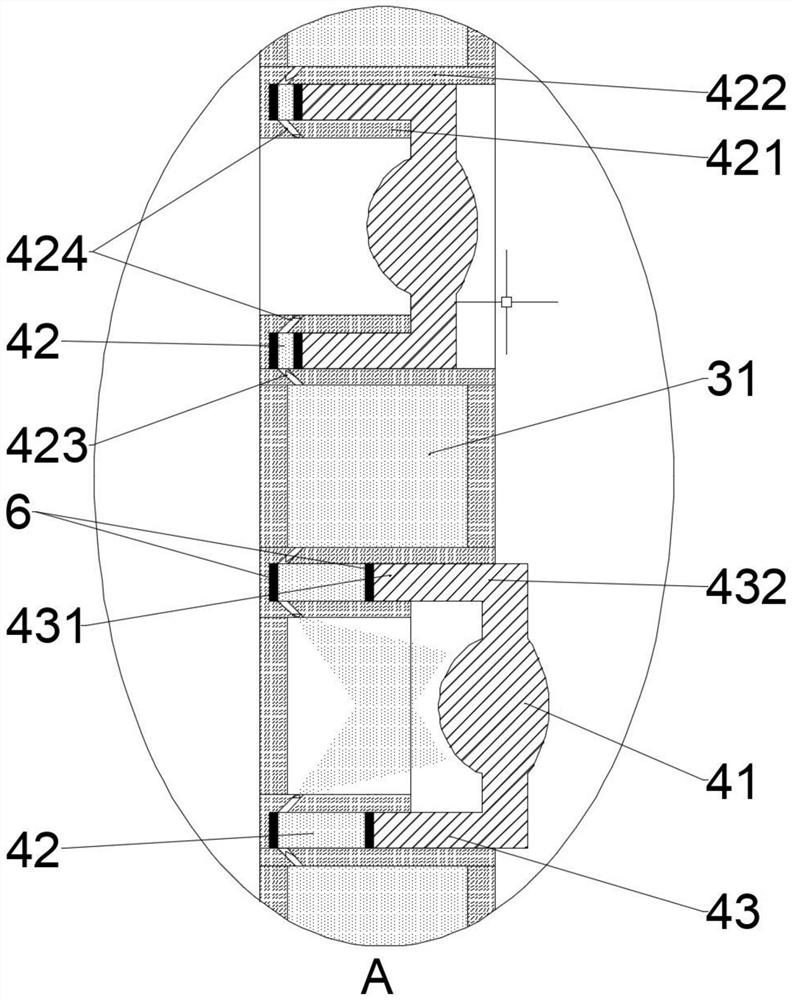
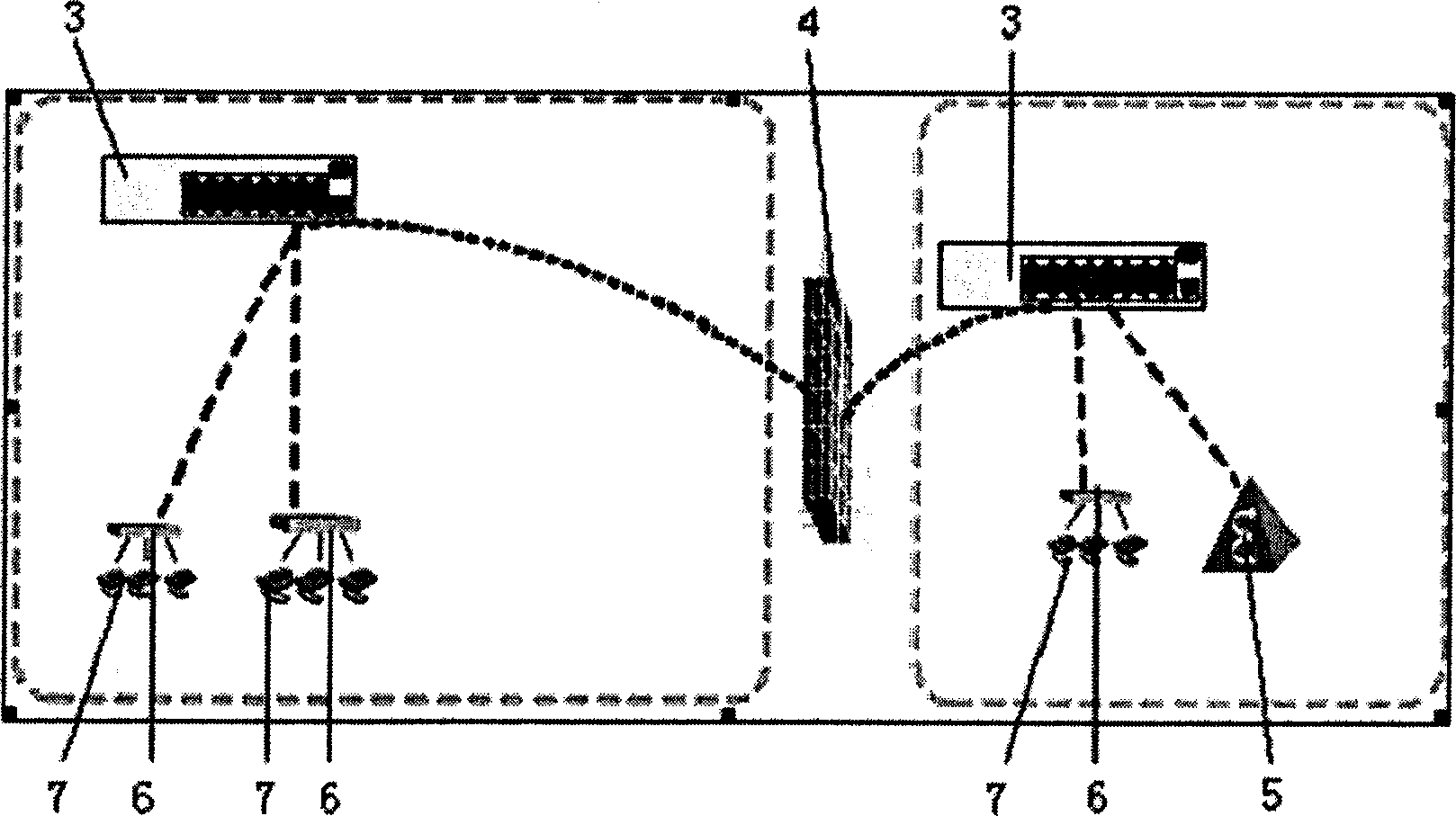
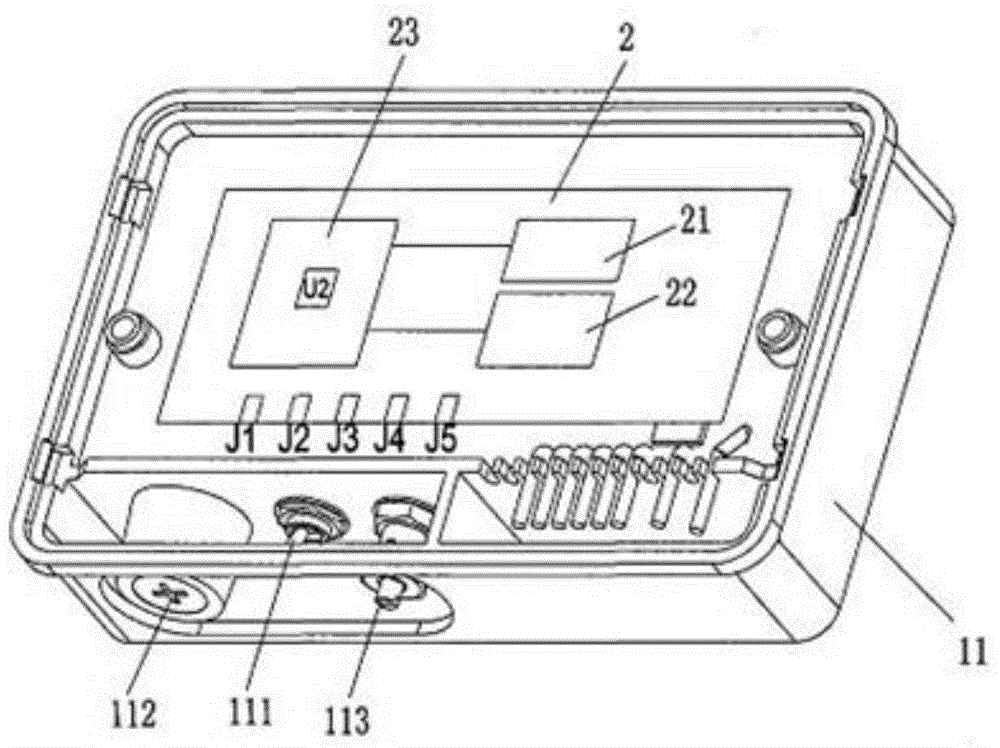
Cooking range controller
InactiveCN104566524AExtended service lifeReduce the temperatureDomestic stoves or rangesLighting and heating apparatusControl engineeringControl theory
The invention discloses a cooking range controller. The controller comprises a shell 1, wherein the shell 1 comprises a shell base 11 and a cover plate 12; the shell base 11 is internally provided with a control circuit board 2; the control circuit board 2 comprises a power supply circuit 21, a driving circuit 22 and a program control circuit 23; the driving circuit 22 and the program control circuit 23 are powered by the power supply circuit 21; the program control circuit 23 sends a signal to the driving circuit 22 so as to control all parts to act; a program for realizing timing and logic control is written into a core control chip U2 of the program control circuit 23; and 5 interfaces are formed in the control circuit board 2.
