Security and privacy level maintenance method and device, electronic equipment and storage medium
A privacy-level, security-level technology, applied in the blockchain field, can solve problems such as data matching, inability to update customer security and privacy levels in a timely manner, and poor timeliness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
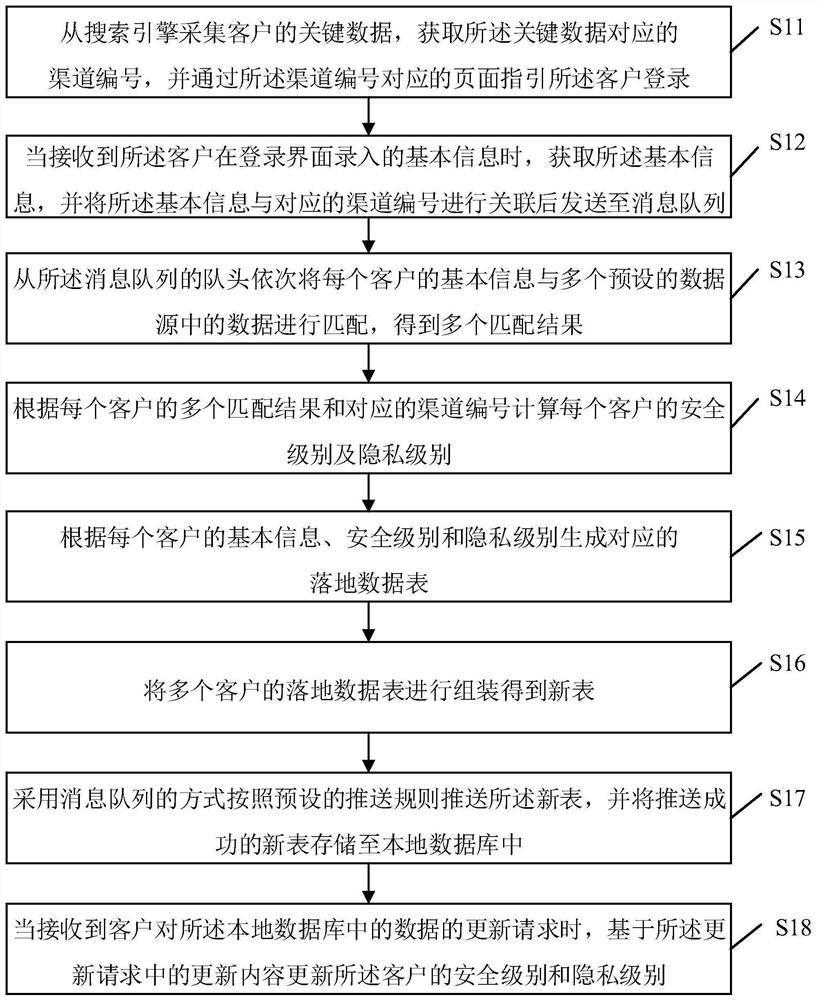
[0061] figure 1 It is a flow chart of the method for maintaining security and privacy levels provided by Embodiment 1 of the present invention.
[0062] The method for maintaining security and privacy levels specifically includes the following steps. According to different requirements, the order of the steps in the flow chart can be changed, and some of them can be omitted.
[0063] S11: Collect the key data of the customer from the search engine, obtain the channel number corresponding to the key data, and guide the customer to log in through the page corresponding to the channel number.
[0064] In this embodiment, the channel number refers to the number corresponding to the media source, and the information left by the customer after browsing the server of the search engine is collected from the search engine, wherein the information includes key data left by the user, the The key data can be the user's mobile phone number, QQ account, WeChat account, etc., and guide the ...
