Token interface degradation method and storage medium
A token and interface technology, applied in the field of security verification, can solve problems such as security risks, algorithm leakage, security risks, etc., to ensure normal use, and achieve the effect of functionality and security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
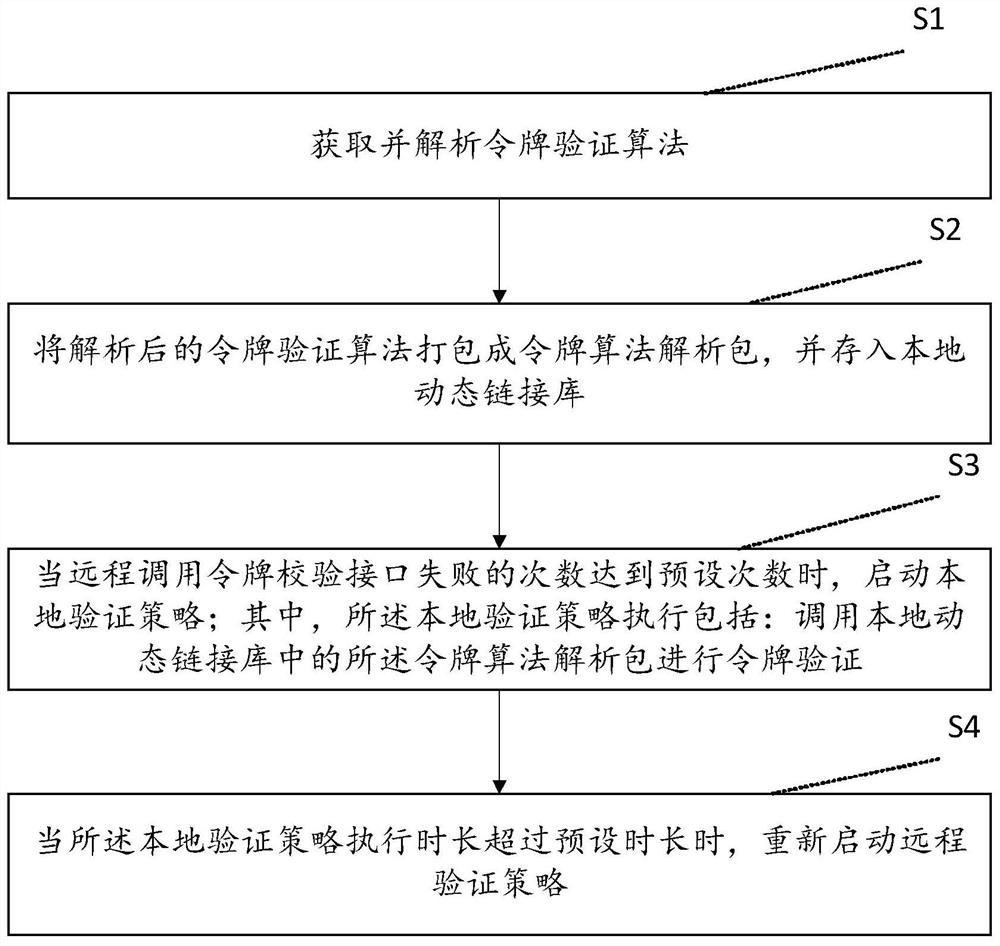
[0064] Please refer to figure 2 , this embodiment provides a method for downgrading the token interface, which supports the caller to independently and flexibly configure the required token verification method, so as to be more suitable for remote verification methods such as the remote token verification interface due to network jitter or failure to respond In the event of failure, ensure that token verification can still be performed safely, and solve the problem that the existing token verification service cannot be provided normally, which affects business processing or directly skips the verification step and brings security risks.