Owner:广东澳士顿电器有限公司
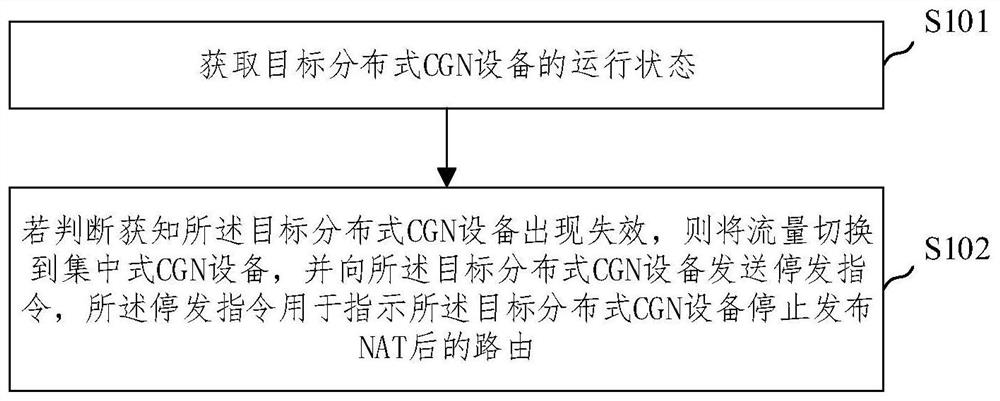
Carrier-level network address translation method and device
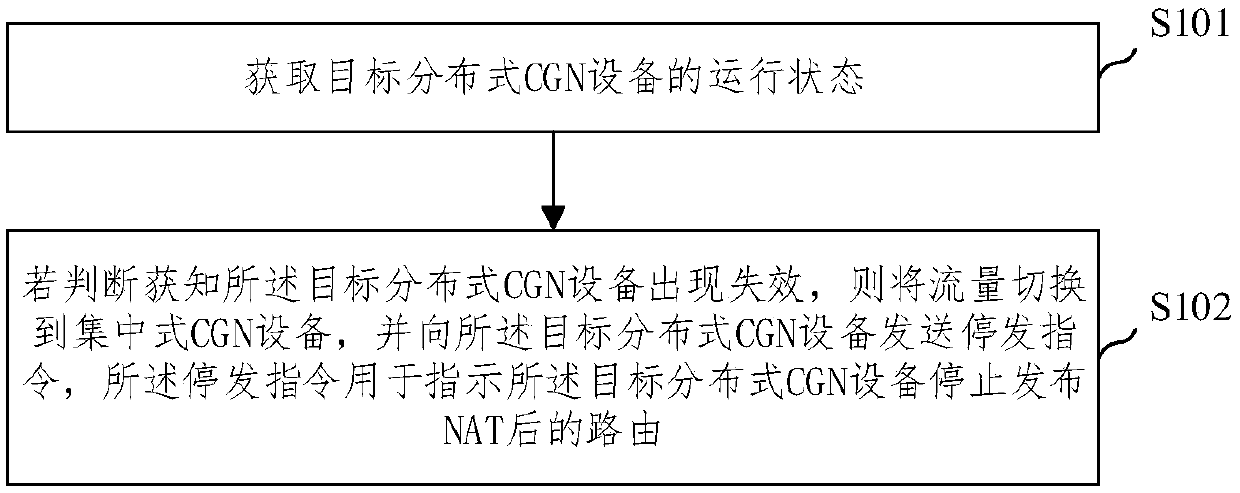
ActiveCN111131530BImprove efficiencyDoes not affect businessTransmissionEngineeringNetwork address translation
An embodiment of the present invention provides a carrier-level network address translation method and device, the method comprising: obtaining the operating status of the target distributed CGN device; if it is determined that the target distributed CGN device fails, then switching the traffic to the centralized CGN equipment, and send a stop instruction to the target distributed CGN equipment. The operator-level network address translation method and device provided by the embodiments of the present invention can dynamically and conditionally release routes after distributed CGN equipment NAT to ensure that the centralized CGN and distributed CGN use the same address space after NAT, and switch between the active and standby CGN equipment The service is not affected at all times, and the efficiency of using IPv4 addresses is improved.
Owner:XINYANG BRANCH HENAN CO LTD OF CHINA MOBILE COMM CORP +1
Optical network system and adaptive connection device in optical network system
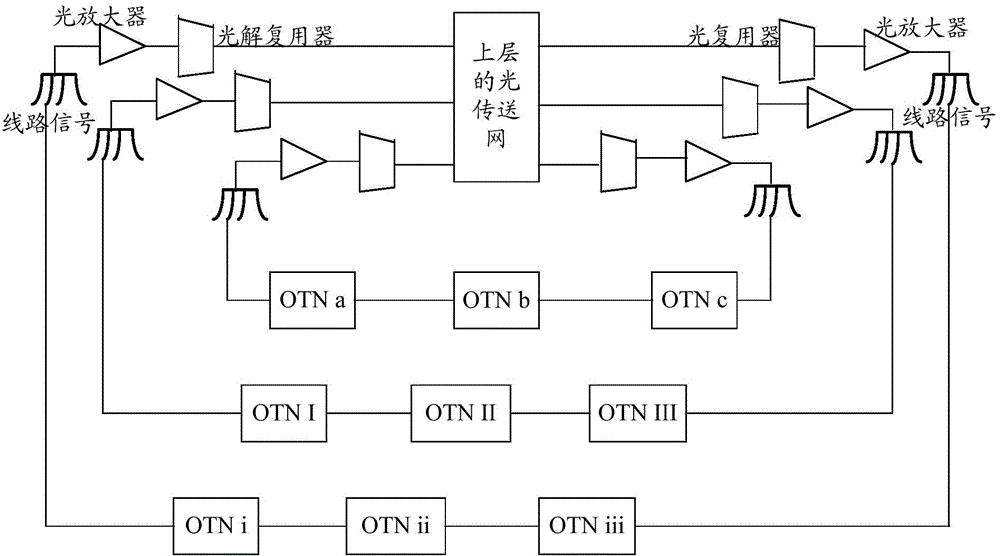
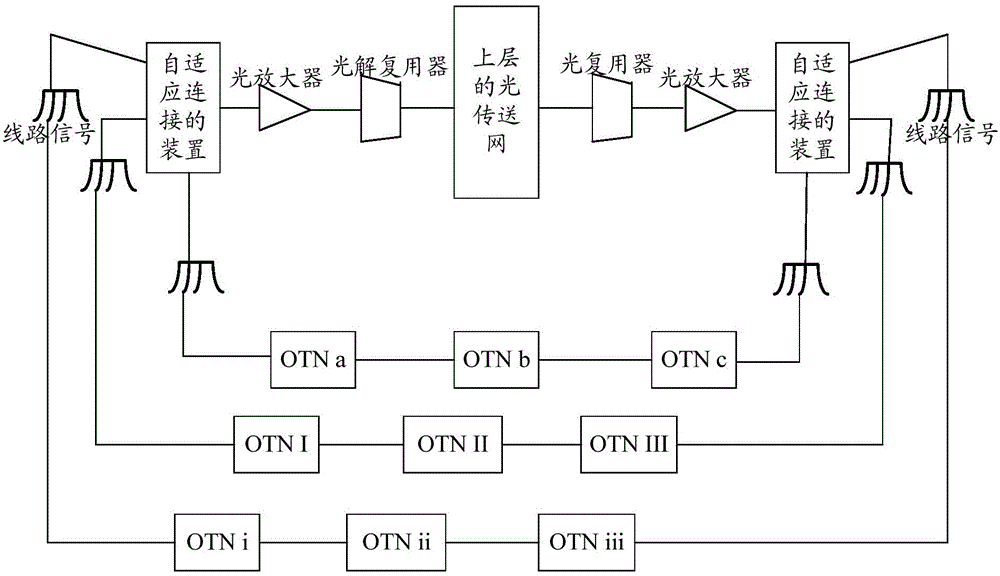
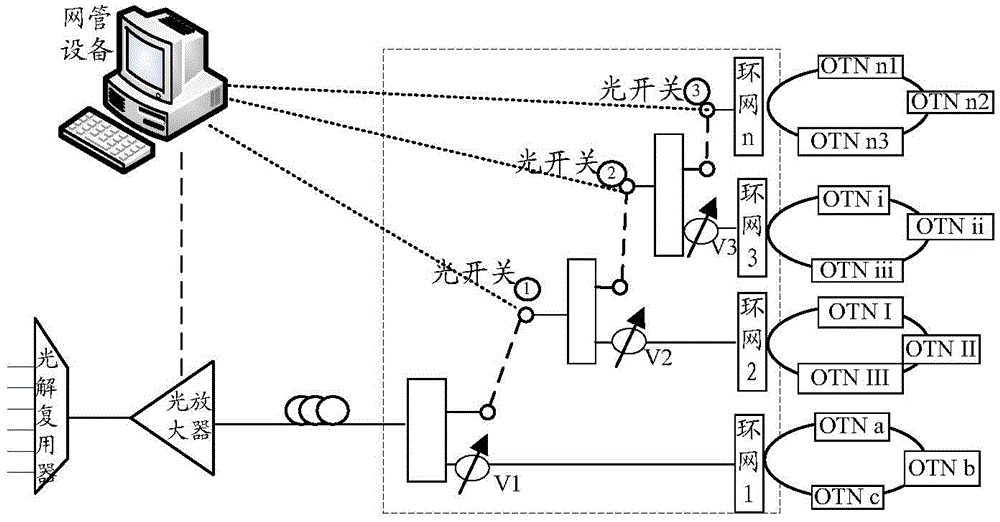
ActiveCN105871467ASolve space problemsSolve energy problemsMultiplex system selection arrangementsRing-type electromagnetic networksNetworked systemRing network
The invention provides an optical network system and an adaptive connection device in the optical network system. The system comprises a plurality of ring networks formed by optical transmission network (OTN) devices and a light amplifier. The system also comprises an adaptive connection device. The device comprises multi-level splitters, a plurality of optical switches, and a plurality of, wherein the splitter of each level is connected with one of the light-modulatable attenuator and one of the optical switches, the first-level splitter is connected with the light amplifier, and the first-level splitter is connected with the adjacent second-level splitter through the first optical switch which is connected with the first-level splitter. The light-modulatable attenuator connected with each splitter is connected with one of the optical transmission ring networks in the system correspondingly. The system enables the plurality of ring networks to share an optical subrack and fully utilizes the single light amplifier and a light demultiplexer.