Embodiment 2
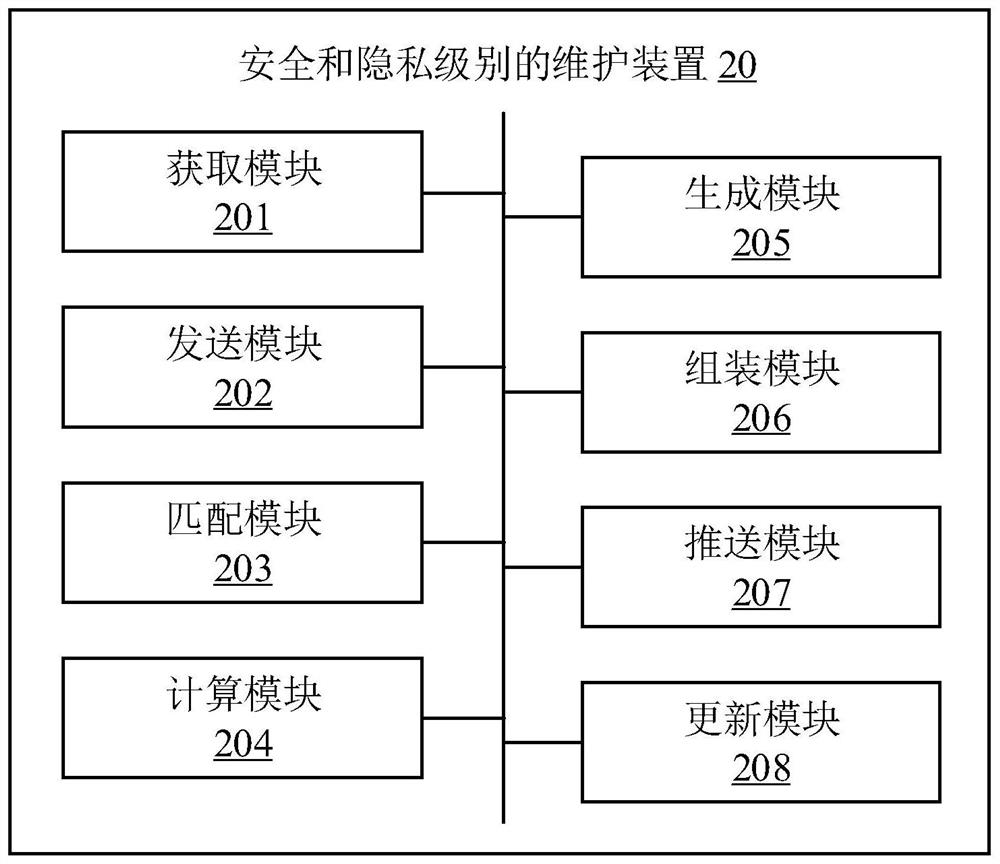
[0118] figure 2 It is a structural diagram of a device for maintaining security and privacy levels provided by Embodiment 2 of the present invention.
[0119] In some embodiments, the device 20 for maintaining security and privacy levels may include a plurality of functional modules composed of program code segments. The program codes of the various program segments in the security and privacy level maintenance device 20 can be stored in the memory of the electronic device, and executed by the at least one processor for execution (see figure 1 Description) Maintenance of security and privacy levels.
[0120] In this embodiment, the device 20 for maintaining security and privacy levels can be divided into multiple functional modules according to the functions it performs. The functional modules may include: an acquisition module 201 , a sending module 202 , a matching module 203 , a calculation module 204 , a generation module 205 , an assembly module 206 , a push module 207...
Embodiment 3
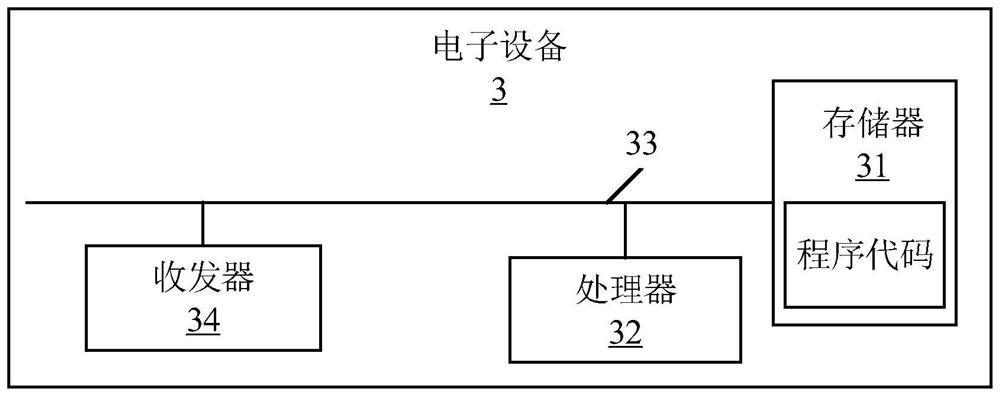
[0173] refer to image 3 As shown in , it is a schematic structural diagram of the electronic device provided by Embodiment 3 of the present invention. In a preferred embodiment of the present invention, the electronic device 3 includes a memory 31 , at least one processor 32 , at least one communication bus 33 and a transceiver 34 .
[0174] Those skilled in the art should understand that, image 3 The structure of the electronic device shown does not constitute a limitation of the embodiment of the present invention, it can be a bus structure or a star structure, and the electronic device 3 can also include more or less other hardware than shown in the figure Or software, or a different arrangement of components.
[0175] In some embodiments, the electronic device 3 is an electronic device that can automatically perform numerical calculation and / or information processing according to preset or stored instructions, and its hardware includes but not limited to microprocessor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com