[0065] The method of this embodiment may include:
[0066] 1. Pre-deployment
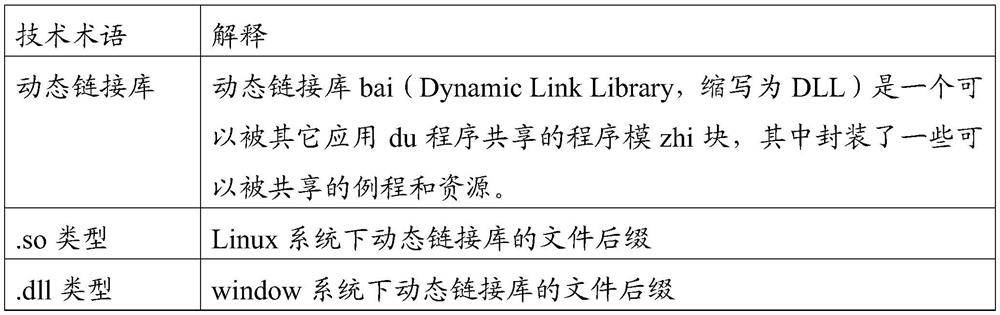
[0067] Suppose the generation rules of the token string (token) are:
[0068] {token version number}_{Token type}_{account type}_{account ID}_{expiration time}_{issuance area}_{5-digit random number}, this is the original plaintext string of the token; The stri...
Embodiment 2
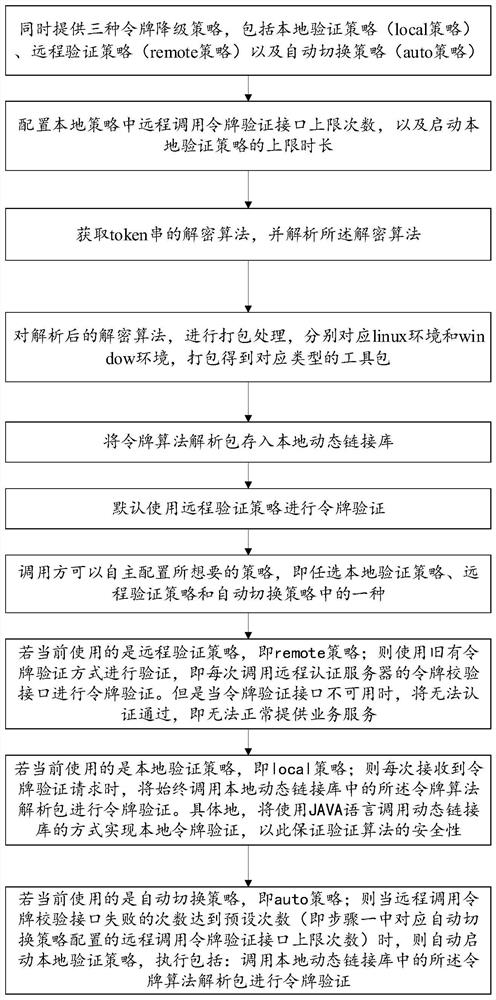
[0101] This embodiment corresponds to Embodiment 1, and provides a specific application scenario, including:
[0102] 1. Assume that the generation rules of the token string are: {token version number}_{Token type}_{account type}_{account ID}_{expiration time}_{issuing area}_{5-digit random number}, this is The original plaintext string of the token, after the string is encrypted by the des encryption method and a fixed encryption key is set, the result obtained is the final token string (ciphertext). The algorithm for parsing the token string (ciphertext) is to use the des decryption method, and also use the same key to analyze the token string, and then obtain the plaintext of the token string.
[0103] 2. There is a UC system, which is what we call the account center system. For the functions of this system, an sdk tool will be provided, that is, a code tool usually provided in the java language, which can package the java language into an sdk tool for other java Systemati...
Embodiment 3
[0123] This embodiment corresponds to Embodiment 1 or Embodiment 2, and provides a computer-readable storage medium on which a computer program is stored. When the program is executed by a processor, it can realize the above-mentioned embodiment 1 or Embodiment 2. The steps involved in a method of token interface downgrade. The specific steps will not be repeated here, please refer to the descriptions of Embodiment 1 and Embodiment 2 for details.
[0124] To sum up, the method and storage medium for downgrading the token interface provided by the present invention realize the automatic reduction and upgrade of the verification mode, can adapt to the current scene, and ensure the safe and normal provision of verification services; and no need to restart Realize the automatic switching of the verification mode and improve the efficiency. Furthermore, the local verification method is improved, which significantly improves the security of the algorithm; further, three token inter...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com