Owner:CHINA MOBILE COMM GRP CO LTD
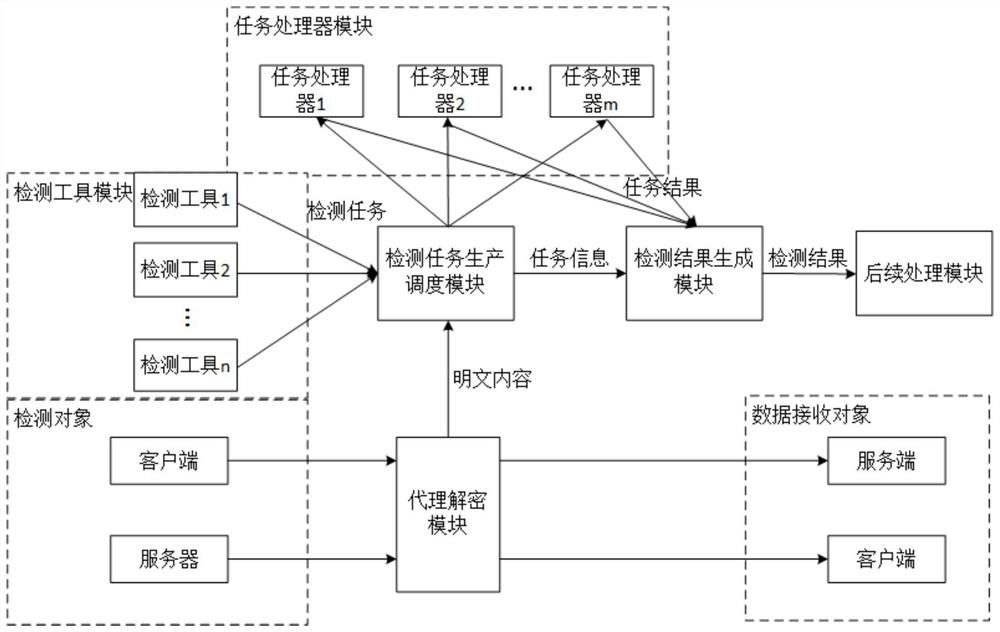
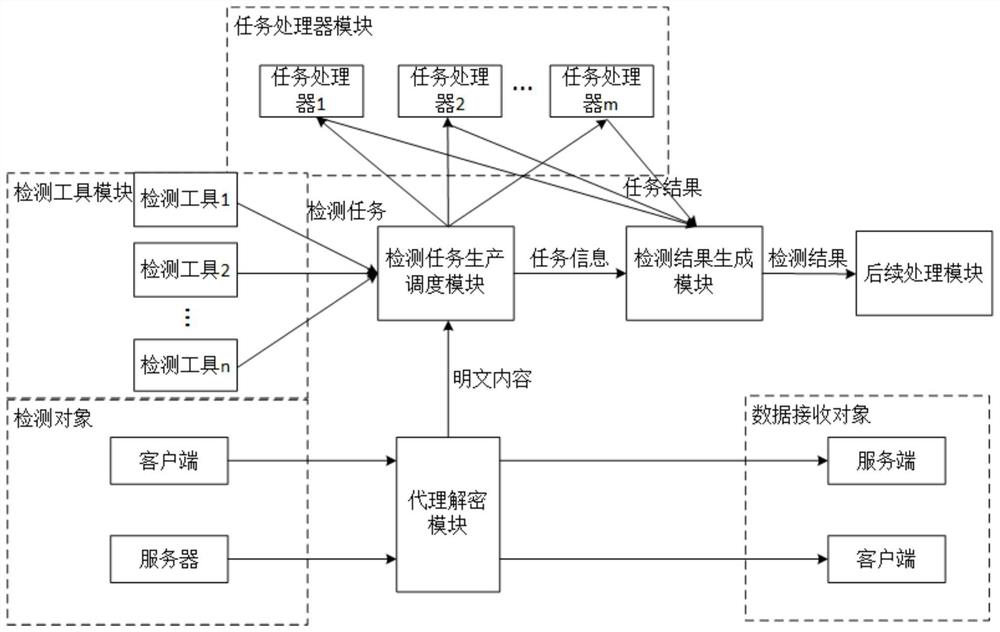
Sensitive data detection system for large-scale SSL/TLS encrypted session flow
ActiveCN111711598AReal-time processingImprove the ability of rapid detection and processingTransmissionRapid processingInternet access
The invention provides a sensitive data detection system for a large-scale SSL / TLS encrypted session stream. The system comprises an agent decryption module which is disposed at an Internet access gateway of a detection object, carries out the intermediate agent of an SSL / TLS encrypted data transmission process, and outputs the plaintext content, a detection task production scheduling module whichcalls a detection tool to generate a detection task and task information, schedules a task processor to execute the detection task, and sends the task information to a detection result generation module, a task processor module which is used for executing the detection task and generating a task result, a detection tool module which is used for detecting sensitive data contained in the plaintextcontent, and the detection result generation module which is used for judging and combining according to the task information and the task result to generate a detection result. According to the system, a complex decryption key management process is not needed, detection task production and result processing are separated, detection tasks are asynchronously produced, task processing resources arescheduled as required, and large-scale SSL / TLS encrypted session streams can be rapidly processed in real time.
Owner:CHINA ELECTRONICS TECH CYBER SECURITY CO LTD
A method, device and equipment for controlling data recovery speed
ActiveCN108958975BDoes not affect businessRedundant operation error correctionControl dataEngineering
The invention discloses a method, device, device and computer-readable storage medium for controlling data recovery speed. The method includes: determining the corresponding cluster recovery speed based on the current busyness of the distributed system; The node is the target node. Multiply the ratio of the number of data to be restored by the target node to the number of data to be restored in the distributed system by the cluster recovery speed to obtain the corresponding node recovery speed, and determine the token allocated to the target node per unit time based on the node recovery speed The number is the number of currently available tokens; when receiving a data recovery request, judge whether the number of tokens allocated to the target node in the current unit time reaches the number of currently available tokens, and if so, refuse to issue tokens for the target node, if If not, a token is issued for the target node to instruct the target node to realize data recovery. To achieve the purpose of controlling the speed of data recovery based on the current situation of the distributed system.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
Call processing method in next generation network
ActiveCN100471218CImprove transmission qualityNo misuseTelephonic communicationMedia gatewayNext-generation network
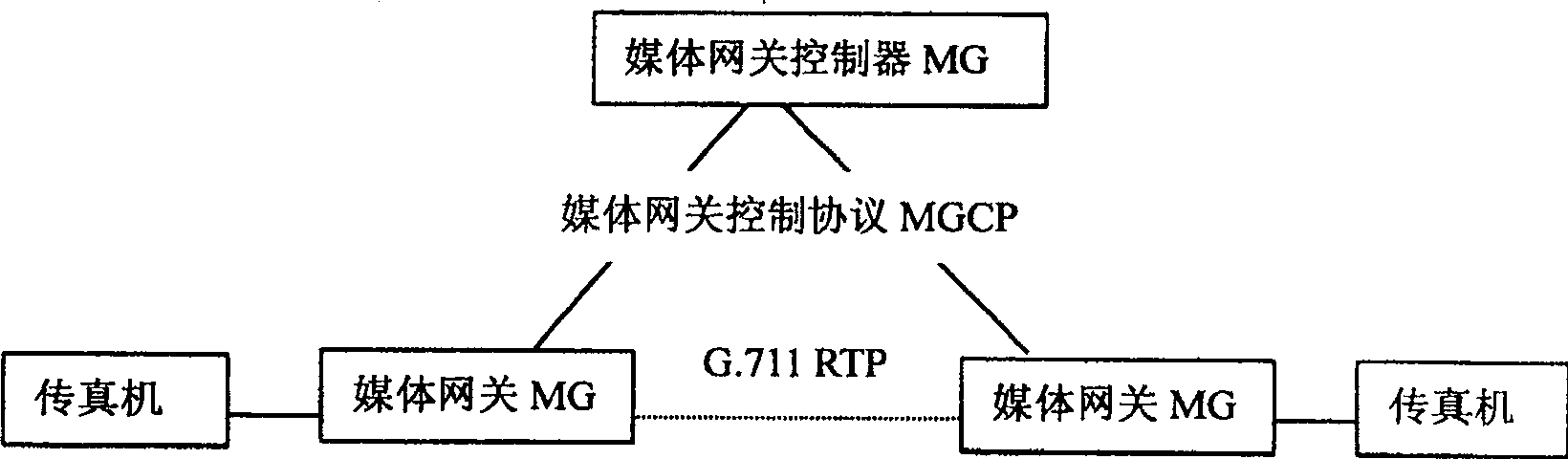
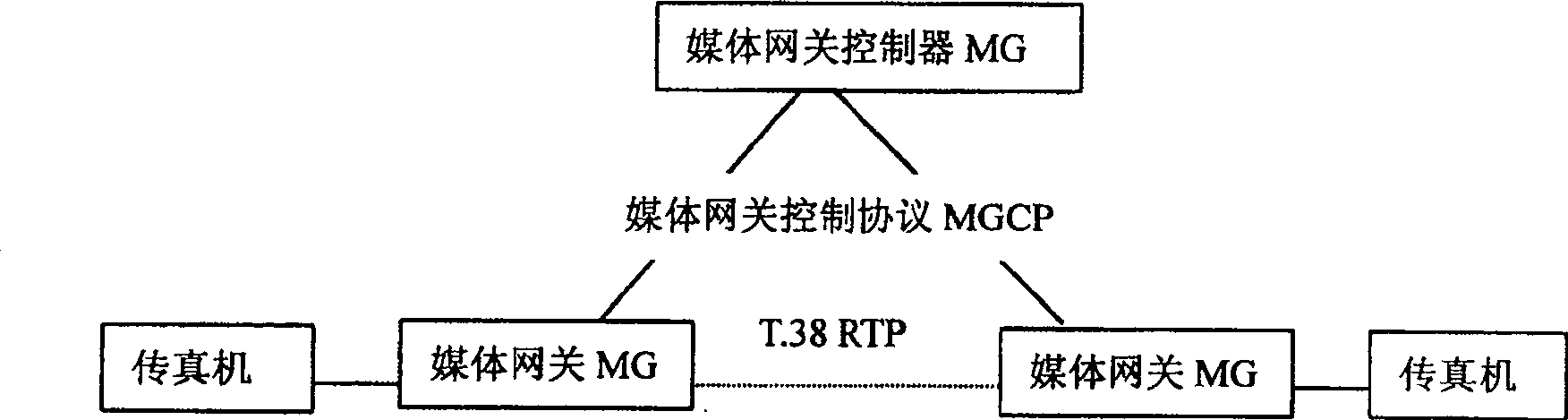
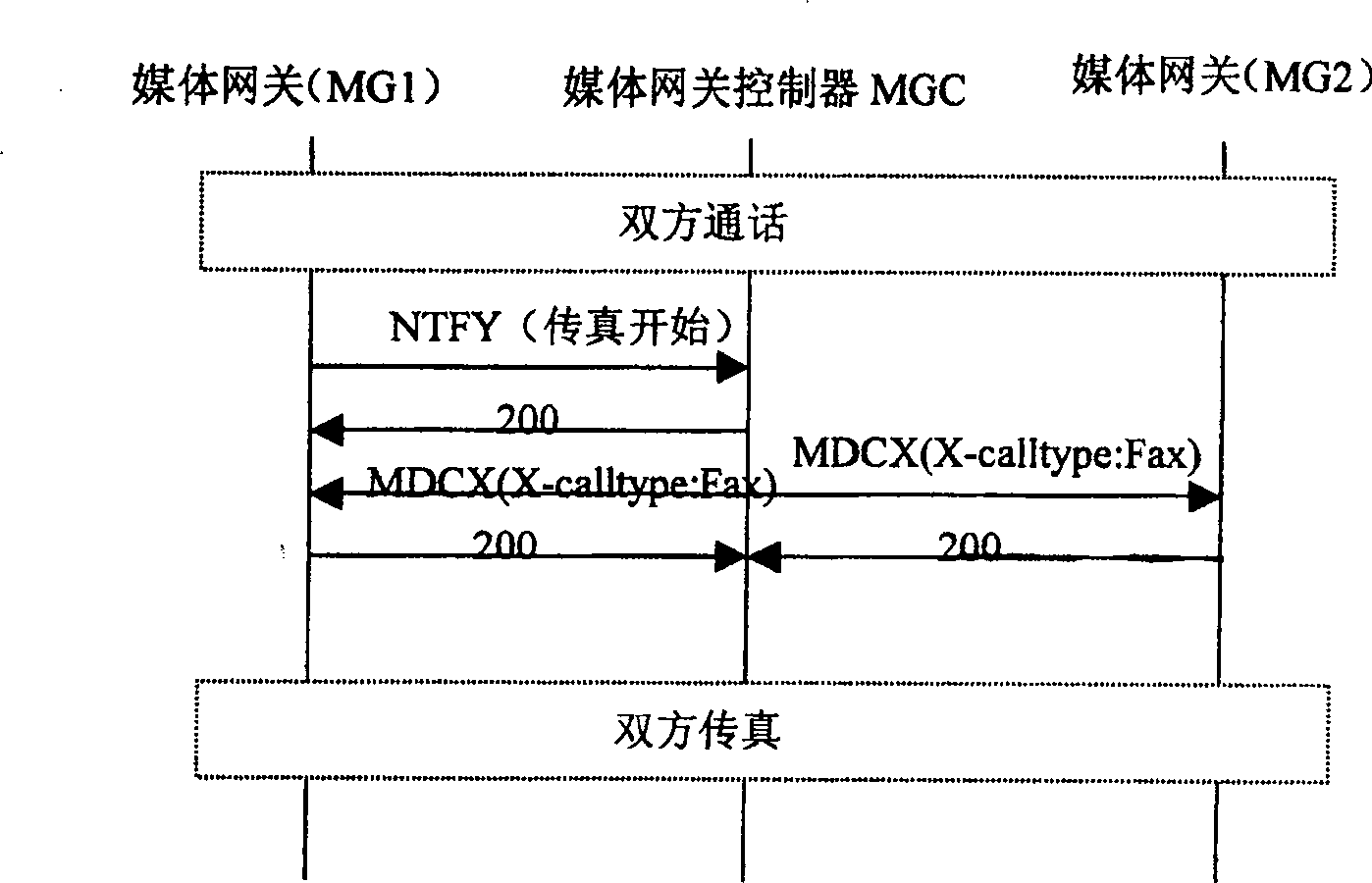
The call processing method for the next generation of network has expanded local connection options in medium gateway control protocol and increased call type parameter to the local connection options. When the medium gateway detects the call service, it informs the medium gateway controller, the medium gateway controller issues connection amending command with the said call type parameter and requires the medium gateway to perform coding / decoding switching. The medium gateway regulates corresponding DSP parameters based on the call type parameter to suit different service transmission. The call type parameter as one expanded parameter has no influence on service and causes no malfunction of the gateway. The present invention makes it possible for the medium gateway to use G.711 coding / decoding service to regulate DSP parameter for different service and this raises the transmission quality.
Owner:HUAWEI TECH CO LTD
Service method and system based on virtual machine one-button packaging migration
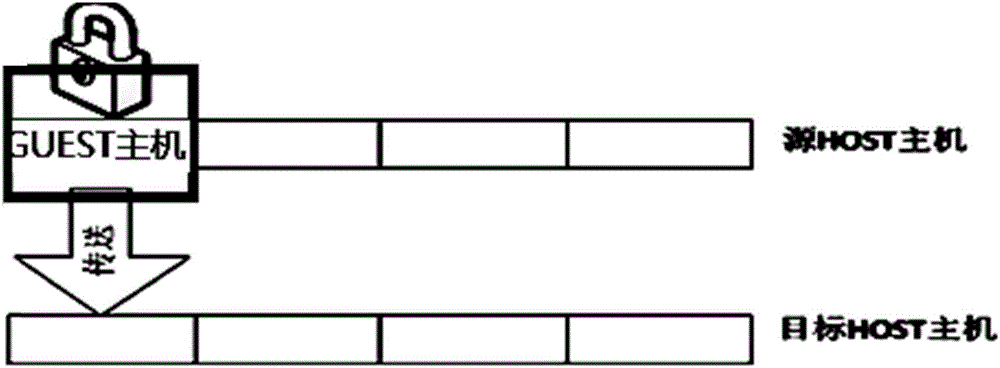
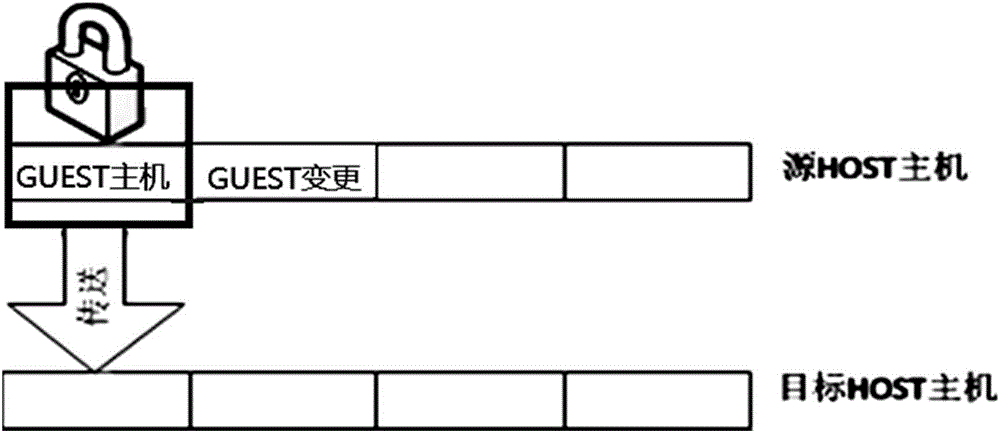
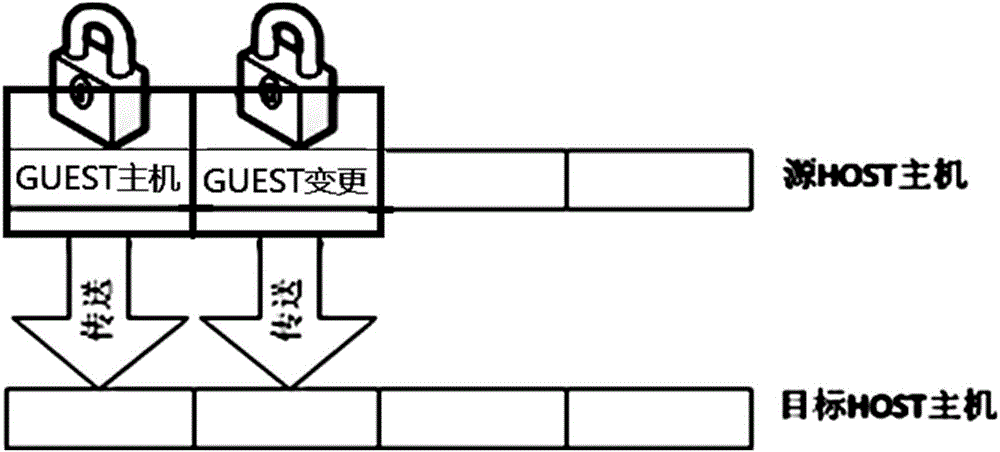
InactiveCN106843999AOne-click packing and moving is convenient and flexibleDoes not affect dataSoftware simulation/interpretation/emulationVirtual machine
The invention provides a service method and system based on virtual machine one-button packaging migration. The memory transfer method includes the steps that in a source host mainframe, a client mainframe memory is locked, and information in the client mainframe memory is transferred to a target host mainframe; in the transfer process, a new memory partition is opened in the source host mainframe to provide services for a client mainframe, wherein the new memory partition only stores changed content of the client mainframe memory; the new memory partition is locked, and the information in the new memory partition is transferred to the target host mainframe. According to the service method and system, no data or service on a virtual machine is influenced, and services will not be interrupted in the migration process; service interruption generated in a traditional mode can be avoided, and the service method and system are suitable for scenarios with high service availability requirements.
Owner:CETC CHINACLOUD INFORMATION TECH CO LTD
A sensitive data detection system for large-scale ssl/tls encrypted session streams
ActiveCN111711598BReal-time processingImprove the ability of rapid detection and processingSecuring communicationThe InternetData transmission
The invention provides a sensitive data detection system oriented to large-scale SSL / TLS encrypted session flow, including: a proxy decryption module, which is set at the Internet entry and exit gateway of the detection object, performs intermediate proxy for the SSL / TLS encrypted data transmission process, and outputs plaintext Content; detection task production scheduling module, which calls detection tools to generate detection tasks and task information, schedules the task processor to execute detection tasks, and sends the task information to the detection result generation module; task processor module is used to execute detection tasks and generate The task result; the detection tool module is used to detect the sensitive data contained in the plaintext content; the detection result generation module is used to judge and merge according to the task information and the task result to generate the detection result. This system does not require complex decryption key management process, separates detection task production and result processing, produces detection tasks asynchronously, schedules task processing resources on demand, and can quickly process large-scale SSL / TLS encrypted session streams in real time.
Owner:CHINA ELECTRONICS TECH CYBER SECURITY CO LTD
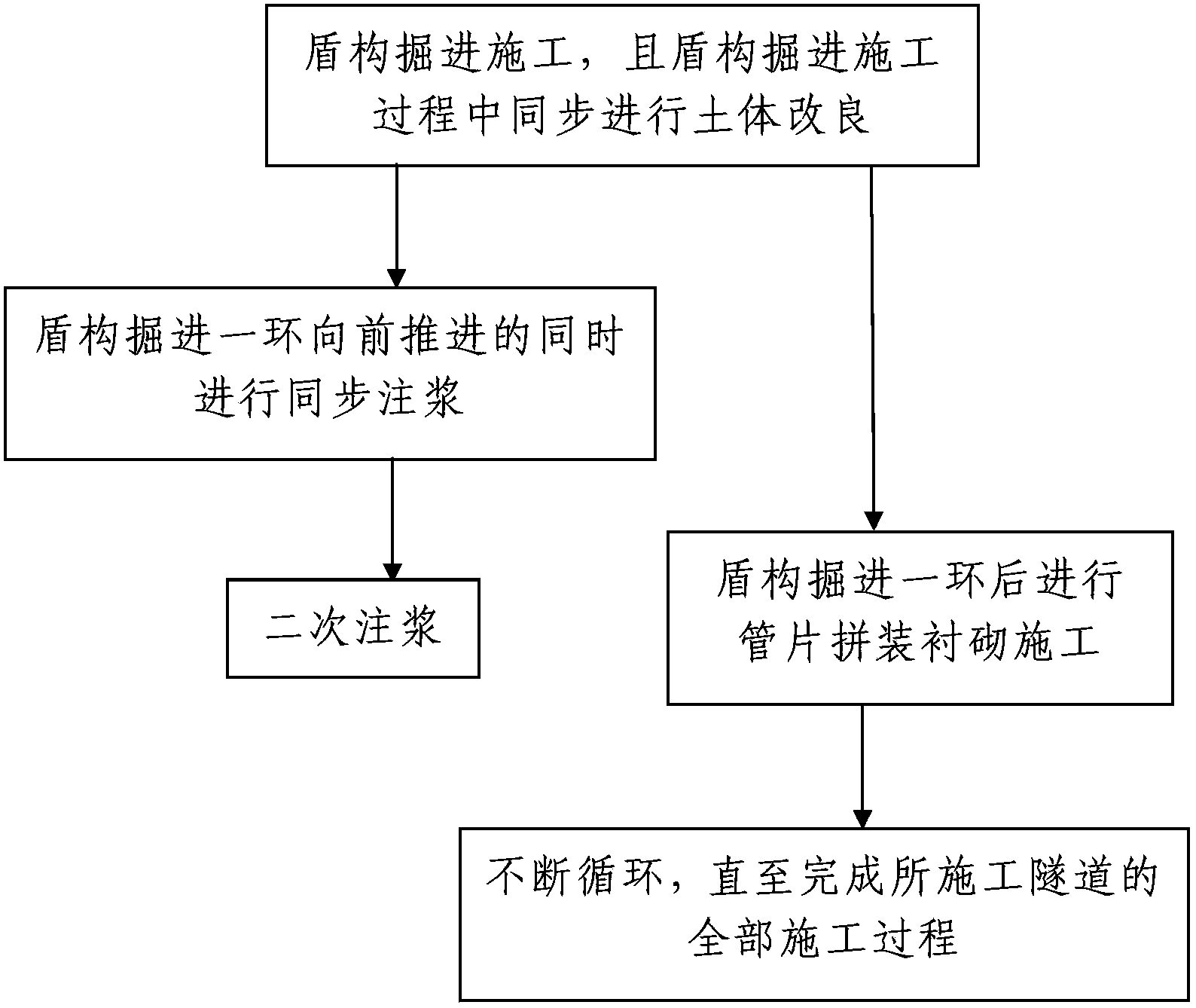
Loess strata subway tunnel earth pressure balance shield construction method
ActiveCN102767377BThe construction process steps are simpleEasy to implementUnderground chambersTunnel liningInternal pressureArchitectural engineering
The invention discloses a loess strata subway tunnel earth pressure balance shield construction method. The method comprises that firstly, shield excavation construction is performed by using a earth pressure balance shield machine; the excavation speed in no more than 10cm / min, the total thrust is no more than 15000KN, and the inner pressure of a soil warehouse is kept in a range between 1bar and 2 bar; the aperture opening ratio of a spoke panel type cutter is in a range of 40-70%, and the rotating speed of the cutter is no more than 1.5rpm; cement, pulverized fuel ash, fine sand, bentonite and water is mixed uniformly to obtain synchronous grouting liquid and second grouting is performed by using double-liquid grouting composed of cement paste and water glass; performing shield duct piece assembly construction after completion of one cycle of the shield excavation construction; and the process is repeated until the overall construction of the subway tunnel is achieved. The construction method is simple in step, easy to operate, fast in construction speed, high in construction quality, low in interference on the environment, high in construction safety and capable of guaranteeing successful construction of loess strata subway tunnels.
Owner:URBAN RAIL TRANSIT ENG CO LTD OF CHINA RAILWAY FIRST GRP CO LTD +1
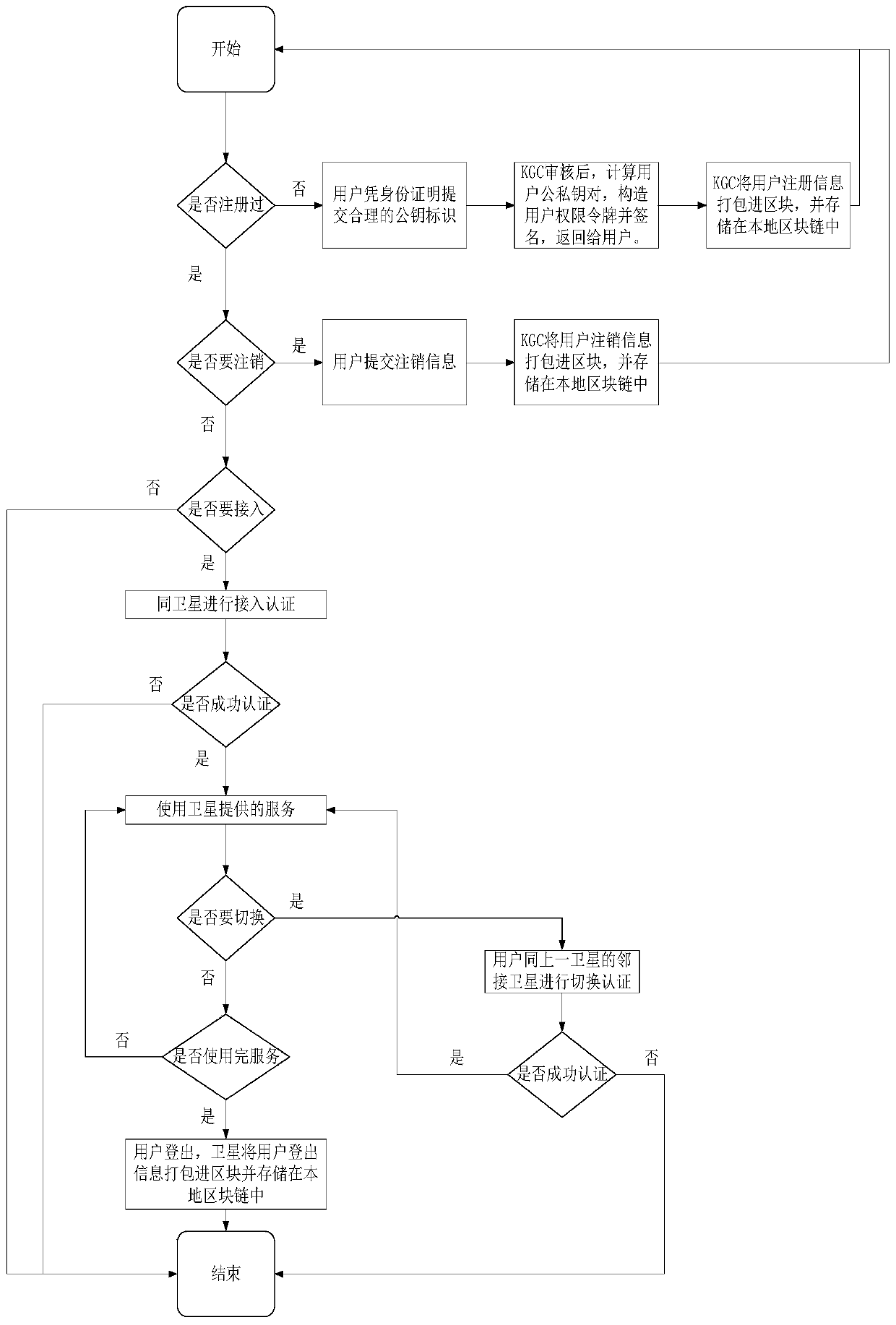
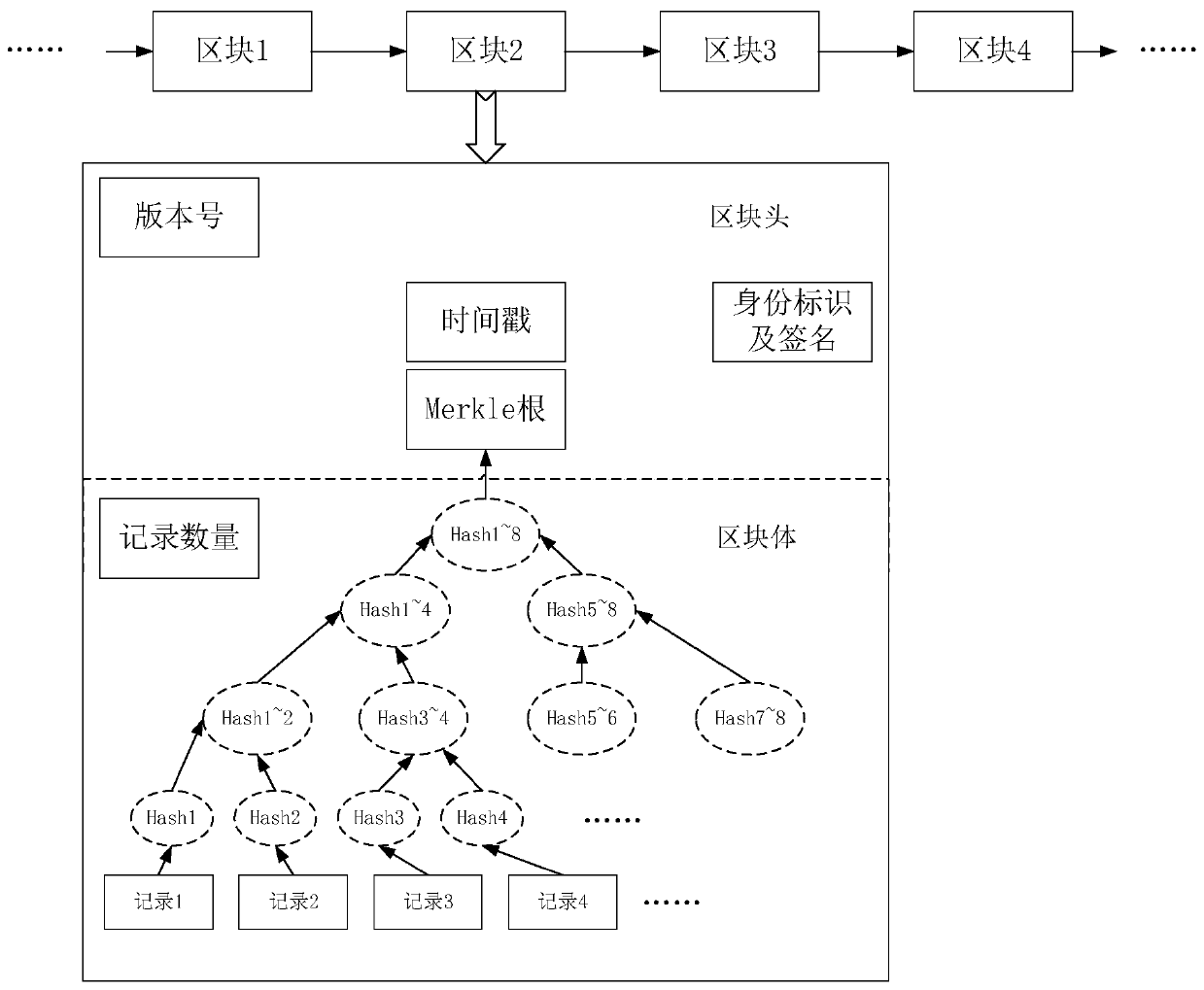
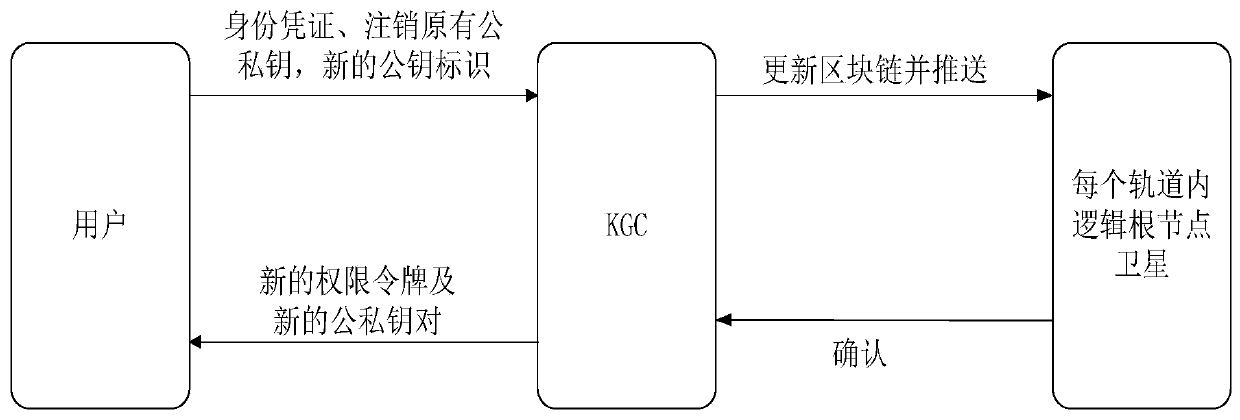
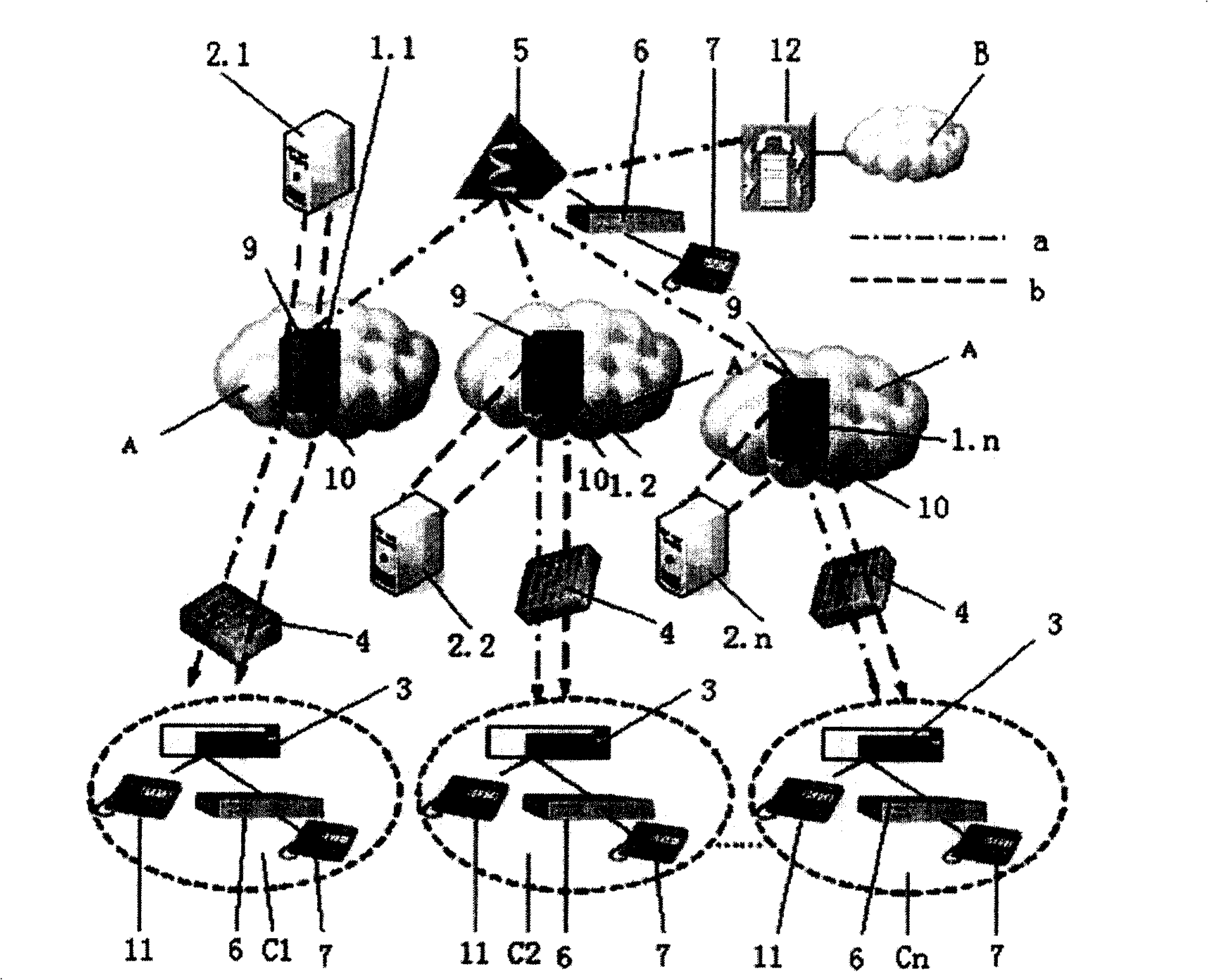
A distributed access authentication management method in a leo satellite network
ActiveCN107147489BEasy to submitImprove scalabilityKey distribution for secure communicationMultiple keys/algorithms usageCryptosystemRapid access
The invention discloses a distributed access authentication management method in a LEO satellite network, which adopts an identity-based cryptographic system, uses the private key of the key generation center to quickly generate the public-private key pair of the user and the satellite node, and stores the public-private key pair in the identification field The identity information is agreed in the system to realize the role distinction in the system; at the same time, based on the chain distributed storage technology of the blockchain, a trusted chain with the key generation center and the satellite as the main body of trust is constructed to realize rapid access authentication of users and fast inter-satellite The handover identity verification function adapts to the characteristics of dynamic topology and frequent handover of satellite-ground links in the LEO satellite network. On the other hand, this method adopts the distributed storage technology of the block chain, and uses the trust chain as the consensus mechanism to record relevant information such as user registration, logout, login, logout, and switching, and to ensure the accuracy, integrity, and accuracy of user logs. Consistency, traceability and non-tampering, avoiding the bottleneck of the central node in the access function and authentication performance.
Owner:NANJING UNIV OF SCI & TECH
A high-availability system and method for mysql application layer applicable to various cloud environments
ActiveCN110569303BInsensibleSimple structureDatabase management systemsDatabase distribution/replicationHigh availabilitySecurity guard
The invention discloses a MySQL application layer high-availability system and method suitable for various cloud environments. The system comprises a plurality of MySQL instance units; a guard unit used for checking whether the MySQL instance units are healthy or not; a state storage unit used for storing the state information of the MySQL instance unit according to the inspection result of the guard unit, and setting a switching mark if the MySQL instance unit is unhealthy; a switching unit used for closing the connection of the unhealthy MySQL instance units and creating the connection of the healthy MySQL instance units; and a switching detection unit used for detecting the switching sign at regular time, and calling the switching unit to trigger switching if the switching sign is found. MySQL high availability, simple architecture, dual-node-based dual-master replication, adaptation to various cloud environments, online use in a plurality of cloud machine rooms, rapid switching, noinfluence on services and no perception of users are realized in the application layer.
Owner:杭州衣科信息技术股份有限公司
Operator-level network address translation method and device
ActiveCN111131530AImprove efficiencyDoes not affect businessTransmissionNetwork addressAddress space
The embodiment of the invention provides an operator-level network address translation method and device. The method comprises the steps of acquiring a running state of target distributed CGN equipment, if it is judged that the target distributed CGN device fails, switching the flow to a centralized CGN device, and sending a stop instruction to the target distributed CGN device. The embodiment ofthe invention provides the operator-level network address translation method and device. Through dynamic conditional release of the routing after the NAT of the distributed CGN equipment, the centralized CGN and the distributed CGN are ensured to use the same address space after the NAT, the service is not influenced when the main CGN equipment and the standby CGN equipment are switched, and the use efficiency of the IPv4 address is improved.
Owner:XINYANG BRANCH HENAN CO LTD OF CHINA MOBILE COMM CORP +1
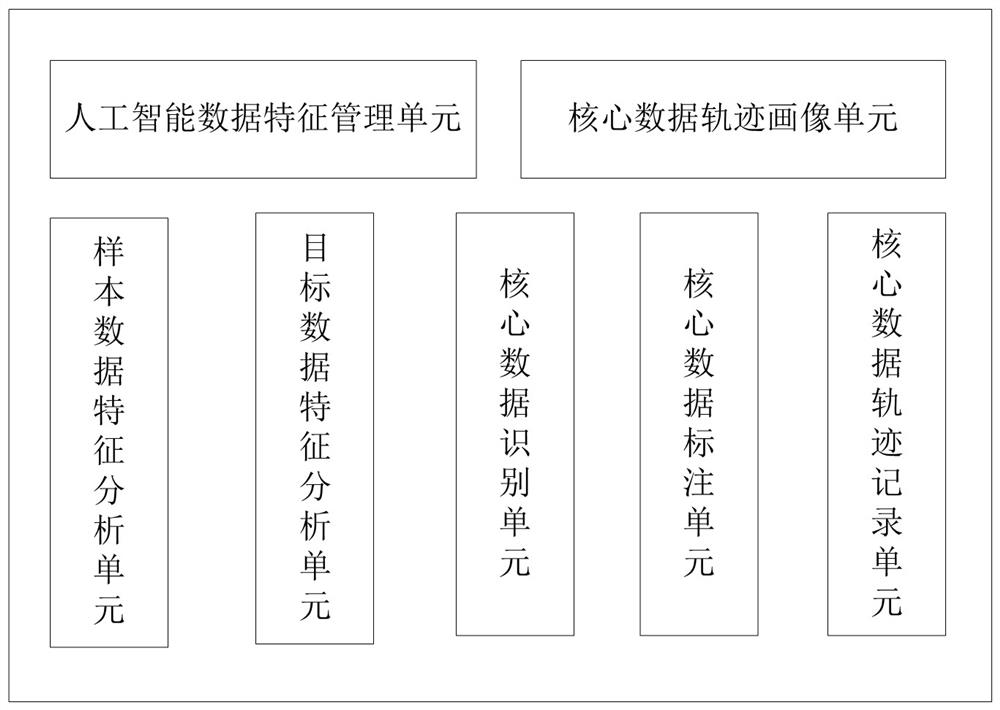
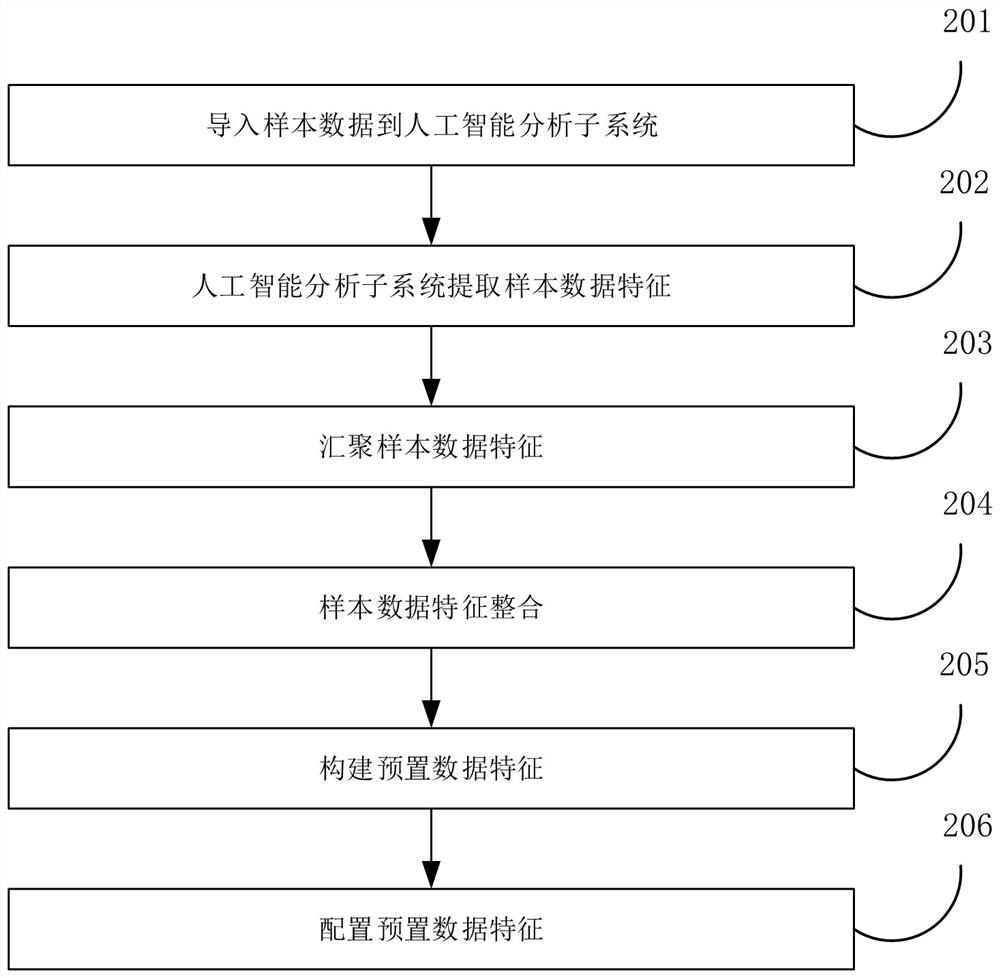
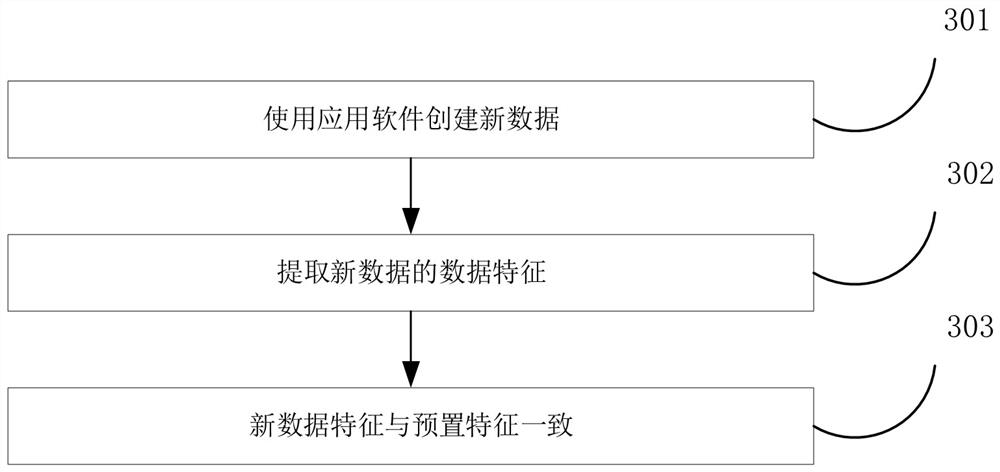
A method and system for generating core data trajectory portraits based on artificial intelligence
The present application discloses a method and system for generating core data trajectory portraits based on artificial intelligence. The administrator obtains the characteristics of the sample data through artificial intelligence analysis of the sample data, and selects the preset data characteristics from the characteristics of the sample data. The sample data includes structured data, semi-structured data and unstructured data. The preset data feature is used to represent the data feature of the core data; when the target data is determined to be the core data by the preset data feature, during the process of using the target data, record the annotation of the target data data, and generate the corresponding trajectory records; obtain all the trajectory records of the labeled data, and build the trajectory portrait of the labeled data in time sequence. The present application solves the technical problem in the related art that an overall trajectory portrait of the data flow process cannot be performed.
Owner:北京数安行科技有限公司
Method and device for upgrading and rolling back a base station
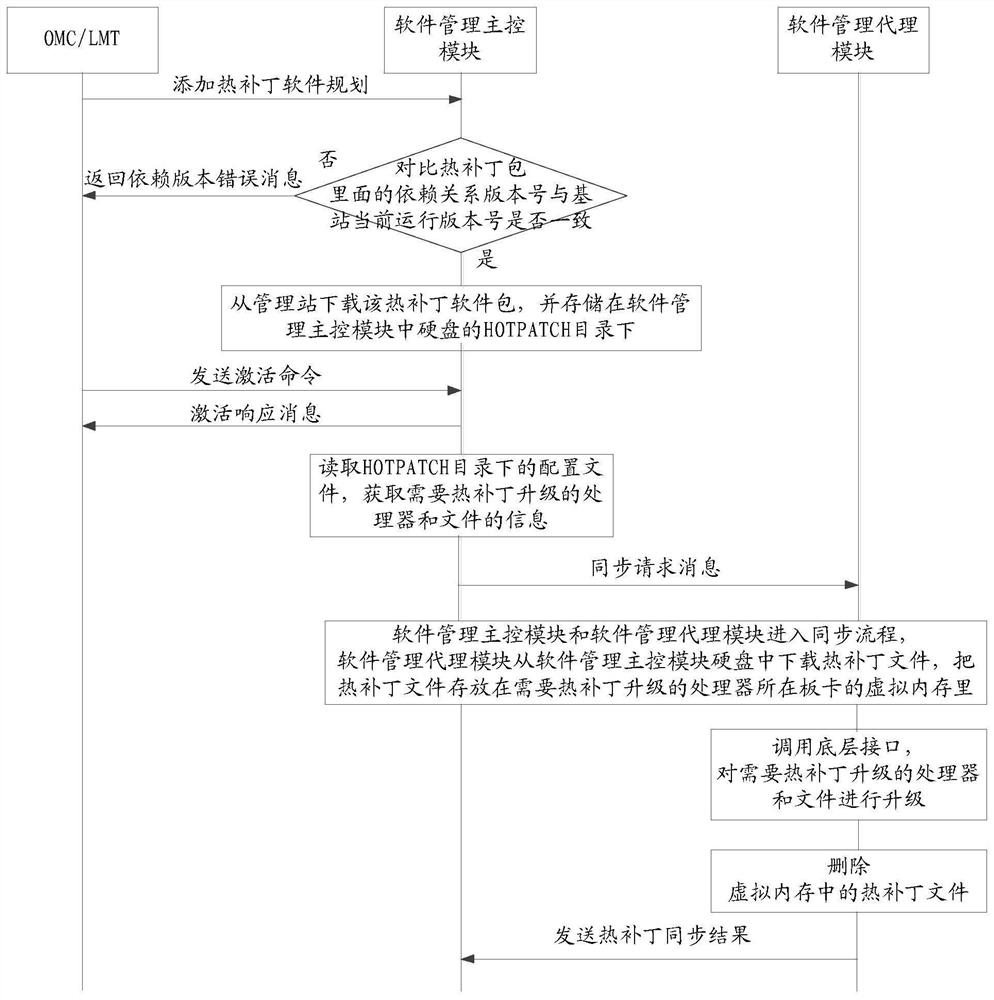
ActiveCN108934033BDoes not affect perceptionDoes not affect businessSoftware deploymentWireless communicationEmbedded systemSoftware package
Embodiments of the invention provide an upgrade method and apparatus, and a rollback method and apparatus of a base station. The upgrade method includes steps: a software management master control module obtains a hot patch software package; the software management master control module determines a target baseband board in one or more baseband boards according to the hot patch software package; the software management master control module generates a synchronous request message for the target baseband board; the software management master control module transmits the synchronous request message to a target software management agent module corresponding to the target baseband board; and the target software management agent module is used for obtaining the hot patch software package by employing the synchronous request message and upgrading the target baseband board by employing the hot patch software package. Therefore, patch upgrade of a base station having a problem in the conventional network can be rapidly realized, patch upgrade with dynamic loading and dynamic come-into-effect of the target baseband board can be performed, other baseband boards can simultaneously and normally operate, the base station does not need to perform resetting during patch upgrade, and the influence on business and user perception is avoided.
Owner:DATANG MOBILE COMM EQUIP CO LTD
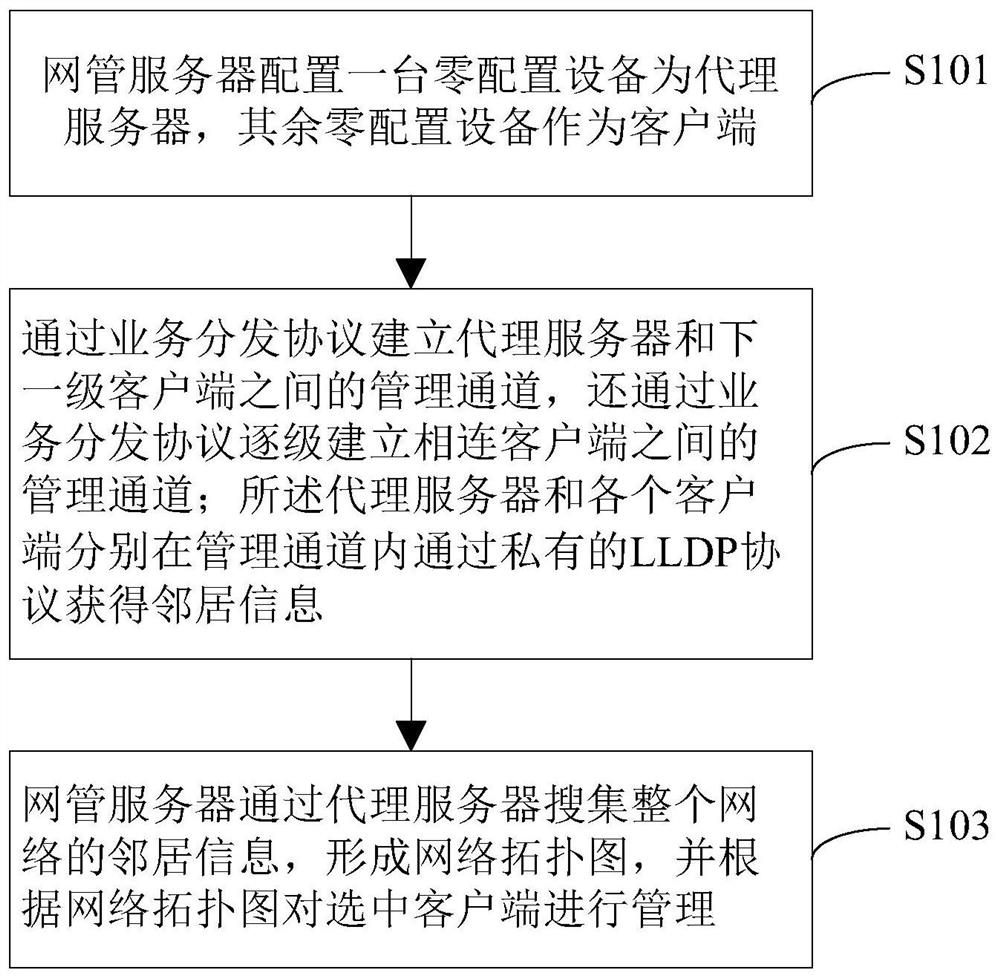
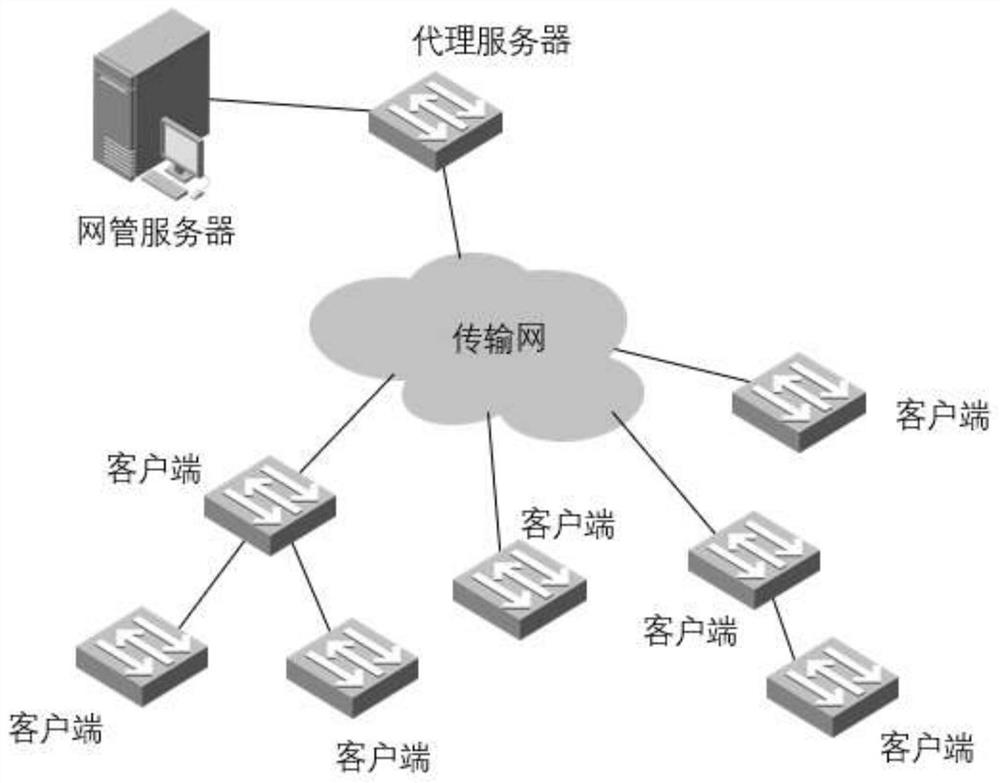
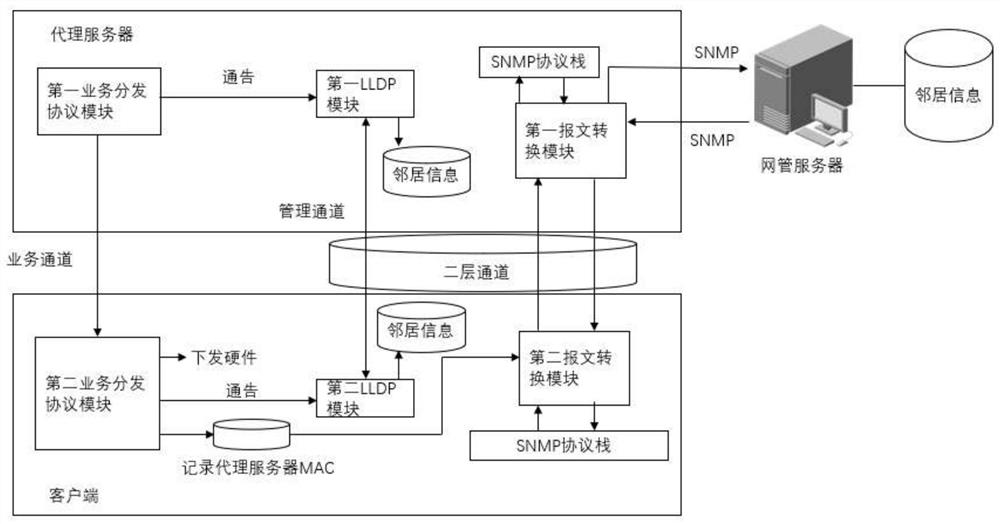
Method and system for accessing network management of large-scale remote zero-configuration equipment
ActiveCN110213089BEasy to operateReduce engineering start-up timeTransmissionHigh level techniquesLink Layer Discovery ProtocolNetwork management
A method and system for connecting a large-scale remote zero-configuration device to a network management, involving the field of Ethernet switching and transmission, the method comprising: configuring a zero-configuration device as a proxy server on a network management server, and using other zero-configuration devices as clients; The link layer discovery protocol service distribution protocol establishes the management channel between the proxy server and the next-level client, and also establishes the management channel between the connected clients step by step through the service distribution protocol; the proxy server and each client are respectively in In the management channel, the neighbor information is obtained through the private LLDP link layer discovery protocol; the network management server collects the neighbor information of the entire network through the proxy server, forms a network topology map, and manages the selected client according to the network topology map. The zero-configuration device connected in the present invention does not need manual participation in pre-configuration or on-site configuration, which saves manpower and improves configuration efficiency.
Owner:FENGHUO COMM SCI & TECH CO LTD
System of soft exchange network passing through firewall based on ALG+MP and its method
InactiveCN100452769CSingle functionImprove shielding effectData switching networksSoftswitchExchange network
Owner:武汉市中光通信公司
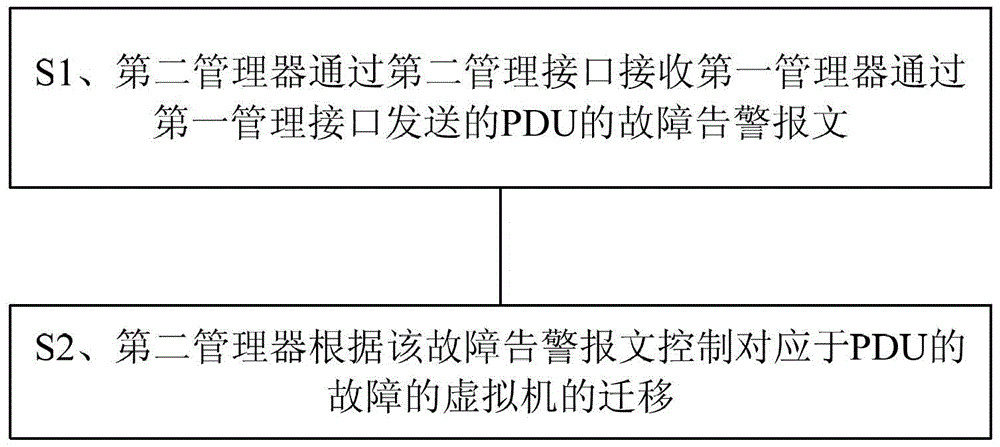
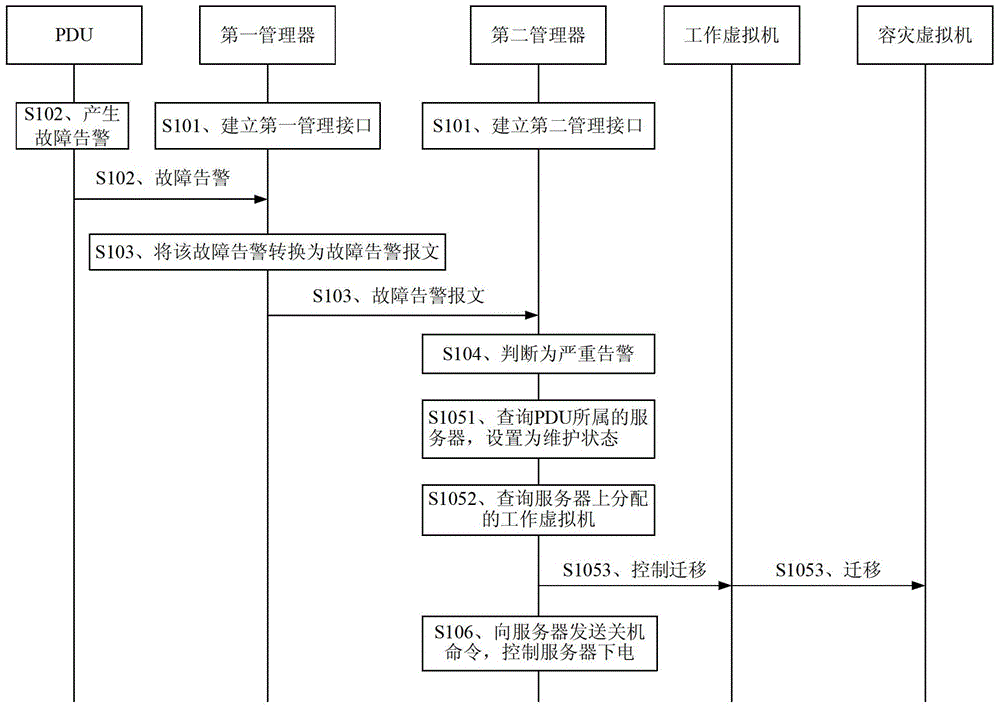
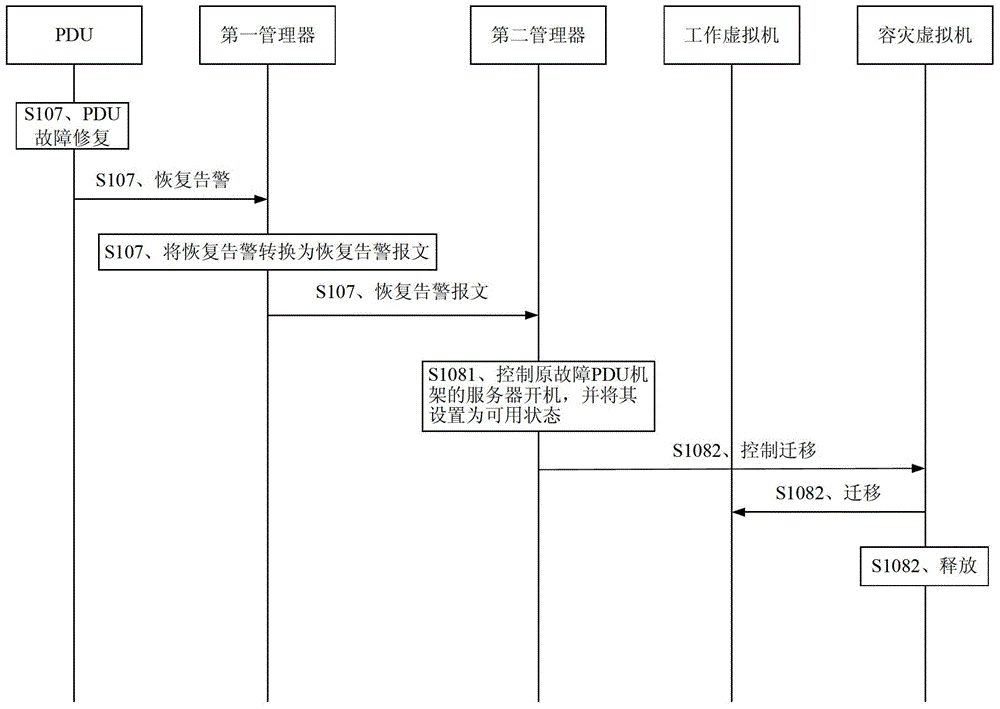
Power distribution unit disaster recovery method, manager and system
ActiveCN103457777BDoes not affect businessReduce manpower requirementsData switching networksAlarm messageCloud data center
The present invention provides a power distribution unit disaster recovery method, manager and system, comprising: the second manager receives the power distribution unit, that is, the fault alarm of the PDU sent by the first manager through the first management interface through the second management interface and the second manager controls the migration of the virtual machine corresponding to the fault of the PDU according to the fault alarm message. Through the power distribution unit disaster recovery method, manager and system provided by the present invention, through the linkage between the first manager and the second manager, the virtual machine can be automatically migrated when the PDU fails, without affecting user services, and the data center cloud After automation, automatic operation and maintenance reduces the manpower requirements for data center operation and maintenance and saves costs for users.
Owner:HUAWEI CLOUD COMPUTING TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com